Work an Investigation
As you examine alerts and events in Secureworks® Taegis™ XDR, use investigations to gather related information together and share it with your team. Other users in your tenant can view and work on the investigations by making comments, adding related data, changing the status of the investigation, and more.
If you subscribe to Secureworks® Taegis™ ManagedXDR, investigations are also how Secureworks documents, shares, and escalates threat related activity to your organization.
Note
Investigations are retained for the life of your contract. However, by default alert and event data is retained for 12 months and no longer appears in Investigations beyond the retention period. Customers can extend the retention period for an additional fee as outlined in the XDR Data Retention Policy.
Get to the Investigations Page ⫘
Select Investigations from the left-hand side navigation bar to view all investigations in the current tenant, including information about who initially created it and when; the current status; when it was last updated; involved entities; and how many alerts, events, or agents are related.
Tip
Investigations can also be accessed from the Recent Investigations widget on the Alert Triage Dashboard, and the Ongoing Investigations widget on the ManagedXDR Dashboard.
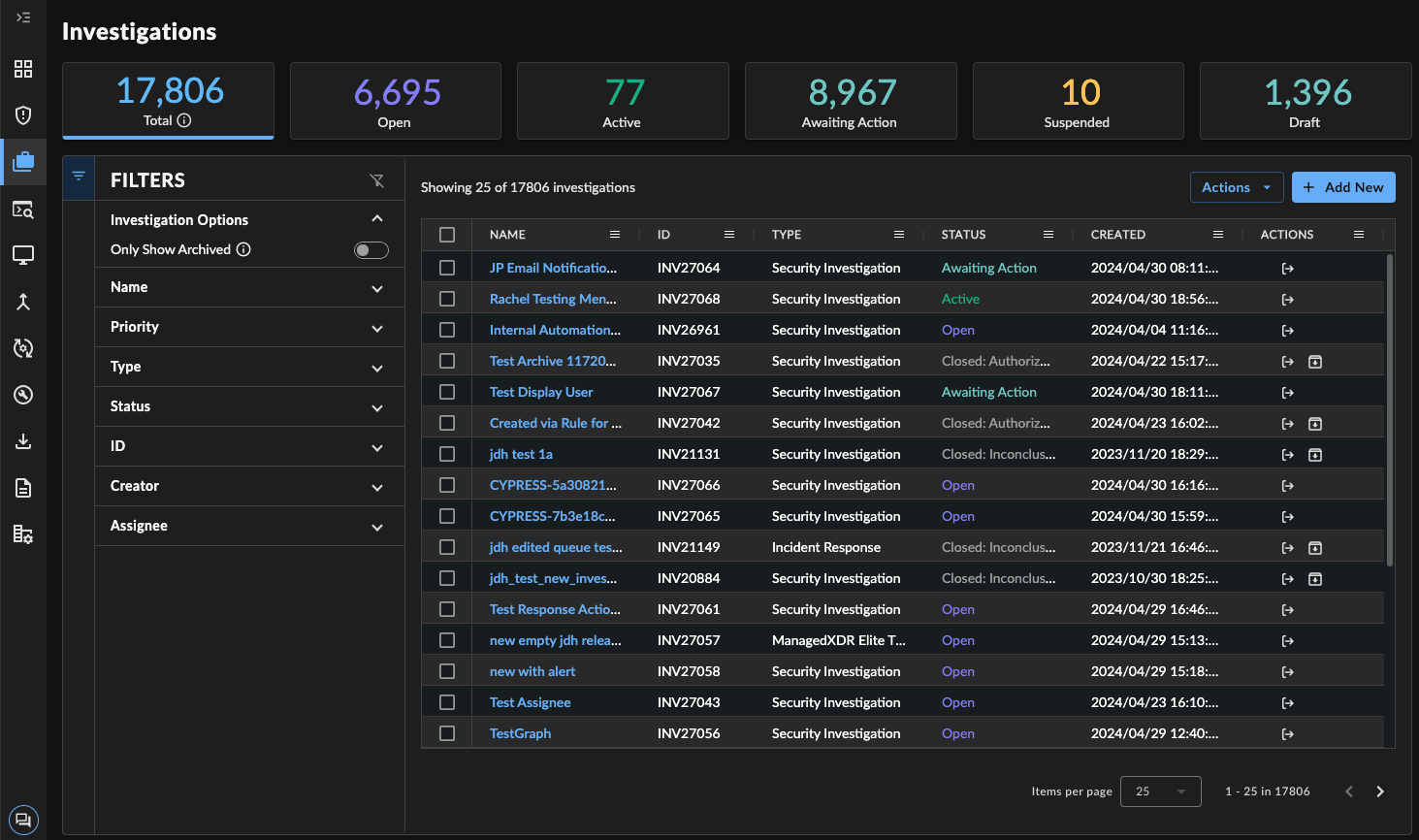
Investigations Page
Filter Investigations ⫘
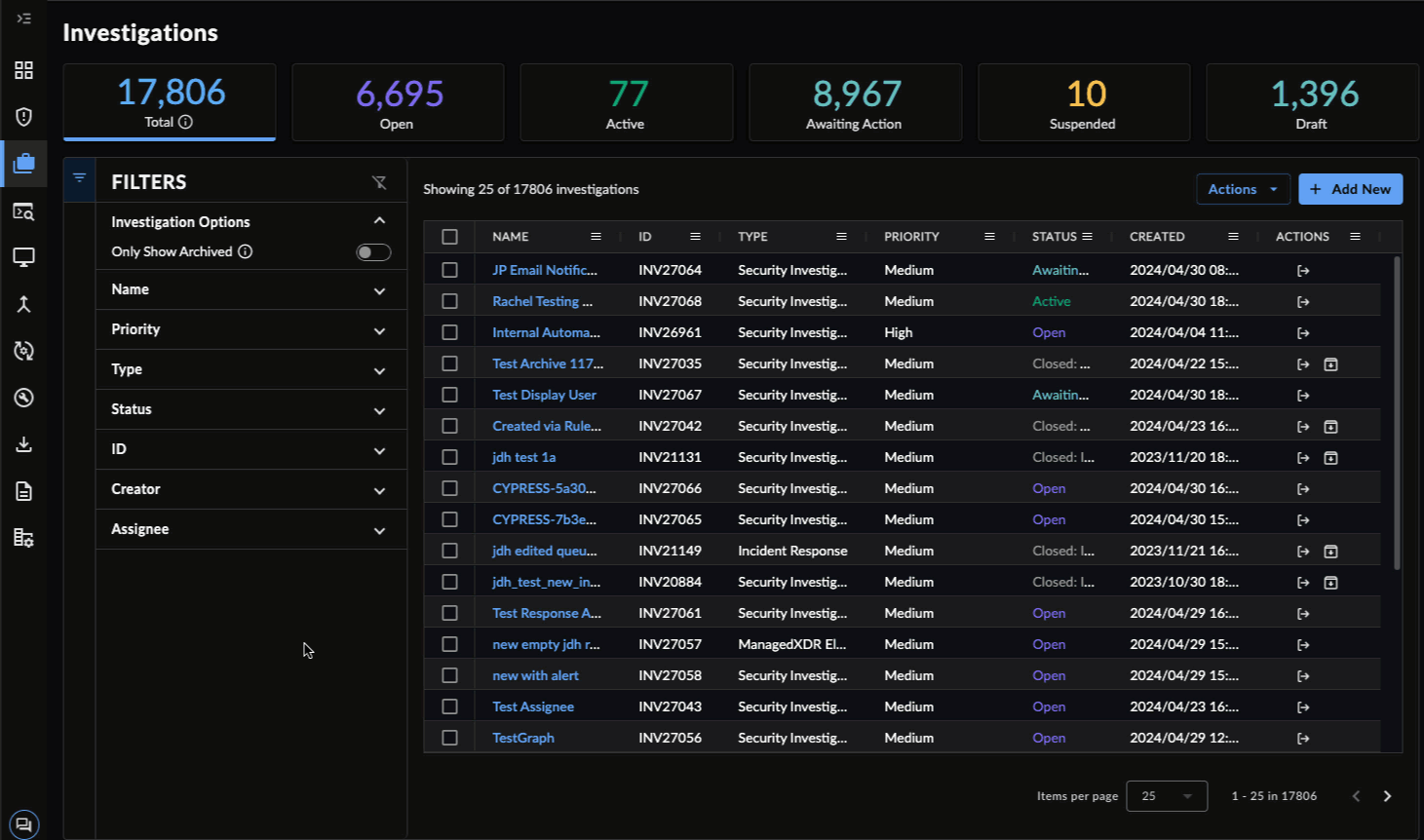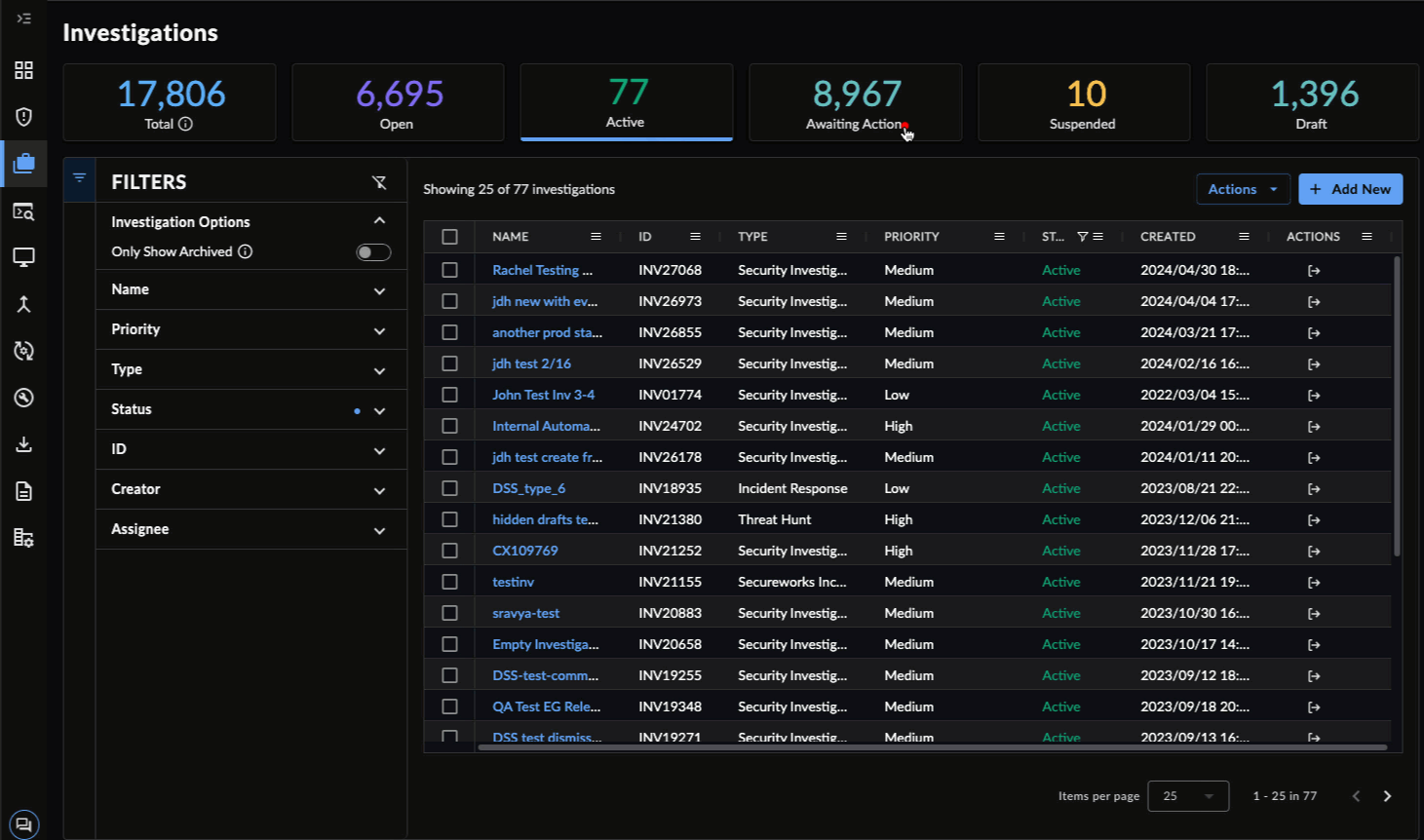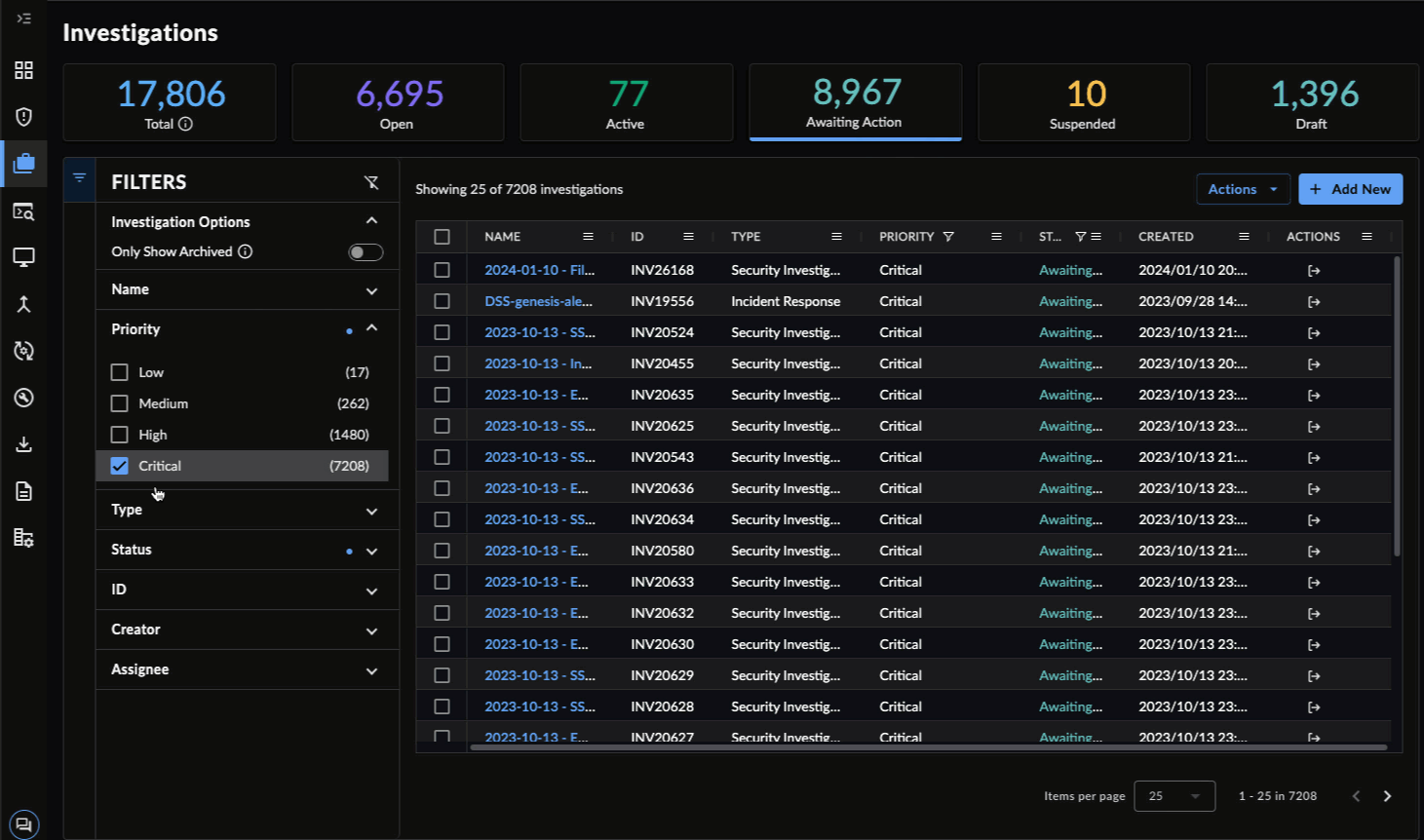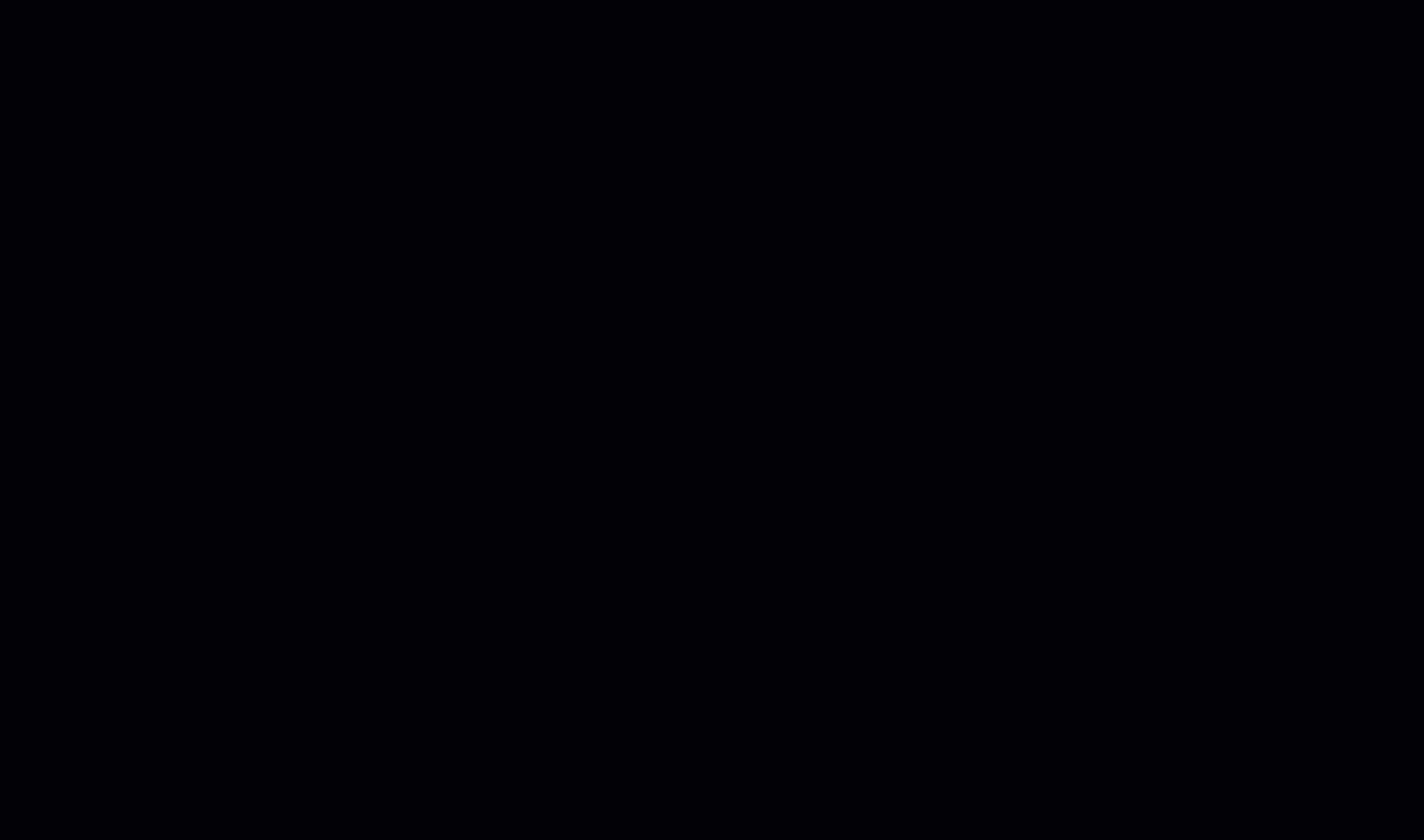
Filtering the Investigations Table
To filter the table of investigations:
- Select the status cards above the Investigations table, which provide a count of all investigations by that status. The number indicates how many investigations are in that state.
