CyberArk
The following instructions are for configuring CyberArk to facilitate log ingestion into Secureworks® Taegis™ XDR.
XDR normalizes logs from the following CyberArk products:
- Privileged Threat Analytics (PTA)
- Vault
Connectivity Requirements ⫘
| Source | Destination | Port/Protocol |
|---|---|---|
| CyberArk | Taegis™ XDR Collector (mgmt IP) | TCP/601 |
Data Provided from Integration ⫘
| Auth | CloudAudit | DNS | HTTP | Netflow | NIDS | Process | Thirdparty | |
|---|---|---|---|---|---|---|---|---|
| CyberArk | D | Y | V |
Y = Normalized | D = Out-of-the-Box Detections | V = Vendor-Specific Detections
Note
XDR detectors are not guaranteed to be triggered, even if a data source's logs are normalized to a schema associated with a given detector. However, you can create Custom Alert Rules to generate alerts based on normalized data from a data source.
Configure the CyberArk Platform ⫘
Configure Log Forwarding for Privileged Threat Analytics (PTA) ⫘
Follow the instructions in the CyberArk documentation to configure log forwarding.
Enter the following information:
| Option | Required Value |
|---|---|
| siem | Taegis |
| format | CEF |
| host | XDR Collector (mgmt IP) |
| port | 601 |
| protocol | TCP |
| syslogType | RFC3164 |
Configure Log Forwarding for Vault ⫘
Follow the instructions in the CyberArk documentation to configure log forwarding.
-
Create an XSL Translator File using this sample to generate Syslog output in the CEF format.
-
Enter the following information in the DBPARM.ini file.
| Option | Required Value |
|---|---|
| SyslogServerIP | XDR Collector (mgmt IP) |
| SyslogServerPort | 601 |
| SyslogServerProtocol | TCP |
| SyslogMessageCodeFilter | Recommended Action Codes for Monitoring |
