Account Compromise
The Account Compromise Detector identifies an account that exhibits signs of being taken over by a threat actor. The detector combines multiple entities related to user login and post-login behavior to deliver a more comprehensive view of account behavior and produce more true positives. If multiple suspicious actions are seen, it is more likely that the account is being used by a threat actor. Entities are provided to the Account Compromise Detector by other Secureworks® Taegis™ XDR detectors including Password Spray and Kerberoasting.
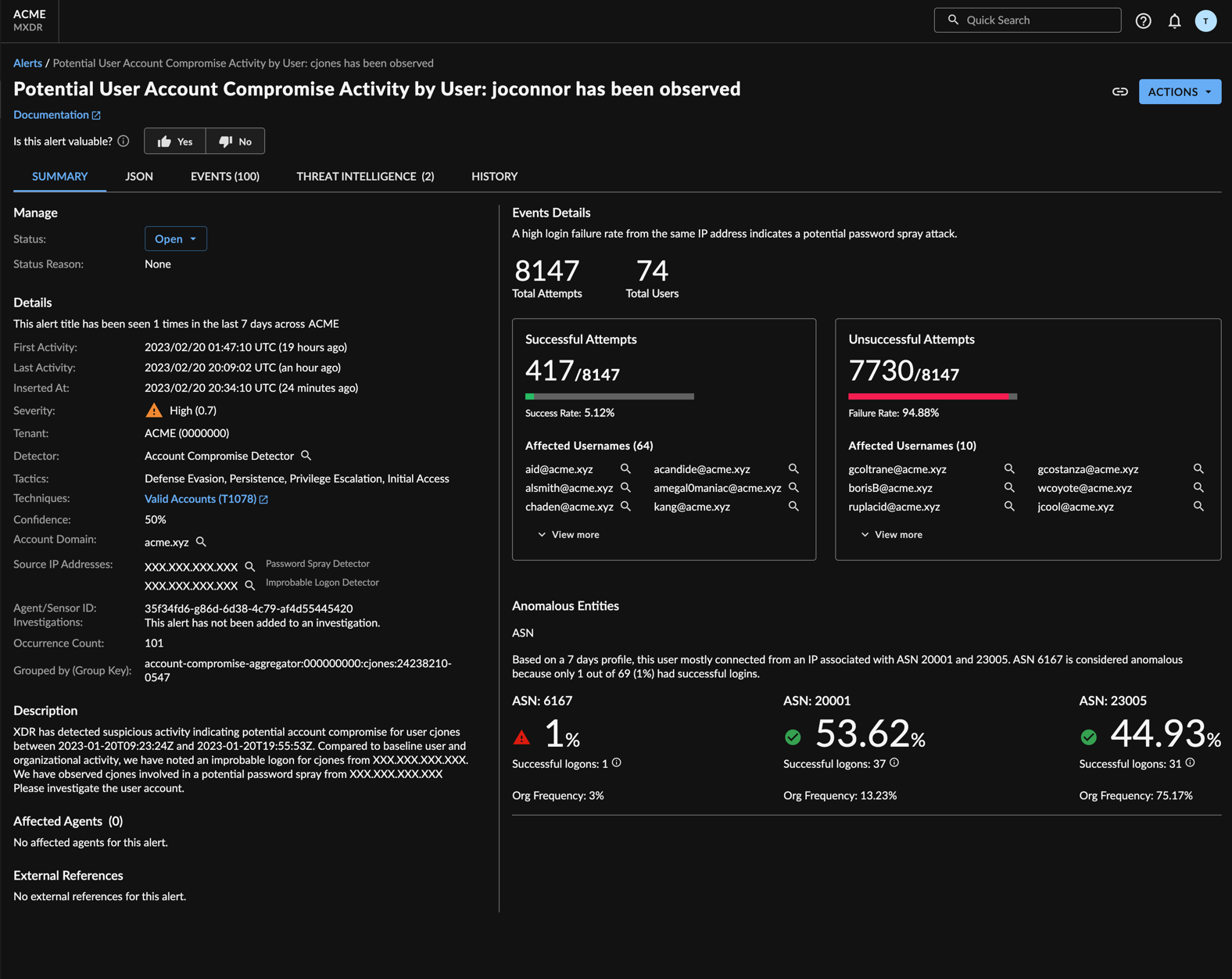
Account Compromise Alert
Schema ⫘
Auth, by way of detections from input detectors.
Inputs ⫘
Detections from the following sources:
- Password Spray Detector detections
- Kerberoasting Detector detections
- Logons from a user with anomalous characteristics (e.g., rare country/ASN based on user’s past activity, which is also abnormal for other users in the company)
Outputs ⫘
Alerts pushed to the XDR Alert Database and XDR Dashboard
MITRE ATT&CK Category ⫘
MITRE Enterprise ATT&CK - Defense Evasion, Persistence, Privilege Escalation, Initial Access - Valid Accounts. For more information, see MITRE Technique T1078.
Configuration Options ⫘
None
