Palo Alto Firewall Integration Guide
integrations network palo alto firewall
The following is a guide for configuring the Palo Alto Firewall or Panorama to send system, configuration (audit), traffic, and security events to Secureworks® Taegis™ XDR.
Implementation Requirements ⫘
| Source | Destination | Port/Protocol |
|---|---|---|
| Palo Alto Firewall or Panorama | Taegis™ XDR Collector IP | UDP/514 |
Note
Naming conventions in this doc are suggestions for reference and not required. Names included in screenshots may differ from the suggested naming conventions.
Note
Saving some steps may require using the Commit button in the Palo Alto configuration interface. For more information on using Palo Alto see Palo Alto Documentation.
Data Provided from Integration ⫘
| Antivirus | Auth | DHCP | DNS | Encrypt | File | HTTP | Management | Netflow | NIDS | Process | Thirdparty | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| PaloAlto Firewall | D | D | D | V |
Y = Normalized | D = Out-of-the-Box Detections | V = Vendor-Specific Detections
Note
XDR detectors are not guaranteed to be triggered, even if a data source's logs are normalized to a schema associated with a given detector. However, you can create Custom Alert Rules to generate alerts based on normalized data from a data source.
Palo Alto Firewall v8.0 - v9.x - v10.0 Configuration ⫘
Important
If security rules are configured with the default profiles you will need to clone the existing profiles and then modify each rule to use the new, cloned profile.
Sending Logs from the Palo Alto Firewall to XDR Only ⫘
Syslog Server Profile ⫘
The Syslog Server Profile is used within different configuration sections of the PAN device to forward logs to a specific syslog server or servers.
-
From the Device tab, select Server Profiles → Syslog from the left-hand tree menu. The Syslog Server Profile Dialog displays.
-
Name the profile TDR-COLLECTOR.
- Add a server entry named TDR-SYSLOG with the XDR Collector IP address.
- Select the option LOG_LOCAL1 under Facility.
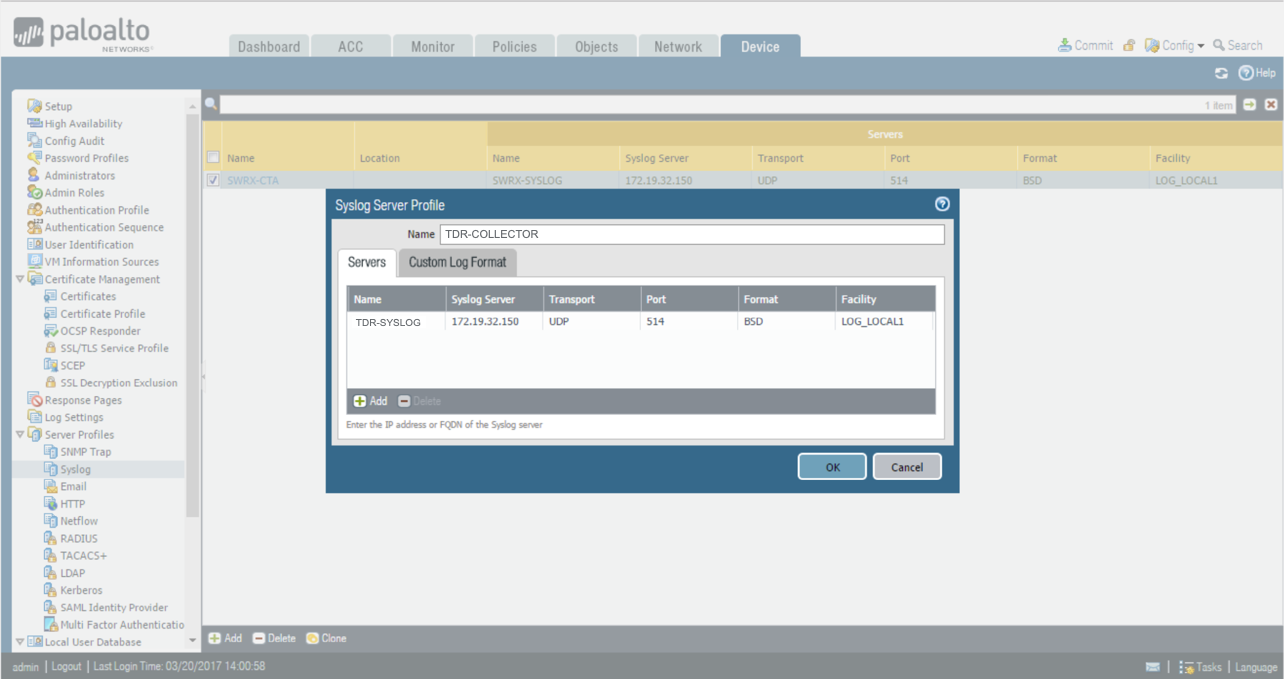
Syslog Server Dialog
Log Settings ⫘
The Log Settings section is used to handle logs not handled by the Log Forwarding Profile. The Log Settings section handles System, Configuration, User-ID, HIP Match, IP-Tag (9.0+), GlobalProtect (9.1+), and Correlation (9.1+) logs. The Log Forwarding Profile handles Auth, Data, Threat, Traffic, Tunnel, URL, and Wildfire logs.
On the Firewall, scroll down to be able to see all types.
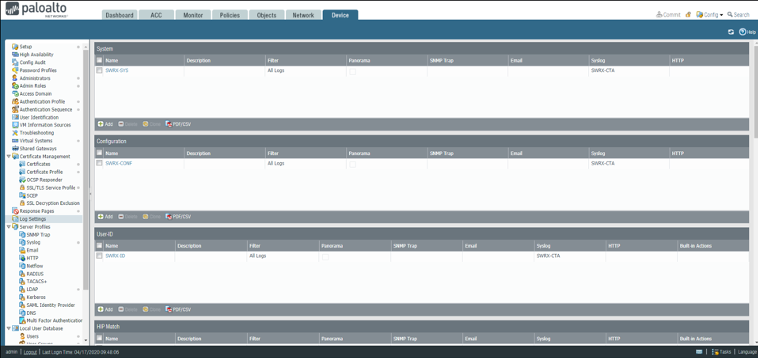
Firewall Log Settings
Note
There may be additional log types with newer versions, so ensure that you configure all of them.
Sending System (Diagnostics) Logs from the Palo Alto Firewall to XDR ⫘
- From the Device tab, select Log Settings from the left-hand tree menu.
- Under System, select Add. The Log Settings - System dialog displays.
- Enter the name as TDR-SYS.
- From the Syslog section, select TDR-COLLECTOR for the Syslog Profile.
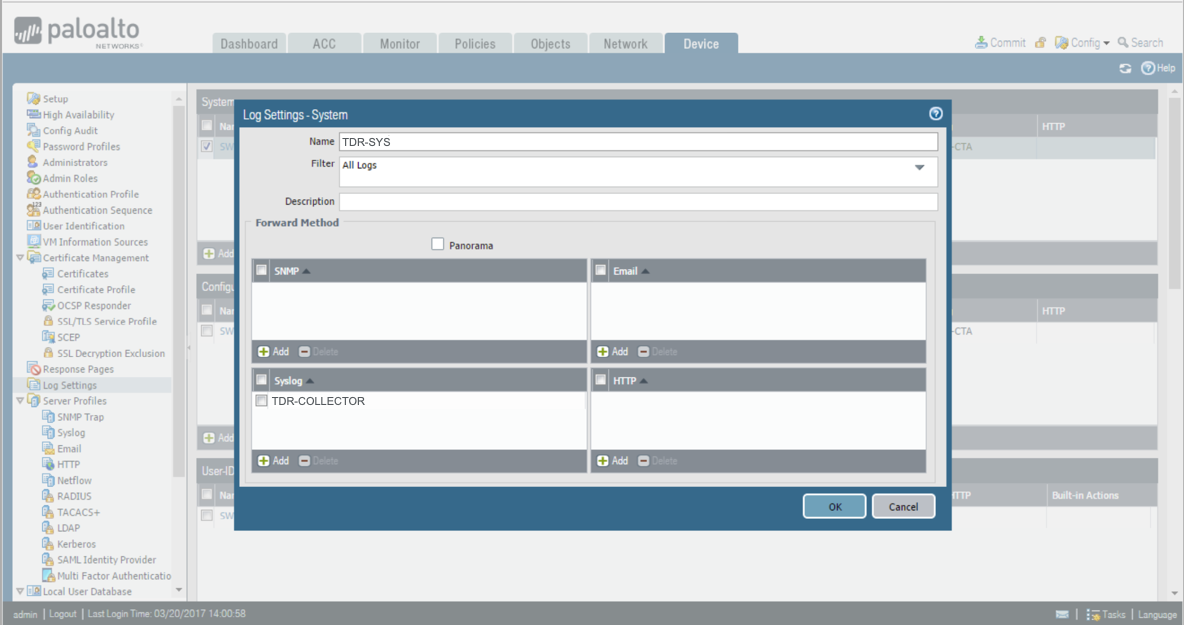
Sending System Logs
Sending Config (Audit) Logs from the Palo Alto Firewall to XDR ⫘
- From the Device tab, select Log Settings from the left-hand tree menu.
- Under Configuration, select Add. The Log Settings - Configuration dialog displays.
- Enter the name as TDR-CONF.
- From the Syslog section, select TDR-COLLECTOR for the Syslog Profile.
