File Analysis
The File Analysis Detector identifies malicious files on endpoints with the Taegis™ XDR Endpoint Agent. This detector generates two types of alerts: YARA Rule and Malicious File Found in Telemetry.
YARA Rule ⫘
YARA Rule alerts are triggered when a new filehash is seen in Taegis Endpoint Agent telemetry, the Taegis Endpoint Agent fetches the file from the endpoint, and analyzes the file against CTU-curated YARA rules. If a YARA rule matches, the detector creates an alert with the rule's confidence and severity.
Note
File upload capability requires a Taegis Endpoint Agent version ≥ 1.2.
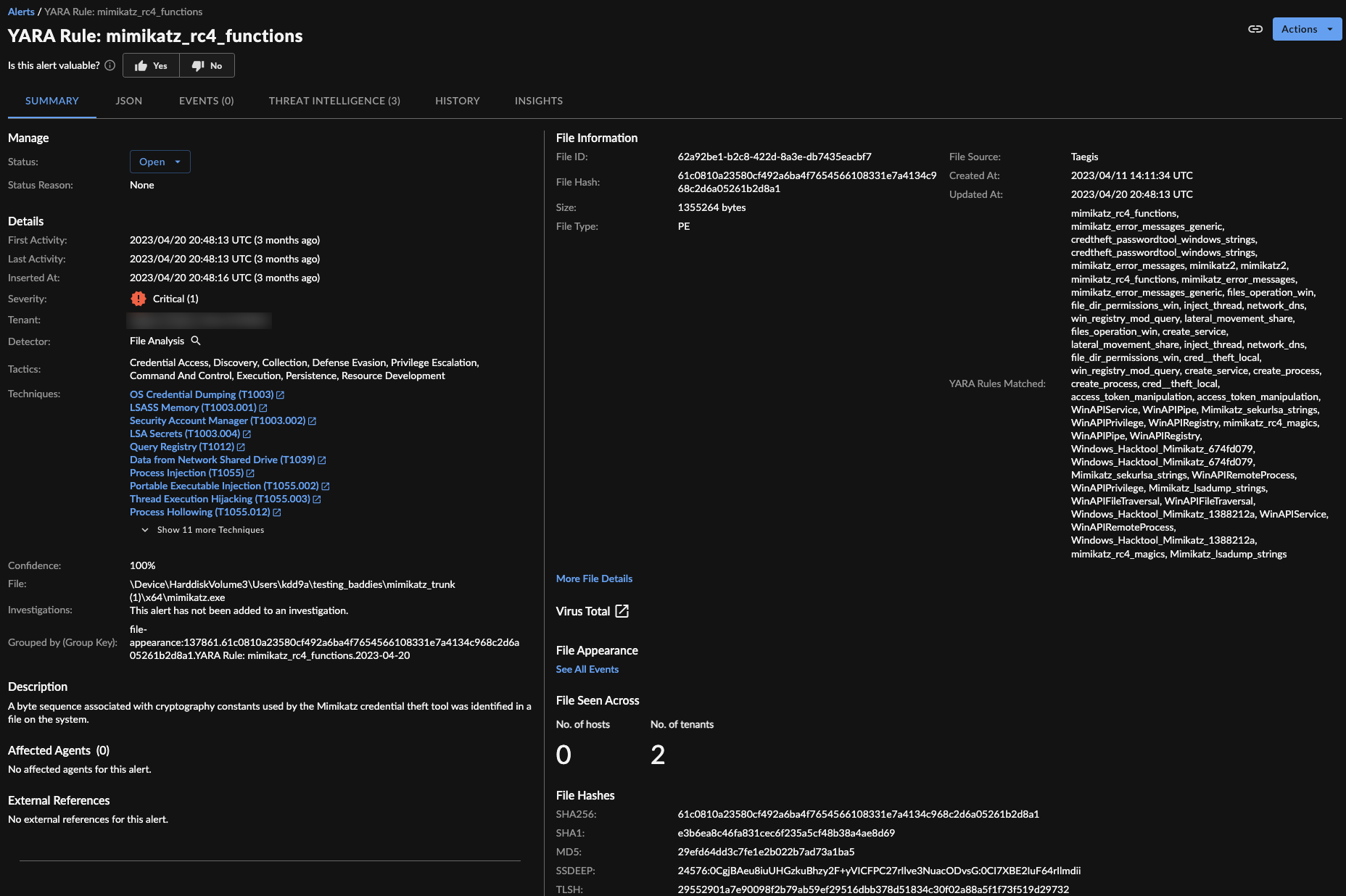
YARA Alert
Analysis
These alerts do not contain related events. Use the See All Events pivot search to find event telemetry surrounding this activity.
