Consulting Scan Results
This article describes how to consult scan results after the scans have successfully launched and completed.
After scans have successfully launched and completed, the scan results and report details can be viewed in multiple ways: by selecting a vulnerability from the Vulnerabilities view, or by selecting an asset from the Websites and Servers view and choosing the Vulnerabilities tab.
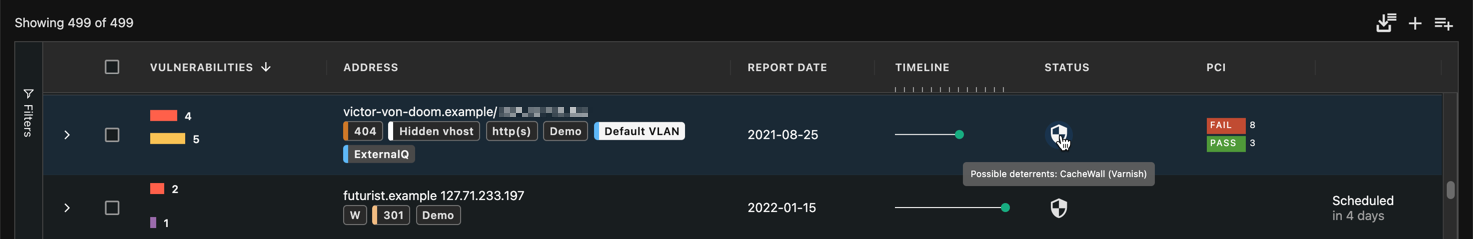
In the Websites or Servers view, certain icons might be visible right after the last report date to indicate important information related to the most recent scan.
If Secureworks® Taegis™ VDR detected one (or multiple) Web Application Firewalls (WAFs) during its web scan, a small shield icon will be displayed in the Status column with a tooltip indicating which WAF was detected. It is important to note that WAFs can affect the quality of Web applications vulnerabilities detection, since their primary role is to block these types of attempts (while leaving the applications code potentially vulnerable). Scan results may vary and be of a lesser quality for assets protected by WAFs.
Scan Results
The entry in the Report Date column lists the date of the last successful scan. Select the asset from the list to view details of the scan in the Vulnerabilities tab, and select the Report Date entry to choose the date of a prior scan to view those details.
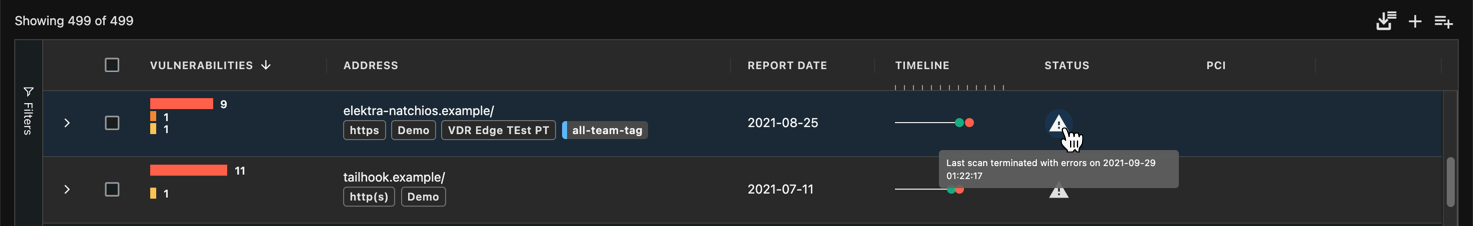
If a scan terminates with an error (because the asset was unreachable, a sudden loss of connectivity, etc.), a warning icon will be displayed in the Status column to inform you of this type of failure.