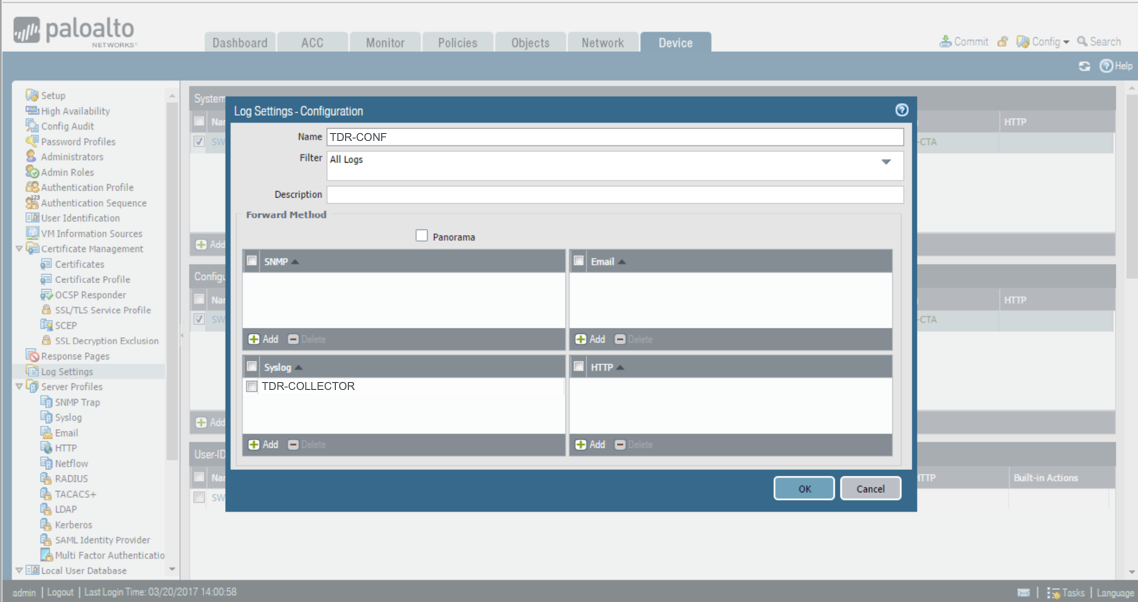
Sending Config Logs
Sending User-ID Logs from the Palo Alto Firewall to XDR ⫘
- From the Device tab, select Log Settings from the left-hand tree menu.
- Under User-ID, select Add. The Log Settings - User-ID dialog displays.
- Enter the name as TDR-ID.
- From the Syslog section, select TDR-COLLECTOR for the Syslog Profile.
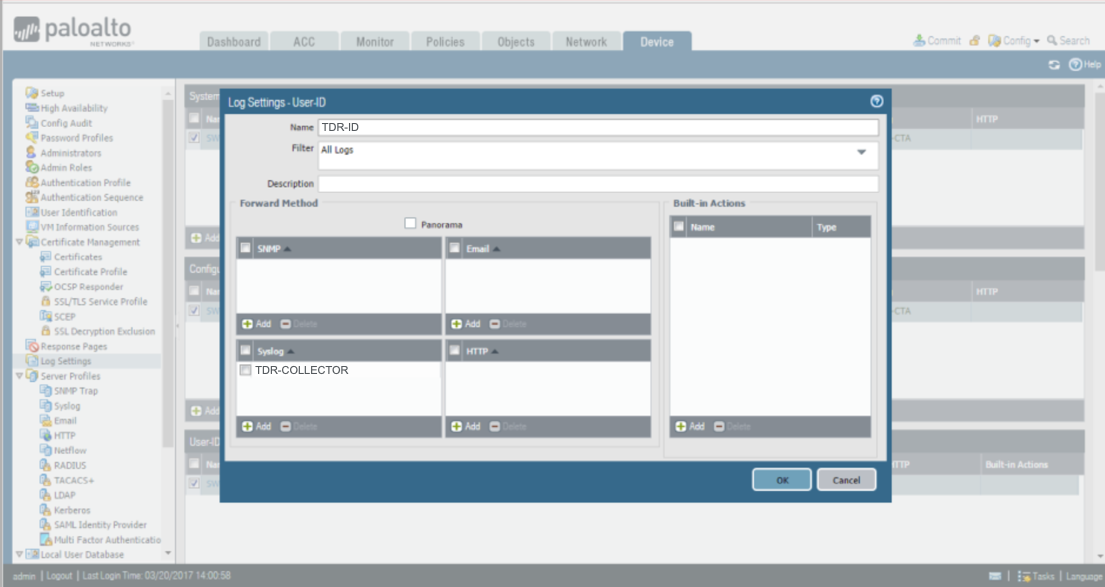
Sending User-ID Logs
Sending HIP-Match Logs from the Palo Alto Firewall to XDR ⫘
- From the Device tab, select Log Settings from the left-hand tree menu.
- Under HIP-Match, select Add. The Log Settings - HIP-Match dialog displays.
- Enter the name as TDR-HIP.
- From the Syslog section, select TDR-COLLECTOR for the Syslog Profile.
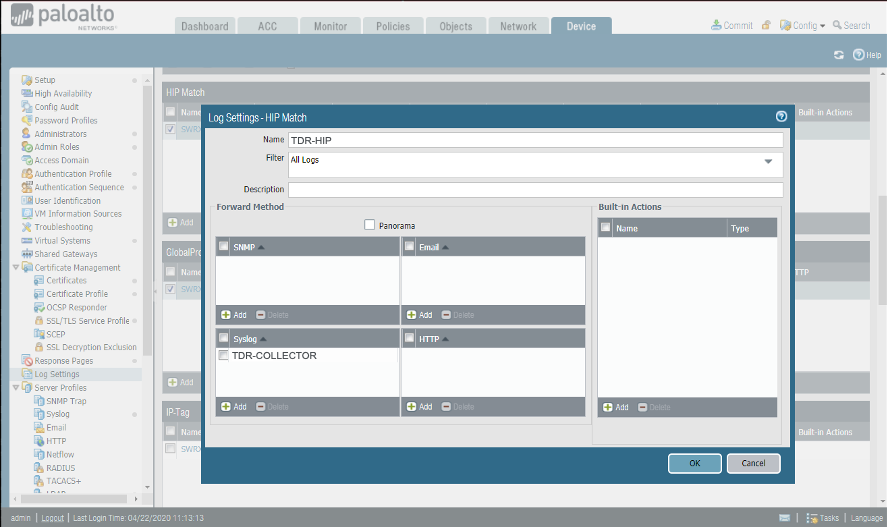
Sending HIP-Match Logs
Sending IP-Tag Logs from the Palo Alto Firewall to XDR (9.0+) ⫘
- From the Device tab, select Log Settings from the left-hand tree menu.
- Under IP-Tag, select Add. The Log Settings - IP-Tag dialog displays.
- Enter the name as TDR-IPTAG.
- From the Syslog section, select TDR-COLLECTOR for the Syslog Profile.
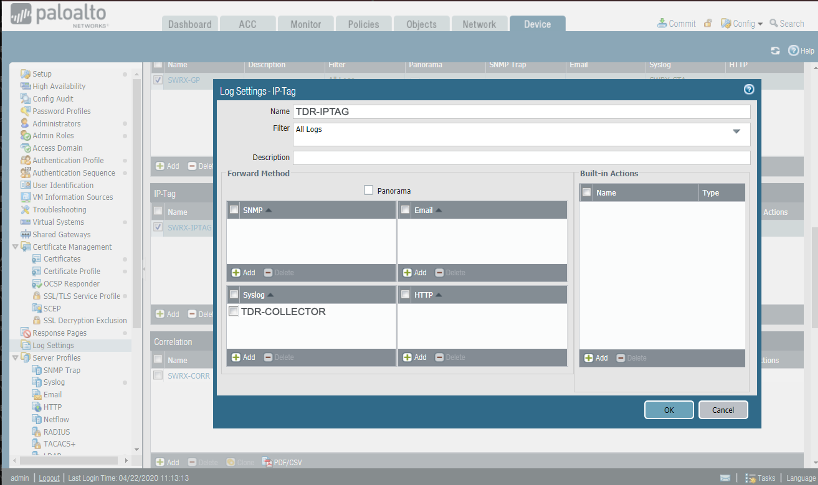
Sending IP-Tag Logs
Sending GlobalProtect Logs from the Palo Alto Firewall to XDR (9.1+) ⫘
- From the Device tab, select Log Settings from the left-hand tree menu.
- Under GlobalProtect, select Add. The Log Settings - GlobalProtect dialog displays.
- Enter the name as TDR-GP.
- From the Syslog section, select TDR-COLLECTOR for the Syslog Profile.
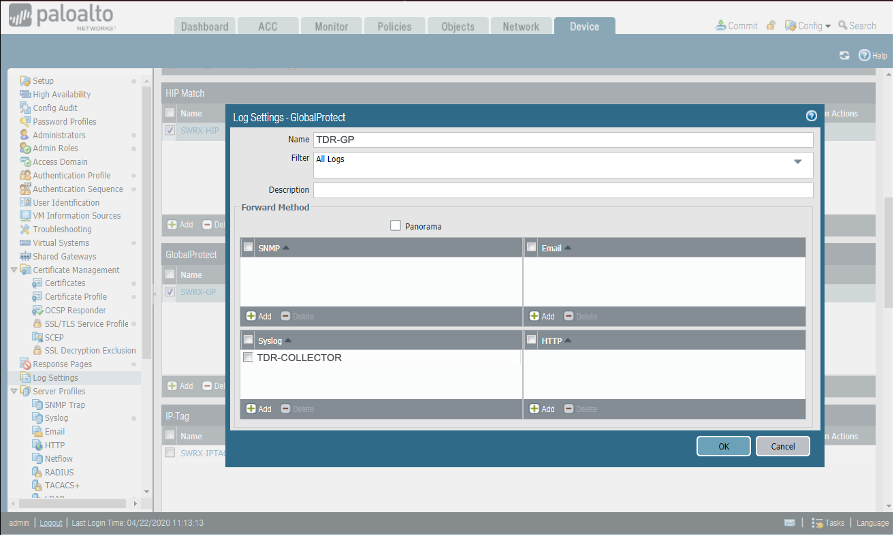
Sending GlobalProtect Logs
Sending Correlation Logs from the Palo Alto Firewall to XDR (9.1+) ⫘
- From the Device tab, select Log Settings from the left-hand tree menu.