Malicious File Found in Telemetry ⫘
The file analysis platform will deem files malicious and future observations of that file's filehash will generate Malicious File Found in Telemetry alerts.
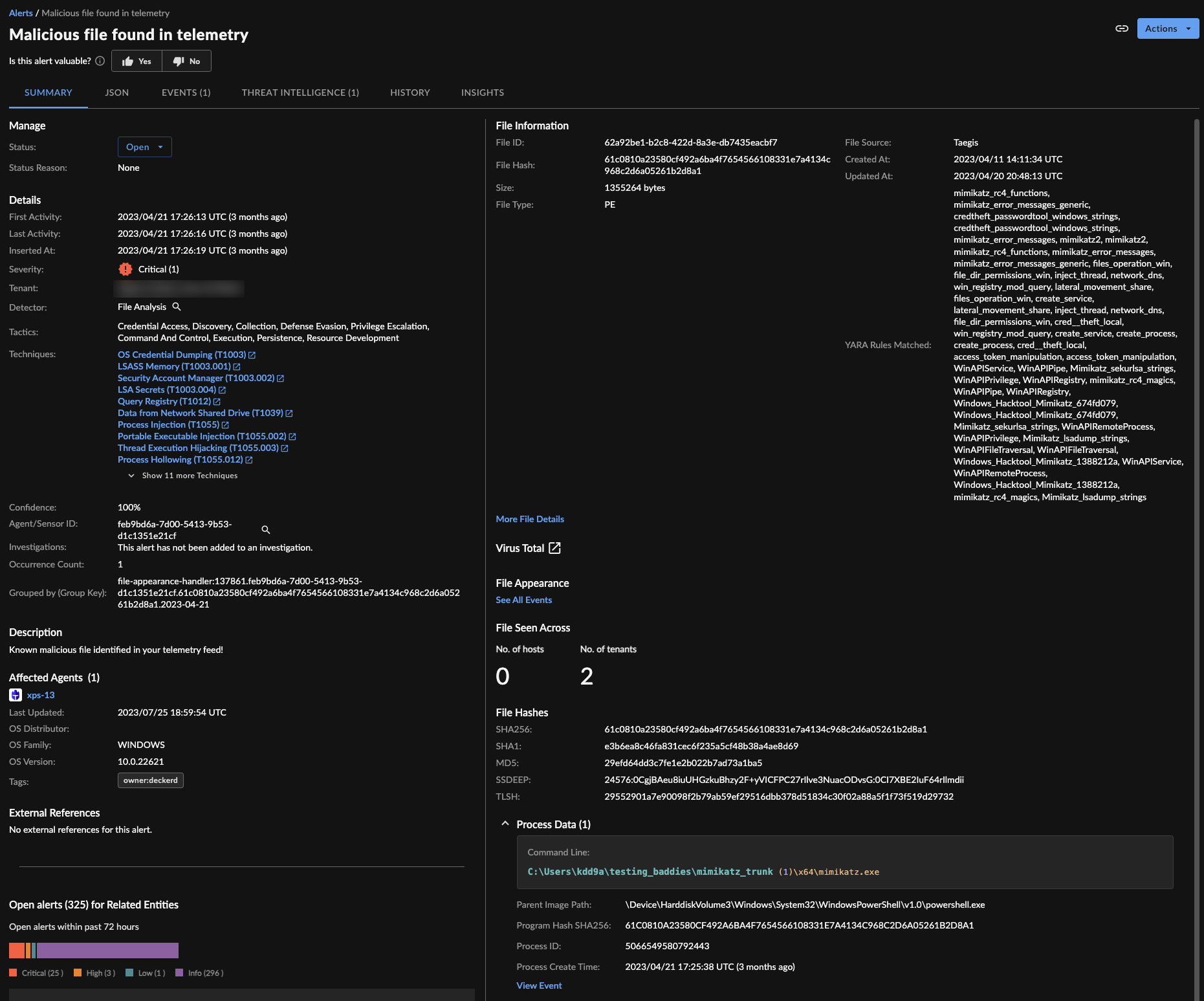
Malicious File Found in Telemetry Alert
Analysis
These alerts contain the telemetry which contained the filehash; however, use the See All Events pivot search to collect more telemetry surrounding this activity.