- Total — All investigations, except those that have an Archived status.
- Open — Investigations with an Open status.
- Active — Investigations with an Active status.
- Awaiting Action — Investigations with an Awaiting Action status.
- Suspended — Investigations with a Suspended status.
- Draft — Investigations still in a Draft state.
- Use the collapsible filter menu at the left of the table to narrow down the list of matching investigations.
- As you select filters, the table updates dynamically and the count of results reflects the updated filtered list.
- Select the Reset Filter Selection icon at the top right of the filter menu to clear all filters at once.
- The open or close state of the menu is saved as a user preference when you navigate away.
- Edit and filter the columns in the table by selecting the menu icon at the right of a column header.
- Select the Only Show Archived filter to update the table with archived, closed, and dismissed investigations. See Archived Investigations for more information.
Manage an Investigation ⫘
Users with the required user role can take the following actions on investigations:
- Start a New Investigation
- Add to an Existing Investigation
- Hand Off an Investigation
- Attach Files to an Investigation
- Comment on an Investigation
- Explore an Investigation in Detail with Entity Graph
- Close an Investigation
- Archive an Investigation
Note
The following affects how an investigation can be edited:
- Investigations with any Closed status are read only, except for the Status field and the Archive action.
- Draft investigations that have been dismissed are read only, except for the Archive action.
- Archived investigations are read only, except for the Unarchive action.
Select an investigation title anywhere throughout XDR to view its details. You can rename the investigation by selecting the Edit icon next to the name.
The full details of an investigation are divided into three tabs: Summary, Evidence, and History.
Investigation Summary ⫘
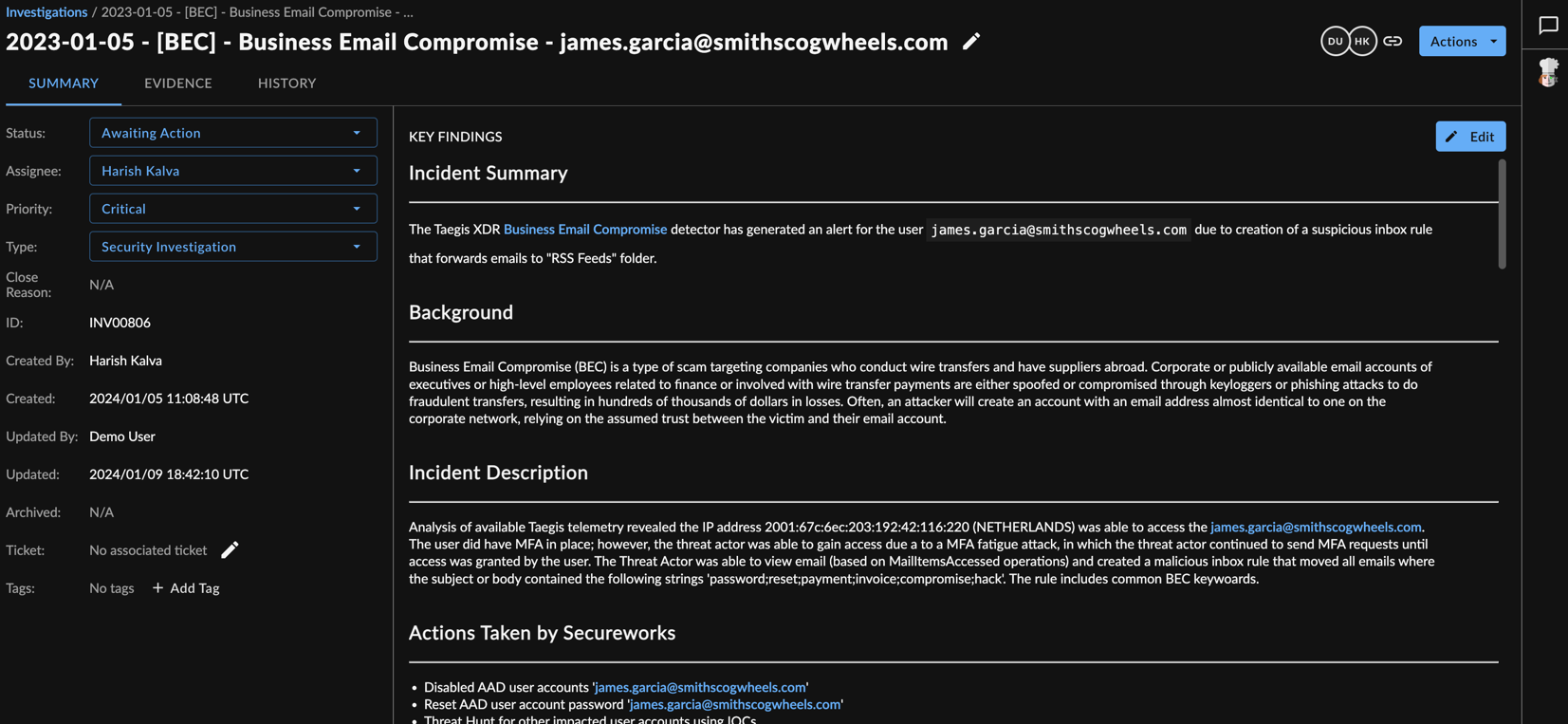
Investigation Summary Tab
The Summary tab includes the basic information about the investigation:
- Status — The current status of the investigation. See Investigation Status for more information.
- Assignee — To whom the investigation is currently assigned.
- Priority — An indication that highlights the importance and potential impact of the activity to your organization. See Investigation Priority for more information.
- Type — The category of investigation. See Investigation Type for more information.
- Close Reason — The optional reason entered when the investigation was closed, if applicable. See Close an Investigation for more information.
- ID — The unique identifier number of the investigation (e.g. INV00001).
- Created By — The user who originally created the investigation.
- Created — The date and time that the investigation was created.
- Updated By — The user who last updated the investigation.
- Updated — The date and time that the investigation was last updated.
- Archived — The date and time that the investigation was archived, if applicable.
- Ticket — A reference number from your organization or your ticketing system, like Zendesk.
- Tags — Tags that can be added to the investigation.
- Key Findings — A text box that investigators can use to record their analysis. See Investigation Key Findings for more information.
Investigation Status ⫘
The status of an investigation changes as the investigation is triaged, worked, and resolved, enabling you to track your team’s workflow.
| Status | Description |
|---|---|
| Open | The investigation has been created. |
| Active | The investigation is underway. |
| Awaiting Action | Some additional action is required for the investigation to continue. See Change Investigation to Awaiting Action for more information. |
| Suspended | The investigation has been paused. |
| Closed: Confirmed Security Incident | Your organization’s systems or data have been compromised or measures put in place to protect them have failed. The investigation is completed. |
| Closed: Authorized Activity | The activity is authorized or expected. The investigation is completed. |
| Closed: Threat Mitigated | The threat associated with the security incident has already been mitigated by a security control. The investigation is completed. |
| Closed: Not Vulnerable | The targeted system is not vulnerable to the exploit in question and therefore the investigation does not constitute a security incident. The investigation is completed. |
| Closed: False Positive Alert | The activity the alert indicated did not occur. This is not a security incident, so the investigation is closed as a false positive. |
| Closed: Inconclusive | The activity’s root cause has not been identified and there is no further activity detected. The investigation is completed. |
| Closed: Informational | Analysis conducted of the activity did not lead to any notable findings. The investigation is completed. |
Note
Investigations may have a Draft status while they are triaged and are not viewable from Investigations in XDR. Upon verification of need to escalate the investigation, the Draft status is removed and the investigation is escalated and viewable.