- Under Correlation, select Add. The Log Settings - Correlation dialog displays.
- Enter the name as TDR-CORR.
- From the Syslog section, select TDR-COLLECTOR for the Syslog Profile.
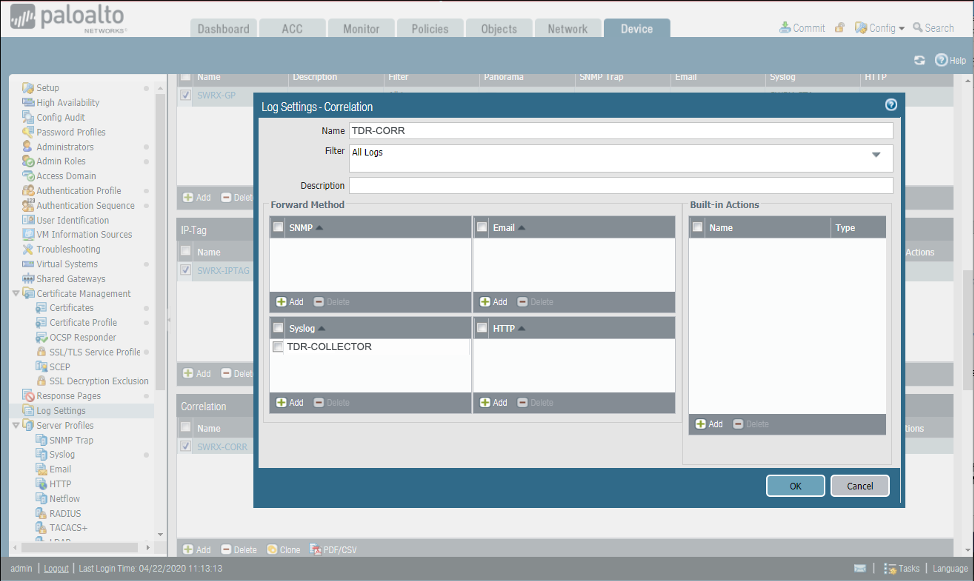
Sending Correlation Logs
Log Forwarding Profile ⫘
The Log Forwarding Profile section is used to handle session logs not handled by the Log Settings section. The Log Forwarding Profile handles Auth, Data, Threat, Traffic, Tunnel, URL, and Wildfire logs. The Log Settings section handles System, Configuration, User-ID, HIP Match, IP-Tag (9.0+), GlobalProtect (9.1+), and Correlation (9.1+) logs.
Create A Log Forwarding Profile on the Palo Alto Firewall for XDR ⫘
- From the Objects tab, select Log Forwarding from the left-hand tree menu.
- From the main panel, select Add.
- The Log Forwarding Profile dialog displays.
- Enter TDR-FORWARDING for the name.
-
Add and name the following:
- TDR-LOGFW-THREAT for threat Log Type and TDR-COLLECTOR as Syslog
- TDR-LOGFW-WF for wildfire Log Type and TDR-COLLECTOR as Syslog
- TDR-LOGFW-DATA for data Log Type and TDR-COLLECTOR as Syslog
- TDR-LOGFW-AUTH for auth Log Type and TDR-COLLECTOR as Syslog
- TDR-LOGFW-URL for url Log Type and TDR-COLLECTOR as Syslog
- TDR-LOGFW-TRAF for traffic Log Type and TDR-COLLECTOR as Syslog
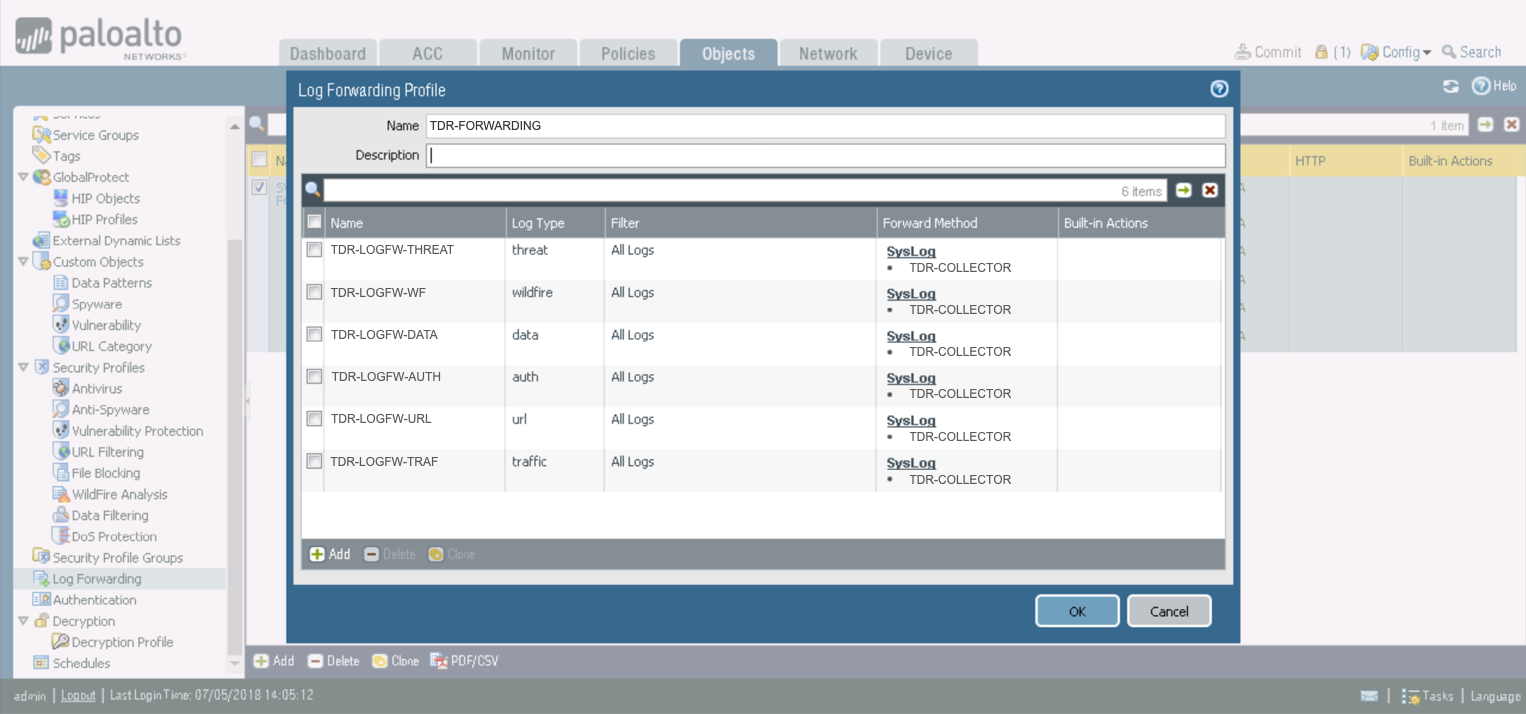
Log Forwarding
Assign the Log Forwarding Profile to Policy Rules and Network Zones on the Palo Alto Firewall for XDR ⫘
- Select Policies > Security and edit the rule.
- Select Actions and select the Log Forwarding profile you created.
- Set the Profile Type to Profiles or Group, then select the security profiles or Group Profile required to trigger log generation and forwarding for:
- Threat logs — Traffic much match any security profile assigned to the rule.
- Wildfire Submission logs — Traffic must match a WildFire Analysis profile assigned to the rule.
- For Traffic logs, select Log At Session Start and/or Log At Session End.
- Click OK to save the rule.
Panorama v8.0 - v9.0 - v9.1 Configuration ⫘
Panorama can forward logs directly to a 3rd-party syslog server. Note that Panorama can run in different modes:
- Panorama mode acts both as a management console and integrated log collector.
- Management Only mode assumes you have other external Panoramas acting as independent Log Collectors.
- Log Collector mode for the most part only receives logs, has no web-gui on itself, and is meant to be managed by a Panorama Management mode.
- Legacy mode is only supported in VMware and has no concept of Log Collectors. All log forwarding is done in the Log Settings section. This mode is the least scalable deployment mode.
Deployment mode can be found on the Dashboard tab in the General Information widget.
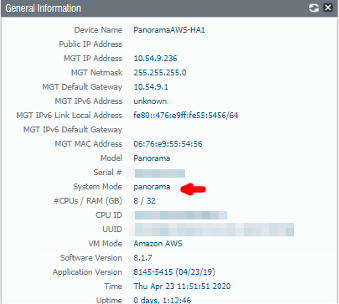
Panorama Deployment Mode
XDR Syslog Server Profile ⫘
- From the Panorama tab, select Server Profiles > Syslog from the left-hand tree menu.
- From the main panel, select Add.
- The Syslog Server Profile dialog displays.
- Name the new profile TDR-COLLECTOR-PNR.
- Select Add to add a server profile. Name it TDR-SYSLOG, and assign it the XDR Collector IP address.