Inputs ⫘
Taegis Endpoint Agent telemetry where sensor_type: ENDPOINT_TAEGIS and sensor_version: 1.2 and greater; or files fetched from Taegis Endpoint Agents.
Outputs ⫘
Alerts pushed to the XDR Alert Database and XDR Alert Triage Dashboard. These alerts have the detector name File Analysis and detector_id: app:file-analysis.
MITRE ATT&CK Category ⫘
Assigned based on YARA rule
Configuration Options ⫘
Tenants can choose to opt out of file fetching for all of their agents. Follow the instructions at Agent Settings to opt out.
FAQ ⫘
What files are fetched by Taegis Endpoint Agents? ⫘
The file analysis pipeline only analyzes a file one time. The file analysis pipeline calculates hash values for the file and tracks the file based on these hash values.
Fetch requests are sent to Taegis Endpoint Agents based on the following criteria:
- Filehash is seen in normalized telemetry where sensor_type is
ENDPOINT_TAEGIS. The following are common schemas that contain filehashes:process— executed filesprocessmodule— filehash of libraries loaded by different processespersistence— files, commands, host program, and shortcut
- The filehash has not been analyzed before
- The filehash is not on a list of known good filehashes
Is file analysis performed only on certain drives, shared drives, or directory paths? ⫘
The file path is not considered.
Does file fetch place extra burden on the endpoint? ⫘
File fetch requests are rate limited to one file per minute to prevent burdening the endpoint.
How long are fetched files retained? ⫘
The Data Retention Policy applies to fetched files.
How are retained files used? ⫘
Files are retained for future use to analyze and develop new YARA rules as new Threat Intelligence is discovered.
Are fetched files private to my tenant only? ⫘
Yes, files are private within your tenant; however, filehashes are utilized across all tenant telemetry. For example, if a file is analyzed from one tenant and YARA rules deem it malicious, then Secureworks® Taegis™ XDR will alert when that filehash is seen in another tenant's telemetry.
What file types have metadata extracted and viewable within file details? ⫘
XDR file analysis pipeline will analyze all file formats, but metadata is only available for the following file formats: PE files, ELF files, LNK files.
What data about the file is available? ⫘
See File Details.
Can I search for files fetched from my endpoints? ⫘
Search is not available at this time; however, you can search alerts by filehash or filename.
Can I download the file for offline analysis? ⫘
Download is not available at this time.
I downloaded an EICAR test file, but do not see any alerts in Taegis? ⫘
File analysis today is limited to executed files, and EICAR files are generally data at rest. The Taegis Endpoint Agent file analysis is not a replacement for anti-virus on the endpoint, and anti-virus is still required to monitor for malicious files at rest.
How can I test the file analysis pipeline? ⫘
There are two testing options:
Option one: Execute Mimikatz on an endpoint with the Taegis Endpoint Agent that supports file analysis. The file analysis engine will only analyze a file once based on unique filehash, and this file is commonly seen by the platform. Therefore, this test will generate "Malicious file found in telemetry" alerts, which indicate the filehash was seen in telemetry. To do so:
- Download a Mimikatz archive distribution and extract the archive.
- Execute either Win32 or x64 version of mimikatz.exe.
- Exit Mimikatz. There is no need to perform any actions in Mimikatz.
