Google Cloud Platform (GCP) Collector
data collectors integrations google gcp
Secureworks® Taegis™ XDR has a collector that can be set up in Google Cloud Platform (GCP). The Taegis™ XDR Collector for GCP is provided as a GCP Deployment Manager template. Each collector is uniquely identified by its configuration. For convenience, configuration data is injected into a GCP template by way of custom data. This template creates the following resources:
- Compute Instance-Template — Defines the compute instance parameters used when launching the instance, which includes the correct image for the region and user-data.
- Network Interface — A network interface for the instance provisioned with appropriate network and subnet parameters.
- Firewall Rules — A set of firewall rules provisioned for the instance to run as a XDR Collector.
XDR provides options to download the sample template. The template should work in most GCP environments, but you must carefully review it before use to ensure it conforms to all relevant network and security policies. Advanced users can extract the GCP template and user-data from the template to incorporate into their own IaC or automation tools.
Configuration Notes ⫘
-
The generated template creates the network interfaces for the compute instance and compute firewall rules for reporting, NTP, TCP-DNS, UDP-DNS, TCP-syslog, and UDP-syslog.
-
The generated template creates a compute engine persistent disk size 200G attached as
/dev/sdbto the collector. If you customize the template or implement your own automation, make sure that the device is always attached as/dev/sdbwith a minimum size of 200G. -
To locate your GCP Service Agent ID, browse to IAM & Admin in the GCP console and find the principal named Google APIs Service Agent. The format should be
<numeric ID>@cloudservices.gserviceaccount.com.
Note
The XDR Collector can support up to 200K EPS (events per second) for properly configured cloud and on-premises collectors.
Note
Third-party tools or applications cannot be installed on any XDR Collector.
Connectivity Requirements for Data Collectors ⫘
Regions
XDR Regional Configuration ⫘
Some configuration specifics of XDR depend on the region you are deployed in (US1, US2, US3, EU).
Any device that uses its own SSL certificate, including Cloud-based and On-Premises Data Collectors, must safelist the following destination IP addresses or domains in order to avoid conflict. If using an AWS data collector, please refer to the AWS table.
For Most Data Collectors ⫘
| Source | Destination | Port/Protocol | Notes |
|---|---|---|---|
| Data Collector IP or hostname | US1collector.ctpx.secureworks.com18.217.45.178/32 3.16.4.173/32 18.224.219.97/32 13.59.146.90/32 3.16.16.254/32 18.223.74.238/32 US2collector.delta.taegis.secureworks.com52.14.113.127/32 3.141.73.137/32 3.136.78.106/32 US3collector.foxtrot.taegis.secureworks.com44.229.101.49 35.166.77.47 34.214.135.78 EUcollector.echo.taegis.secureworks.com18.158.143.139/32 35.159.14.37/32 52.59.37.234/32 |
TCP/443 | Safelisting device access to XDR |
| Data Collector IP or hostname | NTP severs IP/Hostnames provided during provisioning | UDP/123 | Safelisting device access to NTP servers This rule is only necessary when custom NTP servers are provided during provisioning. |
| Data Collector IP or hostname | 0.pool.ntp.org 1.pool.ntp.org 2.pool.ntp.org 3.pool.ntp.org |
UDP/123 | Safelisting device access to default NTP server. This rule is only necessary when custom NTP servers are not provided during provisioning. |
| Data Collector IP or hostname | DNS server IPs provided during provisioning | UDP/53 TCP/53 |
Safelisting device access to DNS servers |
Note
If using local NTP, the access must be safelisted both to and from the data collector on those networks.
