SharpHound
The SharpHound Detector is designed to look for a Red Cloak telemetry profile from a victim host that had SharpHound executed against it using the default collection method. This allows SharpHound to be detected whether the attacker machine had Red Cloak installed or not. SharpHound is a data collector for BloodHound and is often used by threat actors, red teams, and blue teams to quickly identify insecure Active Directory configurations and attack paths. The detector monitors authentication and netflow events from Red Cloak™ Endpoint Agents and creates an alert when there is a particular sequence of these events matching the telemetry profile over a period of time.
Tip
For more information on the Secureworks Counter Threat Unit™ (CTU) research that resulted in the creation of this detector, see the blog post Sniffing Out SharpHound on Its Hunt for Domain Admin.
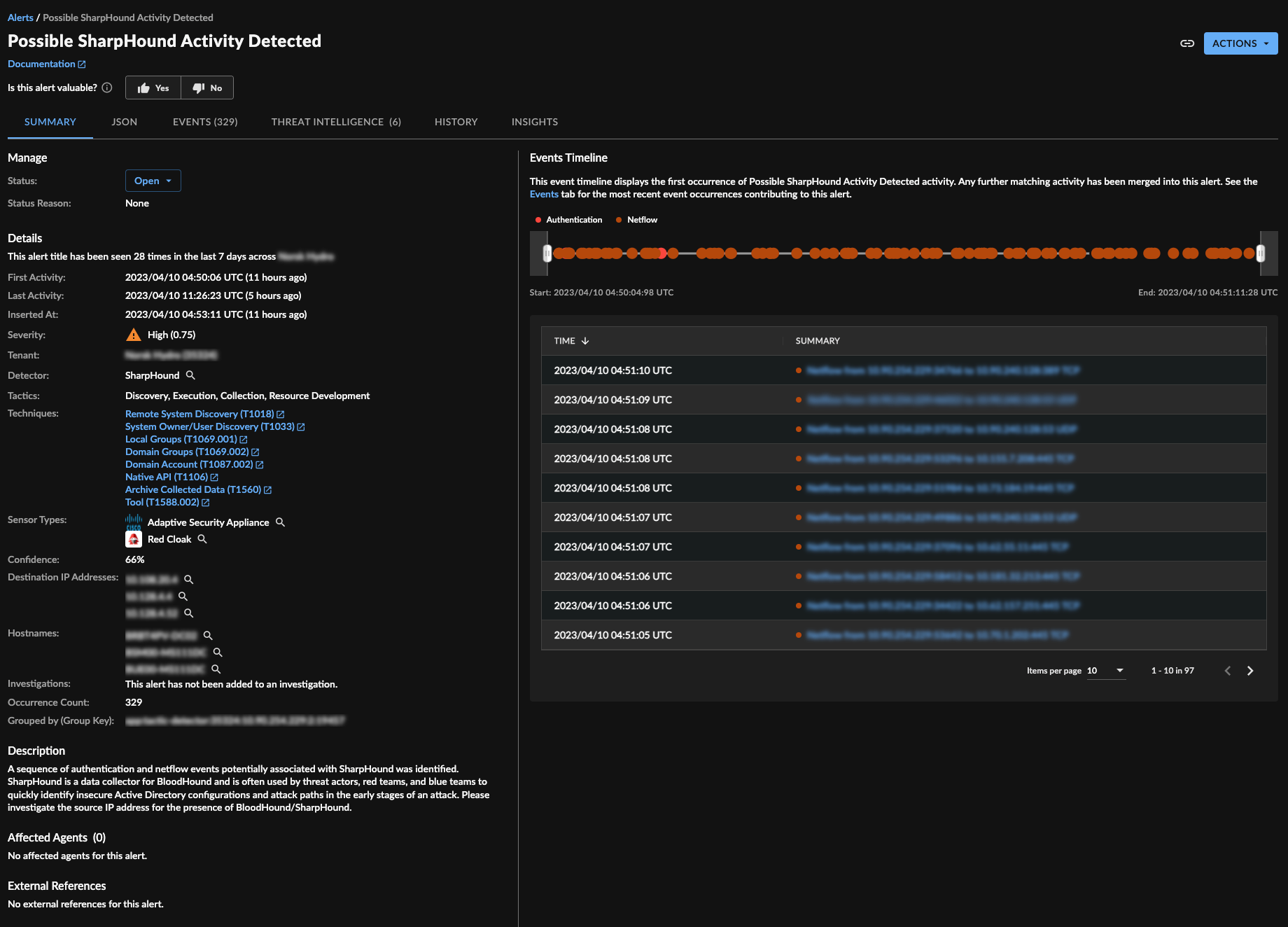
SharpHound Detector Alert
Note
The Events Timeline displays when available.
Inputs ⫘
Authentication and Netflow events from Red Cloak Endpoint Agents.
Schema ⫘
Auth, Netflow
Outputs ⫘
Alerts pushed to the Secureworks® Taegis™ XDR Alert Database and XDR Dashboard.
MITRE ATT&CK Category ⫘
- MITRE Enterprise ATT&CK - Resource Development - Obtain Capabilities: Tool. For more information, see MITRE Technique T1588.002.
- MITRE Enterprise ATT&CK - Collection - Archive Collected Data. For more information, see MITRE Technique T1560.
- MITRE Enterprise ATT&CK - Discovery - Local Groups. For more information, see MITRE Technique T1069.001.
- MITRE Enterprise ATT&CK - Discovery - Domain Groups. For more information, see MITRE Technique T1069.002.
- MITRE Enterprise ATT&CK - Execution - Native API. For more information, see MITRE Technique T1106.
Configuration Options ⫘
None
