Google Cloud Platform Integration Guide
The following instructions are for configuring an integration of Google Cloud Platform (GCP) to facilitate log ingestion into Secureworks® Taegis™ XDR. XDR receives logs from GCP via the Pub/Sub messaging service.
Supported Google Cloud Platform Log Types ⫘
-
- Admin Activity
- Data Access
- System Event
- Policy Denied
- GKE Dataplane V2
- Security Command Center Findings
Before You Begin ⫘
Ensure the following prerequisites are met before proceeding:
- An active Google Cloud account with an administrator role
- A Google Cloud Project
Important
This guide assumes these prerequisite steps are complete before beginning setup.
Data Provided from Integrations ⫘
| Antivirus | Auth | CloudAudit | DHCP | DNS | Encrypt | HTTP | Management | Netflow | NIDS | Thirdparty | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Google Cloud Platform | Y | D | V |
Y = Normalized | D = Out-of-the-Box Detections | V = Vendor-Specific Detections
Note
XDR detectors are not guaranteed to be triggered, even if a data source's logs are normalized to a schema associated with a given detector. However, you can create Custom Alert Rules to generate alerts based on normalized data from a data source.
Configure Log Forwarding Using the GCP Web Interface ⫘
Create Pub/Sub Topic ⫘
- Navigate to Pub/Sub > Topics and select Create Topic.
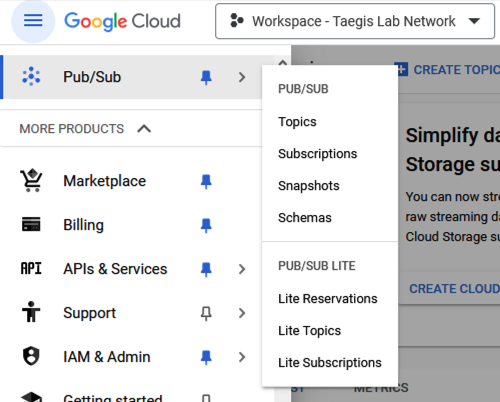
Create Pub/Sub Topic
- Enter a Topic ID, then select Create.
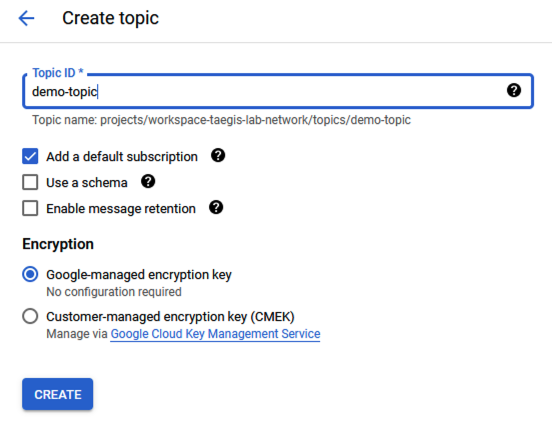
Enter Pub/Sub Topic ID
Create Pub/Sub Subscription ⫘
- Navigate to Pub/Sub > Subscriptions and select Create Subscription.
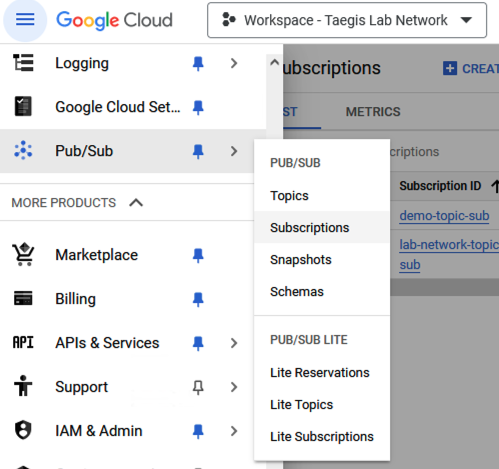
Create Pub/Sub Subscription
- Enter a Subscription ID and select the topic created in Step 2.
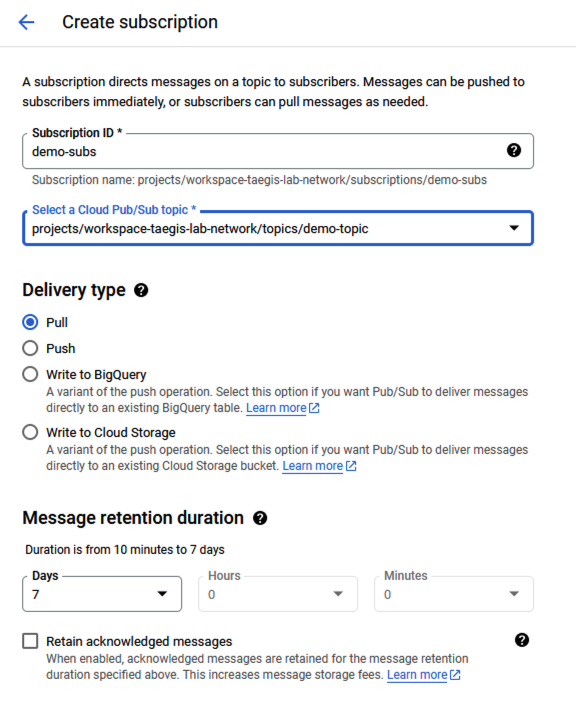
Enter Pub/Sub Subscription ID
- Set the Acknowledgement deadline to 300 seconds and select Create.
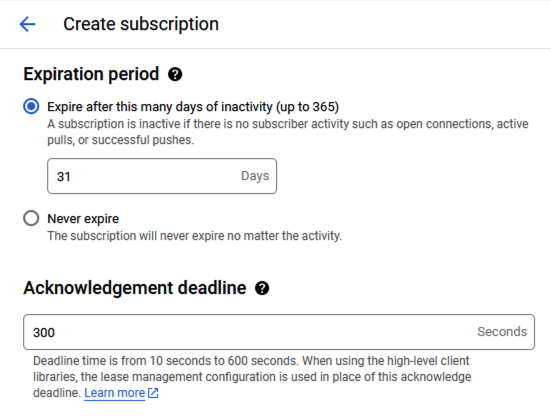
Enter Pub/Sub Subscription Acknowledgement Deadline
Create Sink ⫘
- Navigate to Logging > Log router and select Create Sink.
