Understanding More Complex Prioritization Factors
This article describes certain, more complex prioritization factors, and how they are computed in order to better explain how they should be interpreted as part of the Contextual Prioritization Score (CPS).
Secureworks® Taegis™ VDR uses more than 45 different factors over thousands of data points in order to prioritize vulnerabilities in a continuous way. These 45+ factors are categorized in five big families, each representing a concentric layer of contextual information around a given vulnerability, with each adding or subtracting points to build the final Contextual Prioritization Score (CPS).
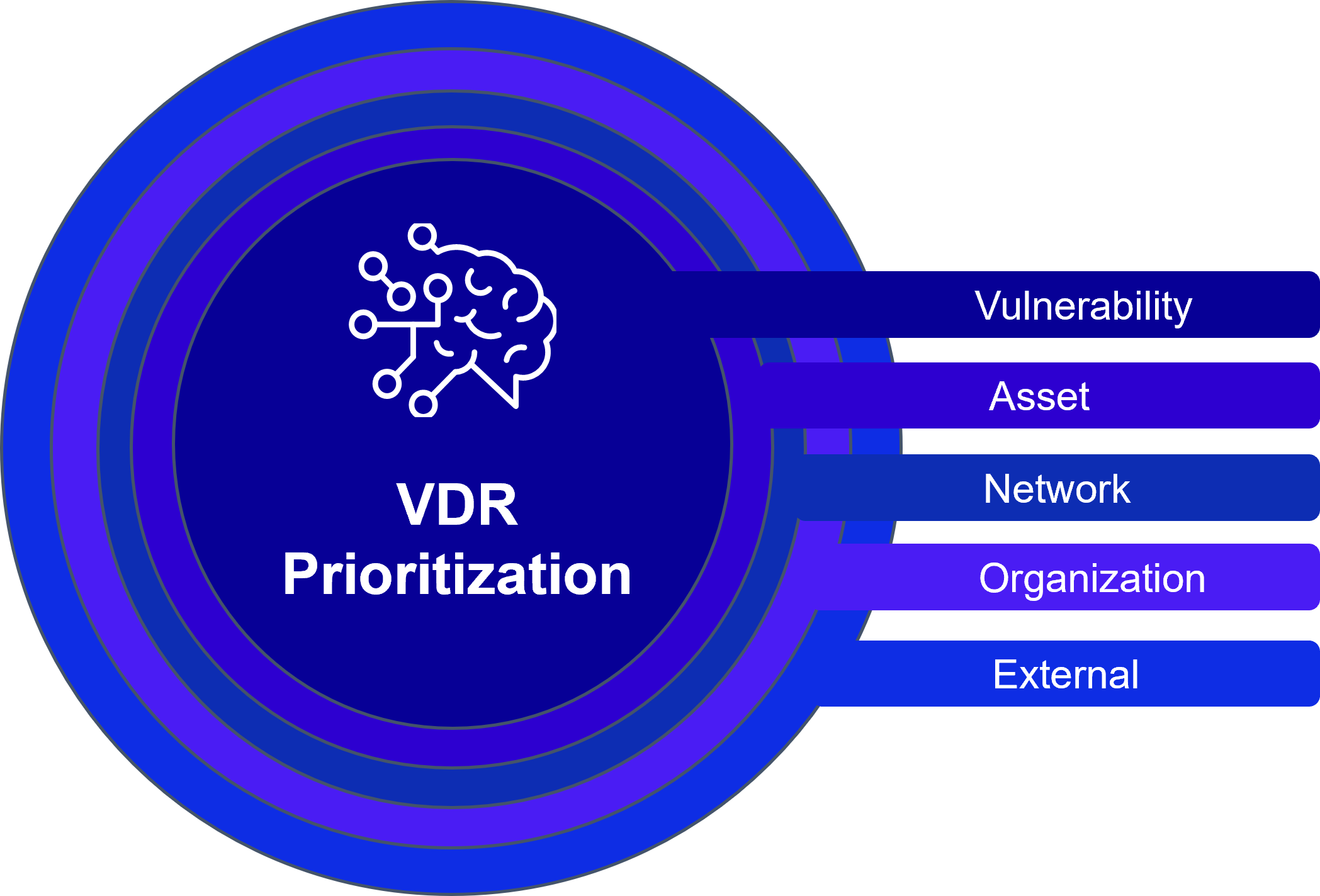
Five Layer Graphic
Some of these factors can be straightforward to understand, but some require more explanation, as follows:
Vulnerability Properties ⫘
Detection Mechanism Is Considered Reliable ⫘
Not all vulnerabilities are detectable in the same way during a Vulnerability Assessment scan, and therefore some detection mechanisms are more reliable than others, providing a better certainty for detection. Since this information can be known in advance, it's already part of the factors that affect the CPS (Contextual Prioritization Score) as soon as we push a new detection rule, so that you don't need to waste time making that judgement by trying to understand how the platform has found a specific vulnerability. This is not the same factor as the "Detection Context" as it represents a different layer of information.