After execution, you should see an alert similar to the following:
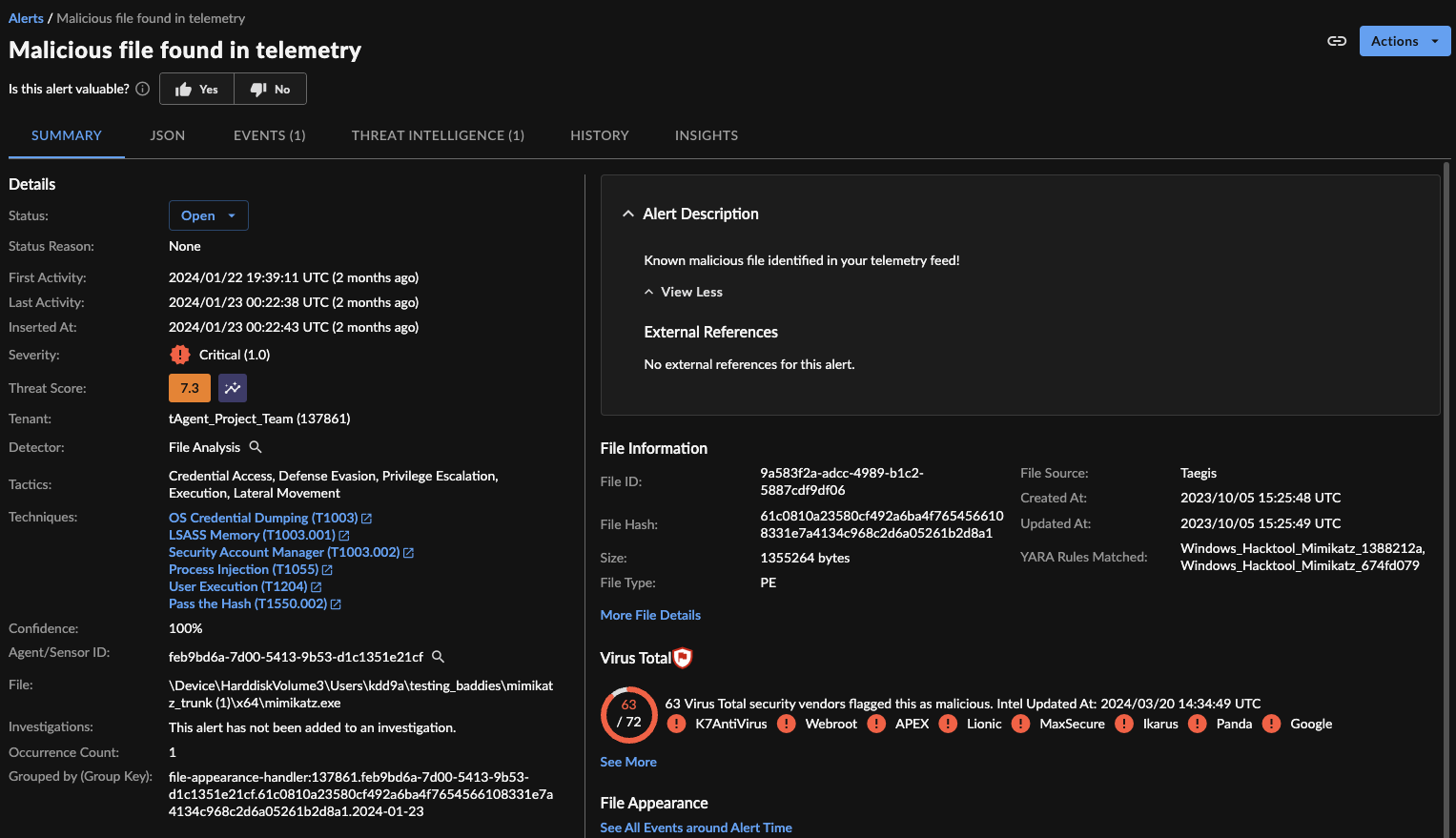
Mimikatz Alert
Option two: Execute file with EICAR String. To do so:
- Open Windows Powershell
powershell.exeand run the following commands to create an executable EICAR file. copy c:\Windows\system32\notepad.exe notepad2.exe$eicar='$EICAR-STANDARD-ANTIVIRUS-TEST-FILE! ' + [guid]::NewGuid().ToString()Add-Content -Path .\notepad2.exe -Value $eicar- Execute
notepad2.exe - Execute
Get-Filehash notepad2.exeand copy the SHA256. - Search XDR advanced search using query
@hash='REPLACE_SHA256_HERE' and Earliest = -1d
This test should result in an info level alert with title "RESEARCH: Yara rule(s) matched"