Tip
If you subscribe to ManagedXDR, your ManagedXDR Dashboard relies on the resolution of investigations to generate the included statistics.
Investigation Priority ⫘
Use the investigation priority to highlight the importance and potential impact to your organization, as well as to determine the order in which each investigation should be addressed.
| Priority | Description |
|---|---|
| Critical | Activity that poses an imminent threat that requires immediate attention. May be a ransomware outbreak, threat actor hands on keyboard, data exfiltration, credential dumping, internal domain and network enumeration, persistence creation and execution, etc. |
| High | Potentially significant activity that requires prompt attention; for example, host infection, stolen credentials, successful exploitation, etc. |
| Medium | Activity that may escalate impact, such as login failures, vulnerability scanning, etc. |
| Low | Activity unlikely to cause impact, like instant messaging, adware, port scanning, etc. |
Investigation Type ⫘
Categorize the different types of investigations that your organization is conducting.
| Type | Description |
|---|---|
| Security Investigation | The default type for investigations identified via alerts in Taegis XDR. |
| Incident Response | Used to collect evidence and investigation details related to Incident Response engagements. |
| Threat Hunt | Used for investigating unidentified, hidden threats. |
| OT Investigation | Used for OT-related investigations. |
Secureworks may also use the following investigation types that are only available to Secureworks users.
| Type | Description |
|---|---|
| ManagedXDR Threat Hunt | ManagedXDR Service monthly proactive Threat Hunt. |
| CTU Threat Hunt | Threat Hunting performed by the Secureworks Counter Threat Unit (CTU™). |
| ManagedXDR Elite Threat Hunt | Used as part of the ManagedXDR Elite Threat Hunting Service. |
| Secureworks Incident Response | Used to automate escalations to Secureworks IR. |
| Unlimited Response | Used as part of Unlimited Response for ManagedXDR customers. |
| ManagedXDR OT Investigation | Used for OT-related investigations as part of the ManagedXDR for OT Service. |
Investigation Key Findings ⫘

Updating the Key Findings on an Investigation
The Key Findings text box provides a space for you and your collaborators to record your analysis of the investigation. Select Edit to write your own report as the investigation develops.
Upon creating a new investigation, you can choose whether the Key Findings are blank or you can choose the Security Investigation template. This template auto-populates the Key Findings with the following sections:
- Incident Summary
- Recommendations
- Technical Details
- References
Tip
Key Findings supports Markdown formatting so you can easily format your investigation and findings.
Investigation Evidence ⫘

Investigation Evidence Tab
The Evidence tab presents all of the gathered documentation related to the investigation in one place and includes the following sub-tabs:
- Entities — All entities extracted from the events that are part of the investigation. Entities are data that played a role in the incident, including usernames, hostnames, IP addresses, and files. See Entities for more information.
- Alerts — Alerts added to the investigation. The first alert(s) used to start the investigation have a flag icon indicating they are Genesis Alert(s).
- Events — Events added to the investigation. The first event(s) used to start the investigation have a flag icon indicating they are Genesis Event(s).
- Agents — Devices affected by the alerts or events in the investigation.
-
Searches — Search queries linked to the investigation. Select one to open the search.
Note
Removing a search query from an investigation does not delete the search query itself; it merely unlinks the two.
-
Attachments — View and manage file attachments related to the investigation. 2GB max file size.
Entities ⫘
From the table in the Entities sub-tab, select an entity name to open the entity details side drawer on the right. The entity details include additional information about the entity depending on the type, such as when the entity was first seen and last seen, related entities, related alerts, and threat intelligence, if available.
Tip
Select Entity Graph from the top right of the investigation to launch Entity Graph and visually explore the investigation‘s associated entities and their relationships and details. See Explore an Investigation in Detail with Entity Graph for more information.
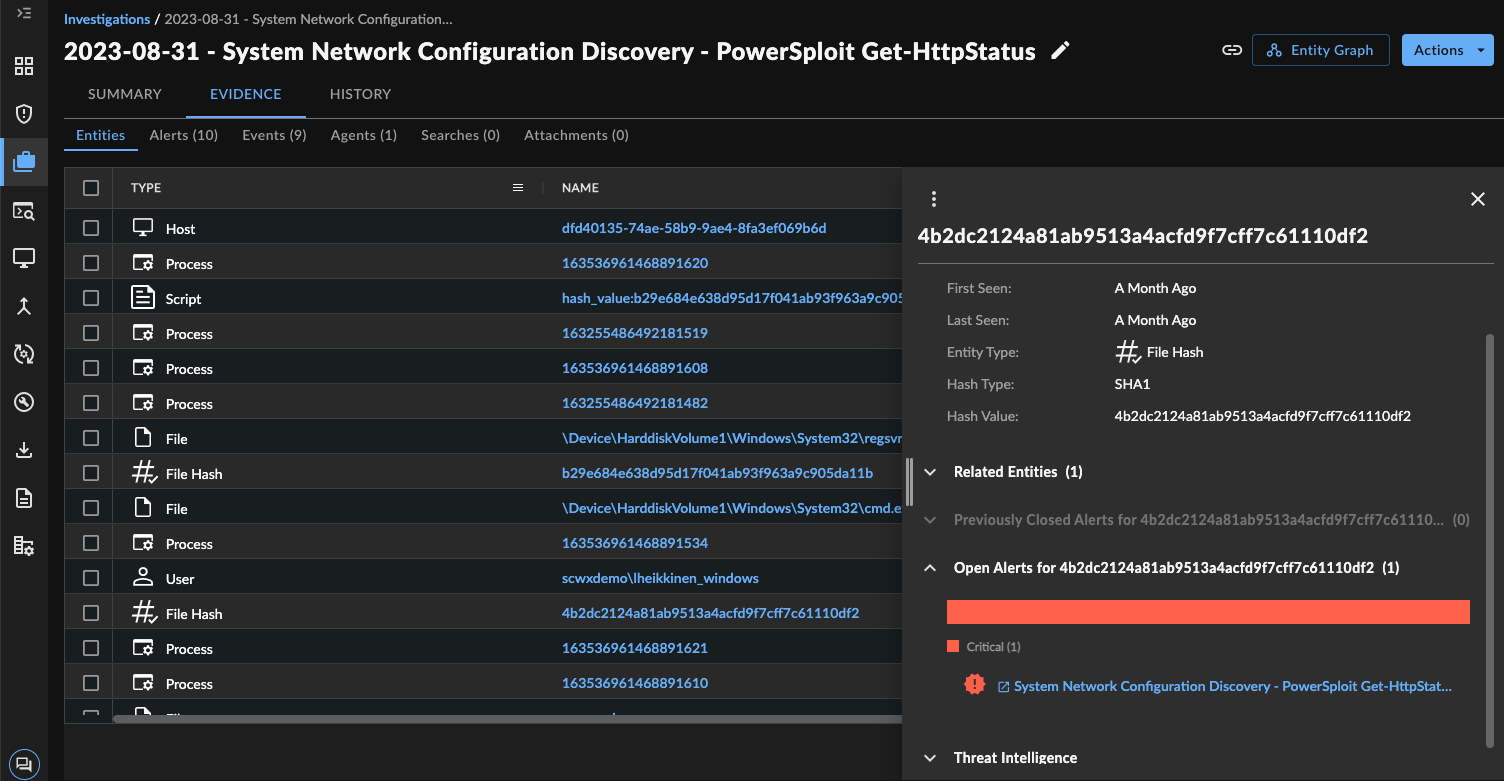
Entities Sub-Tab
Sort and Filter Entities ⫘
To customize the Entities table:
- Select the menu icon next to a column header to pin, autosize, and reset columns.
- Choose the filter icon and enter text or use the checkboxes to filter the content of that column.
- Choose the column icon to choose which columns appear in the table.
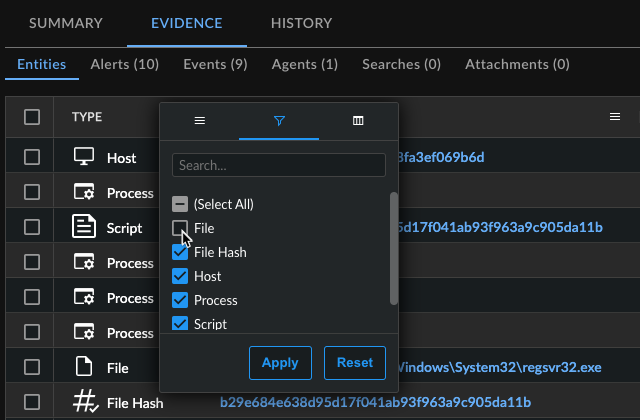
Entities Table Options
Take Response Actions on Entities ⫘
If relevant automations have been configured in your tenant, you can perform response actions on an entity. Select the vertical ellipses from either the Actions column of the Entities table or from an entity details side drawer.