Create Sink
- From Sink details, enter a Sink name and description, then select Next.
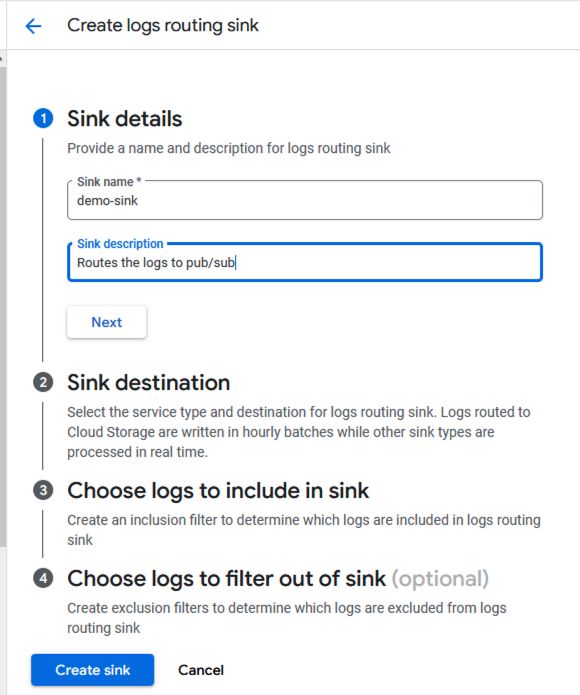
Add Sink Details
- From Sink destination, select Cloud Pub/Sub topic as the sink service, then select the Pub/Sub topic created in Step 2.
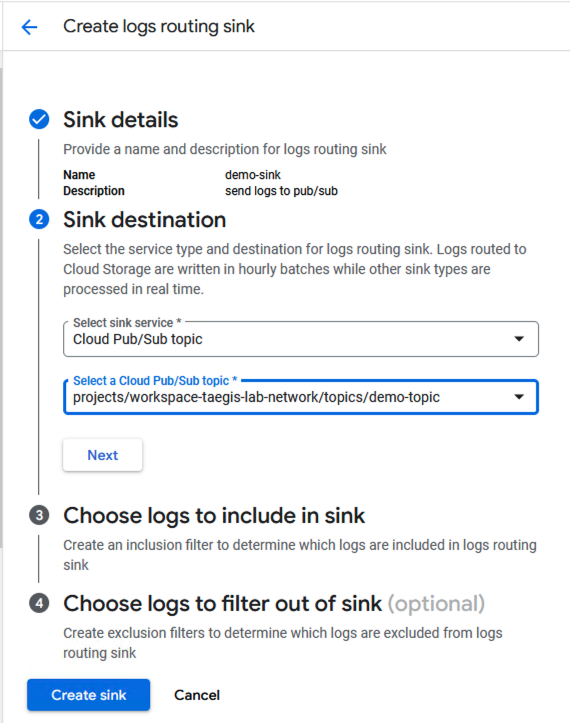
Select Sink Service Type and Pub/Sub Topic
Note
See Select Logs to Send to XDR to create inclusion filters that determine which logs are sent to the sink.
- Select Create sink.
Create a Service Account with Permissions to Read from the Pub/Sub Topic ⫘
- Navigate to IAM & Admin > Service Accounts and select Create Service Account.
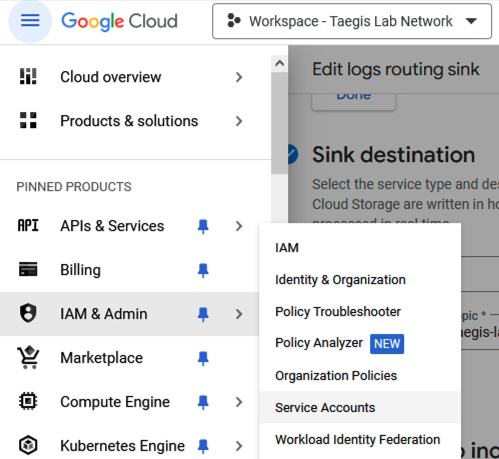
Create a Service Account
- Enter a Service account name and description. Copy the Service account ID email address for use in a subsequent step and select Done.
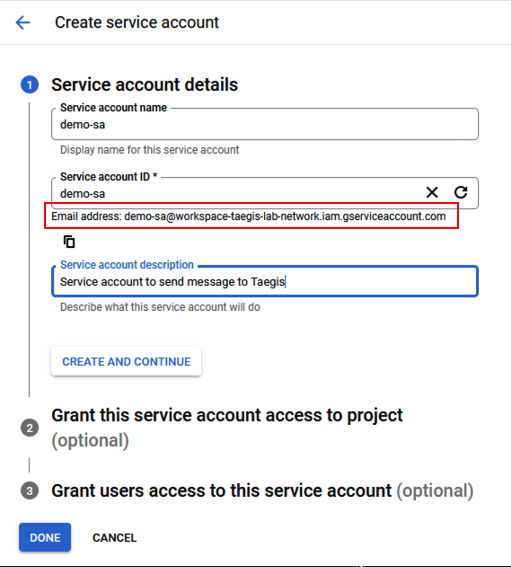
Enter Service Account Details
- Navigate to Pub/Sub > Subscriptions and select Edit for the subscription created in Step 5.