Scan Error
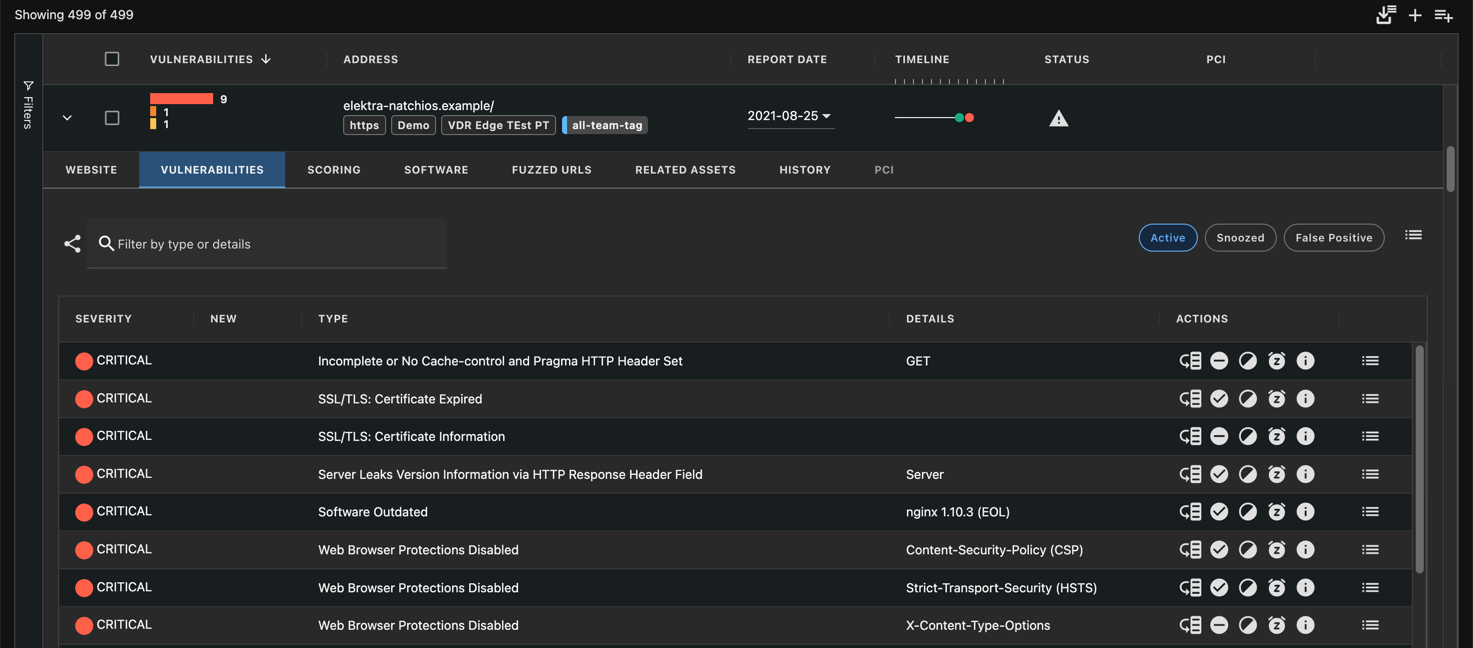
The Vulnerabilities tab of the asset details contains details of the scan itself and all the vulnerabilities that were found during the specific scan listed in the Report Date column.
Further security information relevant to the specific asset that was detected during the scan is available in other tabs of the asset details.
Tip
A PDF version of the report can be produced, including all the vulnerability detail, by selecting the share icon from the top left of the Vulnerabilities tab. See Creating Vulnerability Reports for more information.
Vulnerabilities are sorted according to their severity level in four pre-set categories:
- Critical Vulnerabilities are the ones that are the most likely to be exploited and that require immediate attention and mitigation.
- Medium Vulnerabilities are potentially exploitable and require further analysis to ensure they are addressed in a timely manner.
- Warnings are meant to indicate areas where the security could be reinforced to help mitigate further potential vulnerabilities over time.
- Additional information gathered relates to additional information VDR was able to gather while scanning that may be useful for a better understanding of the environment's complete security posture.
Report Vulnerabilities
Vulnerabilities vary greatly for every asset, so expect differences between web applications and server scans; however, their presentation follows the same pattern.
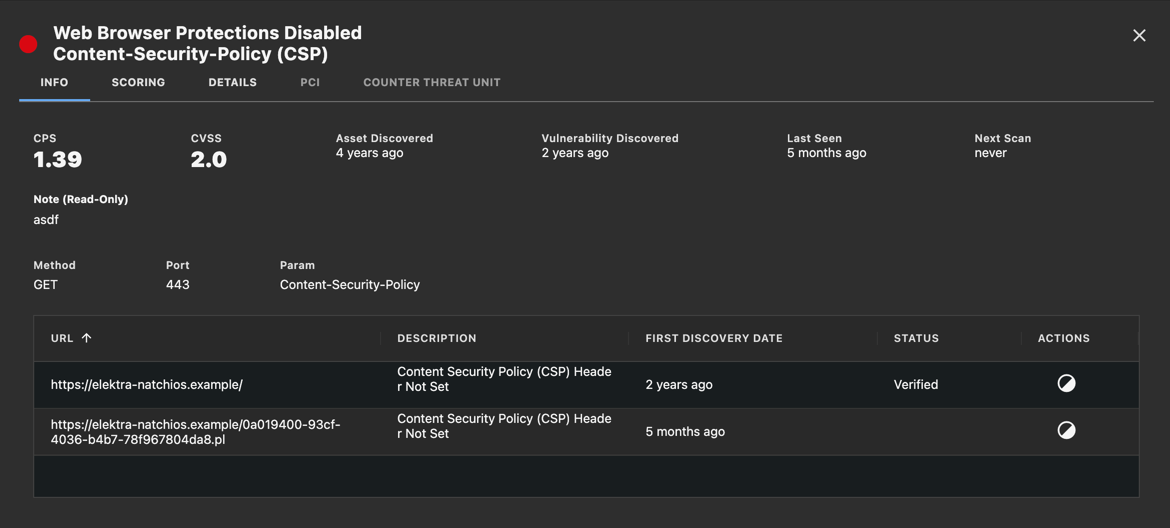
Select the Show More info icon from the Actions column to view the details of the vulnerability.