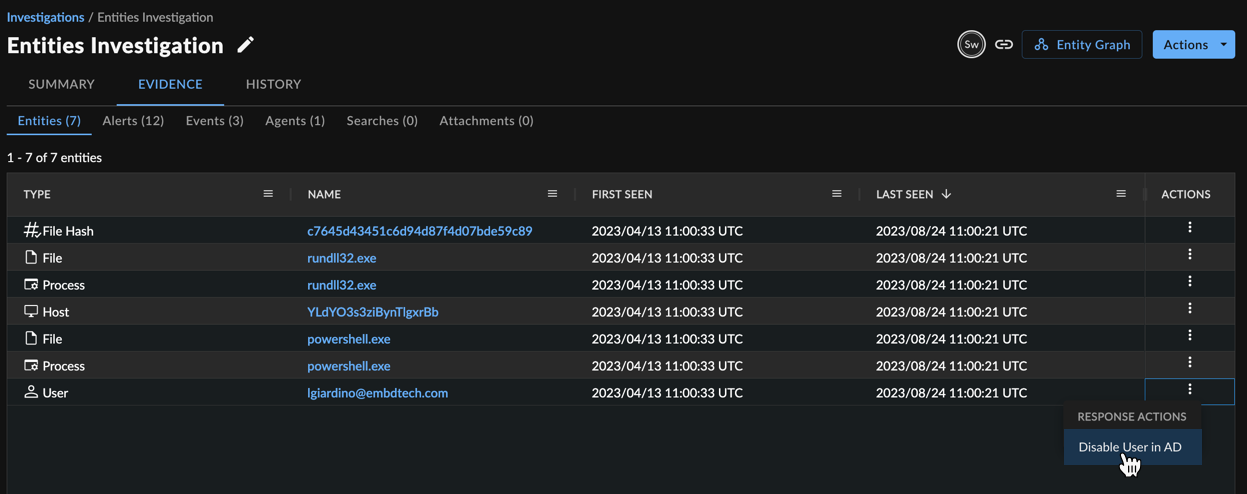
Entities Table Actions
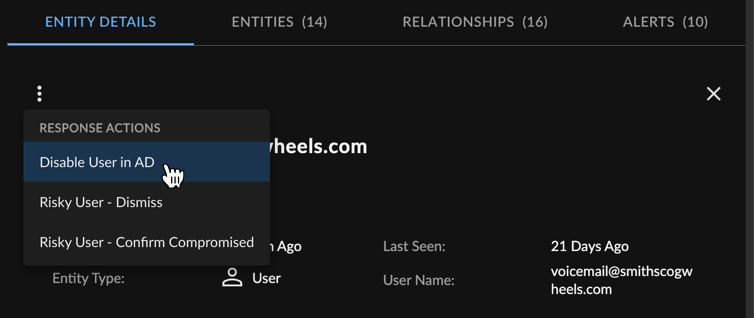
Entity Details Actions
Tip
You can also take response actions on entities from the Entity Graph. See Explore an Investigation in Detail with Entity Graph.
Investigation History ⫘
Note
The History tab replaces the Investigation Timeline tab and includes the timeline, audit logs relocated from the History sub-tab of Evidence, and execution history of related playbooks.
The History tab presents data related to the history of the investigation in one place and includes the following sub-tabs:
Timeline ⫘
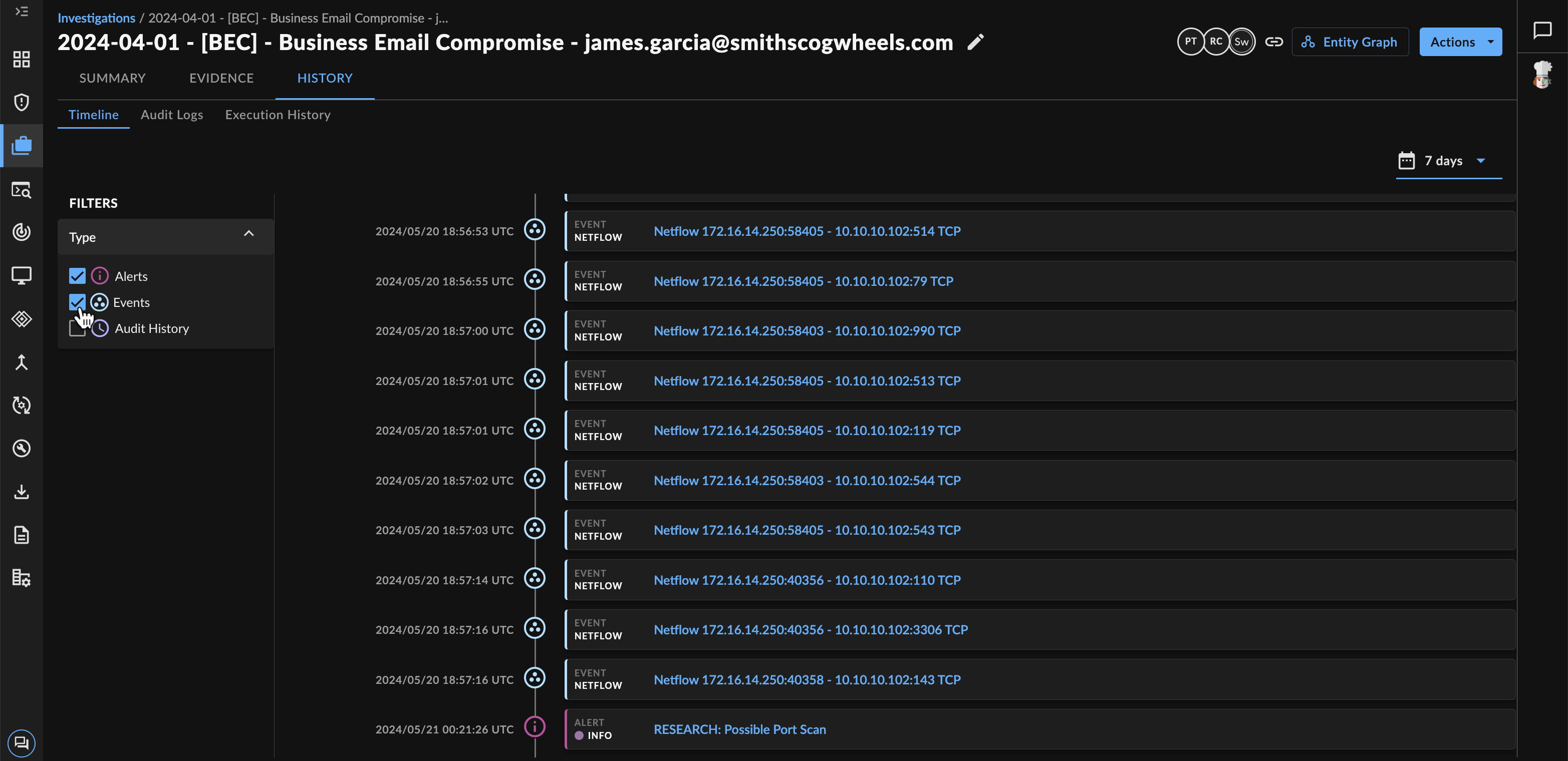
Exploring the Investigation Timeline
The Timeline tab presents a narrative of the investigation by mapping out the various investigation alerts, events, and actions based on the time each activity took place, so you can visualize the scope of the investigation.
- By default, the timeline includes all alerts, events, and audit history actions for the Last 7 Days. Use the date/time picker to change the time frame.
- Use the filters to include or exclude by activity type: Alerts, Events, and/or Audit History.
Note
The investigation timeline only supports alerts that were created since the new Alerts interface became generally available.
Audit Logs ⫘
The Audit Logs sub-tab presents a table of audit logs related to the investigation.
