SCADAfence
SCADAfence Platform is an industrial network monitoring system that provides cybersecurity and visibility for ICS/SCADA networks. It provides automatic asset discovery and inventory management, threat detection, and risk management. By using a wide range of algorithms, machine learning (ML) and artificial intelligence (AI), it detects anomalies and security events that can compromise availability and affect the safety and reliability of the OT network and its assets.
SCADAfence provides visibility into HMI, Historian Server, and PLC activity by monitoring switch mirror ports. More information on the SCADAfence solution can be found in SCADAfence OT Security Overview.
The following instructions are for configuring SCADAfence to facilitate log ingestion into Secureworks® Taegis™ XDR.
Important
Adding this integration to your XDR tenant requires Taegis™ XDR for OT. Contact your account manager or CSM to acquire the required license.
Connectivity Requirements ⫘
| Source | Destination | Port/Protocol |
|---|---|---|
| SCADAfence Platform | Taegis™ XDR Collector (mgmt IP) | TCP/601 |
Data Provided from Integration ⫘
| Antivirus | Auth | DHCP | DNS | Encrypt | File | HTTP | Management | Netflow | NIDS | Process | Thirdparty | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| SCADAfence | D | D | Y |
Y = Normalized | D = Out-of-the-Box Detections | V = Vendor-Specific Detections
Note
XDR detectors are not guaranteed to be triggered, even if a data source's logs are normalized to a schema associated with a given detector. However, you can create Custom Alert Rules to generate alerts based on normalized data from a data source.
Configure the SCADAfence Platform ⫘
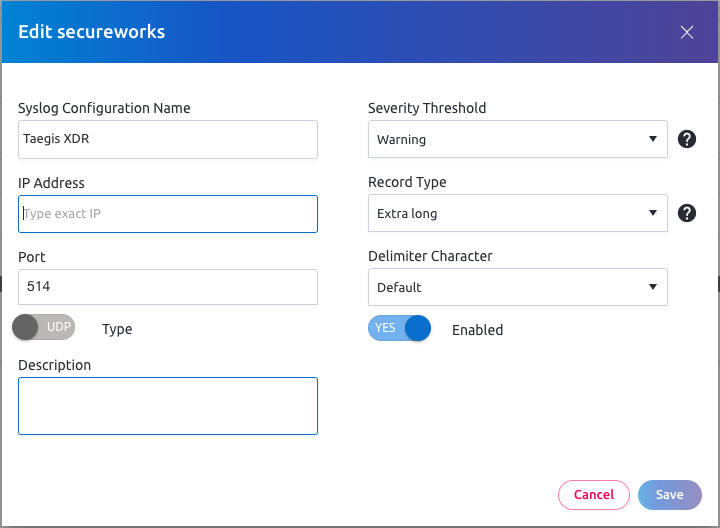
Enter the following information:
| Option | Required Value |
|---|---|
| Syslog Configuration Name | A unique string |
| IP Address | XDR Collector (mgmt IP) |
| Port | 601 |
| Type | "TCP" |
| Severity Threshold | "Warning" |
| Record Type | "Extra long" |
| Delimiter Character | "Default" |
| Enabled | "YES" |
Example Query Language Searches ⫘
To search for netflow events from the last 24 hours:
`FROM netflow WHERE sensor_type = 'SCADAfence' and EARLIEST=-24h`
To search for nids events:
`FROM nids WHERE sensor_type = 'SCADAfence'`