| SyslogTranslatorFile | The XSL Translator File created in Step 1 above |
| SyslogProcessingTasks | Current Value |
| SyslogMessageProcessingLimit | Current Value |
| SyslogServerMessageLimit | Current Value |
| SyslogLimitNotificationFrequency | Current Value |
Example Query Language Searches ⫘
To search for PTA events from the last 24 hours:
FROM thirdparty WHERE sensor_type = 'CyberArk' and EARLIEST=-24h
To search for cloudaudit events:
FROM cloudaudit WHERE sensor_type = 'CyberArk'
To search for auth events associated with a specific user:
FROM auth WHERE sensor_type='CyberArk' AND source_user_name = 'foo'
Event Details ⫘
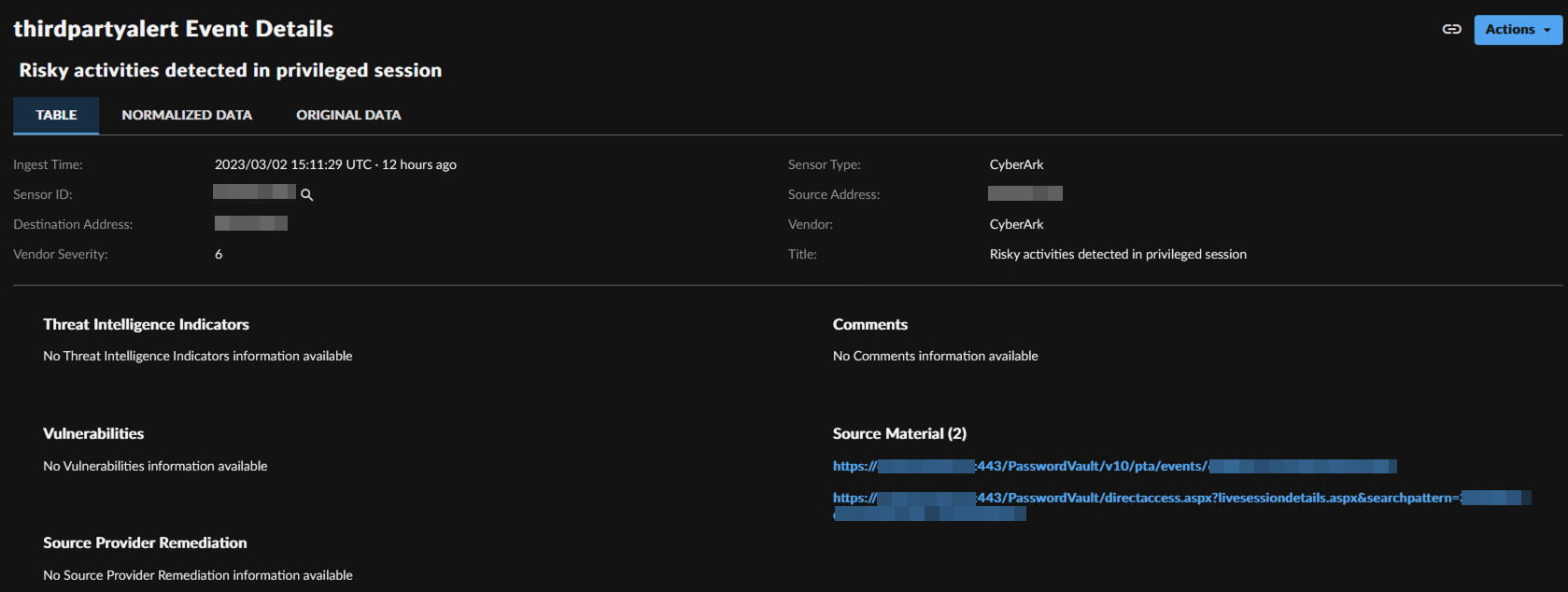
CyberArk PTA Event Details
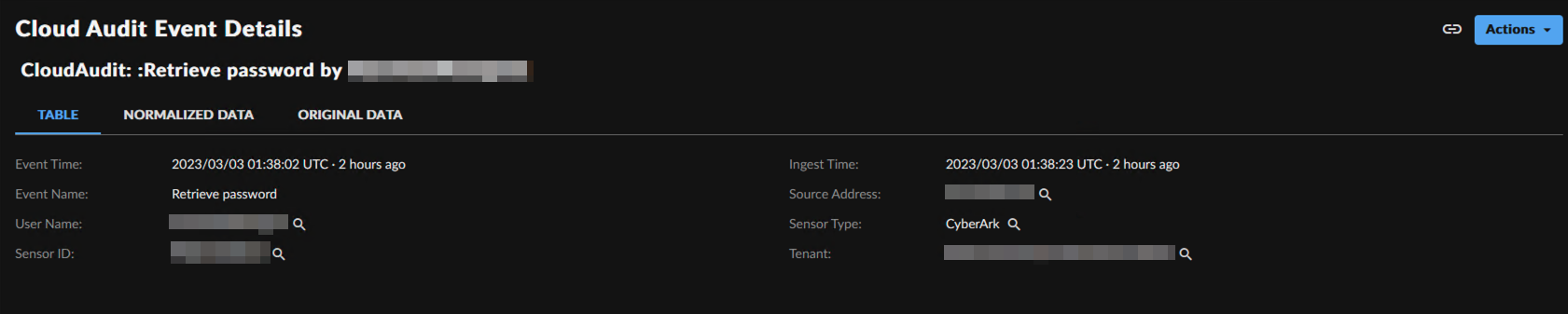
CyberArk Vault Event Details
Sample Logs ⫘
PTA ⫘
Oct 23 03:18:20 10.10.10.10 Oct 22 22:18:20 10.10.10.10 CEF:0|CyberArk|PTA|12.0|23|Privileged access to the Vault during irregular hours|2|suser=user(Vault user) shost=None src=None duser=user@domain.com dhost=host.domain.com dst=10.10.10.11 cs1Label=ExtraData cs1=None cs2Label=EventID cs2=6354b27bc2dc3bbcd4e0ffff deviceCustomDate1Label=DetectionDate deviceCustomDate1=1666495099000 cs3Label=PTALink cs3=https://cyberark.domain.com:443/PasswordVault/v10/pta/events/1234567890cccc cs4Label=ExternalLink cs4=None
Vault ⫘
Oct 21 21:00:27 10.1.2.3 Oct 21 17:00:27 ADEVICE CEF:0|Cyber-Ark|Vault|12.1.0000|7|Logon|5|act=Logon suser=user@domain.com fname= dvc=10.1.2.4 shost=10.10.2.2 dhost= duser= externalId= app= reason= cs1Label=""Affected User Name"" cs1= cs2Label=""Safe Name"" cs2= cs3Label=""Device Type"" cs3= cs4Label=""Database"" cs4= cs5Label=""Other info"" cs5=10.1.2.4 cn1Label=""Request Id"" cn1= cn2Label=""Ticket Id"" cn2= msg=