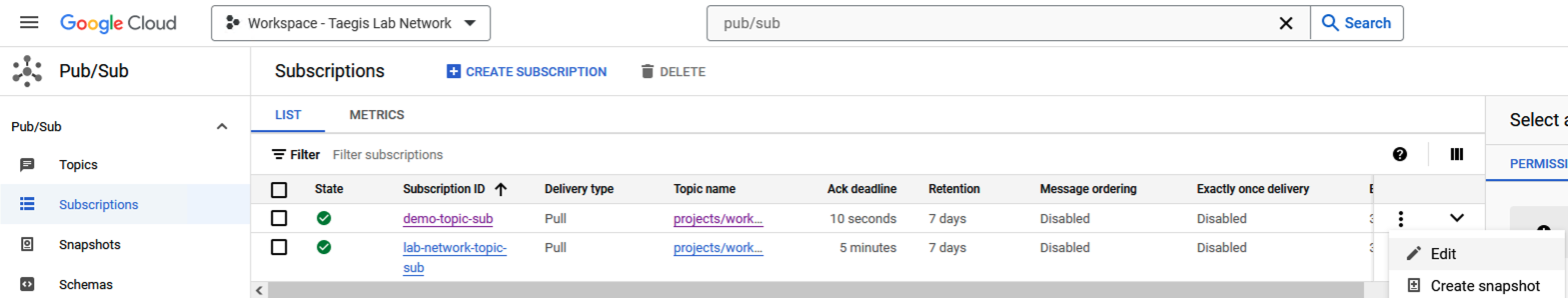
Edit Pub/Sub Subscription
- Select Add Principal.
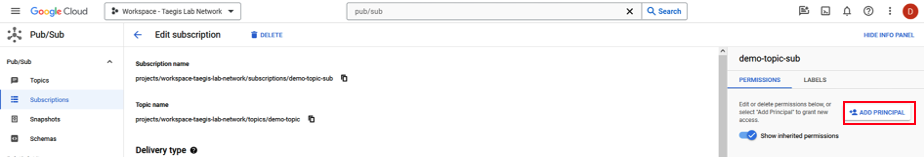
Add Principal
- Enter the service account email copied in Step 11 in the New principals field, and then select the Pub/Sub Subscriber Role.
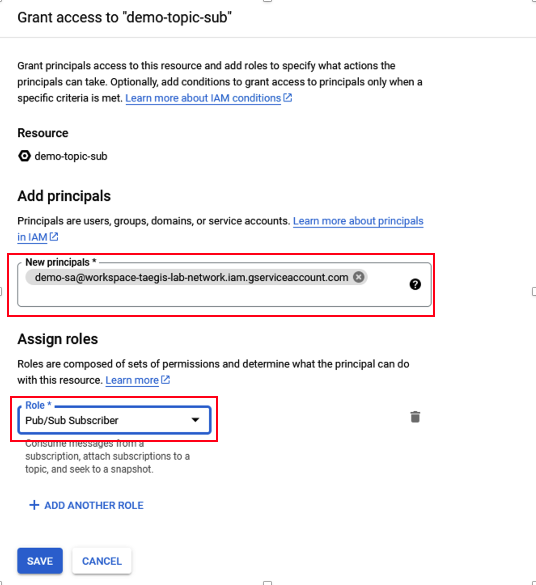
Grant Access
- Select Save.
Create a Service Account Key ⫘
- Open the Service account created in the preceding section and navigate to the Keys tab.
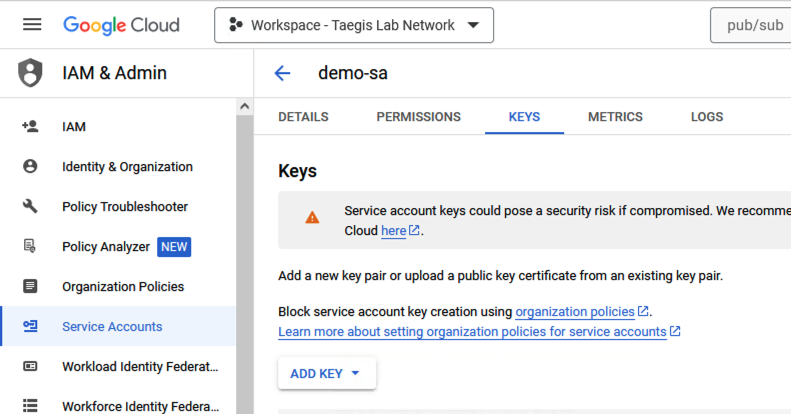
Service Account Key
- Select Add Key, choose the JSON type, and then select Create. Save the key in a secure location for use in Step 20.
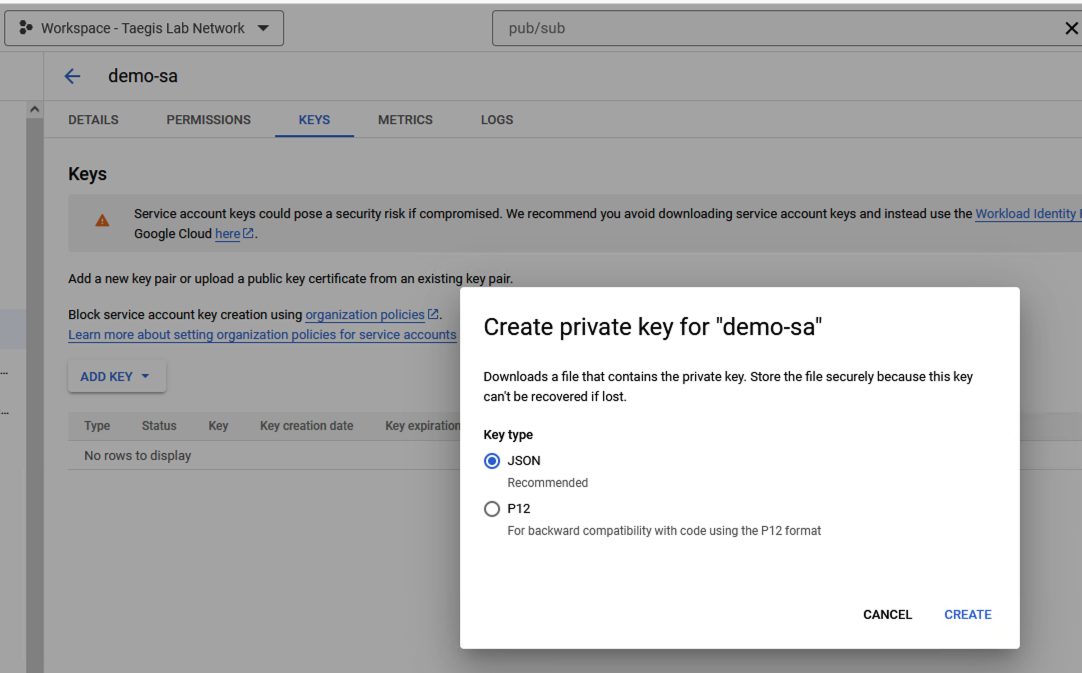
Create Private Key
Complete the Integration in XDR ⫘
- Log in to XDR and navigate to Integrations → Cloud APIs.