For instance, in the case of a web vulnerability (when applicable), the Method, Location, Parameter, and Payload that allowed this vulnerability to be found will be provided.
Web Vulnerability
In the case of system vulnerabilities (when applicable), a CVE number could be provided with technical details on the vulnerability itself.
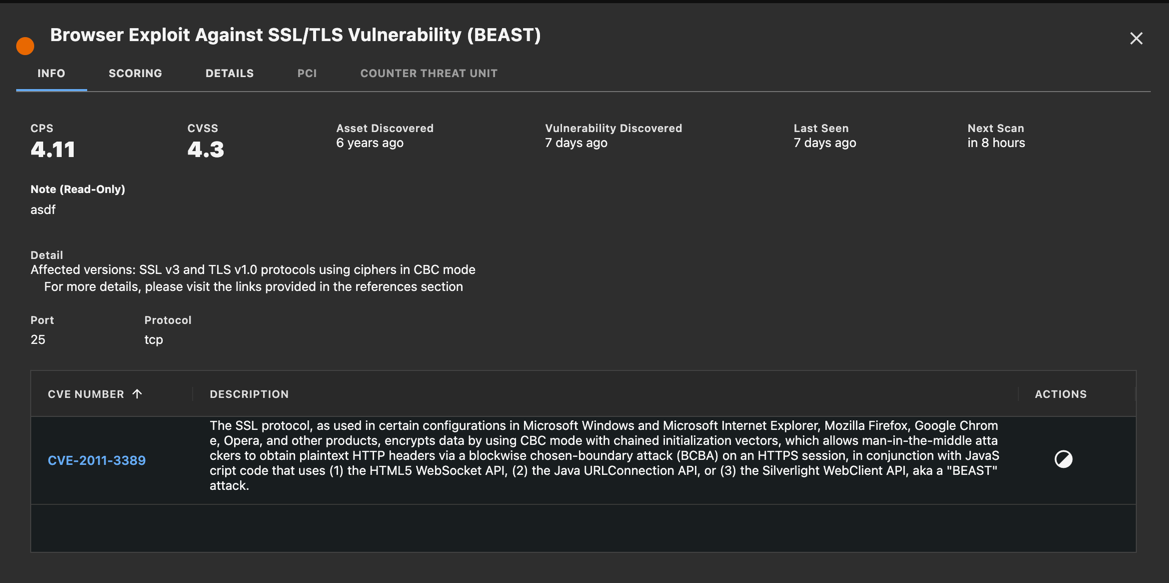
System Vulnerability
For most vulnerabilities, a description, remedy, and references will also be provided in the Details tab, allowing you to obtain more details about the vulnerability using standardized and online documentation.
In addition to the vulnerabilities that were found, entries with additional information will be presented in this report detail view.
The port list of a system that was scanned may also be shown in the Ports tab of the asset details with a description of the official Internet Assigned Numbers Authority (IANA) service name and description.
If the service presence was validated, it will be displayed in darker text. If a banner was grabbed during service validation, it is made available through a link on the right of the service name.
