TLS Enabled Syslog
integrations data collectors tls syslog
All collectors come pre-installed with a Syslog listener listening on UDP port 514 and TCP port 601. You can additionally configure a Syslog listener that enables you to send your Syslog traffic over a TLS connection.
Add a TLS Enabled Syslog Listener to an Existing XDR Collector ⫘

Install a TLS Enabled Syslog Application
To add a TLS enabled Syslog listener to an existing Taegis™ XDR Collector, follow these steps:
- From Secureworks® Taegis™ XDR, select Integrations → Data Collectors.
- Select a card from the summary card view or the collector name from the table view for the collector to which you would like to add the TLS enabled Syslog listener.
- Scroll down to the Applications section, select the gear icon for TLS enabled Syslog from the Actions column, and select Configure.
- Select a listening TCP port from the drop down menu.
- Upload a PKCS12 (or equivalent) certificate and enter the certificate password.
Note
Follow the vendor documentation for the source of the TLS Syslog traffic to generate a certificate. See Additional Information and Other Considerations for more information.
- Select Save when complete.
Edit an Existing TLS Syslog Configuration ⫘
If you have an existing TLS enabled Syslog listener, you can make changes to the configuration, such as editing the listening port or uploading and replacing an existing certificate.
Follow the preceding steps to access the configuration panel.

Edit a TLS Enabled Syslog Application
Remove a TLS Enabled Syslog Listener from an Existing XDR Collector ⫘
- From XDR, select Integrations → Data Collectors.
- Select a card from the summary card view or the collector name from the table view for the collector from which you would like to delete the TLS enabled Syslog listener (see Identify a TLS Enabled Syslog Collector for more info).
- Scroll down to the Applications section, and select the gear icon for TLS enabled Syslog from the Actions column. Select Delete from the drop down menu and confirm your selection in the pop up dialog.

Delete a TLS Enabled Syslog Application
Additional Information ⫘
Identify a TLS Enabled Syslog Collector ⫘
A collector with TLS enabled Syslog will show an Installed status under the Applications section of the collector view.
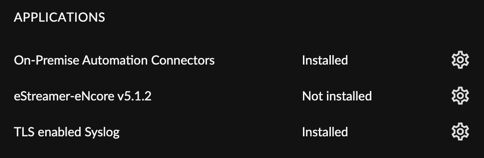
Identify Installed Applications
Generate a Supported PKCS12 File ⫘
As an industry standard, a PKCS12 file is commonly used to bundle a private key with its X.509 certificate or to bundle all the members of a chain of trust.
PKCS12 files are used in XDR to simplify the upload and self-management of your certificates.
Given the appropriate certificates and an associated private key, you can generate a bundled PKCS12 file using the openssl pkcs12 command.
Example ⫘
openssl pkcs12 -export -out server.pkcs12 -inkey server.key -in server.pem -certfile root.pem
Allow Cloud Collector Port Access ⫘
If your collector was provisioned before November 2nd, 2021, your collector’s cloud environment may not have the required firewall (or security group) rules in place to accept traffic on the required Syslog listening ports.
Ensure that you add an ingress TCP rule for your desired TLS enabled Syslog port (514, 6514, or 1470) in your cloud environment before proceeding with the installation of the application.
For more information about configuring the security group, check out the following resources:
Other Considerations ⫘
HA Collector Certificate Generation ⫘
When installing the TLS Enabled Syslog Listeners integration on an HA Collector, the integration runs on all instances and the uploaded certificate is shared by all instances. As such it is important to plan how you intend to configure your clients to send data to the TLS Enabled Syslog Listener. If your network security requirements require end-to-end encryption, then it is recommended to have a Load Balancer in front of the HA Collector that is not performing TLS termination with clients configured to point to a hostname that resolves to the VIP of the load balancer. In this case, issuing a certificate with the Subject equal to the hostname should be sufficient. If you are using any other means of connecting (via IP address) you must ensure the Subject Alternate Name includes all combinations of IPs and hostnames that you intend to use on your clients to ensure certificates are properly validated.
Performance Overhead of TLS Enabled Syslog Listeners ⫘
As with any other TLS enabled connection, sending traffic to a Syslog listener over a TLS connection incurs additional startup and per-packet overhead when compared to an equivalent insecure connection. Because of this, expect a slight drop in peak throughput for your TLS enabled Syslog listener when compared to a standard insecure Syslog instance. To reduce this overhead and to reduce redundant discrete TCP connections, consider enabling the appropriate KeepAlive configuration modules in your Syslog client setup.
Manage Your Certificates ⫘
Any valid PKCS12 certificate is accepted when configuring a TLS enabled Syslog listener for XDR. Certificate management services are not supported at this time, and the recommended best practice is for you to remain in control of your PKI infrastructure.
Configuration Notes ⫘
XDR TLS enabled Syslog listeners support connections with most modern TLS protocols. Deprecated algorithms are not supported. SSLv3 (or below) and TLS 1.1 (or below) are not supported.