- Select Set Up Google Cloud Platform.
- In the XDR configuration panel, enter the following:
- Taegis Integration Name — Any user-friendly name to uniquely identify this integration
- Project ID — The GCP Project ID
- Subscription ID — The GCP Subscription ID
- Upload the JSON key generated in Step 17
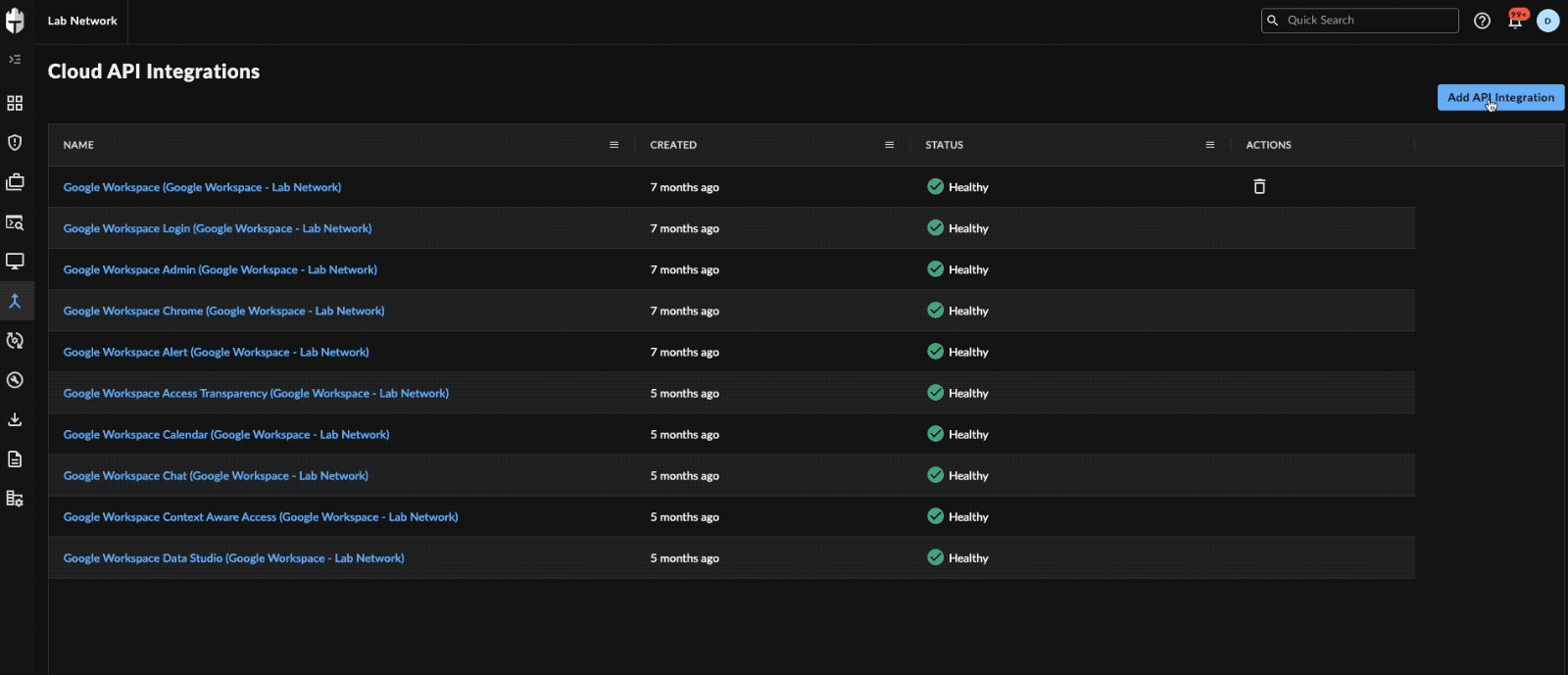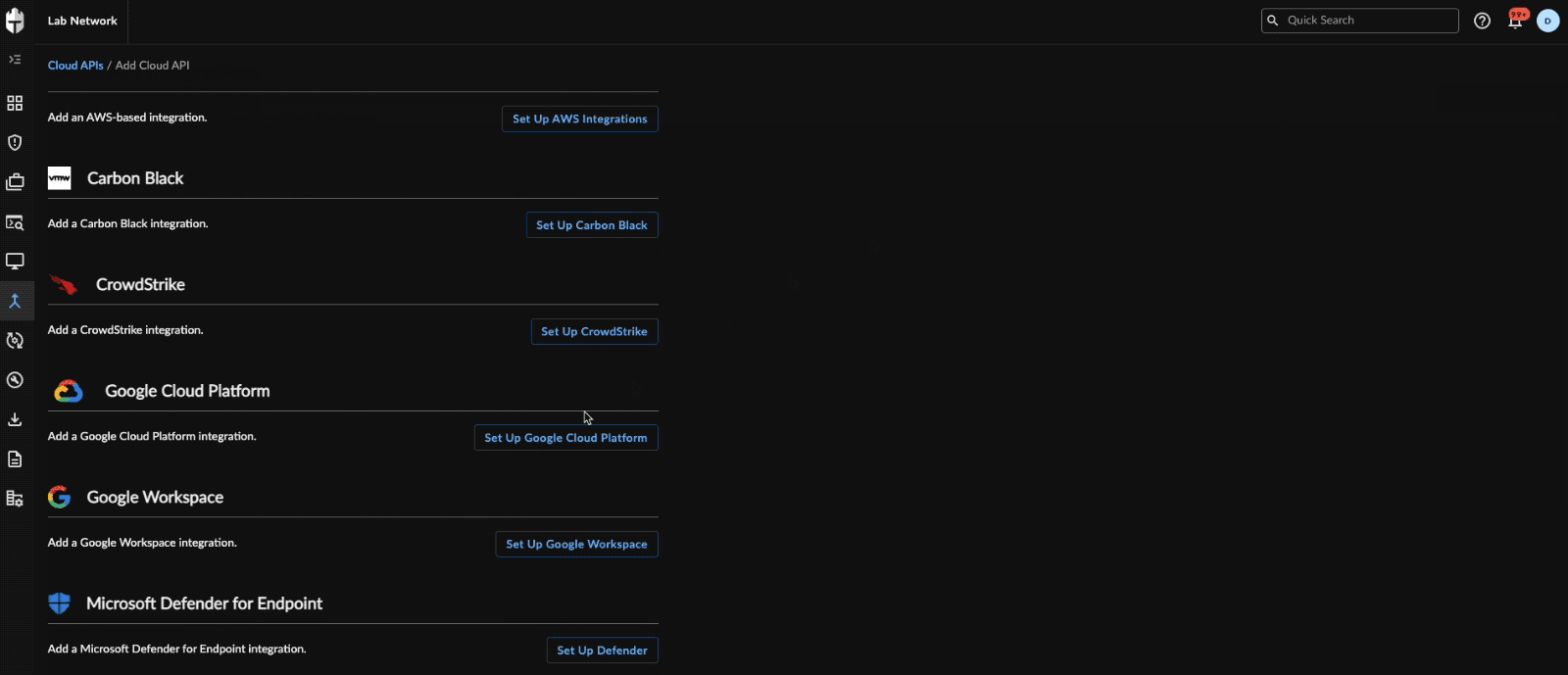