For AWS Data Collectors ⫘
| Source | Destination | Port/Protocol | Notes |
|---|---|---|---|
| AWS Data Collector IP or hostname | US1collector.ctpx.secureworks.com18.217.45.178/32 3.16.4.173/32 18.224.219.97/32 13.59.146.90/32 3.16.16.254/32 18.223.74.238/32 US2collector.delta.taegis.secureworks.com52.14.113.127/32 3.141.73.137/32 3.136.78.106/32 US3collector.foxtrot.taegis.secureworks.com44.229.101.49 35.166.77.47 34.214.135.78 EUcollector.echo.taegis.secureworks.com18.158.143.139/32 35.159.14.37/32 52.59.37.234/32 |
TCP/443 | Safelisting device access to Taegis XDR via hostname |
| AWS Data Collector IP or hostname | NTP severs IP/Hostnames provided during provisioning | UDP/123 | Safelisting device access to NTP servers This rule is only necessary when custom NTP servers are provided during provisioning. |
| AWS Data Collector IP or hostname | 169.254.169.123 | UDP/123 | Safelisting device access to default NTP server. This rule is only necessary when custom NTP servers are not provided during provisioning. |
| AWS Data Collector IP or hostname | DNS server IPs provided during provisioning | UDP/53 TCP/53 |
Safelisting device access to DNS servers |
Proxy Support ⫘
Cloud-based and On-Premises Data Collectors attempt to discover local proxy settings on the host if they are unable to connect directly to the internet.
Cloud-based and On-Premises Data Collectors also support a hard-coded proxy. If you need to create a data collector that contains a hard-coded proxy, please submit a support request with the following required information:
- Proxy IP
- Proxy Port
If the proxy is configured but is unavailable or not reachable, the data collector will fall back to a direct connection.
Note
Cloud-based and On-Premises Data Collectors do not support hard-coded authenticated proxies at this time. A proxy with man in the middle (MITM) capability needs to safelist the above network connections.
Install and Configure a XDR GCP Collector ⫘
Start the process to configure your XDR GCP Collector in XDR from Integrations > Data Collectors. Follow the prompts to create and then download the template. The template must be applied using the gcloud CLI tools per Google’s GCP documentation to complete the configuration.
- From XDR, select Integrations from the left-hand navigation and then choose Data Collectors.
- Select Actions > Add Collector from the top right.

Add New Collector
- Select Cloud-Hosted as the collector type and then select Next.
- Fill in the required name and hostname fields, and the optional description, host proxy, and NTP servers fields, and then select Create Collector.
Note
You have the option to specify your own NTP servers if desired, and to add an HTTP proxy address, which must follow the following format: [http\[s]://\[user:pass@]hostname\[:port]|http://<hostname>[:port]].
Note
Default and custom NTP settings are only used during initial Data Collector setup. Once connectivity is established, the Data Collector synchronizes time via the XDR backend connection.

Create Cloud Collector
Tip
To add the eStreamer app to the collector to retrieve all security event logs from your Cisco Firepower Threat Defense (FTD) device, see eStreamer App. For more information, see the Cisco FTD Firewall guide.
-
The Install Collector section displays the following options:
- Amazon Web Services (AWS) — This option is for deploying the XDR Collector to AWS.
- Google Cloud Platform (GCP) — This option is for deploying the XDR Collector to GCP.
- Microsoft Azure — This option is for deploying the XDR Collector to Azure.
-
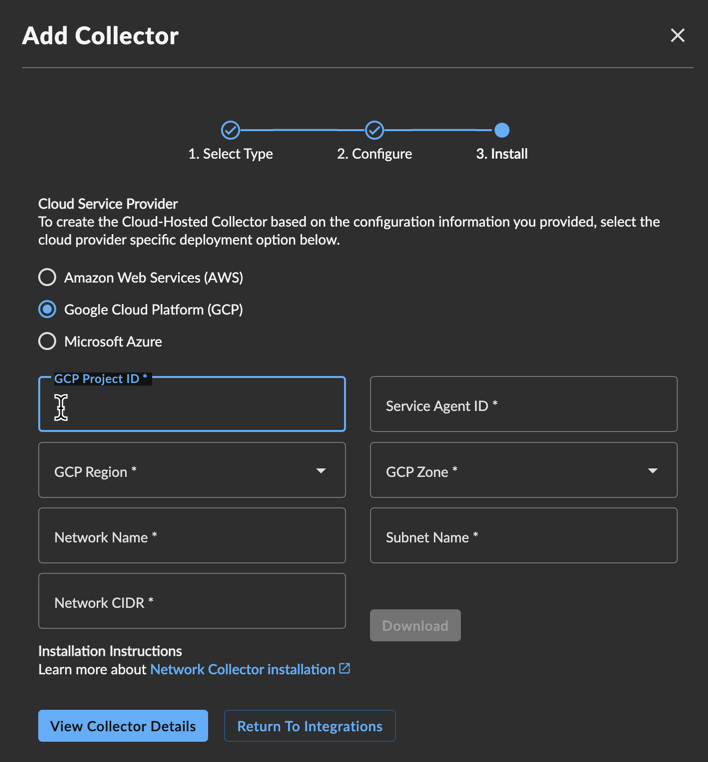
Select Google Cloud Platform (GCP).
