Create an AWS CloudFormation Stack
- Log in to the AWS Console with an account that has permissions to create roles, lambdas, secrets, and policies, or using a role that can assume another role with these permissions.
- In the Management and Governance section, select CloudFormation.
- Select the orange Create Stack button.
Note
Alternatively you might see a list of CloudFormation stacks when you select CloudFormation like the following image. If that is the case, select the Create Stack drop down and choose With new resources (standard).
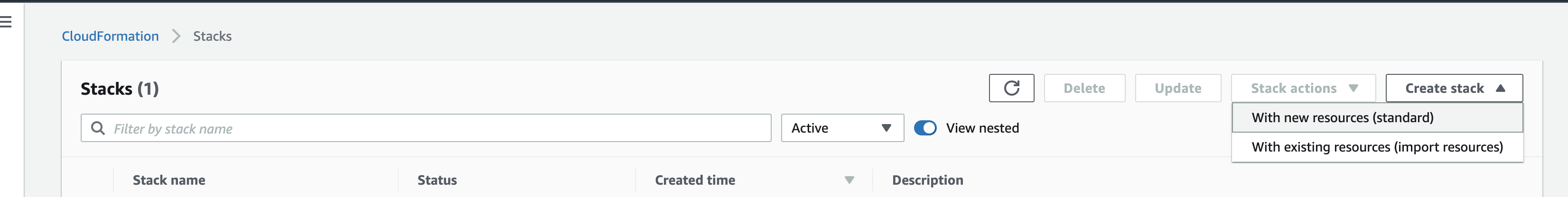 Alternate CloudFormation View
Alternate CloudFormation View
- From the Prepare Template selector choose Template is ready.
- From the Specify Template selector choose Amazon S3 URL.
-
Input the CloudFormation object URL gathered previously into the Amazon S3 URL field. For example:
https://cf-templates-1qg1cz0jktk-us-east-1.s3.amazonaws.com/tdr-lambda-cloudformation-for-awsCloudTrail-hasVpc-false.yaml. -
Choose Next. On the following screen, enter an appropriate stack name.
Note
Spaces are not allowed in stack names.
Lambda Location ⫘
- Enter the S3 bucket name, not a URL or URI, and key you created in the Upload the Lambda Executable and CloudFormation Template to S3 section into S3Bucket and S3Key, respectively. See AWS ALB, AWS VPC, AWS WAF, Cisco Umbrella, or Cloudtrail.
Note
The default value for S3Key is tdr-lambda.zip. You must change it if the zip filename was renamed after the download. The default values under LambdaConfig are normally unchanged.
Tip
If you receive a KMS Decrypt or related error message, see Adding kmsDecrypt Permission To Lambda For Encrypted Logs.
Integration Configuration ⫘
- For
NotificationBucket, enter the bucket name, not a URL or URI, that houses the CloudTrail Logs. -
In SecretValue, copy/paste in the full output received after selecting Download Credentials on the Taegis™ XDR Add Integrations page.
-
Select Next.
- (Optional) Enter any Tags needed for billing tracking or other purposes.
- (Optional) Select an alternate IAM role for CloudFormation to use when creating this stack.
- (Optional) Enter any Advanced options needed by your organization.
- Select Next.
- Review all parameters. Make sure that all fields you have specified from Step 4 through to Step 15 have a valid value.
- Scroll to the bottom and check
I acknowledge that AWS CloudFormation might create IAM resources. - Select Create stack .
- Wait at least 30 seconds then select the refresh button. The process may take a minute or more to finish. A status of CREATE_COMPLETE for the stack indicates the process has finished. The JSON containing the client_id and client_secret should be discarded. These values are now stored in the AWS SecretsManager.
Add the Lambda Trigger ⫘
- In the AWS console, switch to the Lambda service.
- Locate the new lambda by name. The default name is STACKNAME-scwx-tdr-lambda-for-INTEGRATIONSELECTED.
- Select the lambda name. The edit page for that lambda displays.
- Expand the Function overview, and in the Designer section, choose Add Trigger.
- In the Trigger Configuration editor, select the drop down menu and choose S3. Additional configuration options display.
- From the Bucket options, find the bucket containing the CloudTrail logs and select it.
- From the Event Type options, choose All Object Create Events.
- In the prefix field, enter the bucket prefix where the CloudTrail logs are located. Leave this blank if no prefix is used.
- Leave the suffix field blank.
- Check the following box to acknowledge the cost impact of a lambda function.
- Choose Add. The configuration page for that lambda displays again. A message displays at the top indicating adding a trigger was successful; for example: "The trigger wmikeking-CloudTrail was successfully added to function CloudTrail-Logs-TDR-Upload".
- The function is now receiving events from the trigger.
Important
AWS Concurrent Execution Limit ⫘
If you see the following error when running your lambda:
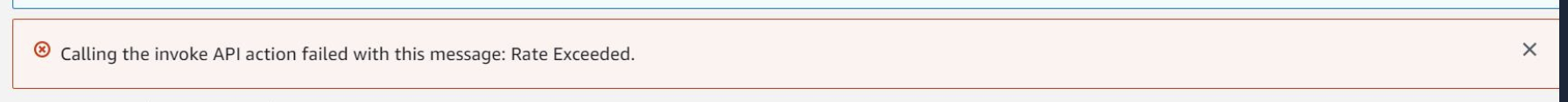 You need to request a quota increase from AWS to raise your concurrent execution limit. For more information, see Lambda quotas from AWS Docs.
You need to request a quota increase from AWS to raise your concurrent execution limit. For more information, see Lambda quotas from AWS Docs.