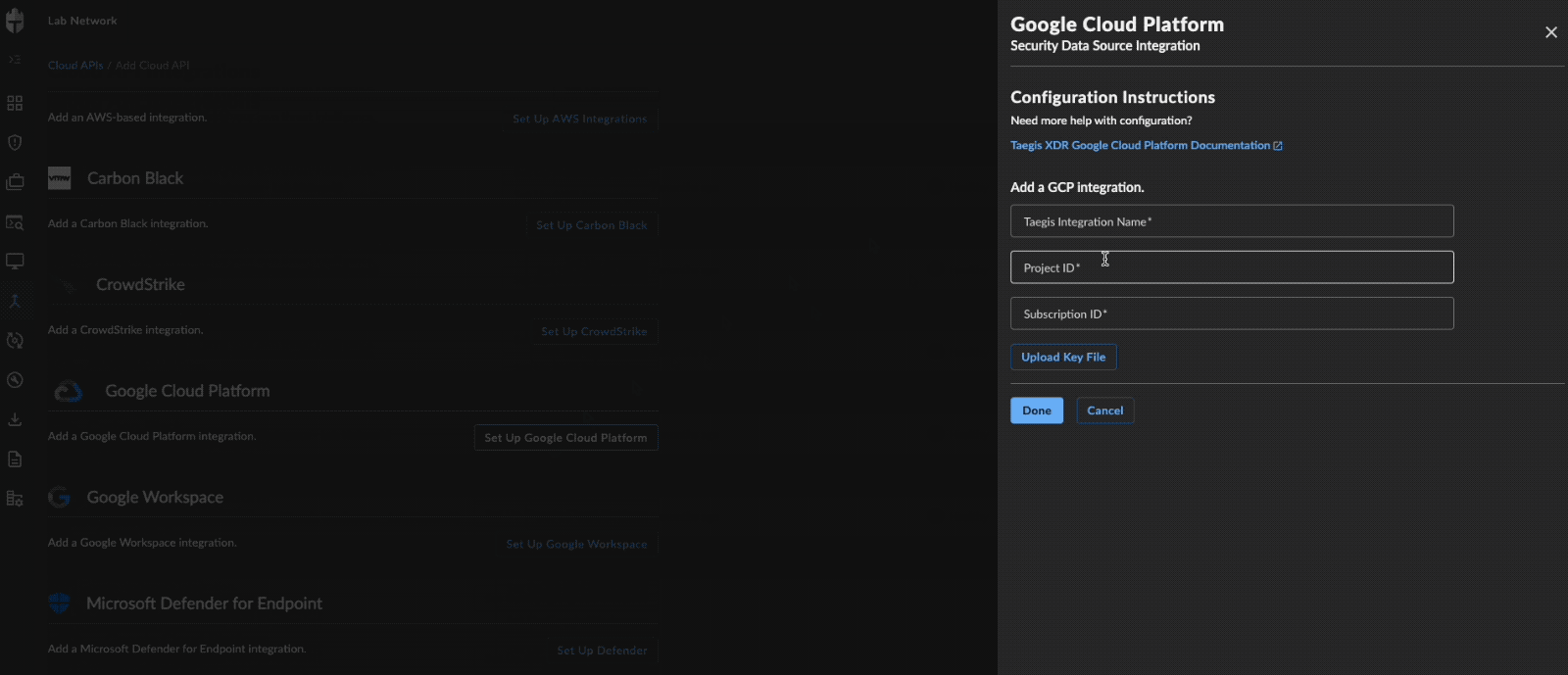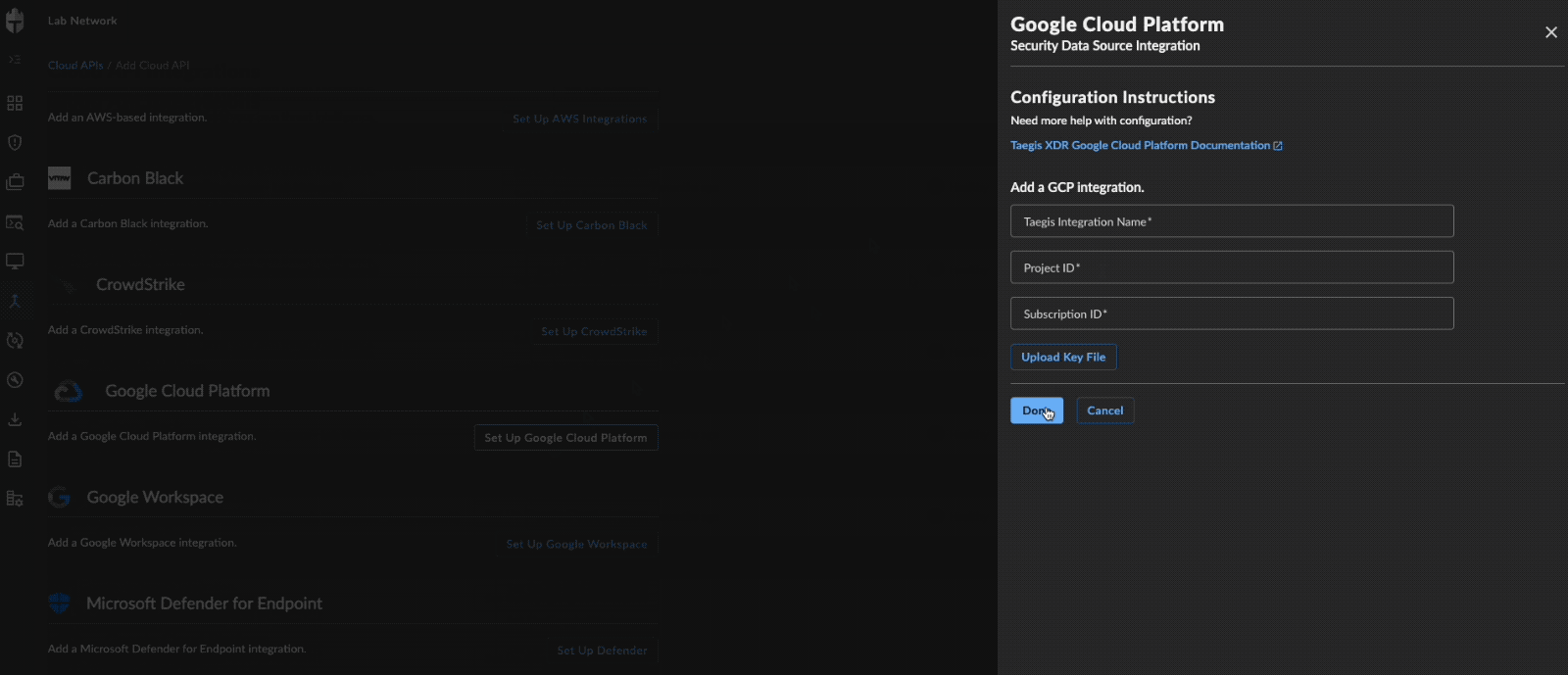
Add Google Cloud Platform Integration
Select Logs to Send to XDR ⫘
Reference the Google Cloud resource hierarchy to form the log inclusion filters.
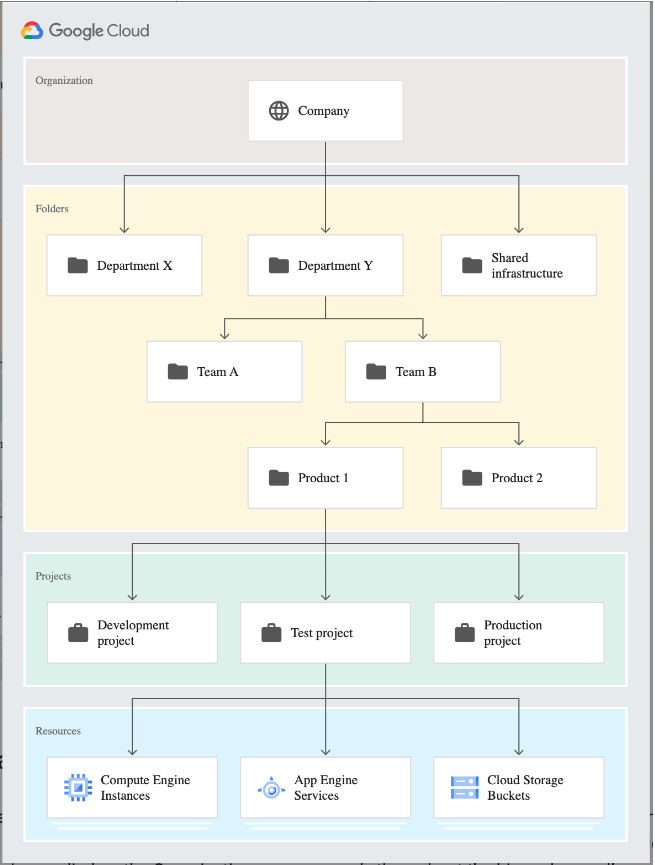
Google Cloud Resource Hierarchy
To select the logs to be sent to XDR, refer to the Create Sink section and update the inclusion filter using the following Cloud Audit Logs, VPC Flow Logs, Google Kubernetes Engine (GKE) Dataplane V2, and Security Command Center Findings sections.
Cloud Audit Logs ⫘
For more information on Cloud Audit Logs, see the Google documentation.
Configuration ⫘
- In the Google Cloud console, navigate to IAM & Admin > Audit Logs. Select the services for which Data Access audit logs should be enabled.