- Under Facility, add the option LOG_LOCAL1.
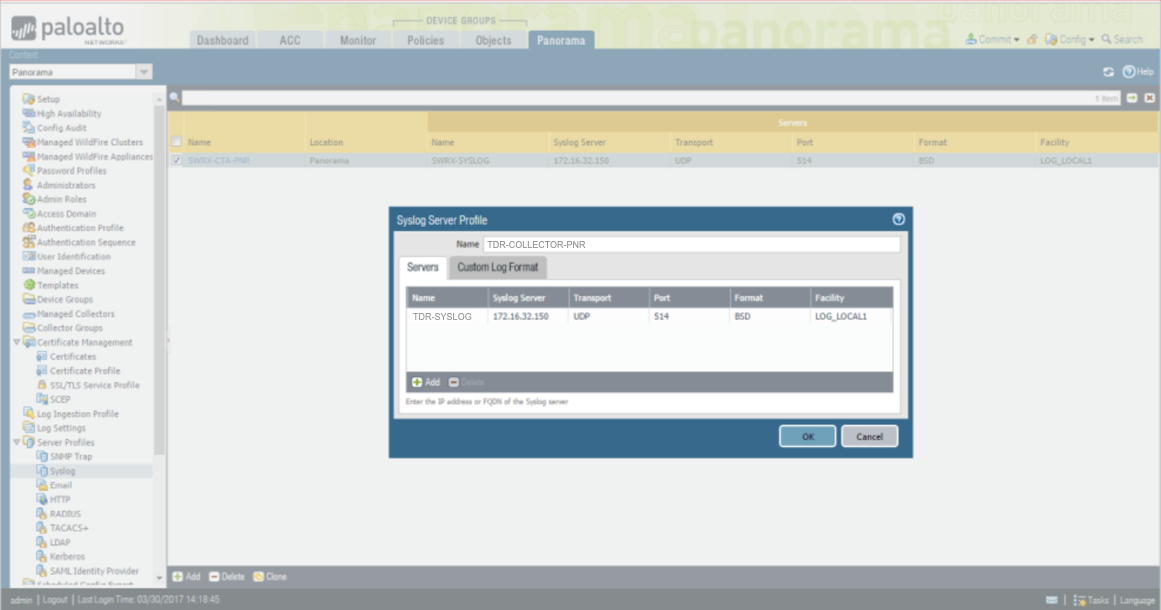
Panorama VM Syslog Server Profile
Sending Logs from Legacy Mode (VM) Panorama (w/o Log Collectors) to XDR ⫘
Important
This section is not for M-100 or higher hardware models which require more complex configurations. This particular mode is not common practice.
Note
Do not configure both Panorama and firewalls to send logs to XDR. Choose one or the other.
Configure Log Settings ⫘
- From the Panorama tab, select Log Settings from the left-hand tree menu.
-
In the main panel, Add an entry for each of the following log types and configure syslog for each using the TDR-COLLECTOR-PNR value you created in the preceding section:
- TDR-SYS for System Logs
- TDR-CONF for Config Logs
- TDR-ID for UserID Logs
- TDR-THREAT for Threat Logs (spyware/vulnerability)
- TDR-URL for URL Logs (web filtering)
- TDR-DATA for DATA Logs (DLP)
- TDR-TRAFFIC for Traffic Logs (session traffic logs)
- TDR-WF for Wildfire Logs
- TDR-TUN for Tunnel Logs (VPN)
- TDR-AUTH for Authentication Logs
- TDR-CORR for Correlation Logs
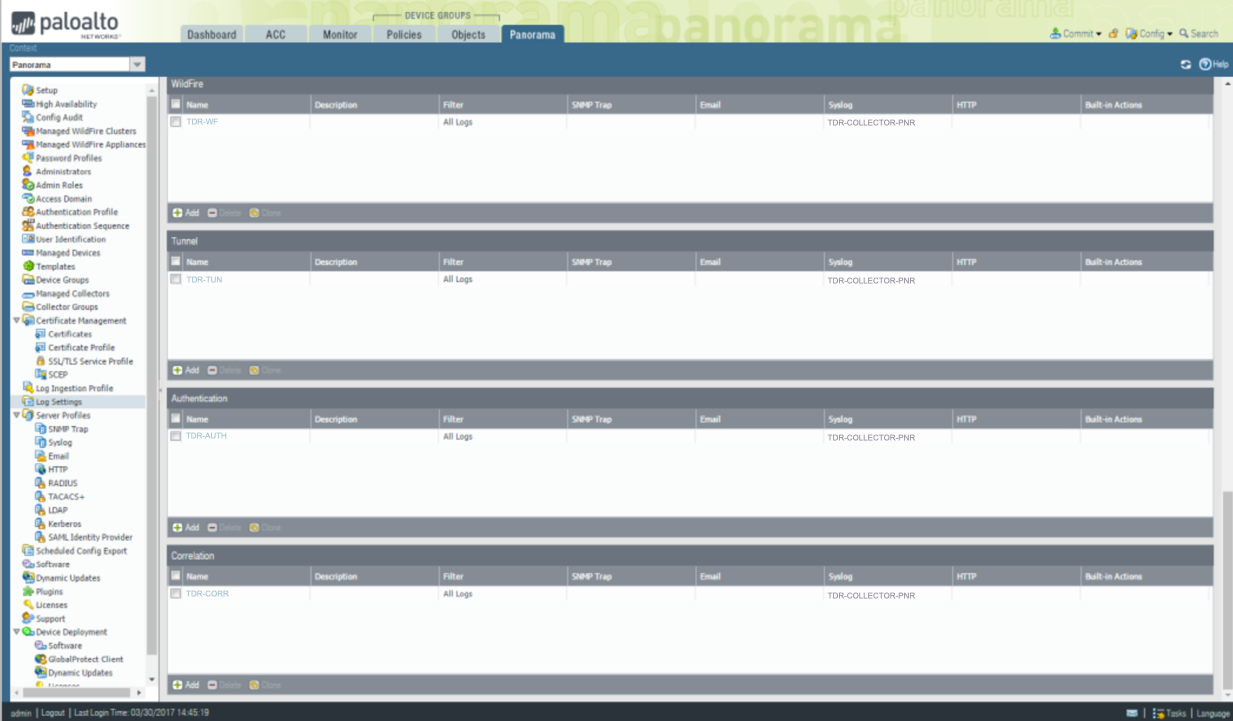
Panorama VM Log Settings
Note
There may be additional log types with newer versions, so ensure that you configure all of them.
Sending Logs from Panorama (VM Or M) To XDR with Managed Collectors ⫘
Panorama M Hardware Models and VM with Managed Collectors (Mgmt Only/Panorama Modes) ⫘
Important
For distributed log collection, the device log forwarding configuration in Panorama is no longer done under Log Settings but instead under Collector Groups → Collector Log Forwarding.
Note
Do not configure both Panorama and firewalls to send logs to XDR. Choose one or the other.
The following is a simplified diagram of a distributed log collecting architecture.
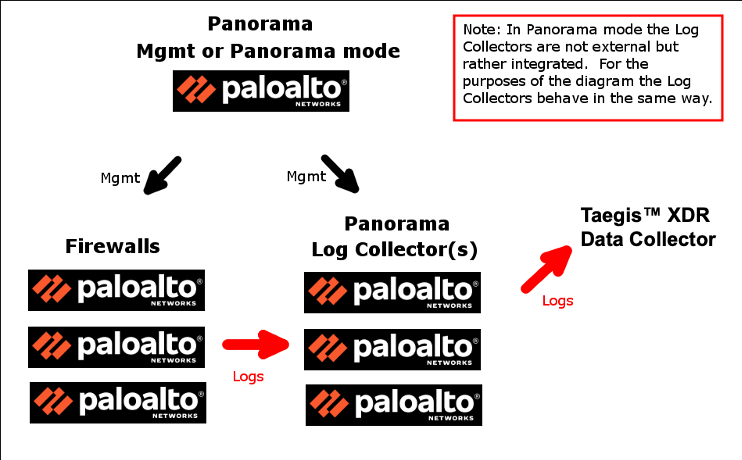
Panorama Managed Collectors
Configure Log Settings - Log Collector Group ⫘
- From the Panorama tab, select Collector Groups from the left-hand tree menu.
- Edit the customer existing collector group(s) in-scope to be monitored. There might only be one Collector Group called default, which means the M hardware is running in Panorama mode.
- Select the desired Collector Group, then select the Collector Log Forwarding tab.
