Microsoft Azure Activity Log Integration Guide
cloud integrations microsoft azure event hubs
The following instructions are for configuring an integration of Azure Activity Logs to facilitate ingestion into Secureworks® Taegis™ XDR.
XDR supports two integration paths for Azure Activity Logs:
- (Preferred) Integrate via Azure Event Hubs — This option is preferred due to it providing the fastest and highest throughput of data, however it may incur additional costs to enable.
- Integrate via Azure Monitor API (REST) — This option provides equivalent data to event hubs, but due to the polling nature of a REST-based API in addition to Microsoft rate-limiting, there may be limitations with how quickly data can be collected. See Office 365 and Azure Data Availability for information on our polling practices.
Start Event Hub Integration ⫘
Configure Azure Monitor Diagnostic Settings ⫘
Follow the Microsoft instructions to enable Azure Monitor diagnostic settings:
XDR supports the following diagnostic categories for data normalization:
Optimized Structured Logs Categories ⫘
Note
All other logs will normalize to the Generic schema. A custom parser may be needed to enable normalization of other data sources beyond the Generic schema. It is not recommended to forward metric data to XDR as it will be treated as all other log data and not metrics.
Forward to Event Hub and Enable Integration with XDR ⫘
- Once the desired log categories are selected, choose to Stream to an event hub and enter the desired event hub destination.
- Follow the integration instructions for an event hub to complete the integration with XDR and to begin data ingestion.
Data Provided from Integration ⫘
| Antivirus | Auth | CloudAudit | DHCP | DNS | Encrypt | HTTP | Management | Netflow | NIDS | Thirdparty | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| MS Azure Activity Logs | V |
Y = Normalized | D = Out-of-the-Box Detections | V = Vendor-Specific Detections
Note
XDR detectors are not guaranteed to be triggered, even if a data source's logs are normalized to a schema associated with a given detector. However, you can create Custom Alert Rules to generate alerts based on normalized data from a data source.
Start Azure Monitor API ⫘
Note
Collection of Azure Activity logs uses the Azure Monitor REST API, which leverages an authorization scope of user_impersonation to collect log data. In addition to this, the permission is delegated, meaning actions are performed on behalf of the consenting user, instead of on behalf of the application. This document guides you through the process of setting up and configuring a user within Azure that has least-privileged access to the data to be collected, in addition to consenting to the application and enabling the collection of logs within XDR. If a user with the required access to Azure activity logs is already configured, the steps for configuring a user in Azure are optional.
Notes
Azure integrations are supported in US and EU regions, but may not be supported by Microsoft in other regions. Contact Microsoft directly to verify their support of services in other regions.
Note
The integration collects subscription-level activity logs from Azure. Please see the vendor documentation for more details.
Configuring an Azure User ⫘
Creating a user in Microsoft Azure requires a user with the role User Administrator or equivalent permissions.
Note
Creating a new Azure Active Directory user creates an identity with access to your Azure resources. Securing this identity is the responsibility of the user. This guide will only cover configuring the necessary user settings for integration with XDR, however additional steps should be taken to secure the user according to recommended best practices, as well as your organizations security controls and standards.
Create the User ⫘
- Navigate to the Microsoft Azure Portal.
- Proceed to the Azure Active Directory resource and select the Users option in the left-hand pane.
- From Users, select New User.
- Leave the default option selected to Create a New User.
-
Under Identity fill in the following fields:
- User Name — TaegisActivityIntegrationUser, for example. Make a note of the user name, you'll need it in a later step.
- Name — Secureworks Taegis, for example.
-
In the Password, select the option for Let me create the password and fill in a secure password. You will be prompted to enter this password when performing consent in a later step.
- From Groups and roles, click on the User role to be prompted with a set of built-in roles to assign to the user. Select the Directory readers role in the right-hand pane and click Select.
- Click the Create button to finish creating the user.
Collect a List of Subscription IDs to be Integrated ⫘
- Navigate to the Subscriptions Resource in the Microsoft Azure Portal.
- Copy the Subscription ID(s) for each subscription to be monitored by XDR. You will be prompted to enter this ID in the next step.
Note
Filters and user IAM roles may prevent viewing some subscriptions. Ensure your user allows access to view all subscriptions and that any subscription filters are not hiding subscriptions to be monitored.