Adjusted for XSS Exploitability Confidence ⫘
Not all XSS payloads in the context where they are found have the same potential exploitability level. Some payloads indicate a bit more work or interaction from the user might be needed to make this XSS viable. As such, this factor represents the level of confidence the platform has towards that specific XSS payload in that context. This is taken into account for these specific vulnerabilities as part of the CPS (Contextual Prioritization Score).
SQLi Exploitability Is Considered Highly Probable ⫘
Not all SQL Injections have the same resilience; for instance, some are based on timing calculations that could be thrown off because of a temporary network issue, or specific behaviors of certain DBMSes. This factor represents the level of confidence the platform has towards that specific SQLi type in the context where it was found. This is taken into account for these specific vulnerabilities as part of the CPS (Contextual Prioritization Score).
Asset Context ⫘
Asset Scan Frequency Stands Out as Important ⫘
Typically VDR is set up to continuously discover and scan all your assets in an autonomous way. Some assets, however, will be scanned more than others, either because you specified different scheduling requirements, or because you launched manual scans on them. This represents a form of attention you're giving to certain assets over others, and as such, it is an analytical metric we can use to affect the vulnerabilities priority through the CPS (Contextual Prioritization Score) on these specific assets.
Asset Has Scheduled Availability Requirements ⫘
Though all assets are discovered and scanned in a continuous way by default in the platform, you can always specify that some of them shouldn't be touched during certain hours, either because they are more sensitive, or play a more critical role during business hours. This is why this simple fact will slightly influence the CPS (Contextual Prioritization Score), as it confers a form of importance or special care to the underlying asset.
Asset Is Important, as Indicated by Its Tags ⫘
As you categorize assets naturally in the platform based on the business line, geographical location, severity, or other factor, some of the tag names can confer a form of heightened importance to the categorized assets. Maybe they are production assets versus your development ones, or maybe they represent critical business functions. The VDR platform does not impose a specific tagging scheme, so that you can naturally represent your reality in the tags, but certain keywords will affect the CPS (Contextual Prioritization Score) and we continuously improve this system through active analysis of tagging schemes.
Tagging Scheme on This Asset Stands Out from the Rest ⫘
As you categorize assets naturally in the platform based on the business line, geographical location, severity, or other factor, some tagging patterns will emerge on assets, especially for certain portions of your network. Certain assets, however, will deviate from this tagging pattern with regards to other assets in the same subnet: maybe it's a special sub-section of this network that represents services consumed by others in the network, or maybe it's a PCI subnet, or some other scenario. As the tagging scheme on these assets stands out from the rest, this difference of entropy will slightly influence the CPS (Contextual Prioritization Score), as it confers a form of importance or special care to the underlying assets.
Network Context ⫘
The Server Significantly Stands Out from Its Network Context ⫘
When pentesters look at very large networks, one of the key activities is to identify which assets are more interesting than others from an attacker's perspective: which are the "gold nuggets."
This factor uses advanced machine learning techniques using our continuously trained models to identify the outlier assets from a large group of machines in the same network, based on the meta-characteristics of the assets (services, OS, ports, etc.). As such, the CPS (Contextual Prioritization Score) will be slightly affected for these outlier assets in the entire subnet as they represent a heightened form of interest for a potential attacker.
Want to see this in action directly? This factor is similar in mind to the Open Source tool we released on our GitHub called Batea, that allows for doing the same "gold nugget" detection straight out of nmap scans, albeit without the use of our pre-trained model.
Simulated Paths of Attacks on the Network Frequently Include This Asset ⫘
By looking at vulnerabilities present on assets and how they relate to each other in the same network, we can use data science techniques to simulate probable paths of attacks from asset to asset in a statistical way. Over thousands of these statistical simulations, we obtain a very good data science-backed approach to understand which assets are the most likely to be targeted during a real attack scenario: they end up statistically more than others on probable paths of attacks. This probabilistic ranking that continuously evolves over time allows for more precision during the evaluation of network-centric factors of the CPS (Contextual Prioritization Score).
Organization Context ⫘
The Underlying Asset Seems Especially Important to the Organization ⫘
As you naturally use the platform to consult and categorize vulnerabilities or assets and as you export reports and remediate vulnerabilities, VDR passively collects these signals from analysts and uses machine learning models that are able to infer what the typical priorities are for specific users in the same organization. We then use this model to infer which assets and vulnerabilities are more important for the organization globally. This allows VDR to influence the CPS (Contextual Prioritization Score) of vulnerabilities on more important assets in your instance, and it is also coupled with knowledge of the global customer landscape, with which we can drive comparative analysis and help you remediate more valuable vulnerabilities.