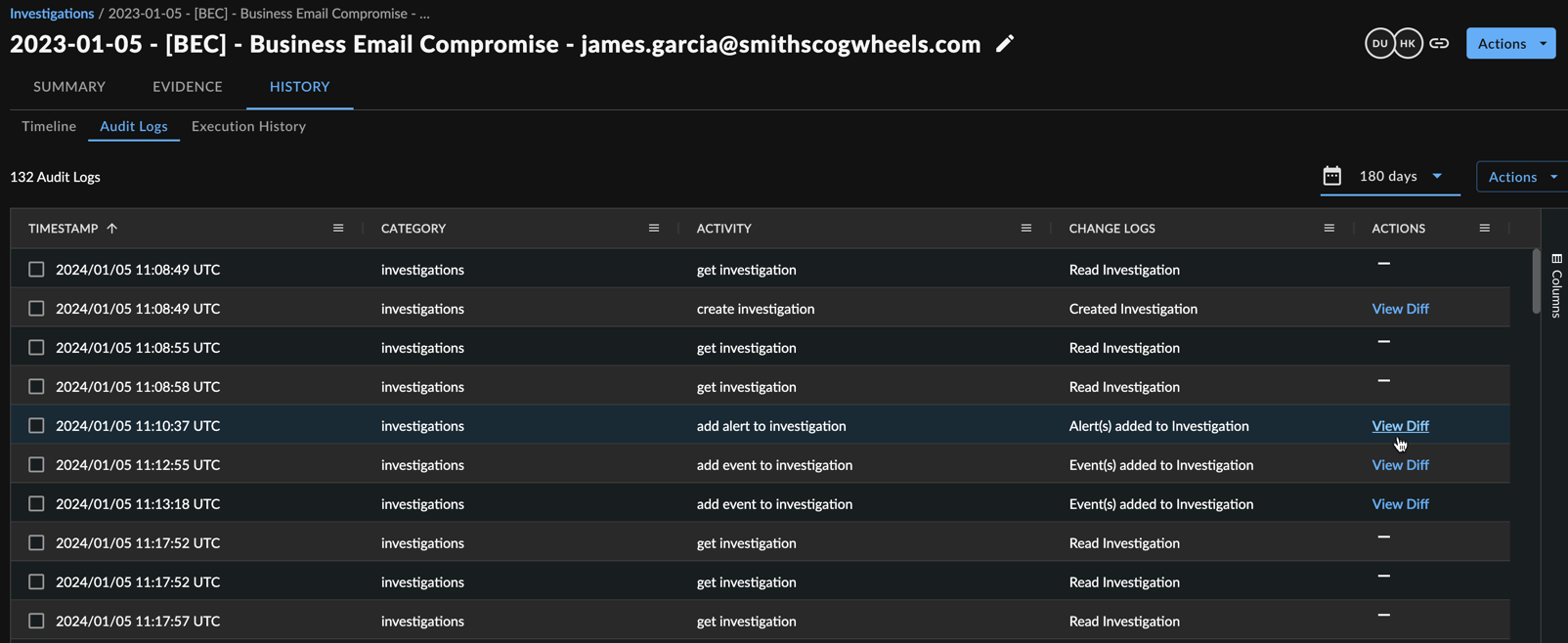
Investigation Audit Logs
Execution History ⫘
The Execution History sub-tab presents a history of playbook executions related to the investigation. Select a row to expand and view more details, or select the Open in New Tab icon at the right of a row to open the playbook execution log.
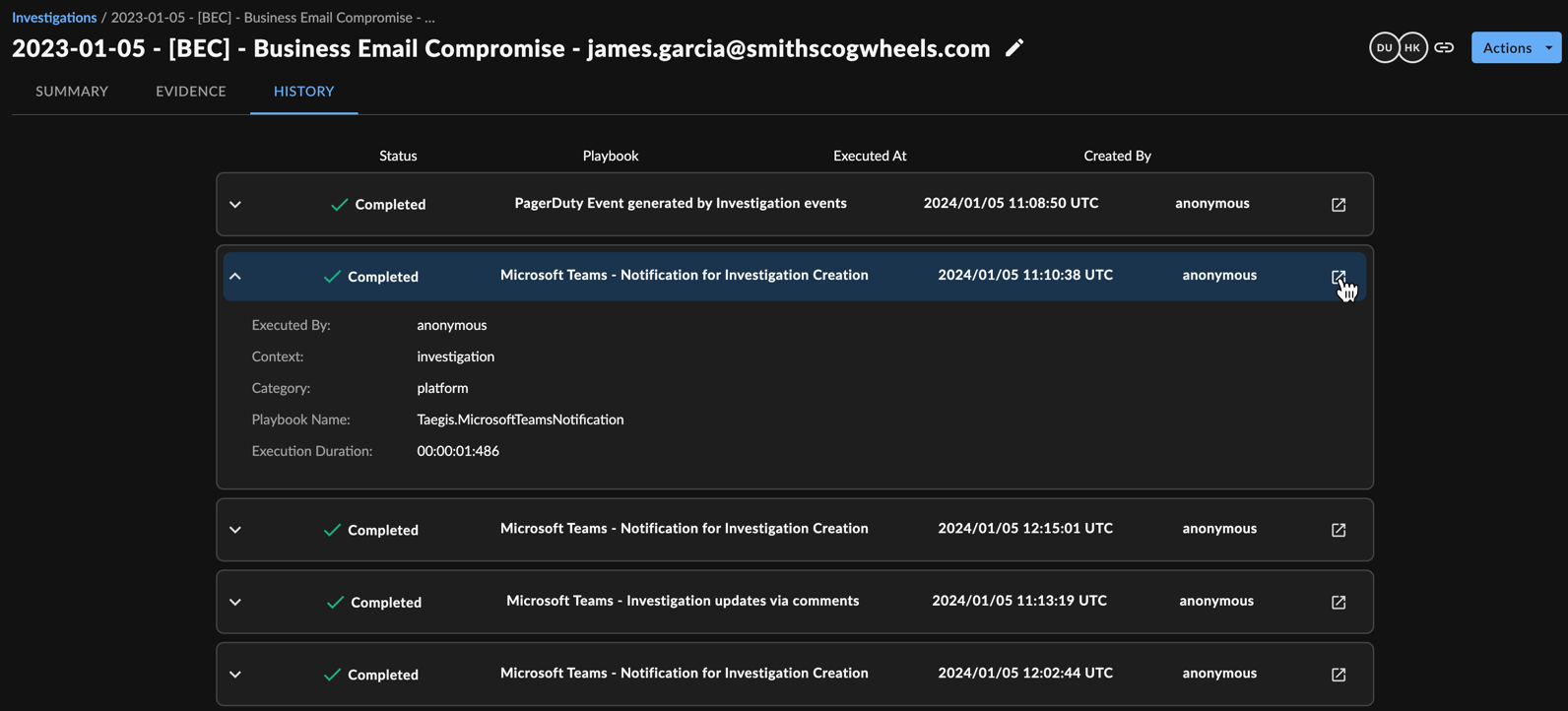
Investigation Execution History
Explore an Investigation in Detail with Entity Graph ⫘
To deep dive into the investigation‘s associated entities and explore their relationships and details, select Entity Graph from the top right of the investigation to launch Entity Graph.
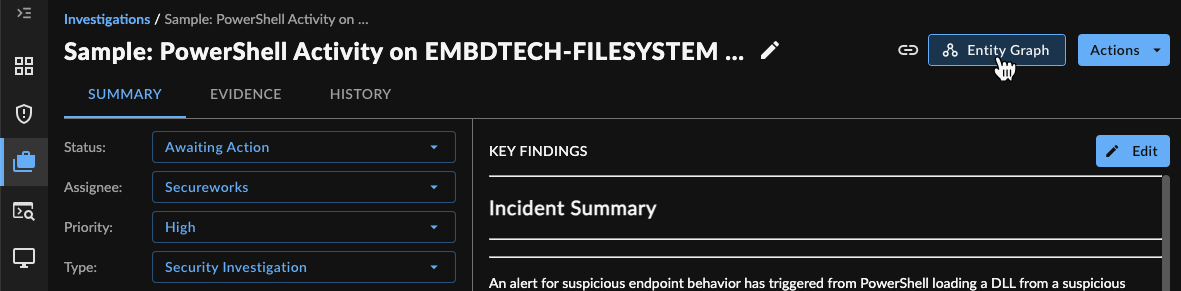
Open Entity Graph
Tip
You can also launch Entity Graph by selecting the Entity Graph icon from the Actions column of the Investigations table.
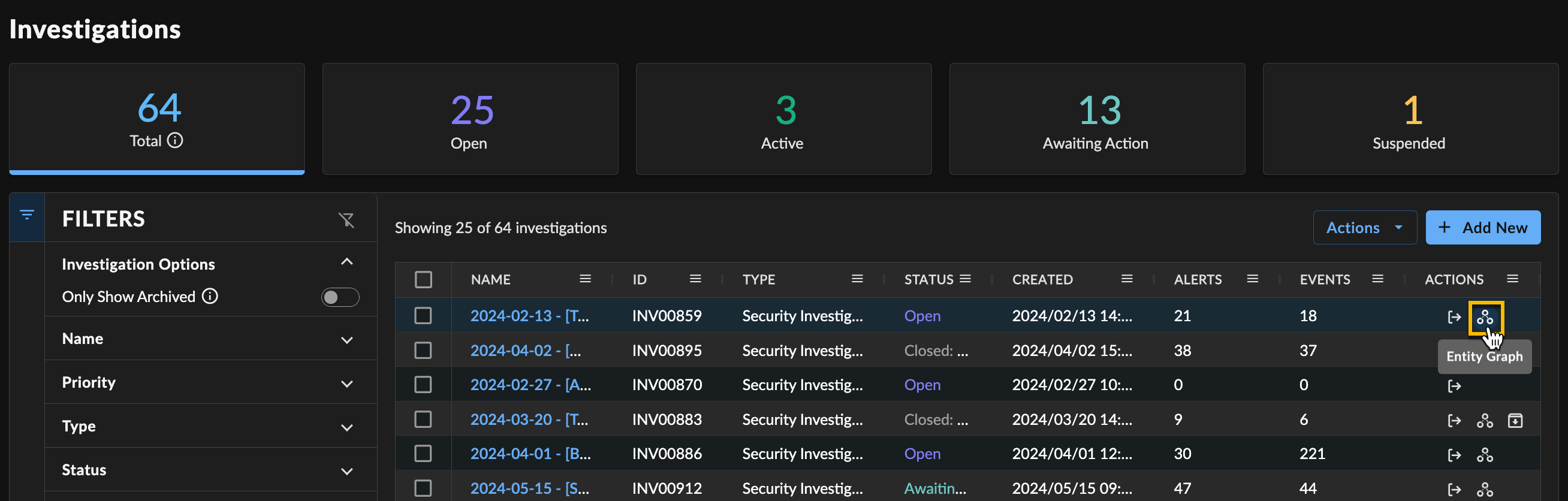
Open Entity Graph from Investigations Table
Add Comments to an Investigation ⫘
You can view all the comments made on an investigation in the collapsible sidebar.
