Brute Force
The Brute Force Detector identifies instances where a threat actor has attempted to break into an Active Directory environment by repeatedly trying different passwords, in the hope that eventually a correct combination is found. The Brute Force Detector processes streams of auth events and creates an alert when there is a particular sequence of auth failures followed by a successful logon within a small time window.
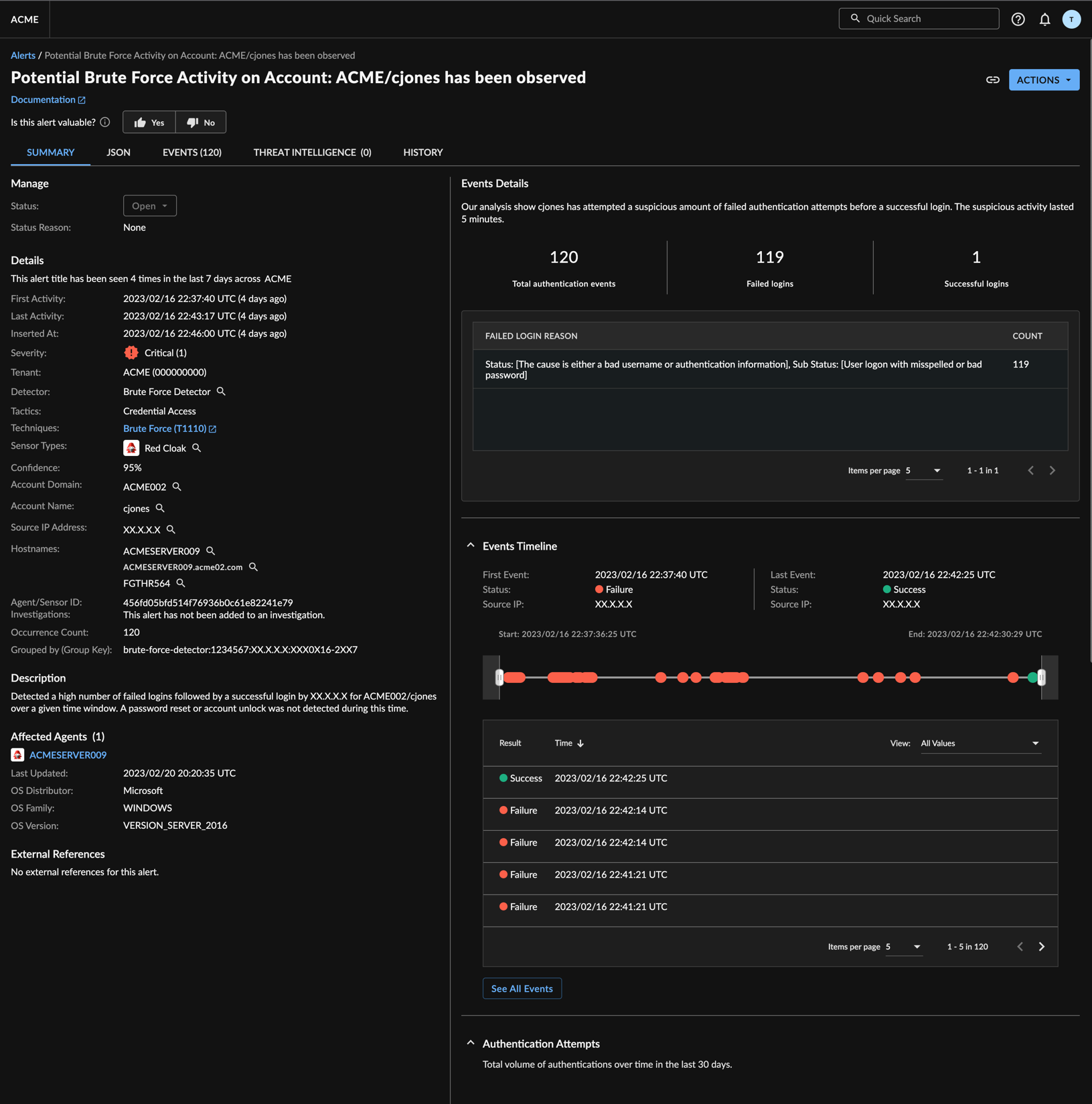
Brute Force Detector
Note
The Login Failure Detector is now no longer available in Secureworks® Taegis™ XDR, and has been superseded by the Brute Force Detector.
Schema ⫘
Auth
Outputs ⫘
Alerts pushed to the XDR Alert Database and XDR Dashboard.
MITRE ATT&CK Category ⫘
- MITRE Enterprise ATT&CK - Credential Access - Brute Force. For more information, see MITRE Technique T1110.
Configuration Options ⫘
None
