Using the Okta Authorization Server with VDR
This article describes how to set up Okta authentication in Single Page App mode in order to use it instead of Secureworks® Taegis™ VDR’s built-in authenticator.
Follow this guide to create your application inside Okta to use your own authorization server to use VDR. You must create a user account in VDR for each user authenticating via Okta. Each account must be associated with the same email address in VDR and Okta.
Following this configuration will also allow Okta-initiated login via the Okta My Apps portal.
Step-by-Step Guide ⫘
- Log in to your Okta Admin account. The URL should be something like https://
<company-name>.okta.com/. - Select the Applications menu, choose the Add Application button, and then select Create New App.
- Select Single-Page App as your platform (sign-in method should be OpenID Connect).
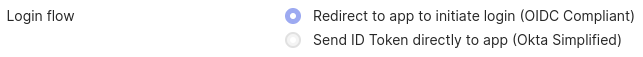
Okta Login Flow
- Complete the form with the following information:
- Name: VDR
- optional Base URIs: https://
<vdr-instance>.vdr.secureworks.com - Login Redirect URI:
- https://
<vdr-instance>.vdr.secureworks.com/auth/okta/authorize (for VDR UI & API)
- https://
- Group assignments: Any group in your Okta domain to which you want to give access to VDR
- Once completed, make sure the provided information is correct.
- Send this info to VDR Labs by email:
- Okta Domain (e.g., company.okta.com)
- Okta App Client ID
Warning
VDR expects an email address as the authentication identifier in order to match the Okta identity to a VDR User (VDR users are identified with their email address as it appears in VDR under Settings > Users).
If your users log in to Okta using email@domain.com, you likely do not require any Profile mapping changes in Okta.
If your users log in to Okta using an attribute other than an email, such as a userid (e.g., first.last), then you will need to update the Okta Profile for VDR using the following steps.
(Optional) Update Okta Profile Mappings to Pass Email as Login ⫘
As noted in the preceding warning section, it might be necessary to create a custom Profile mapping in Okta to ensure that the email attribute is sent as the login variable to VDR. This customization can be done in Okta on a per application basis.
- In Okta, navigate to Applications > VDR, select the Sign On tab, and then select Configure profile mapping in the Settings section.
- In VDR User Profile Mappings, select Okta User to VDR.
- Select the Override with mapping option next to User is set by. This will add a new row at the top of the attribute list.
- Choose the attribute email (also shown as
user.email), and in the second column, select Apply mapping on user create and update. - The updated attribute mapping shows the attribute
user.emailmapped touserName. - Select Save Mappings and then Apply updates now to save changes.
- Log in to VDR using the Okta option with your Okta Domain, similar to the following screenshot:
Okta Login