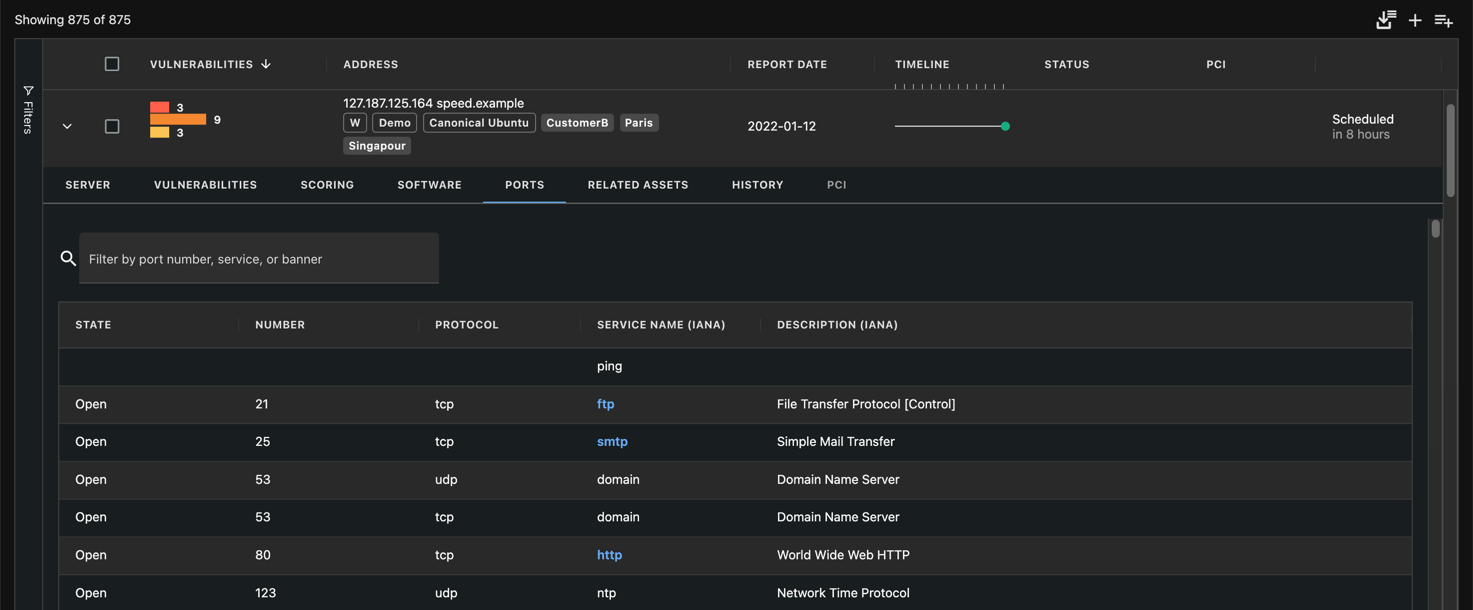
Port List
A list of the software that was detected may also be provided in the Software tab of the asset details view for systems and websites.
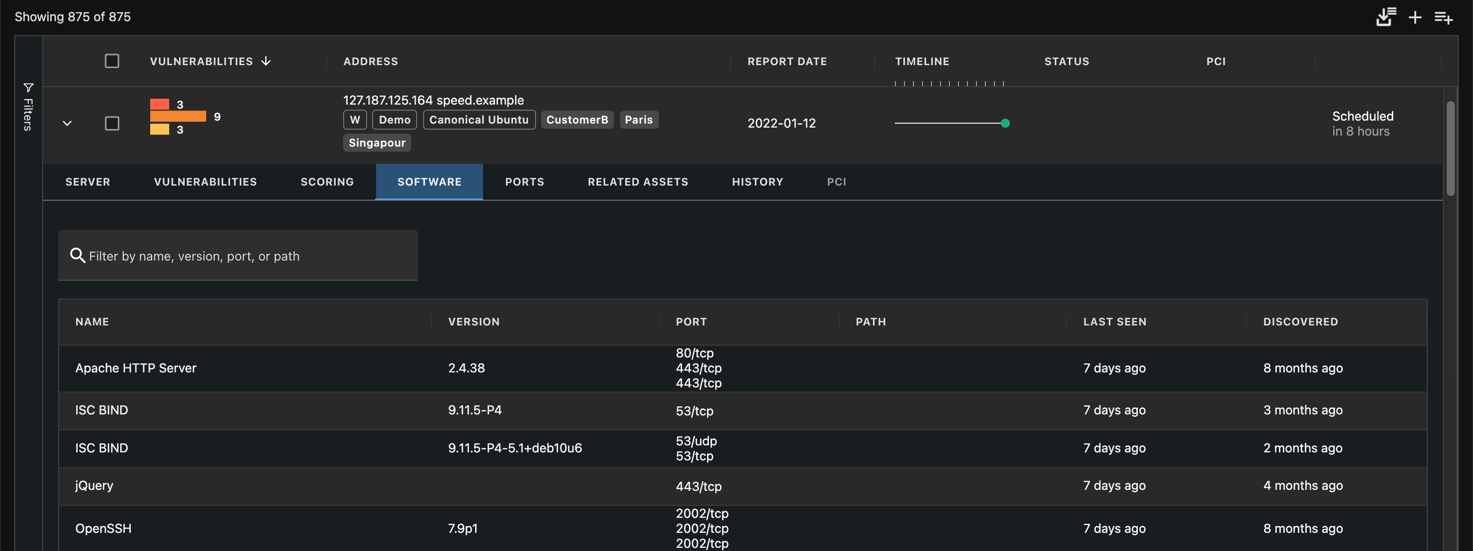
Software