- Enter your GCP Project ID to deploy the instance into.
- Enter your Service Agent ID.
- Select the GCP Region and GCP Zone you want to deploy from.
- Specify the Network Name that the instance is part of.
- Specify the Subnet Name that the interface is part of.
- Enter the Network CIDR or network destinations for the firewall rules.
- Select Download to download the GCP template.
GCP Collector
Note
Carefully review the template to ensure it conforms to all relevant network and security policies. Advanced users can extract the GCP template and user-data from the template to incorporate into their own IaC or automation tools.
- In the GCP console, open Cloud Shell using the icon on the top right.
Open Cloud Shell
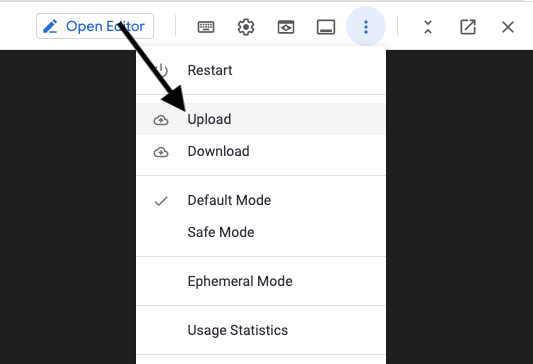
- Select the menu icon and choose Upload to upload the template you downloaded from XDR in Step 13.
Upload Template
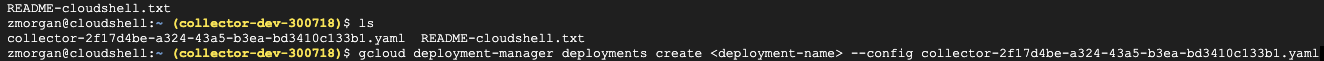
- Apply the template using deployment manager by running:
gcloud deployment-manager deployments create <deployment-name> --config <the file name you just uploaded>
Apply Template
- After the Cloud Shell command reports success, the collector should change status from Provisioning in a little under ten minutes. At this point the collector will be online and ready to receive logs. Confirm the collector status from Integrations > Data Collectors in XDR.
Access Troubleshooting Console ⫘
The Admiral console allows you to access information about a deployed XDR Collector locally. The tools provided within Admiral assist in device setup and troubleshooting of common problems such as network connectivity. For more information, see Admiral Console.
Edit Your XDR Collector Configuration ⫘
Important
Making changes to the XDR Collector configuration of a live system carries the risk of rendering the device inoperable. The XDR Collector makes every attempt possible to rollback to a previous configuration when a configuration change is unsuccessful, but XDR Collector configuration changes should be treated with the same level of caution used for any other kind of change in your environment and you should follow your risk and change management guidelines. Always be prepared to redeploy the device.
Certain configuration parameters of a running and healthy XDR Collector can be changed on a live collector. To edit these parameters, select Actions and choose Edit Collector Configuration from a collector details page. Editable fields include the hostname, proxy settings, and NTP server. If you need to change to the network interface configuration, you must provision a new XDR Collector.
