Suspicious DNS Activity
The Suspicious DNS Activity detectors identify attempts by threat actors to steal data by exfiltration over existing command and control channels. This detector monitors DNS activity for sequences and patterns indicative of possible DNS exfiltration or C2 communication over DNS to an attacker machine from a compromised host.
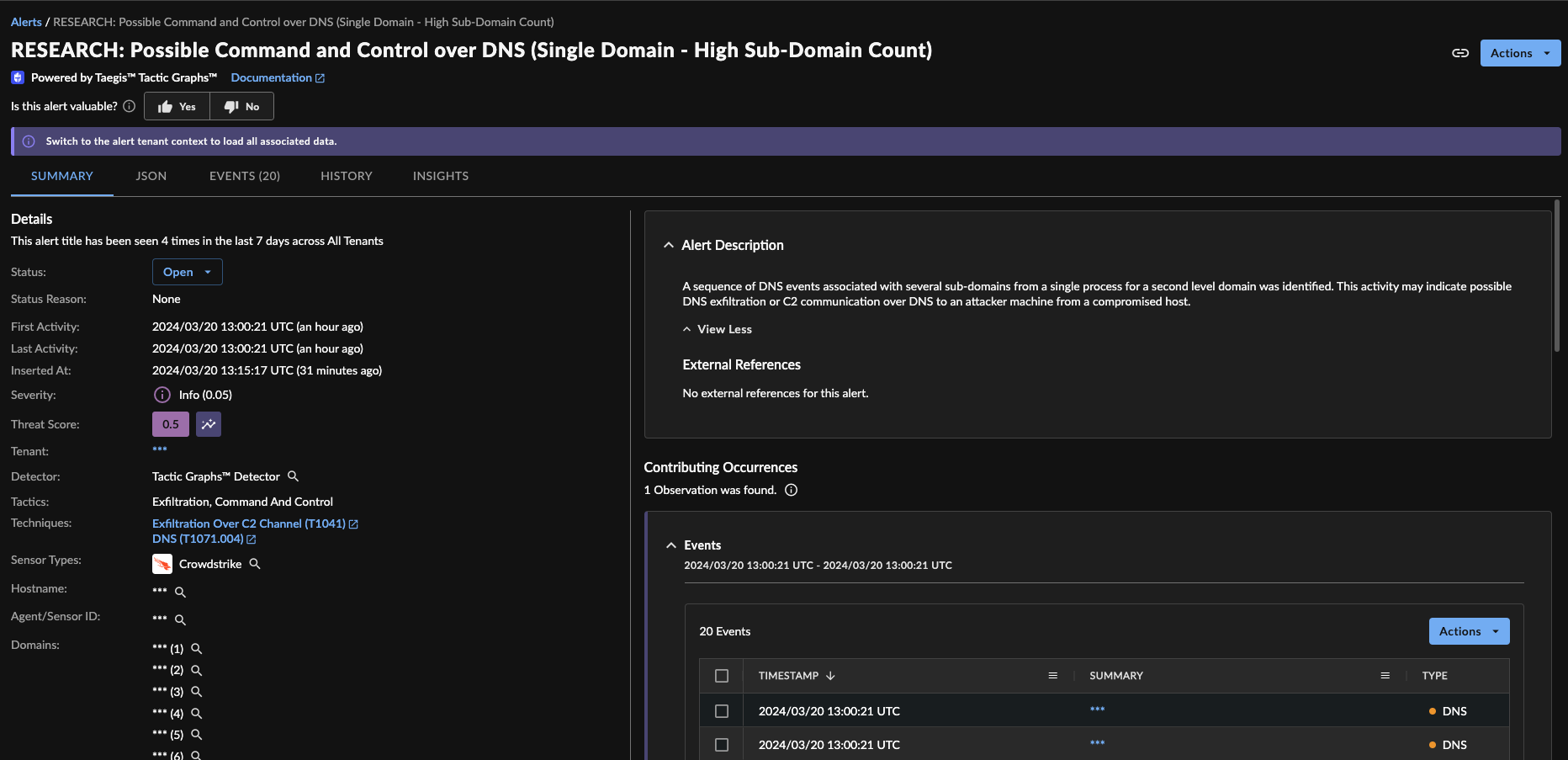
Suspicious DNS Activity Alert
Schema ⫘
DNS
Outputs ⫘
Alerts generated by Tactic Graphs™ Detector are pushed to the Secureworks® Taegis™ XDR Alert Triage Dashboard.
MITRE ATT&CK Category ⫘
- MITRE Enterprise ATT&CK - Exfiltration - Exfiltration Over C2 Channel. For more information, see MITRE Technique T1041.
- MITRE Enterprise ATT&CK - Command and Control - Application Layer Protocol: DNS. For more information, see MITRE Technique T1071.004.
