Imperva Cloud WAF Integration Guide
integrations imperva waf cloud waf
The following instructions are for configuring Imperva Cloud WAF to facilitate log ingestion into Secureworks® Taegis™ XDR. This integration leverages Imperva's Near Real-Time SIEM log integration to send logs to your AWS S3 bucket.
Data Provided from Integration ⫘
The following Imperva Cloud WAF event types are supported by Secureworks® Taegis™ XDR in JSON format.
- Account Takeover Protection
- Audit Trail
- Client-Side Protection
- DDoS Protection
Note
Imperva Cloud WAF event types not listed above are normalized to the generic schema.
| Auth | CloudAudit | DNS | HTTP | Management | Netflow | NIDS | Process | Thirdparty | |
|---|---|---|---|---|---|---|---|---|---|
| Imperva Cloud WAF | D | Y | D | Y |
Y = Normalized | D = Out-of-the-Box Detections | V = Vendor-Specific Detections
Note
XDR detectors are not guaranteed to be triggered, even if a data source's logs are normalized to a schema associated with a given detector. However, you can create Custom Alert Rules to generate alerts based on normalized data from a data source.
Configure the Imperva Cloud WAF to Send Logs to S3 ⫘
Follow the instructions in the Imperva Cloud WAF documentation to configure log forwarding to an S3 bucket.
Choose Amazon S3 as the log destination.
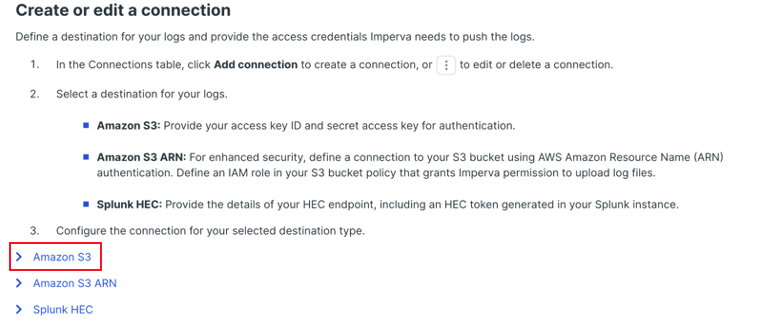
Imperva Cloud WAF Connection
Deploy the XDR Lambda Function in Your AWS Environment ⫘
Follow all steps in these instructions to deploy the Lambda function that will send Imperva Cloud WAF logs from your S3 bucket to XDR.
Note
The above instructions reference CloudTrail; however, the mechanism to send logs from S3 to XDR are data source-agnostic. You must follow all steps in the instructions.
Advanced Search Using the Query Language ⫘
Example Query Language Searches ⫘
To search for http events from the last 24 hours:
FROM http WHERE sensor_type = 'Imperva Cloud' and EARLIEST=-24h
To search for high severity events:
WHERE sensor_type = 'Imperva Cloud' AND severity = 'high'
To search for http events for a specific host:
FROM http WHERE sensor_type = 'Imperva Cloud' AND @ip = 10.10.10.10
Event Details ⫘
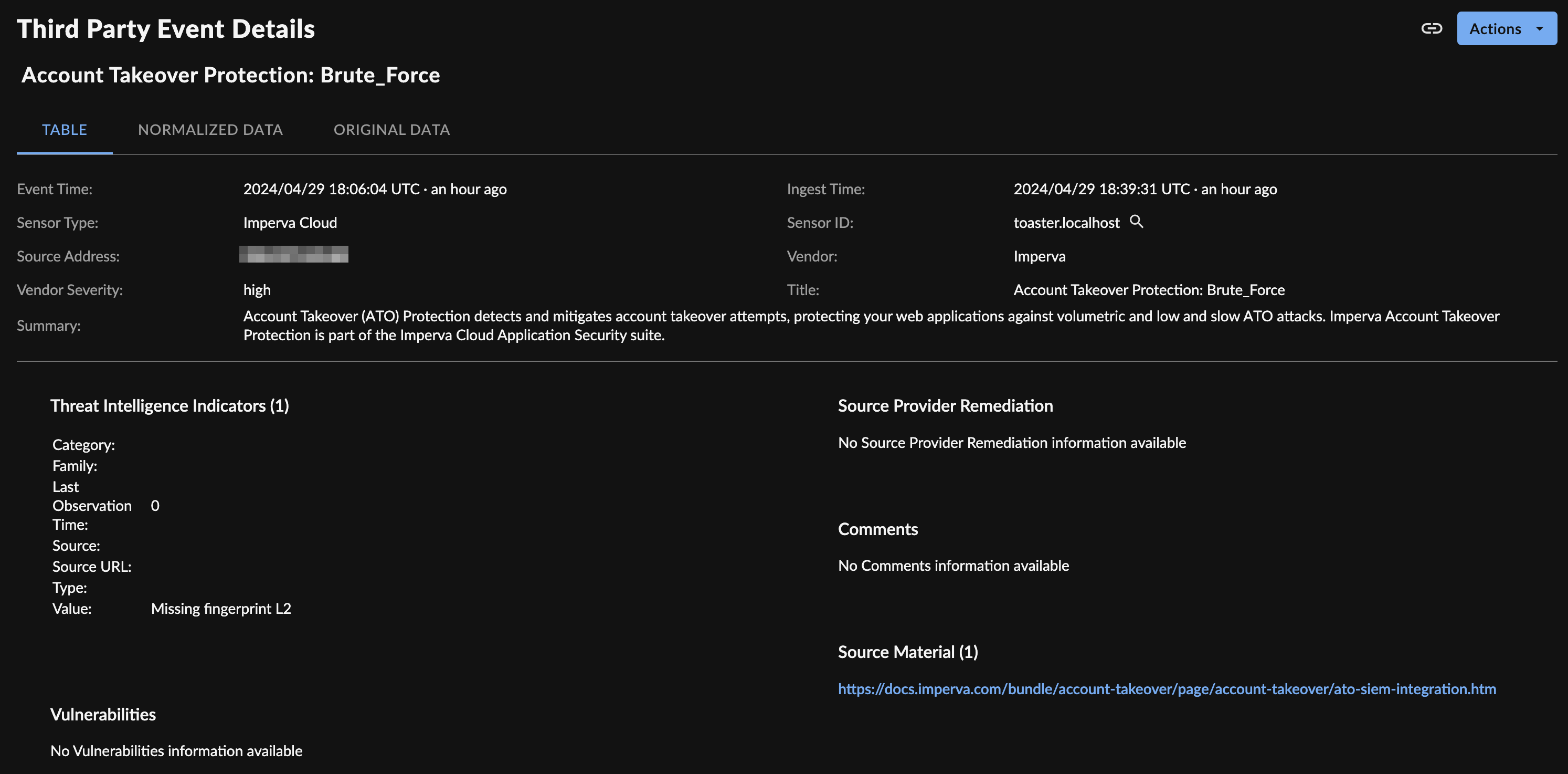
Imperva Cloud WAF Event Details
