Portscanning and Broadscanning
The Portscanning and Broadscanning Detectors identify attempts by a threat actor to search assets in your environment for open ports that might present attack opportunities. They do this by attempting to open a connection from one machine to another, and if the connection succeeds, then the port is open.
There are two subversions of this activity:
- Portscanning looks for many open ports of interest on a single asset.
- Broadscanning looks for many portscan activities on a large number of assets.
These detectors process streams of netflow data and look for the combinations of events that match the threshold criteria.
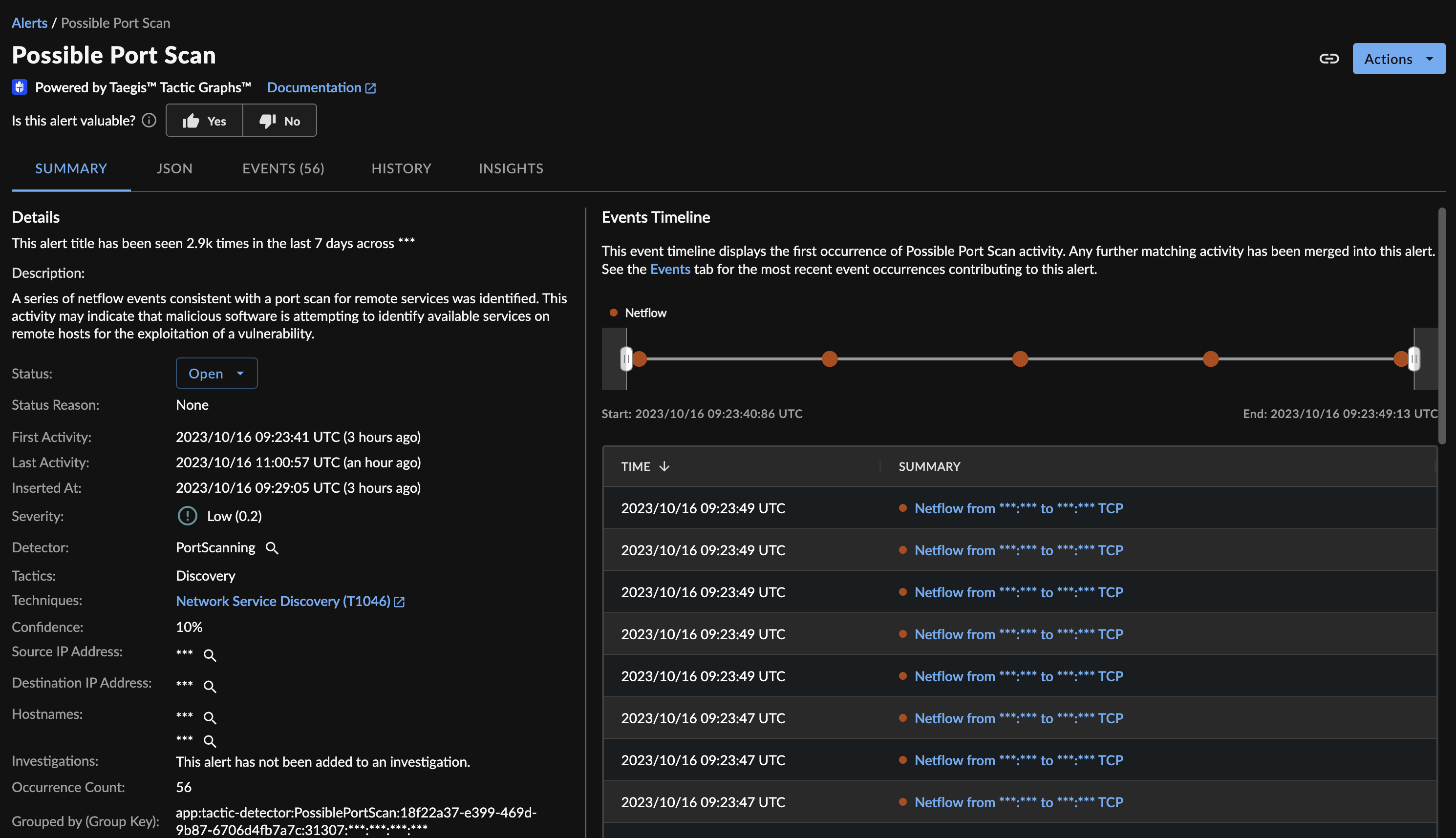
Portscanning Alert
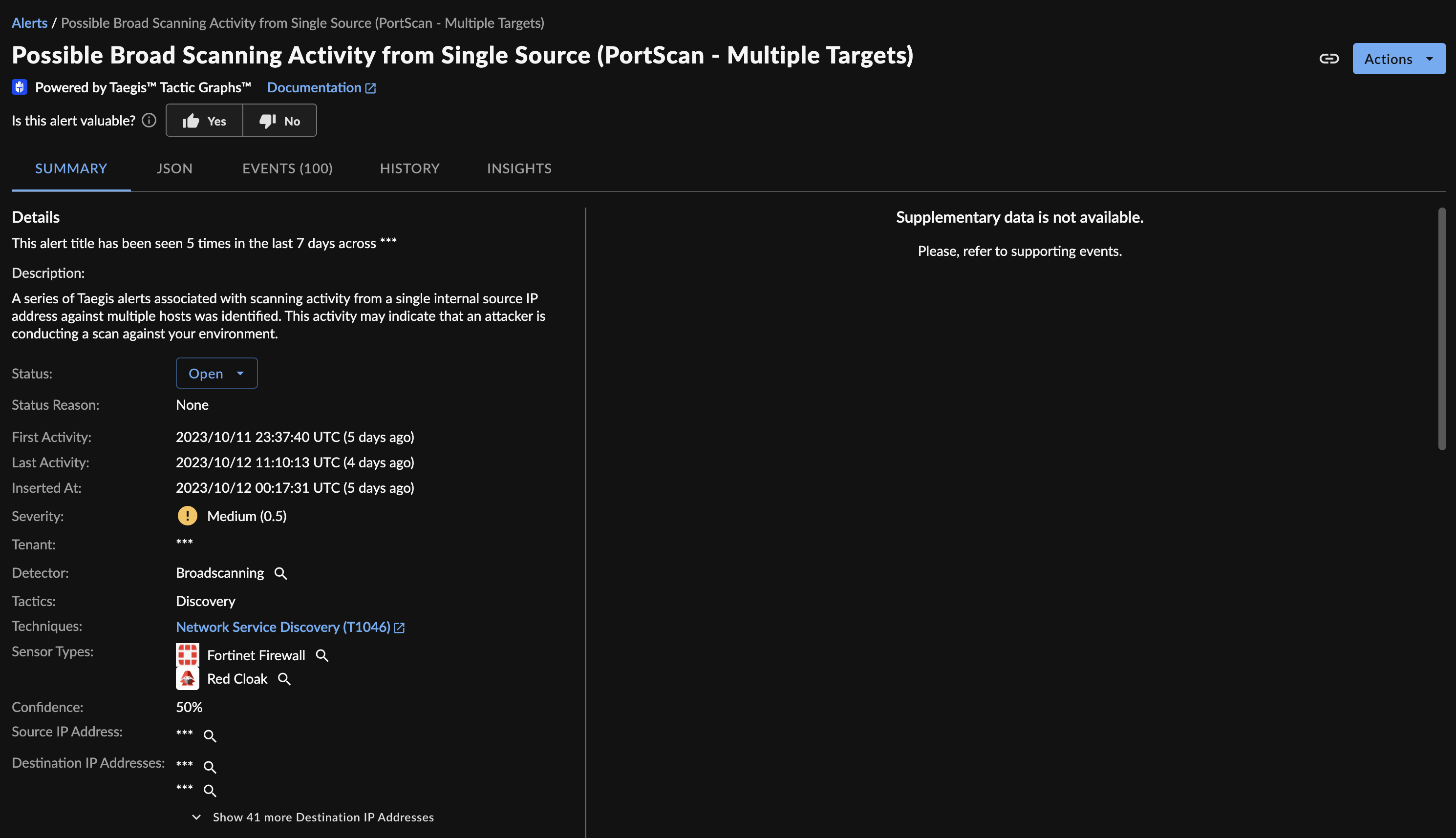
Broadscanning Alert
Schema ⫘
Netflow
Event Filtering ⫘
Events are filtered to match the following criteria:
- Source and destination addresses are internal / loopback
- Set of important destination ports
Outputs ⫘
Alerts generated by Tactic Graphs™ Detector are pushed to the Secureworks® Taegis™ XDR Alert Triage Dashboard.
MITRE ATT&CK Category ⫘
- MITRE Enterprise ATT&CK - Reconnaissance - Gather Victim Network Information. For more information, see MITRE Technique T1590.
- MITRE Enterprise ATT&CK - Reconnaissance - Active Scanning. For more information, see MITRE Technique T1595.
