Rare Program to Rare IP
The Rare Program to Rare IP Detector looks for a combination of a rare program hashes executed and traffic with rare destination IP addresses on a single host within the same time period.
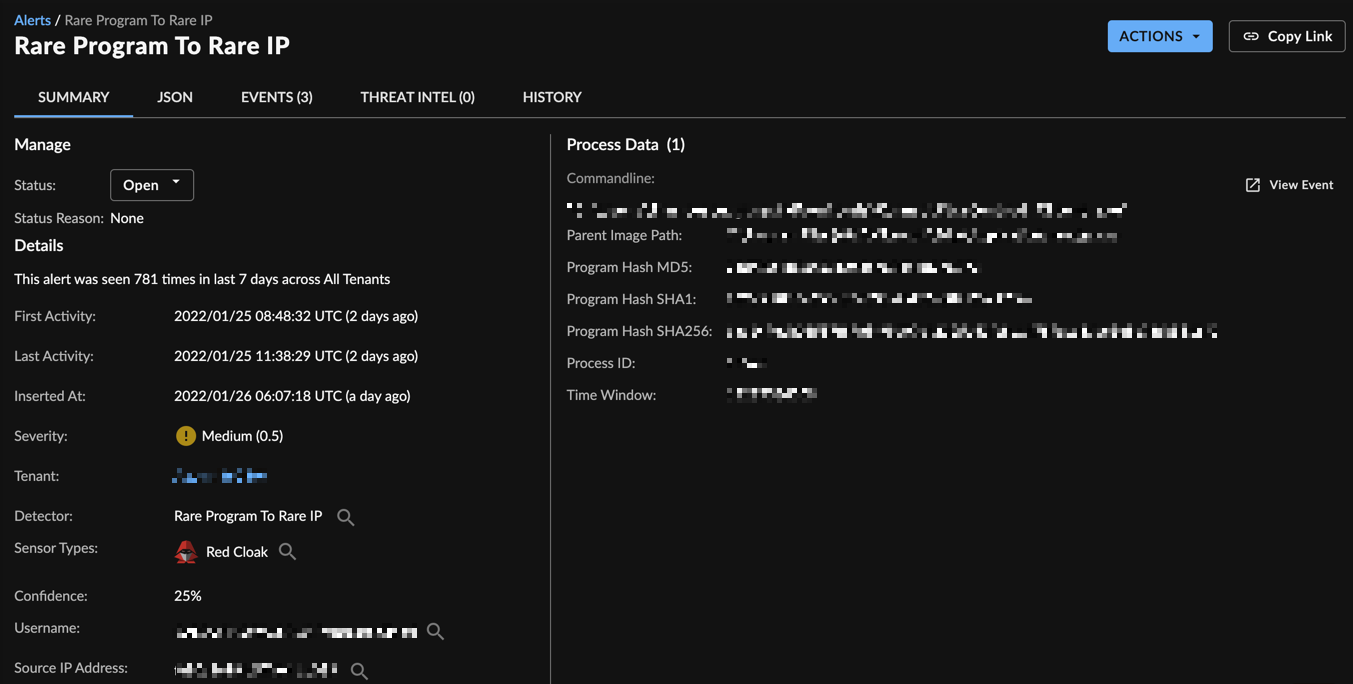
Rare Program and Rare IP Alert
If there is a correlation—that is, the process id and process time window of the process and destination IP address match—between the destination IP and the rare program for the same host, an alert is sent to the Secureworks® Taegis™ XDR Alert Database and Dashboard. The recommended action for an alert is to pivot on the host or source IP address listed in the alert and to look into the user that executed the process listed in the alert.
Rare is defined as unique within the entire XDR data lake within a period of 60 days. Rare doesn’t necessarily mean the program is malicious. Adversaries might craft a weaponized valid program or even deploy outdated and vulnerable programs to exploit these. At the same time, unsuccessful patch management might also leave outdated programs behind that this detector potentially could surface. Therefore the detection helps increase visibility to potential entry vectors for adversaries.
Schema ⫘
Netflow, Process
Outputs ⫘
Rare Program to IP alerts pushed to the XDR Alert Database and XDR Dashboard.
MITRE ATT&CK Category ⫘
The Rare Program to Rare IP Detector has no MITRE Mapping.
Detector Requirements ⫘
- Netflow, Process