-
Create an entry under each log type for each of the following to send syslog to the TDR-COLLECTOR-PNR you created earlier. Configure it as follows:
- TDR-SYS for System Logs
- TDR-CONF for Config Logs
- TDR-ID for UserID Logs
- TDR-THREAT for Threat Logs (spyware/vulnerability)
- TDR-URL for URL Logs (web filtering)
- TDR-DATA for DATA Logs (DLP)
- TDR-TRAFFIC for Traffic Logs (session traffic logs)
- TDR-WF for Wildfire Logs
- TDR-TUN for Tunnel Logs (VPN)
- TDR-CORR for Correlation Logs
- TDR-AUTH for Authentication Logs
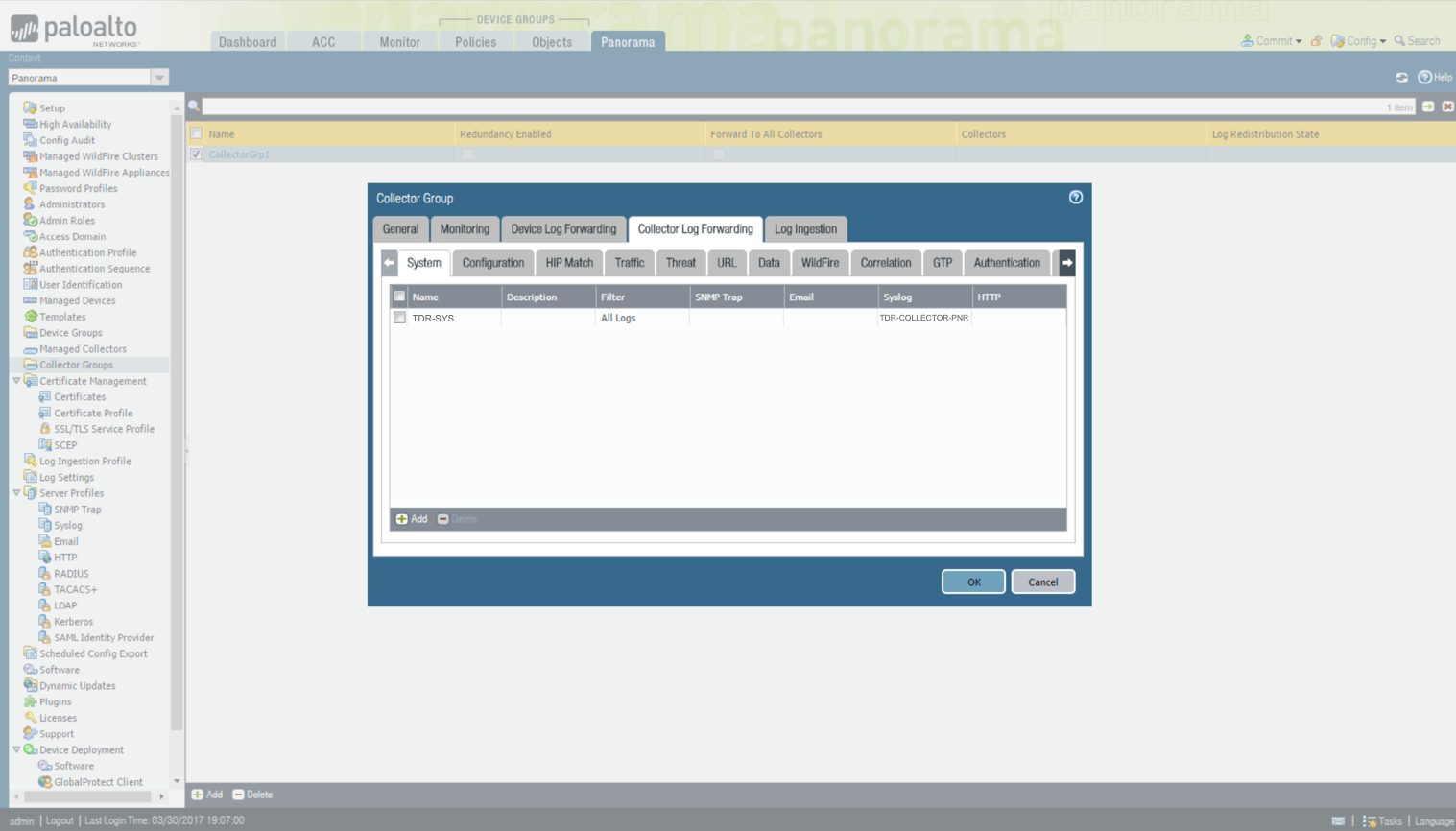
Collector Log Forwarding
Note
There may be additional log types with newer versions, so ensure that you configure all of them.
Update Existing Security Rules (Firewall Rules) All Versions ⫘
Apply Security Profiles—UTM/NGFW Features—And Enable Log Forwarding ⫘
Security Profiles are useless unless they are applied to security rules. Furthermore, security rules do not forward logs unless there is a Log Forwarding Profile associated with it. Define a security policy rule:
- From the Policies tab, select Security from the left-hand tree menu.
- Select each security rule to open the Security Policy dialog for that rule.
- Go to the Actions tab.
- For Profile Type, select Profiles.
- Select the corresponding Antivirus, Vulnerability Protection, Anti-Spyware, URL Filtering, File Blocking, Data Filtering and Wildfire Analysis (PANOS 7.1 and above) security profiles you use in your environment.
- Make sure the Log Forwarding has TDR-FORWARDING selected.
Note
In the Log Setting section of the Action tab, it is a PAN best practice to only enable Log at Session End. If you need to enable Log at Session Start for troubleshooting purposes, it is recommended to disable it after you’re done troubleshooting
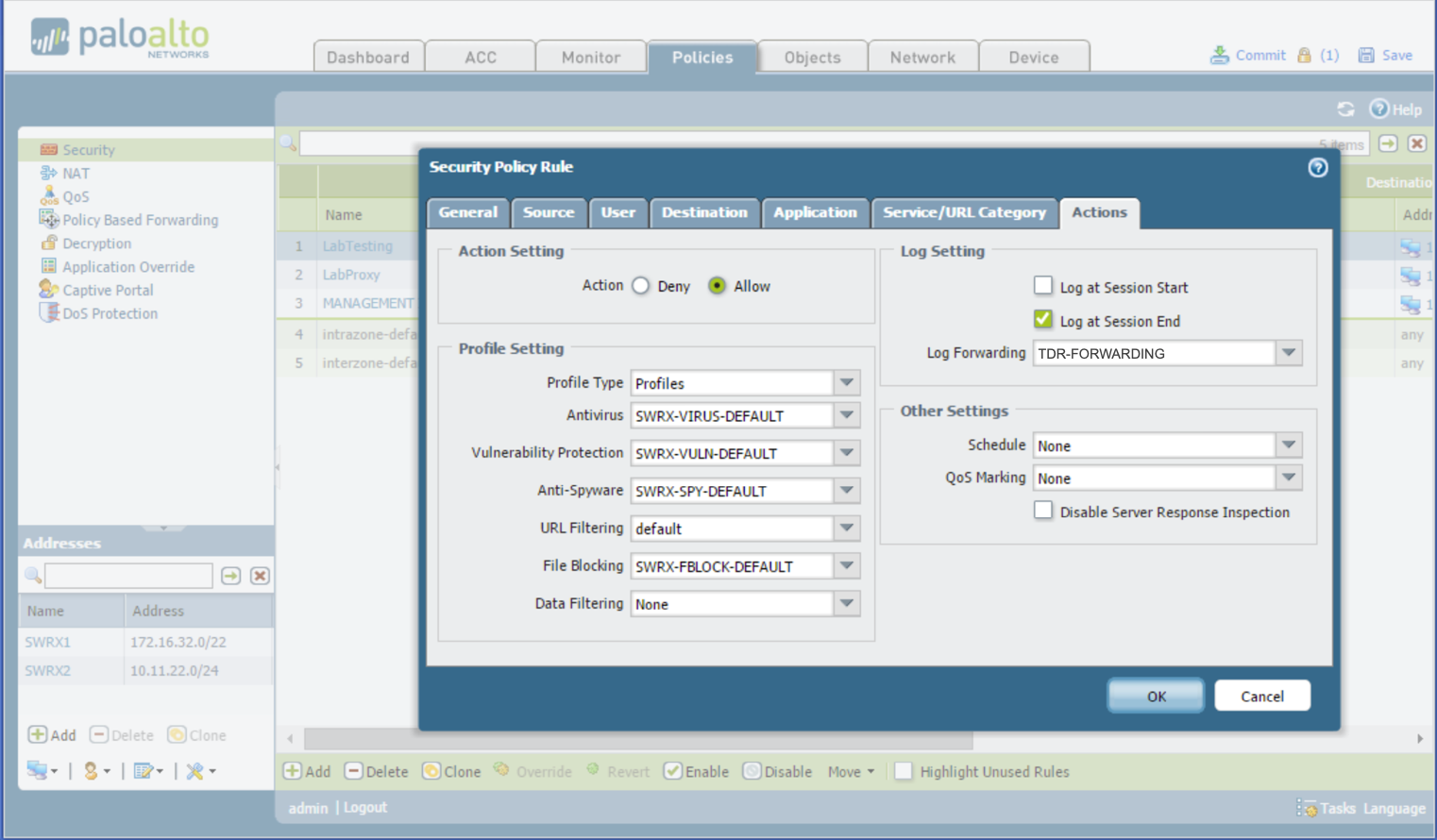
Security Policy Rule
Palo Alto Firewall v6.1 - 7.0 - 7.1 Configuration (End of Life) ⫘
The following covers multiple configuration scenarios for Palo Alto Firewall to XDR. Select the one appropriate to your version of Palo Alto.
Sending Logs from Palo Alto Firewall to XDR Only ⫘
Note
Do not configure both Panorama and Palo Alto Firewall to send logs to XDR. Choose one or the other.
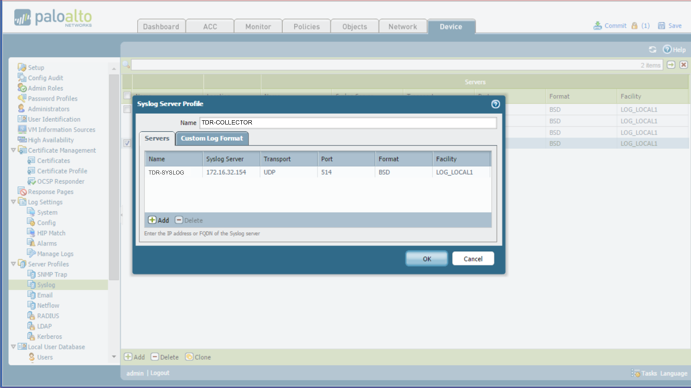
Create a XDR Syslog Server Profile ⫘
This creates a named syslog object that is used in later steps for forwarding syslog events to XDR.