Consent the Application ⫘
Note
Currently subscriptions must be added to XDR one at a time, but you can add any number of subscriptions. For each subscription to be added, the consent process must be repeated. When completing the consent process, you may use the same user created previously.
- Navigate to Integrations and select Cloud APIs from the left-hand navigation in XDR.
- Select the option to Add API Integration and choose Office 365/Azure from the cards displayed.
- In the Azure Activity Logs box, enter a valid Subscription ID.
Note
This ID may have been copied in the previous section.
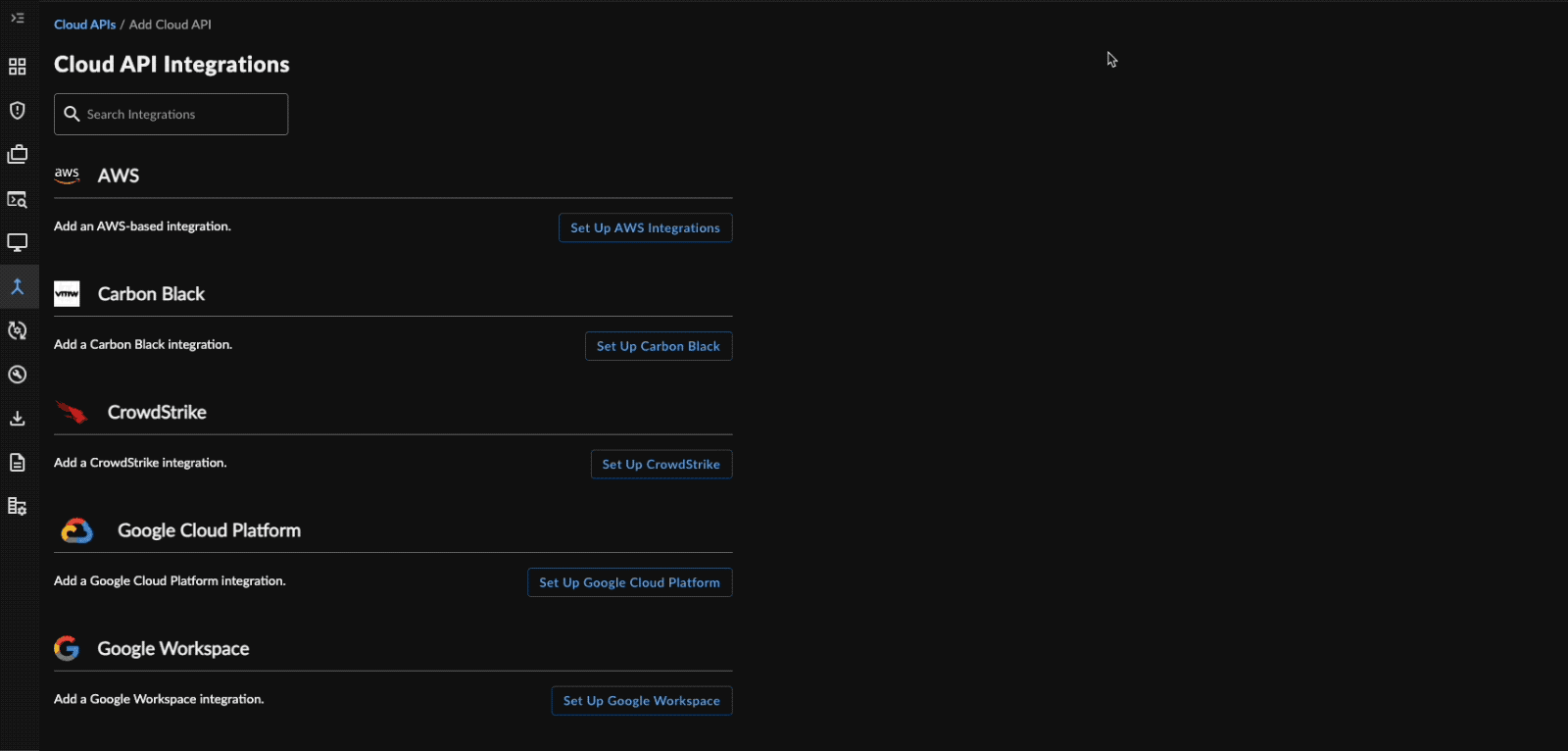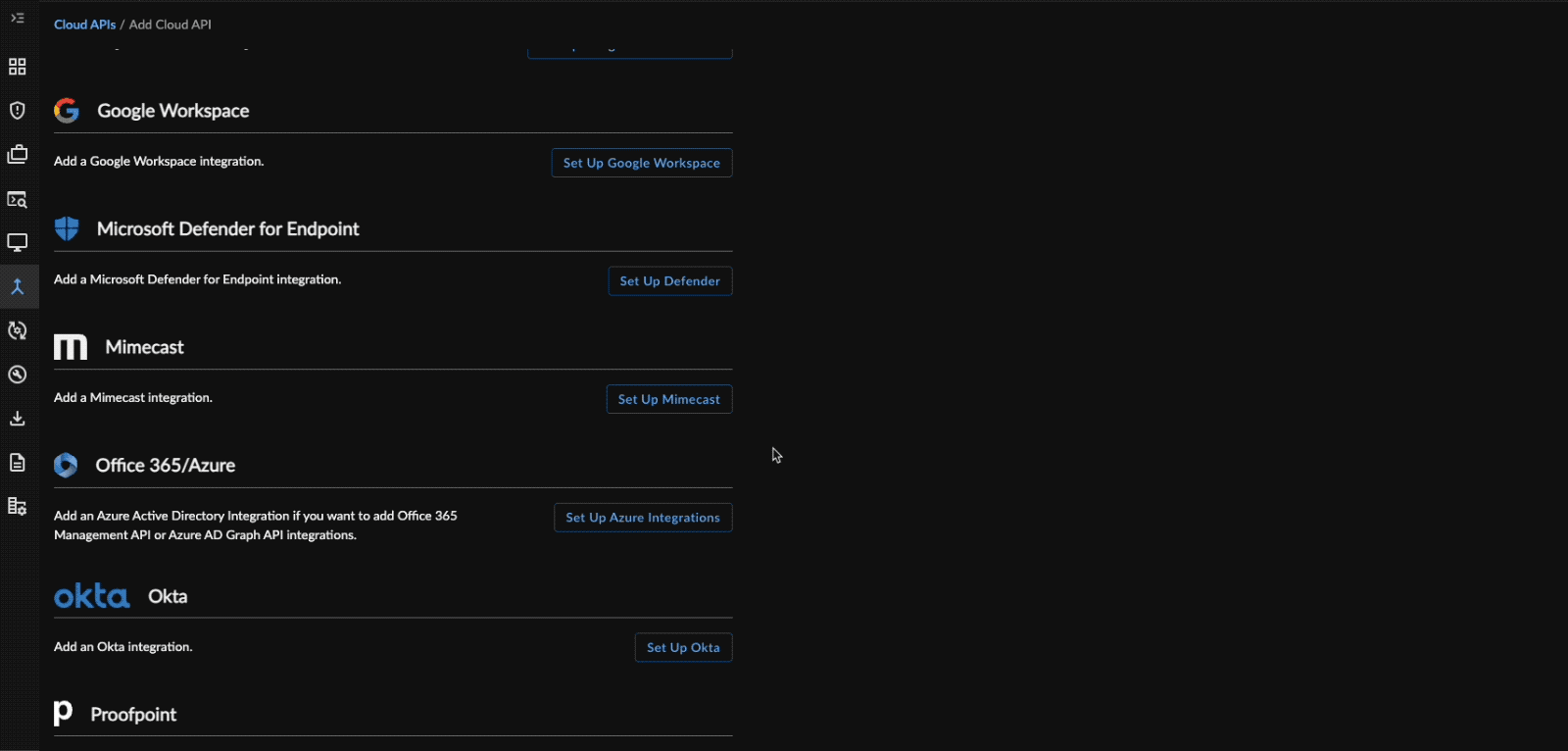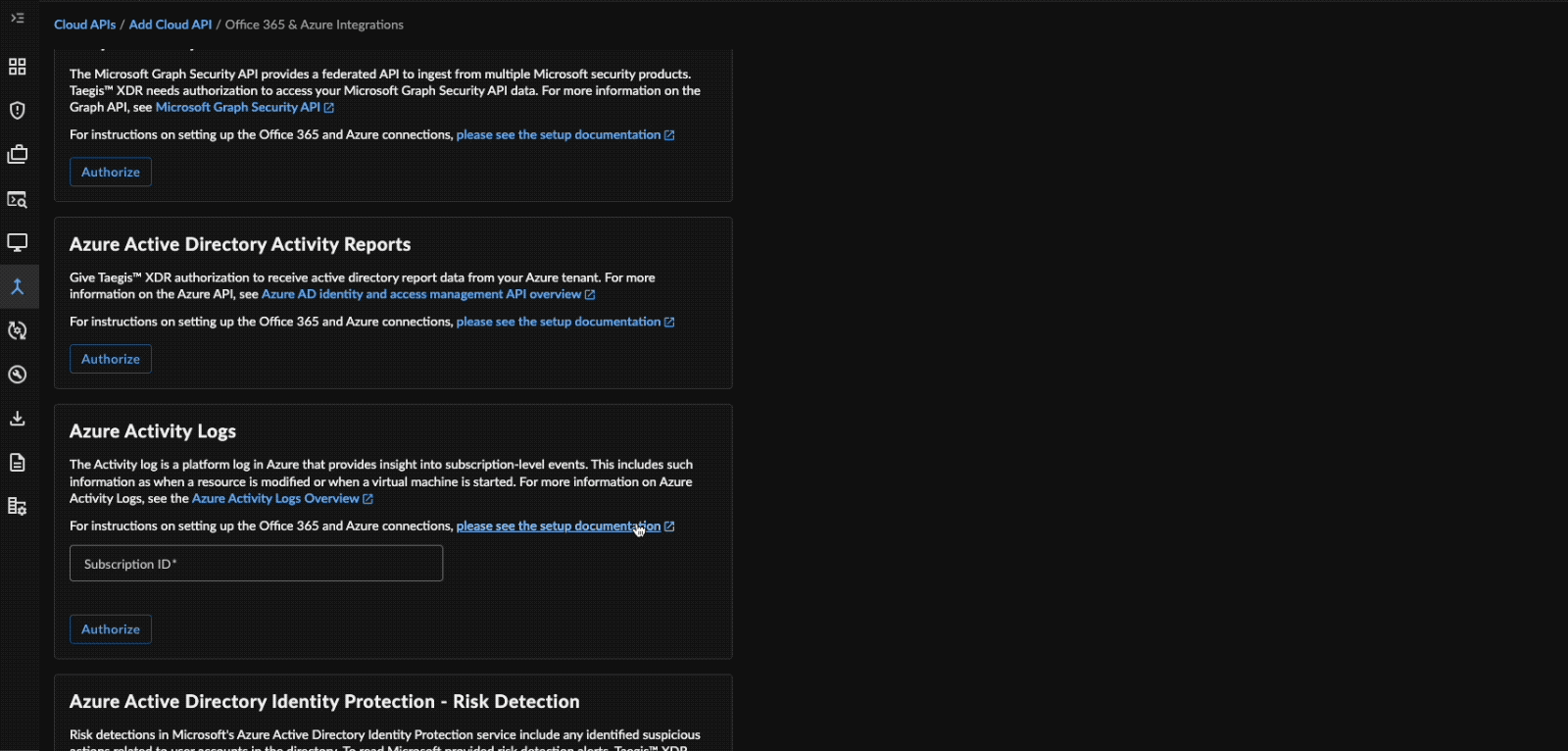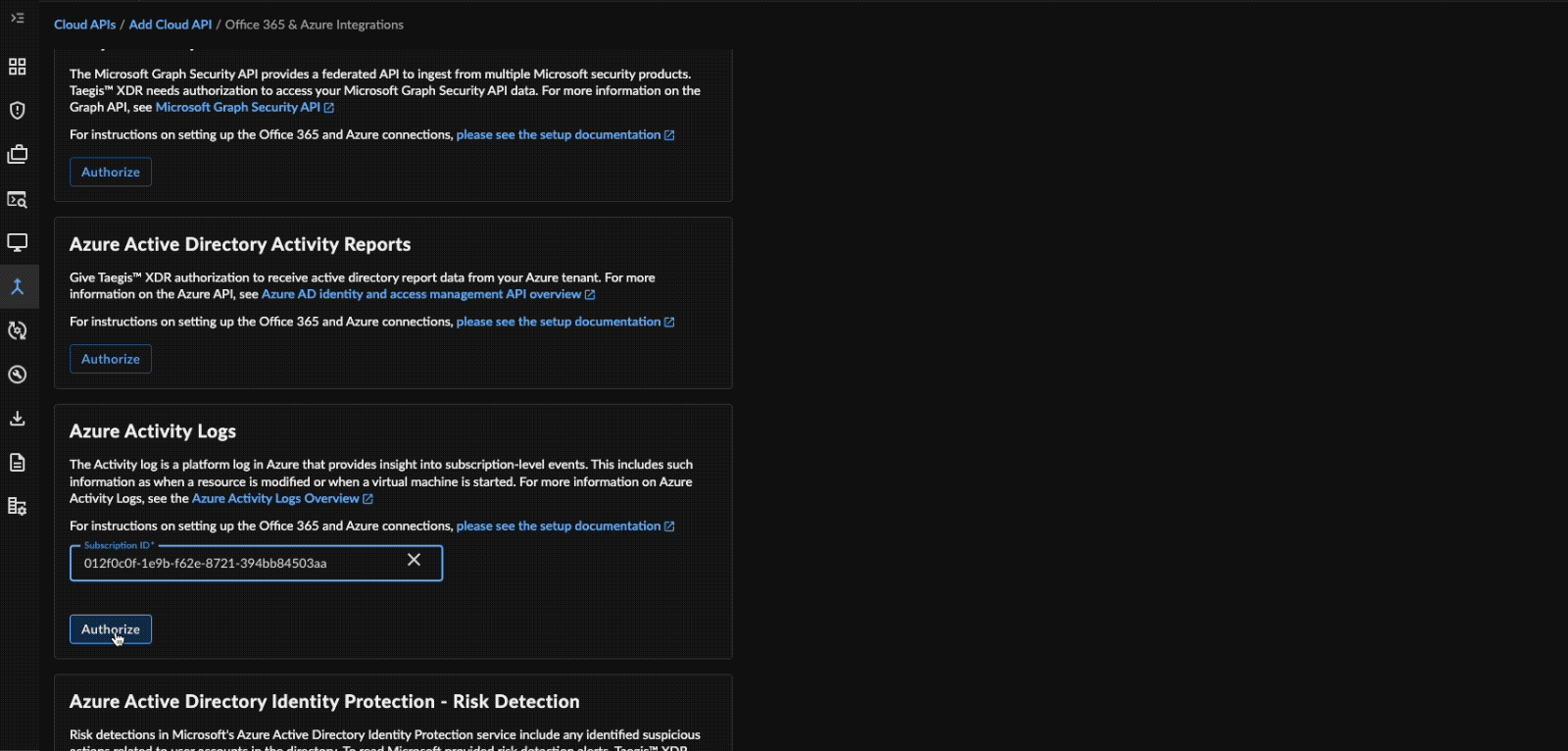
Add Azure Subscription
- Once the subscription is entered, you will be redirected to Microsoft’s identity provider to consent access. Log in using the user you created from Create the User and approve the listed permissions to authorize XDR access.
- If the consent process is successful, you will be redirected back to XDR. Do not yet enter a name for the integration, and instead proceed to the next step.
Note
If you receive an error message related to application consent, the underlying cause is that the Azure account has Admin Consent enabled. XDR is unable to process the asynchronous application consent and complete the integration regardless of whether the correct permissions are assigned to it. There are two options to resolve this issue:
- Add the Application Administrator role to the
TaegisActivityIntegrationUserand perform the consent using that user. Once the consent has been granted the Role can be removed from the user. - Disable Admin Consent option on the Azure account and perform the consent using the user
TaegisActivityIntegrationUser. Once the integration has been completed Admin Consent option can be re-enabled on the Azure account.
Add the Service Principal to the Subscriptions to be Monitored ⫘
Note
This step can only be completed once the Consent the Application section is completed successfully. This step will add the service principal created via the consent process to the subscription to be monitored. Note that this is being done for the application service principal and not the user created earlier.
- Navigate to the Subscriptions Resource in the Microsoft Azure Portal.