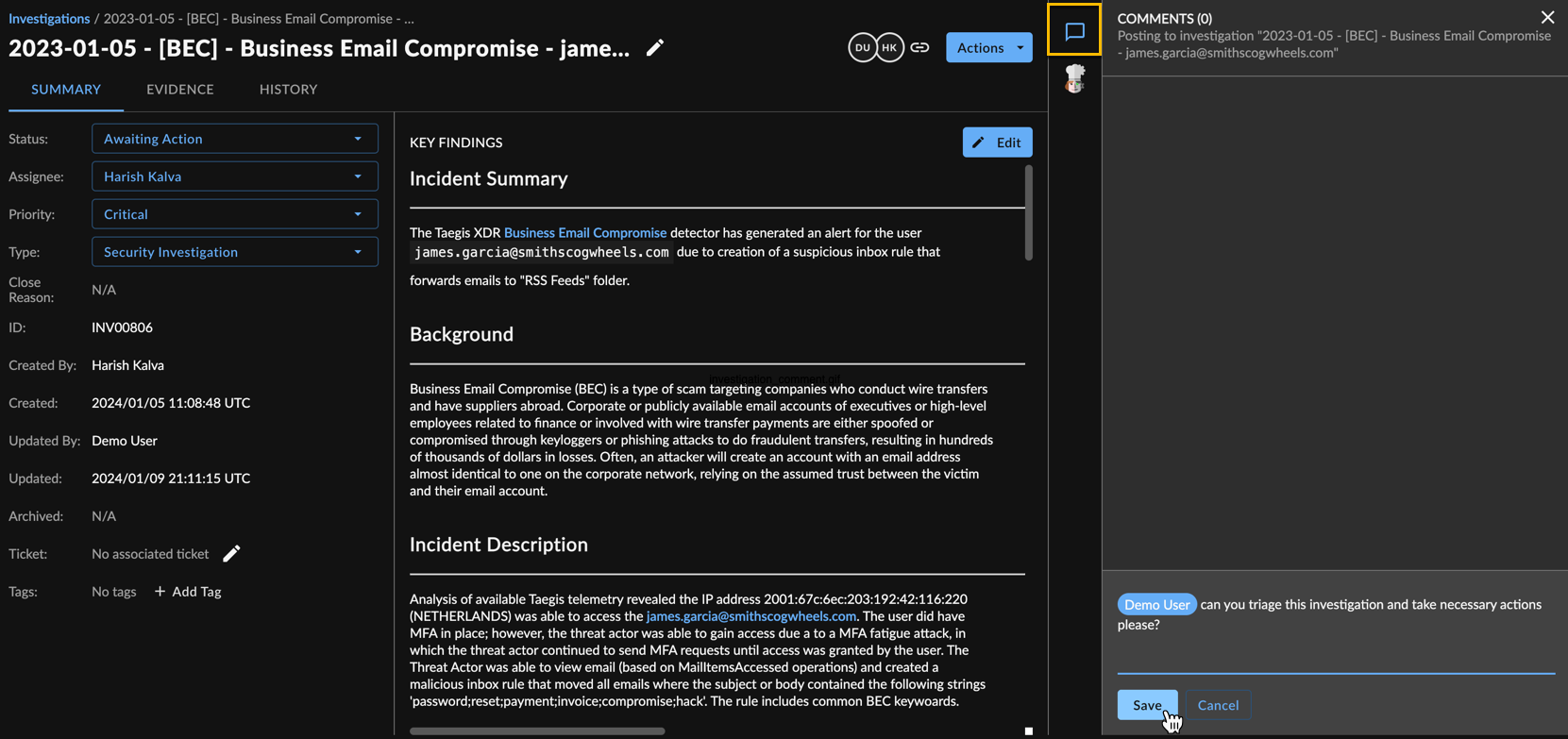
Adding Comments to an Investigation
To add your own comments to an investigation, follow these steps:
- Open the investigation details page.
- Select the comment icon in the right-hand utility tray.
-
Type your message.
Tip
The Investigation Comments text entry field supports basic HTML tags, as well as emoji, so you can 🙂 , 🤔, or even 😱 where needed.
Tip
@ mention other users to send them a notification in XDR, so they can reply.
If you have a subscription for ManagedXDR, you can communicate directly with your Secureworks Threat Hunter team by adding @secureworks to your comment. This notifies your support team and includes them in your discussion.
When replying to a comment that used an @ mention, the new comment automatically starts with an appropriate @ mention to ensure the party receives a notification. This automatic mention can be removed if unwanted.
-
Choose Save.
Hand Off an Investigation ⫘
The current owner of an investigation is called the assignee. Other users that add comments or modify the investigation are collaborators. The assignee and collaborators avatars display in the header of the investigation. Each investigation has one assignee at a time. This is either someone from your organization or Secureworks.
There are two ways to hand off an investigation to a specific user:
Choose an Assignee ⫘
- Open the investigation details page.
- Select the current Assignee’s name.
- Choose an assignee. This can be yourself, the entire tenant, or a specific user. ManagedXDR subscribers can also assign the investigation to Secureworks.
- The investigation’s status changes to Awaiting Action, or to Active if you assigned it to yourself. The new assignee is notified via their in-app notifications and by email if they have opted to receive these.

Choosing an Assignee
Change Investigation to Awaiting Action ⫘
- Select Awaiting Action from the status drop-down list on an investigation.
- In the pop-up modal, select a user whose action you are waiting for.
- Choose Assign Investigation.
- The investigation’s status changes to Awaiting Action. The new assignee is notified via their in-app notifications and by email if they have opted to receive these.

Awaiting Actions from Another User
Share an Investigation ⫘
To share an investigation with another user within the tenant, select the Copy share link icon for a direct URL.
Copying the Share Link for an Investigation
Export Investigations ⫘
Export All to CSV ⫘
To download a CSV file of the table of investigations, follow these steps:
- Select Investigations from the left-hand side navigation bar to view the Investigations page.
-
Filter the table if needed.
Tip
While you can filter according to column content, all possible columns will be included in the final CSV file.
-
Select Actions → Export All as CSV. When your download is ready, it appears in the Data Exports table.
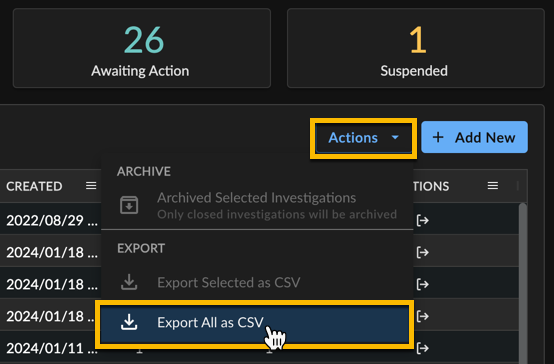
Exporting All Investigations
Export Selected to CSV ⫘
To download a CSV file of a single row from the table, choose the export icon from the Actions column for the desired row.
To export multiple selected rows, follow these steps:
- Select Investigations from the left-hand side navigation bar to view the Investigations page.
-
Filter the table if needed.
Tip
While you can filter according to column content, all possible columns will be included in the final CSV file.
-
Select the checkboxes at the left of the rows you wish to export.
- Select Actions → Export Selected as CSV. When your download is ready, it appears in the Data Exports table.
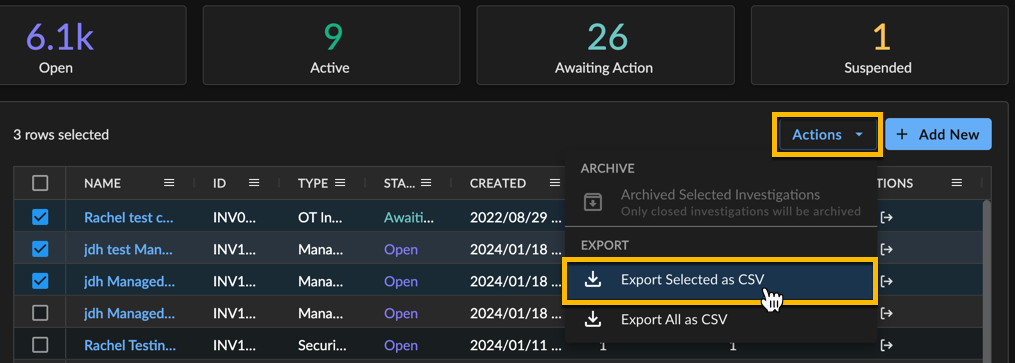
Exporting Selected Investigations
Export Investigation Details to PDF ⫘
You can also export a PDF file of an individual investigation's details. To do so, follow these steps:
- Select Investigations from the left-hand side navigation bar to view the Investigations page and then select the name of the investigation you wish to export.