- Navigate to the Device tab, then on the left pane under Server Profiles select Syslog.
- Name it TDR-COLLECTOR and add an entry named TDR-SYSLOG with the XDR Collector IP address.
- Under Facility, select the option LOG_LOCAL1.
XDR Syslog Server Profile
Sending System (Diagnostic) Logs from Palo Alto Firewall to XDR ⫘
System logs provide a wide array of useful information for auditing and troubleshooting (user login information, NTP issues, hardware events, user-id events, etc.).
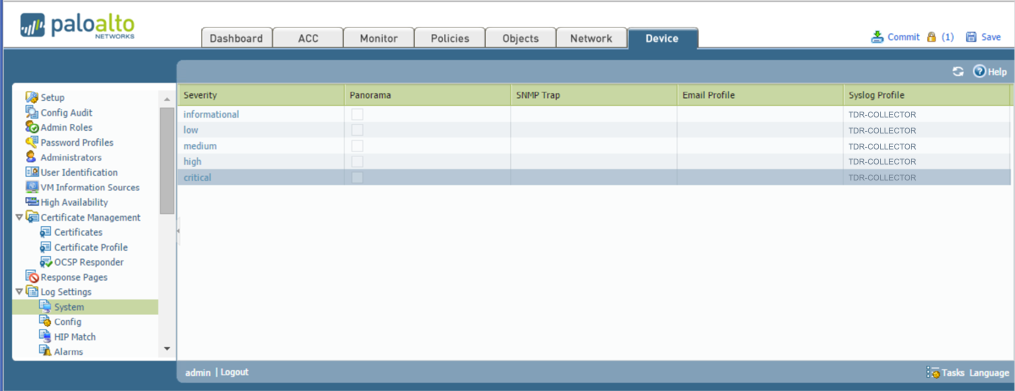
PANOS 6.1 and Below ⫘
- Under the Device tab, select Log Settings > System from the left-hand tree menu.
- In the main panel, select each severity level and select TDR-COLLECTOR for the Syslog Profile.
Device Tab, System Log Settings
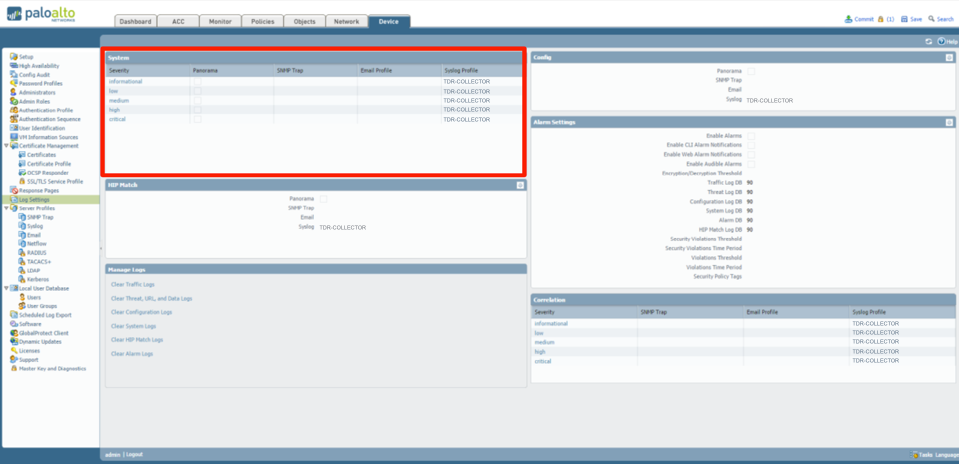
PANOS 7.0 and 7.1 ⫘
On PANOS versions above 7.0 Config, System, and Correlation events are all on one screen.
- Under the Device tab, select Log Settings from the left-hand tree menu.
- In the main panel, select TDR-COLLECTOR for the System widget.
Device Tab, System Log Settings
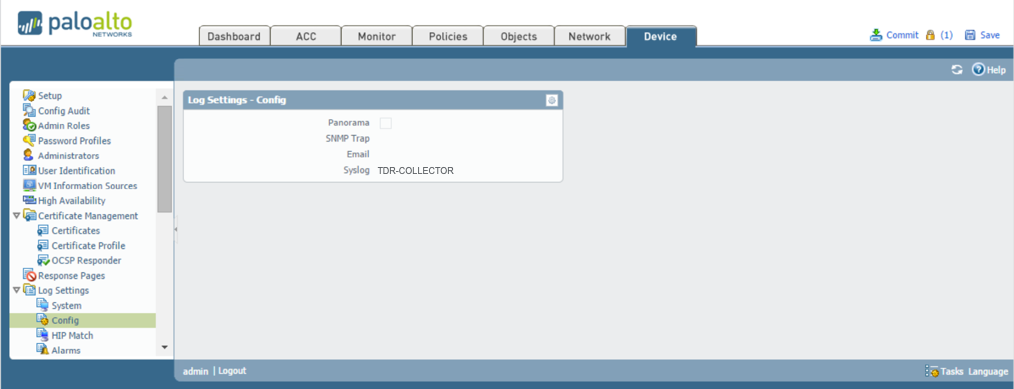
Sending Config (audit) Logs from Palo Alto Firewall to XDR ⫘
Configuration logs provide information on who and what changes have been made on a PAN FW. These are useful for backtracking configuration mistakes and/or possible unauthorized changes compromising the security of the device/network.
PANOS 6.1 and below ⫘
- Under the Device tab, select Log Settings --> Config from the left-hand menu.
- In the main panel, select TDR-COLLECTOR for the Syslog Profile.
Panos 6.1 and Below Config
PANOS 7.0 and 7.1 ⫘
On PANOS versions above 7.0, the Config, System, and Correlation events are all on one screen.
- From the Device tab, select Log Settings from the left-hand menu.
- In the main panel, select TDR-COLLECTOR for the Config widget.
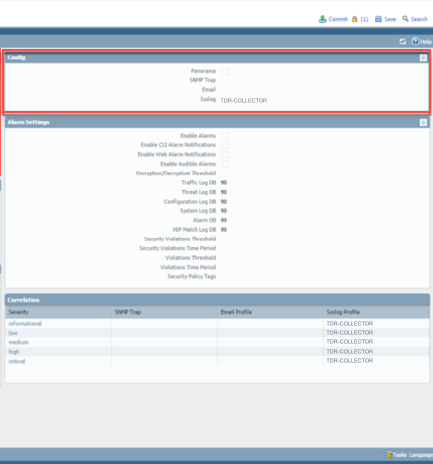
Panos 7 Config
Sending Correlation (Security) Logs From the Palo Alto Firewall to XDR (PANOS 7.0+) ⫘
PANOS 7.0 and above now contains a new type of security event called Correlation events, which are vendor proprietary meta-events made up of the correlation of multiple threat events. These new security events are valuable in detecting infected hosts. On PANOS versions above 7.0 Config, System, and Correlation events are all on one screen.
- Under the Device tab, select Log Settings.
- From the main panel, select TDR-COLLECTOR for the Correlation widget.
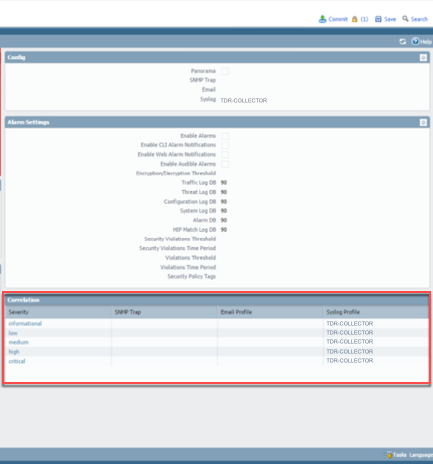
Correlation Logs
Create a Log Forwarding Profile on the Palo Alto Firewall for Logging to XDR Only ⫘
This creates a named profile that specifies the only events (traffic, security/vulnerability, wildfire) and criticality levels that are be forwarded to XDR by referencing the syslog server profile.
- Under the Objects tab, select Log Forwarding.
- In the main panel, select Add. The Log Forwarding Profile dialog displays.
- Enter TDR-FORWARDING for the name.
- Select TDR-COLLECTOR for every item under Syslog column.