- Select the Access Control (IAM) option in the left-hand pane.
- Select the option to Add and choose Add role assignment.
- Select the Reader role and click Next.
- Under Assign access to, leave the option selected for User, group, or service principal.
- In the Members section, select to add a member. In the right-hand pane, search for the service principal of the application that was consented, Secureworks Taegis - Azure Activity Logs Integration.
- Click the Review and Assign button to assign the user to the subscription.
Note
The above steps must be completed for each subscription to be monitored.
Add the Integration Name ⫘
- Enter a unique name for the integration in XDR and click Done
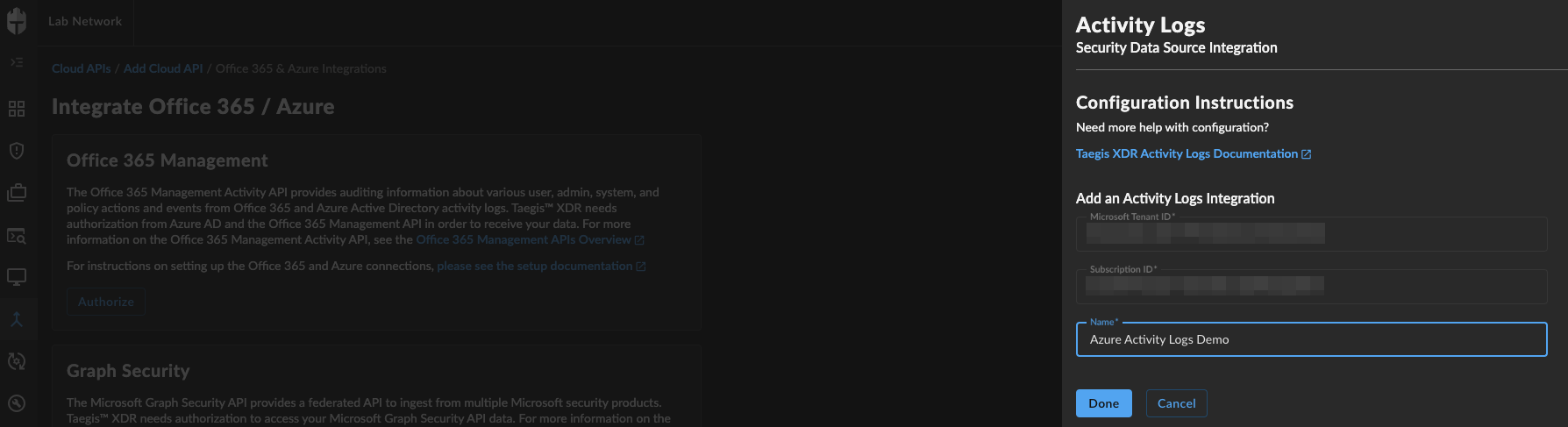
Azure Activity Logs Integrations
- Repeat these steps to add additional subscriptions.
Data Provided from Integration ⫘
| Antivirus | Auth | CloudAudit | DHCP | DNS | Encrypt | HTTP | Management | Netflow | NIDS | Thirdparty | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| MS Azure Activity Logs | V |
Y = Normalized | D = Out-of-the-Box Detections | V = Vendor-Specific Detections
Note
XDR detectors are not guaranteed to be triggered, even if a data source's logs are normalized to a schema associated with a given detector. However, you can create Custom Alert Rules to generate alerts based on normalized data from a data source.
Link Secureworks as a Microsoft Partner ⫘
Linking Secureworks as a Solution Provider for Security is an optional process that enables Microsoft to better understand what customers Secureworks is enabling to achieve their security goals and realize the value of the Microsoft ecosystem. This allows Secureworks better access to Microsoft as a partner, enabling us to provide you, our customer, with better products and services. If you have successfully added access to your Azure environment to allow Secureworks to help enable your business through improved security, we would appreciate if you would additionally add us as a partner link to show that this is in place.
To link Secureworks as a partner, folllow these steps:
- Navigate to Link to a partner ID in the Azure Portal.
- Use a user with eligible roles or permissions, see Roles and Permissions Required to Receive Credit.
- In the Microsoft Partner ID box, enter the value:
4834104 - Click on the Link a partner ID button to complete the process.