- From the investigation’s details page, select Actions → Export to PDF.
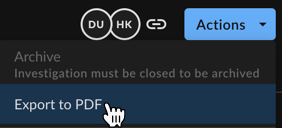
Exporting a PDF of an Investigation
- Choose to include Top Level Findings and/or Key Findings in the report and select Print.
- When your download is ready, it appears on Completed Reports.
Archived Investigations ⫘
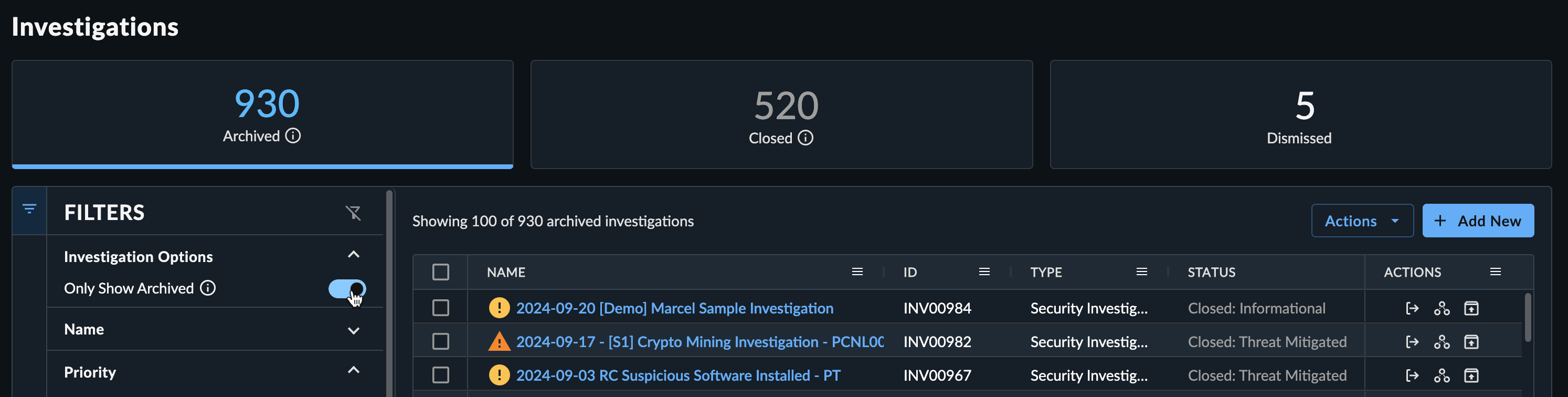
Archived Investigations Summary Table
If investigations are no longer relevant or may have been created by mistake, you can archive them.
To view archived investigations:
- From the filters menu, select Show Archived Only to update the table with archived, closed, and dismissed investigations.
- Use the status cards to view by state:
- Archived — Investigations that have been archived.
- Closed — Investigations that have been closed using one of the close codes.
- Dismissed — Draft investigations that have been dismissed.
-
Use the filters menu to further narrow down the results.
-
Select the status cards above the Investigations table, which provide a count of all investigations by that status. The number indicates how many investigations are in that state.
Note
The following affects how an investigation can be edited:
- Investigations with any Closed status are read only, except for the Status field and the Archive action.
- Draft investigations that have been dismissed are read only, except for the Archive action.
- Archived investigations are read only, except for the Unarchive action.
Archive an Individual Investigation ⫘
Important
Investigations must be closed first to be archived.
Archive an individual closed investigation in one of two ways:
- By selecting Actions → Archive from the investigation’s details page.
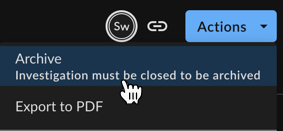
Archiving an Individual Investigation from Details
- By selecting the Archive icon from the Actions column of the Investigations table.
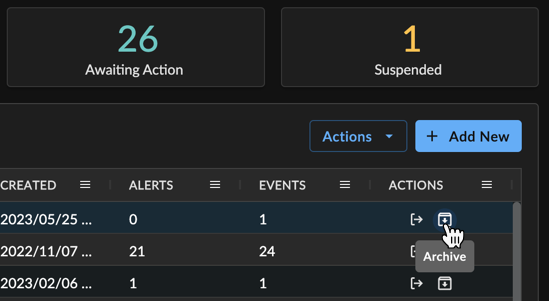
Archiving an Individual Investigation from Table
Archive Multiple Investigations ⫘
Important
Investigations must be closed first to be archived.
To archive multiple investigations from the Investigations table, follow these steps:
- Select Investigations from the XDR side menu bar to view the Investigations page.
- Use the checkboxes to select the investigations you wish to archive.
- Select Actions → Archive Selected Investigations from above the table. The investigations are archived.
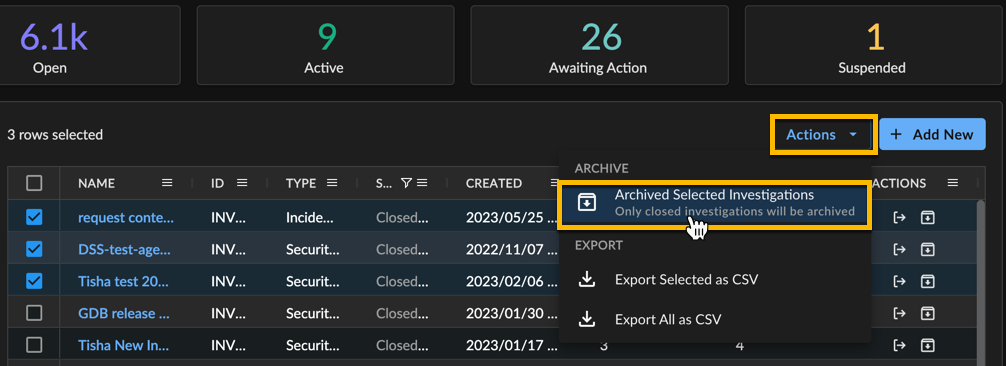
Archiving Multiple Investigations
Restore Archived Investigations ⫘
Restore an Individual Investigation ⫘
Restore an individual archived investigation in one of two ways:
- By selecting Actions → Unarchive from the investigation’s details page.
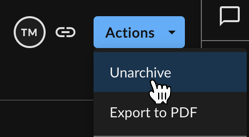
Restoring an Archived Investigation from Details
- By selecting the Unarchive icon from the Actions column of the Investigations table.
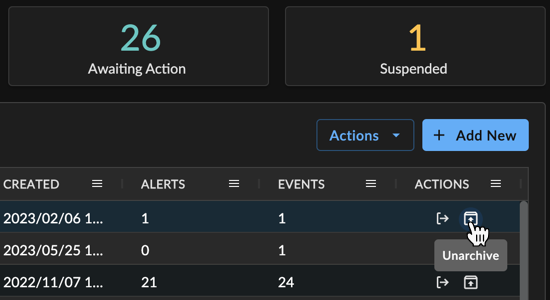
Restoring an Archived Investigation from Table
Restore Multiple Investigations ⫘
To restore multiple archived investigations:
- Select Investigations from the XDR side menu bar to view the Investigations page.
- Select the Show Only Archived toggle from the filter menu on the left to view all archived investigations.
- Use the checkboxes to select the investigations you wish to restore.
- Select Actions → Unarchive Selected Investigations from above the table. The investigations are restored.
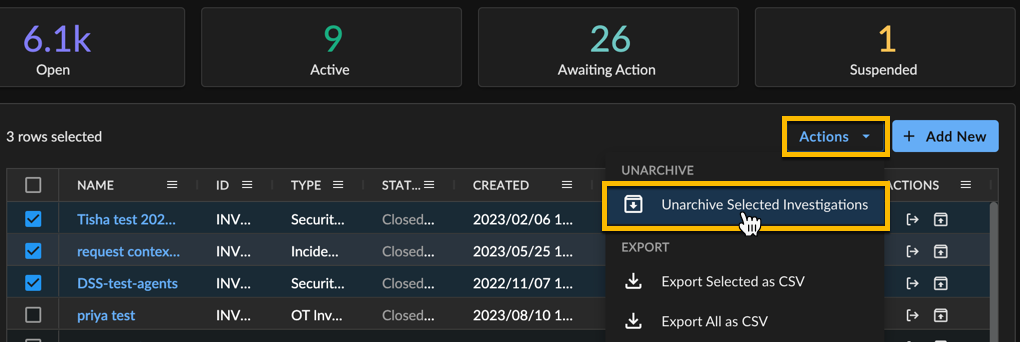
Restoring Multiple Archived Investigations