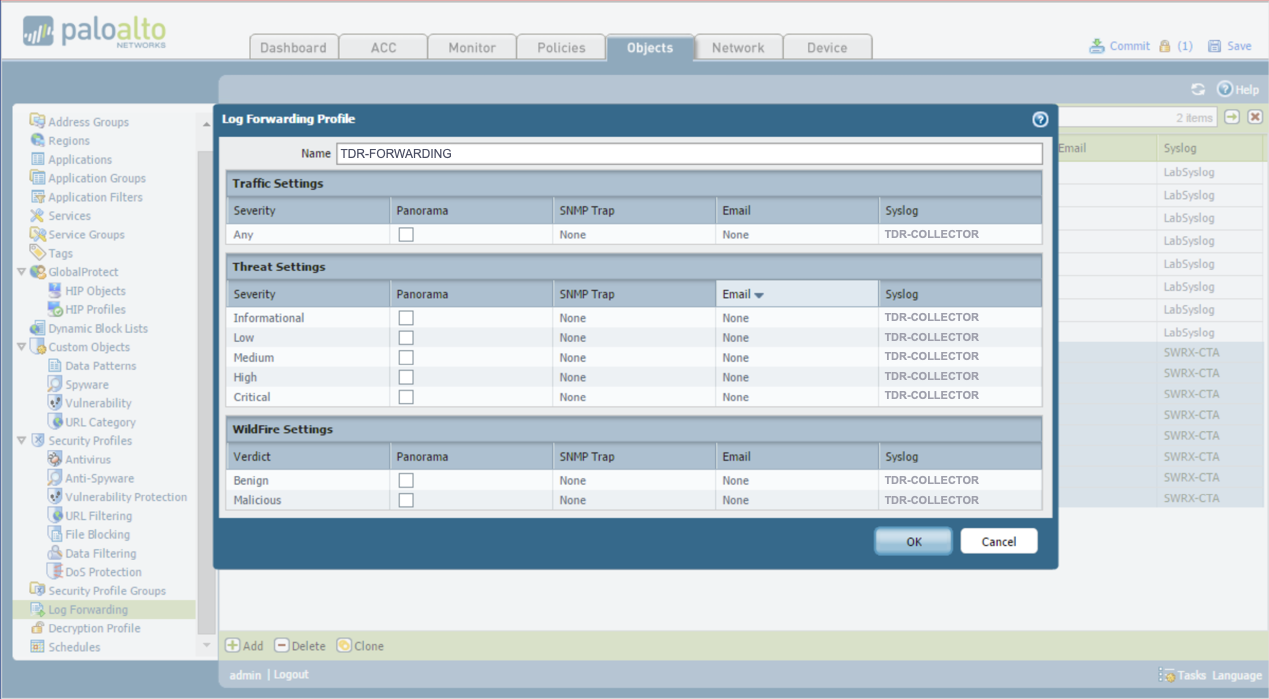
Log Forwarding Profile
Panorama v6.1 - 7.1 Configuration (End of Life) ⫘
The following covers multiple configuration scenarios for Panorama to XDR. Select the one appropriate to your version of Panorama.
Sending Logs from Customer Panorama to XDR ⫘
Note
Do not configure both Panorama and Palo Alto Firewall to send logs to XDR. Choose one or the other.
XDR Syslog Server Profile ⫘
In Panorama, create a Server Syslog Profile called TDR-COLLECTOR with XDR Collector’s corresponding IP address.
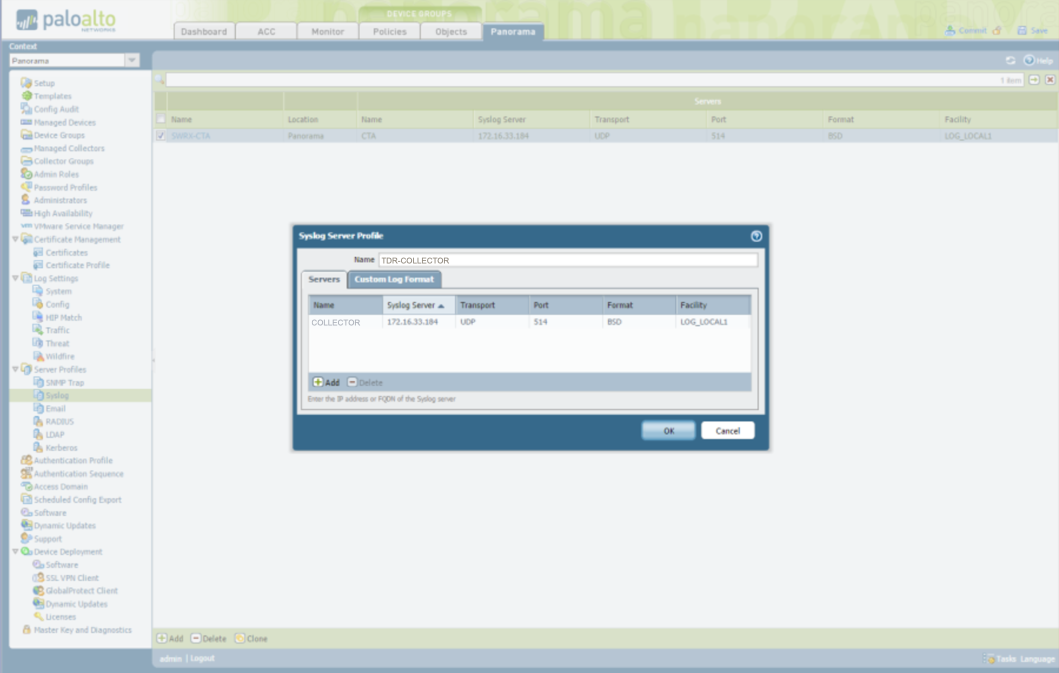
Panorama Syslog Server Profile
Sending System (Diagnostics) Logs From Panorama To XDR ⫘
System logs provide a wide array of useful information for auditing and troubleshooting (user login information, NTP issues, hardware events, user-id events, etc.).
PANOS 6.1 and Below ⫘
Configure the System Log Settings to point to the TDR-COLLECTOR syslog server profile.
- From the Panorama tab, select Log Settings → System from the left-hand tree menu.
- Select TDR-COLLECTOR for every item under the Syslog Profile column.
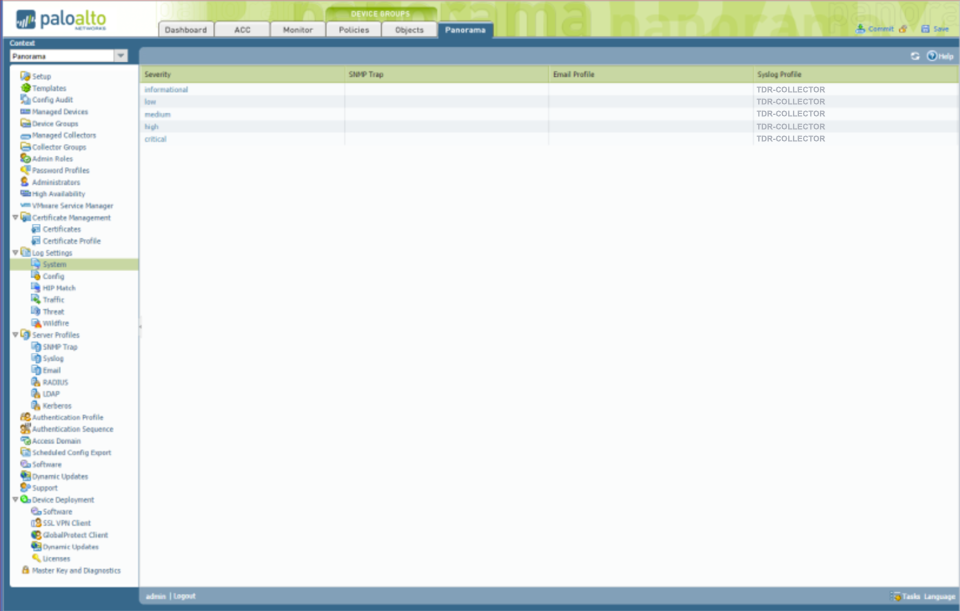
Panorama System Logs
PANOS 7.0 and 7.1 ⫘
On PANOS versions above 7.0 Panorama, Config, System, Threat, Wildfire, Traffic, and Correlation events are all on one screen.
- From the Device tab, select Log Settings from the left-hand tree menu.
- Select TDR-COLLECTOR for the System widget in the main panel.
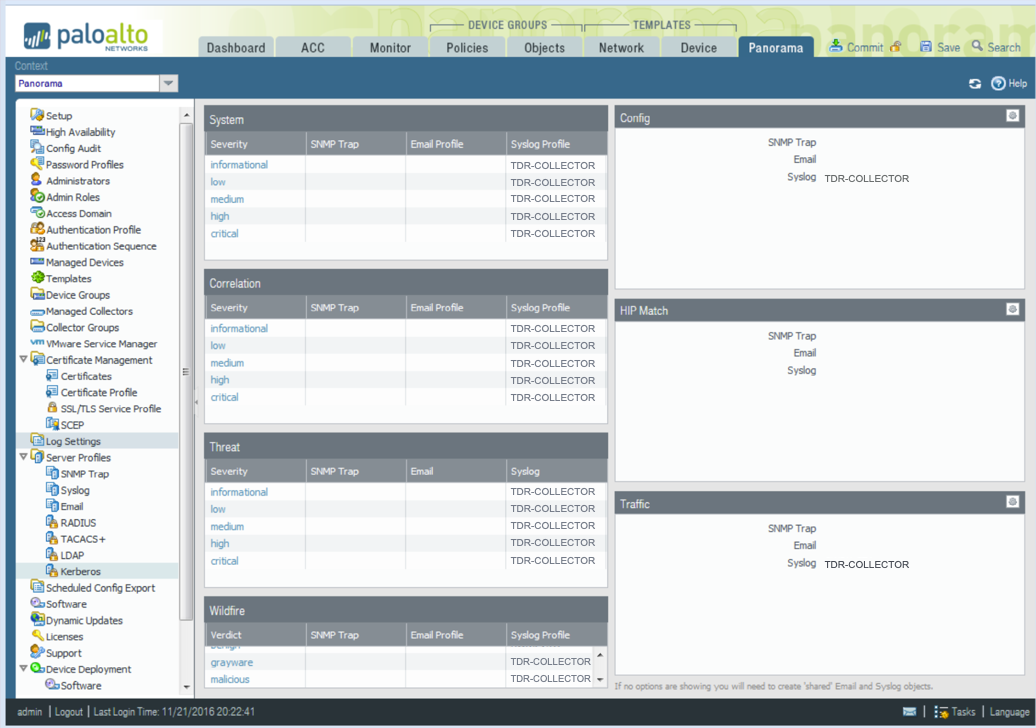
Panorama System Logs
Sending Config (Audit) Logs From Panorama To XDR ⫘
Config logs provide information on who and what changes were made on a Panorama Firewall. These are useful for backtracking configuration mistakes and/or possible unauthorized changes compromising the security of the device/network.