All of that without having to build and maintain complex tagging and categorization models that require substantial investment of effort over time.
Vulnerability Exposed within the Typical Timeframe for Effective Remediation ⫘
Machine learning is used to predict how long it should take to remediate a specific vulnerability based on a number of factors that are continuously computed. These include the characteristics of the organization itself (each client) but are also influenced by peer-data (what the best teams are doing). The remediation time prediction not only contributes to the CPS (Contextual Prioritization Score), but also provides VDR customers a remediation team benchmarking opportunity.
Detection Context Is Considered Reliable ⫘
To improve the reliability of vulnerability detections, VDR uses machine learning techniques in order to identify how frequently a detection mechanism being used generates false positives, or whether the specific vulnerability has often been identified manually as a false positive in the past, which you can do in the platform. This supervised classification of every vulnerability as either being confirmed or false positive is done using a blend of methods that blindly takes user labels and features (Random Forest Classifier) and prior expert knowledge (Bayesian Networks) in a statistically-sound ensemble machine learning model, just like a democratic process. When a vulnerability has a high chance of being a False Positive, this will slightly affect the CPS (Contextual Prioritization Score), in order to lower the ranking of this specific vulnerability.
External Context ⫘
Trusted Exploits Are Available ⫘
Not all exploits are as efficient and as dangerous, and not all dangerous exploits have successfully been weaponized in either offensive tools or malware kits. This factor's objective is to represent that reality and slightly increase the CPS (Contextual Prioritization Score) for vulnerabilities that have known trusted exploits.
Topics Related to this Vulnerability Are Currently Trending ⫘
This factor continuously surveys online activity from specialized Cyber Security Open Source Intelligence (OSINT) and dark web exchange platforms as Threat Intel feeds and applies machine learning techniques to extract global trends from them. An additional machine learning approach then identifies the most influential actors through the topology of the network of online discussions. By combining these important actors to the identified vulnerability trends, this factor identifies currently important vulnerability trends and correlates them with the ones that are exposed in your environment.
Secureworks CTU Intelligence ⫘
These factors use the Secureworks Counter Threat Unit™ (CTU) (CTU) intelligence to identify notable CVEs. As a result, assets will see a slightly higher CPS (Contextual Prioritization Score) when they have a vulnerability that is related to CTU Intelligence and countermeasures.
Secureworks® Threat Intel Mentions This Vulnerability ⫘
Vulnerabilities that are directly cited in CTU TIPs are more critical. The higher the number of TIP entries mentioning a CVE ID, the higher its CPS will be. Recent TIPs have a higher score than older TIPs.
Secureworks® Advisories Mention This Vulnerability ⫘
Vulnerabilities that are directly cited in CTU Customer Advisories are more critical. The higher the number of entries mentioning a CVE ID, the higher its CPS will be. Recent entries have a higher score than older advisories.
Secureworks® Threat Analysis Mentions This Vulnerability ⫘
Vulnerabilities that are directly cited in CTU Threat Analyses are more critical. The higher the number of entries mentioning a CVE ID, the higher its CPS will be. Recent threat analyses have a higher score than older ones.
Secureworks® iSensor® Rules Target This Vulnerability ⫘
Vulnerabilities that are directly cited in CTU iSensor rules are more critical. The higher the number of entries mentioning a CVE ID, the higher its score will be. Additionally, internet-facing assets are given a higher CPS score. Recent rules also have a higher score than older ones.
Secureworks® Identified Malware / Threat Actors Using This Vulnerability ⫘
Vulnerabilities that are directly cited in CTU identified malware or threat groups are more critical. The higher the number of entries mentioning a CVE ID, the higher its score will be. Recent malware and threat group activity have a higher score than older ones.
Vulnerabilities Predicted to Have an Attack Target Them Are More Critical ⫘
This factor uses supervised machine learning and natural language processing (NLP) techniques to predict the probability of whether a newly published vulnerability will be targeted by a threat, which will increase the CPS (Contextual Prioritization Score). In contrast, a vulnerability predicted to not be the target of a threat will have its CPS diminished. This is accomplished through training on historical data from the CTU attack data and Open Source Intelligence (OSINT) data and identifying the similarity of new vulnerabilities to previously targeted vulnerabilities. The factor outputs the following information:
- The probability of an exploit being published in the near future.
- The probability that the vulnerability will be used by malware in the near future.
Vulnerability within CISA Known Exploited Vulnerability Catalog ⫘
This factor correlates observed vulnerabilities within your environment to the CISA Known Exploited Vulnerabilities Catalog. This catalog is maintained by the CyberSecurity & Infrastructure Security Agency (CISA) and contains a list of vulnerabilities that are known to have been exploited. This factor will increase the CPS (Contextual Prioritization Score) for vulnerabilities in your environment that are contained within the CISA list.