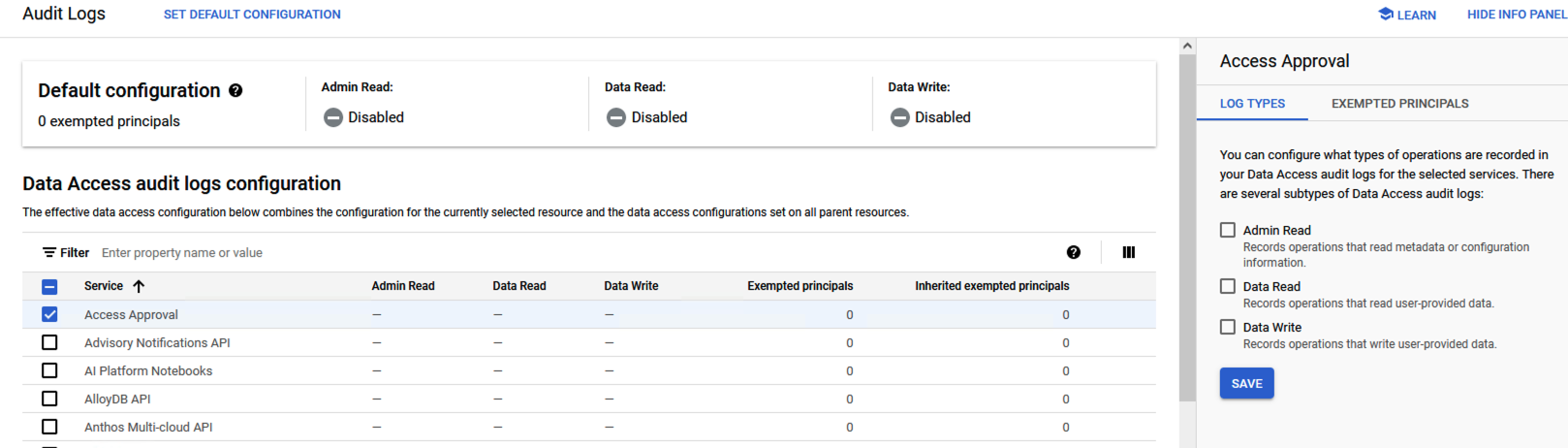
Data Access Audit Logs
- Create an inclusion filter to determine which logs are sent to the Pub/Sub topic. Refer to the following table to assist in the building of the inclusion filter for Cloud Audit logs.
| Admin Activity | Data Access | System Event | Policy Denied | |
|---|---|---|---|---|
| Projects | projects/PROJECT_ID/logs/cloudaudit.googleapis.com%2Factivity |
projects/PROJECT_ID/logs/cloudaudit.googleapis.com%2Fdata_access |
projects/PROJECT_ID/logs/cloudaudit.googleapis.com%2Fsystem_event |
projects/PROJECT_ID/logs/cloudaudit.googleapis.com%2Fpolicy |
| Folders | folders/FOLDER_ID/logs/cloudaudit.googleapis.com%2Factivity |
folders/FOLDER_ID/logs/cloudaudit.googleapis.com%2Fdata_access |
folders/FOLDER_ID/logs/cloudaudit.googleapis.com%2Fsystem_event |
folders/FOLDER_ID/logs/cloudaudit.googleapis.com%2Fpolicy |
| Organization | organizations/ORGANIZATION_ID/logs/cloudaudit.googleapis.com%2Factivity |
organizations/ORGANIZATION_ID/logs/cloudaudit.googleapis.com%2Fdata_access |
organizations/ORGANIZATION_ID/logs/cloudaudit.googleapis.com%2Fsystem_event |
organizations/ORGANIZATION_ID/logs/cloudaudit.googleapis.com%2Fpolicy |
VPC Flow Logs ⫘
For more information on VPC Flow Logs, see the Google documentation.
Considerations ⫘
-
VPC Flow logs can be enabled/disabled on a subnet level.
-
When enabled on a subnet, logs will be collected for all the virtual machines within that subnet.
-
Both the inbound and outbound network traffic will be sampled for log generation for TCP, UDP, ICMP, ESP, and GRE protocols. To learn more about sampling, see the Google documentation.
Configuration ⫘
- In the Google Cloud console, navigate to VPC Network > VPC Networks, select the network for which you would like to enable VPC Flow Logs, and then select the Subnets tab.
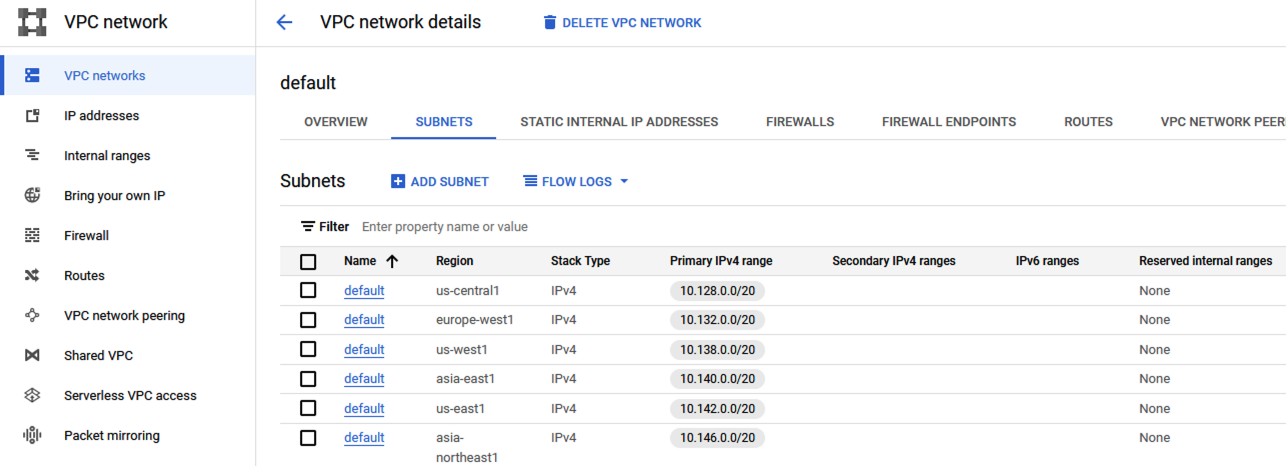
VPC Flow Logs
- On the subnet for which VPC Flow Logs are to be enabled, enter Edit mode. Under the Flow Logs section, select On.