PANOS 6.1 and Below ⫘
- From the Panorama tab, select Log Settings → Config from the left-hand tree menu.
- In the main panel, make sure the Log Settings - Config is pointing to TDR-COLLECTOR for syslog.
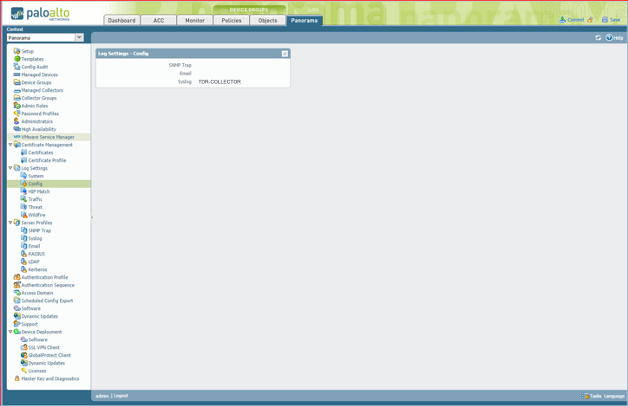
Panorama Config Logs
PANOS 7.0 and 7.1 ⫘
On PANOS versions above 7.0 Panorama, Config, System, Threat, Wildfire, Traffic, and Correlation events are all on one screen.
- From the Device tab, select Log Settings from the left-hand tree menu.
- Select TDR-COLLECTOR for the Config widget in the main panel.

Panorama Config Logs
Sending Traffic Logs from Panorama to XDR ⫘
Traffic logs provide additional information used for event correlation and/or network forensics. For example, suspicious outbound traffic to watchlisted IP networks/hosts.
PANOS 6.1 and Below ⫘
- From the Panorama tab, select Log Settings → Traffic.
- In the main panel, configure the Traffic Settings to point to the TDR-COLLECTOR syslog server profile.
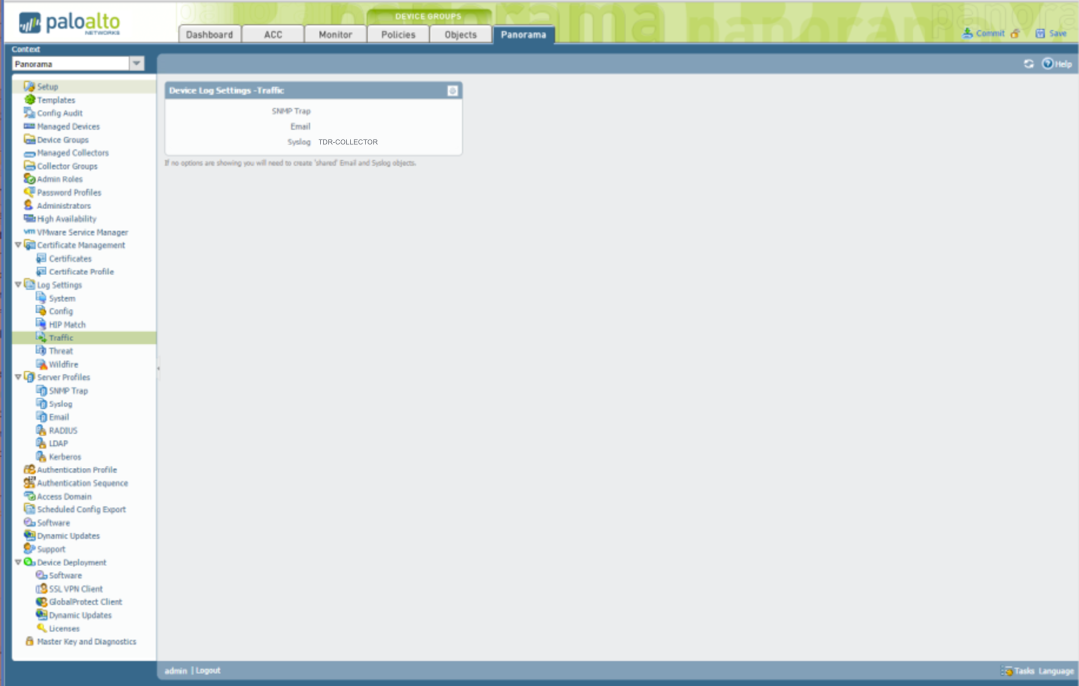
Panorama Traffic
PANOS 7.0 and 7.1 ⫘
On PANOS versions above 7.0 Panorama Config, System, Threat, Wildfire, Traffic, and Correlation events are all on one screen.
- From the Panorama tab, select Log Settings from the left-hand tree menu.
- From the main panel select TDR-COLLECTOR for the Traffic widget.

Panorama Traffic Logs
Sending Threat (Security) Logs from Panorama to XDR ⫘
Threat logs provide security events on malicious activity detected by the PAN device. Examples of this are remote exploits, intrusion attempts, and denial of service attacks.
PANOS 6.1 and Below ⫘
-
From the Panorama tab, select Log Settings → Threat from the left-hand tree menu.
-
In the main panel, configure the Threat settings to point to the TDR-COLLECTOR syslog server profile.
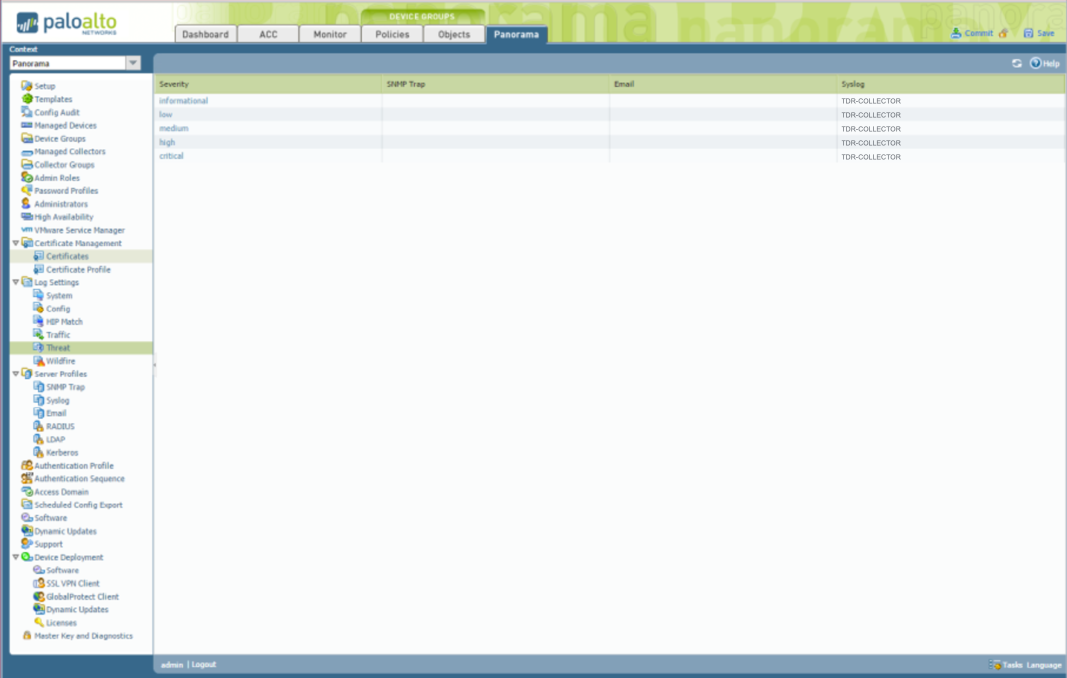
Panorama Threat Logs
PANOS 7.0 and 7.1 ⫘
On PANOS versions above 7.0 Panorama Config, System, Threat, Wildfire, Traffic, and Correlation events are all on one screen.
-
From the Panorama tab, select Log Settings from the left-hand tree menu.
-
In the main panel, select TDR-COLLECTOR for the Threat widget.

Panorama Threat Logs
Sending Correlation (Security) Logs From Panorama To XDR - PANOS 7 ⫘
PANOS 7.0 and above now contains a new type of security event called Correlation events, which are vendor proprietary meta-events made up of the correlation of multiple threat events. These new security events are valuable in detecting infected hosts.
PANOS 7.0 and 7.1 ⫘
On PANOS versions above 7.0 Panorama Config, System, Threat, Wildfire, Traffic, and Correlation event log configurations are all on one screen.
-
From the Panorama tab, select Log Settings from the left-hand tree menu.
-
From the main panel, select TDR-COLLECTOR for items in the Syslog Profile column of the Correlation widget.

Panorama Correlation Logs
Sending Wildfire (Security) Logs from Panorama to XDR ⫘
Wildfire security events are for the most part either sandboxing analysis results of suspicious files or wildfire virus (wildfire signatures) alerts. These are useful to detect relatively new malware via instantaneous sandboxing or via the wildfire signatures created from the malware samples sent from the wildfire community.
PANOS 7.0 and 7.1 ⫘
On PANOS versions above 7.0 Panorama you can now send Wildfire events from Panorama. Additionally, all Config, System, Threat, Wildfire, Traffic, and Correlation event log configuration are all on one screen.
-
From the Panorama tab, select Log Settings from the left-hand tree menu.
-
From the main panel, select TDR-COLLECTOR for items in the Syslog Profile column of the Wildfire widget.

Panorama Wildfire Logs