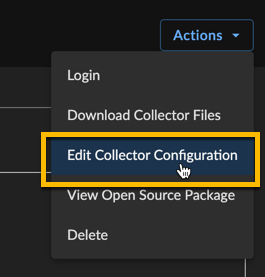
Edit Collector Details
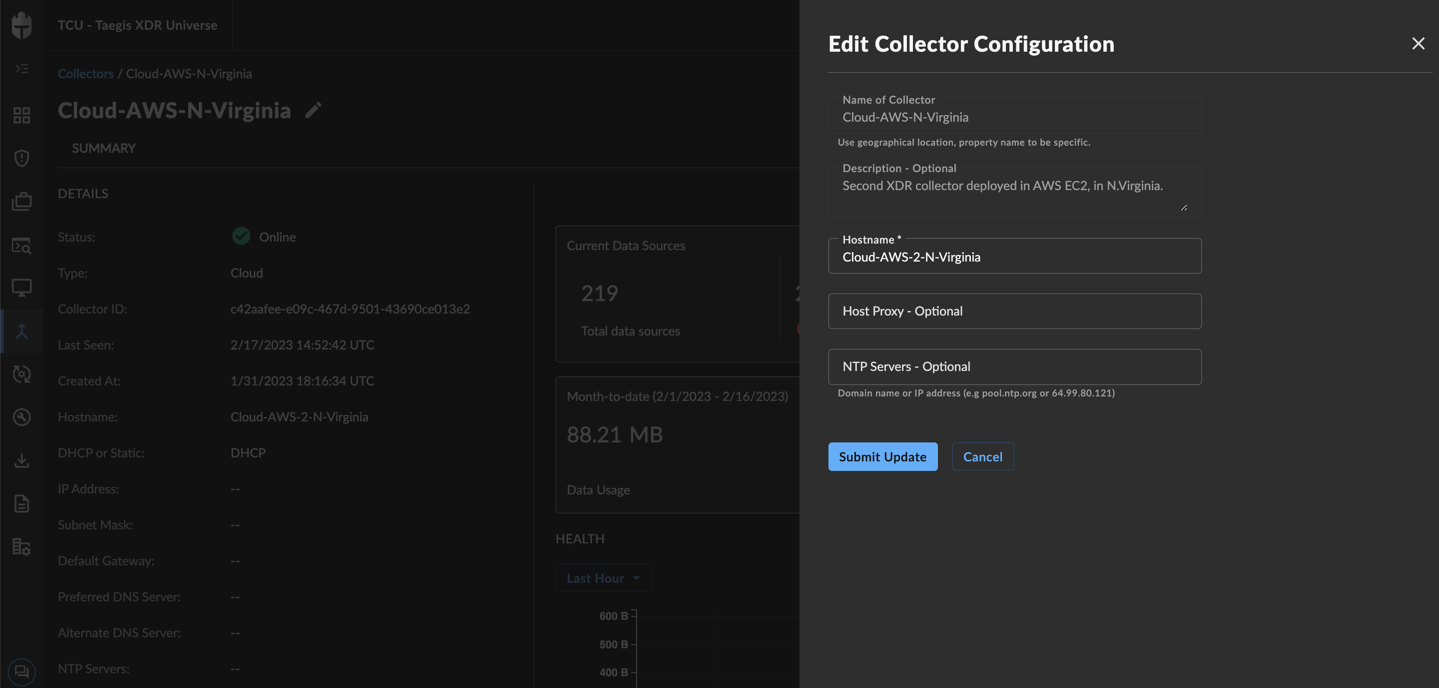
Edit Collector Configuration
After submitting a XDR Collector configuration change, a note appears that indicates the change is pending. The edit action is not available until the change has completed. Pending changes are pushed to your XDR Collector where they are applied and connectivity testing is conducted.

Edit Collector Configuration Pending
If pending changes cause the XDR Collector to be unable to successfully connect, the change is automatically rolled back to the previous configuration and a failure message appears in the banner.

Edit Collector Configuration Rolled Back
A notification displays when a change is successfully implemented.

Edit Collector Configuration Success
In rare circumstances, it’s possible that the configuration change and rollback are both unsuccessful. Example scenarios include, but are not limited to, changes to the underlying network during the change or network connectivity failures to the backend during an inflight change. In these circumstances, a failure banner displays and the XDR Collector must be redeployed.

Edit Collector Configuration Failed
Once the change is complete, download the new GCP Template and apply the updates to your current deployment. This ensures that your new configuration persists if and when a new instance is created.
Manage Integrations Collector Downloads