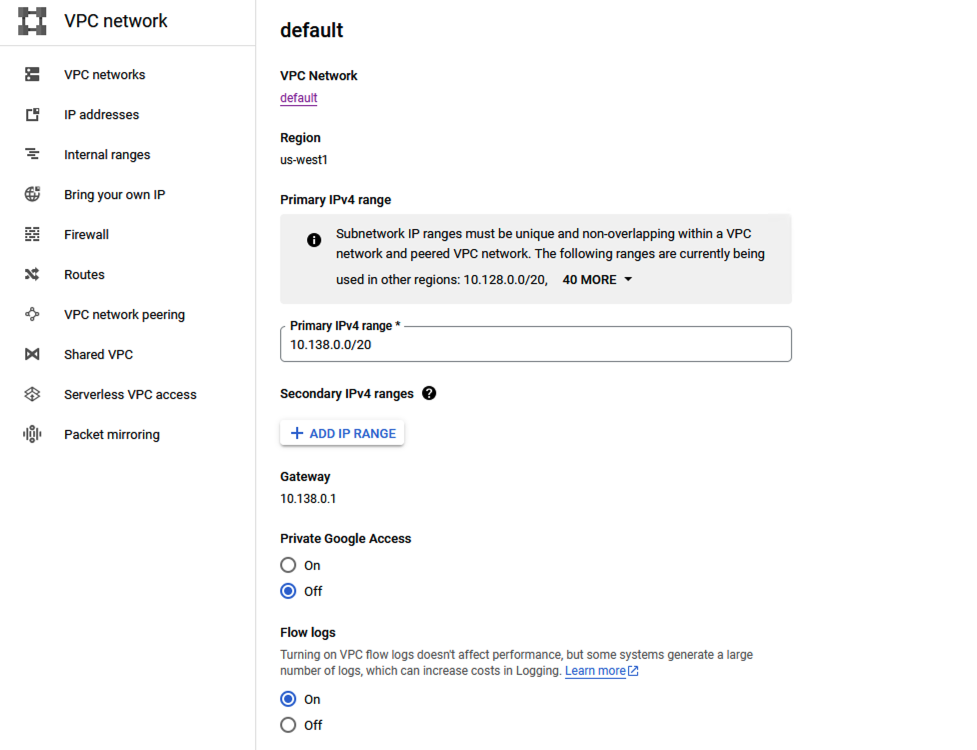
Enable VPC Flow Logs
- To route Flow Logs to the Log Router Sink created in the Create Sink section, edit the Sink and then update the Inclusion Filter.
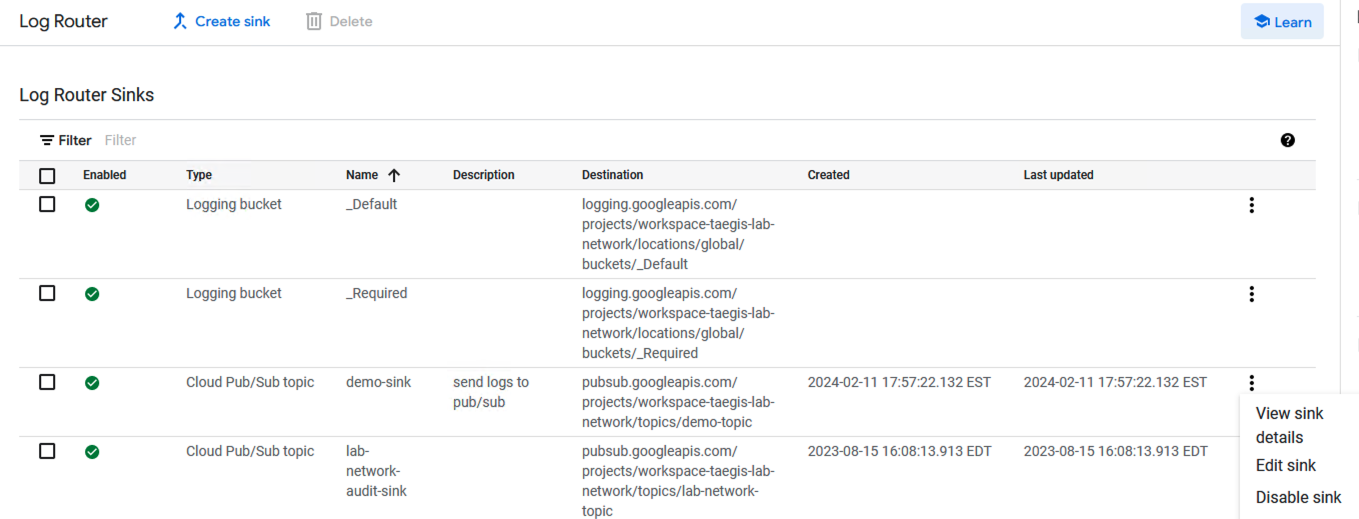
Route VPC Flow Logs
Example Inclusion Filter:
logName="projects/gcp-dataflow-poc/logs/compute.googleapis.com%2Fvpc_flows"
Google Kubernetes Engine (GKE) Dataplane V2 ⫘
For more information on GKE Dataplane V2, see the Google documentation.
Configuration ⫘
- Refer to the Google documentation to create a GKE cluster.
Important
GKE Dataplane V2 can only be enabled when creating a new cluster.
-
Refer to the Google documentation to enable network policy logging.
-
To route Flow Logs to the Log Router Sink created in the Create Sink section, edit the Sink and then update the Inclusion Filter.

Route VPC Flow Logs
Example Inclusion Filter:
logName="projects/gcp-dataflow-poc/logs/policy-action"
Security Command Center Findings ⫘
For more information on Security Command Center, see the Google documentation.
Configuration ⫘
- Security Command Center can be activated at the Organization and Project levels.
Organization Level ⫘
Refer to the Google documentation to activate Security Command Center for an organization.
Project Level ⫘
Refer to the Google documentation to activate Security Command Center for a project.
- In the Google Cloud console, navigate to Security > Security Command Center > Overview and select Edit Settings.
Edit SCC Settings
-
Select the Continuous exports tab.
-
Select Create Pub/Sub Export. Enter a user-friendly name and then select the Pub/Sub topic created in the Create Pub/Sub Topic section.
-
Select Save.
