Snapshot Exfiltration Detector
The Snapshot Exfiltration Detector alerts when AWS EC2 snapshots are maliciously exported or when permissions are granted to an unknown account in preparation for copying a snapshot. The detector looks for a sequence of events where a user is granted permissions to an EC2 instance snapshot and then the snapshot is copied to another account within a specified timeframe.
This detector scores process events for a set timeframe using predetermined rules and then uses these scores to identify potential Snapshot Exfiltration activity, published as alerts to the Secureworks® Taegis™ XDR Dashboard.
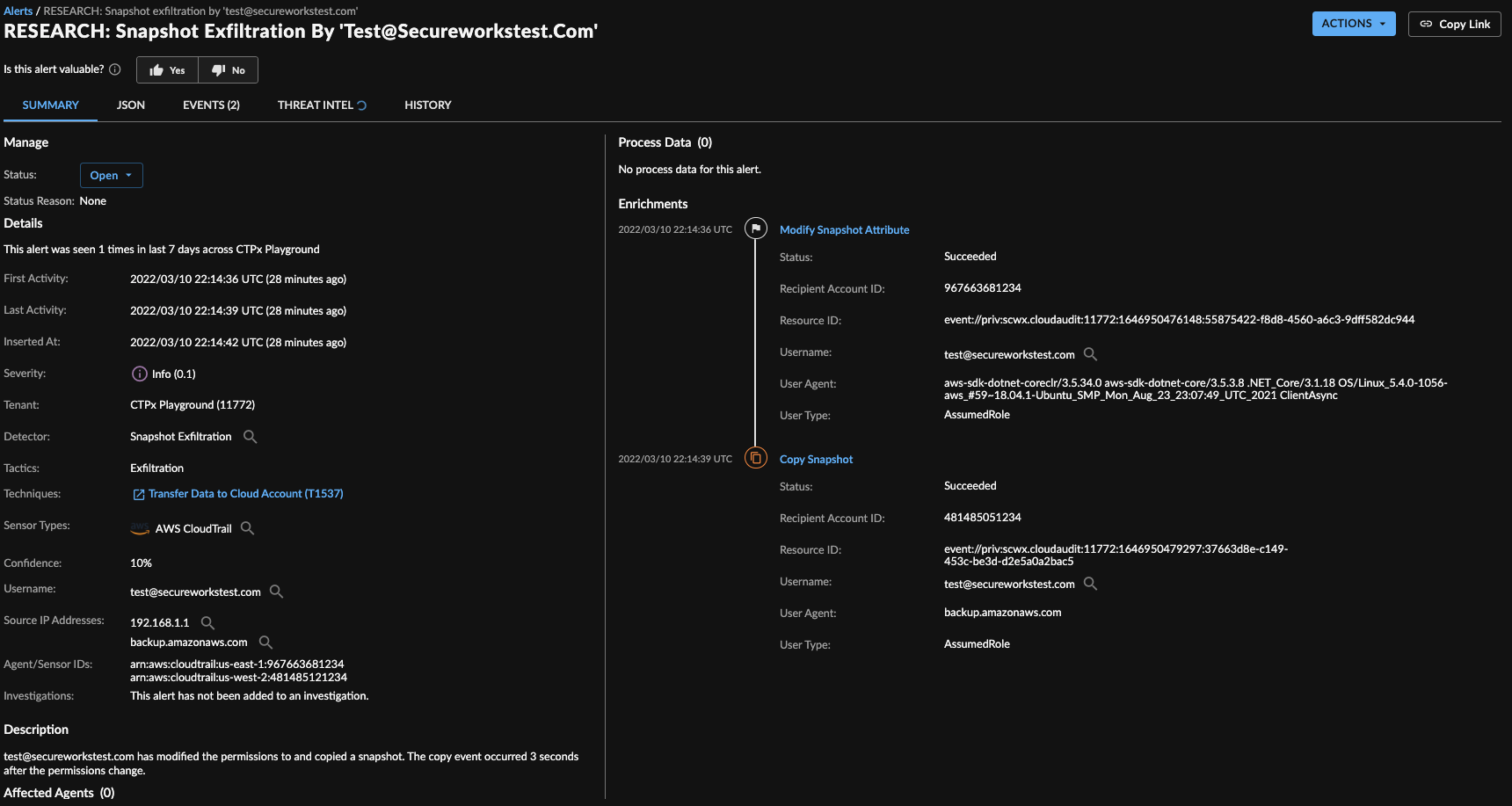
Snapshot Exfiltration Alert
Schema ⫘
CloudAudit
Outputs ⫘
Snapshot Exfiltration alerts pushed to the XDR Dashboard
MITRE ATT&CK Category ⫘
MITRE Enterprise ATT&CK - Exfiltration - Transfer Data to Cloud Account. For more information, see MITRE Technique T1537.
Configuration Options ⫘
None
