Enterprise SSO
Single sign-on (SSO) enables you to integrate Secureworks® Taegis™ XDR access with a localized corporate authentication system, termed a connection in XDR.
With SSO enabled, XDR users utilize their corporate authentication credentials when accessing XDR, which means if you are logged in to your corporate network, you no longer need a separate password or MFA to log in to XDR.
Important
Users still require a user account to be created in XDR including an applicable role with the same email address used in your corporate authentication system. The email address is what allows the synchronization between the authentication systems on a per-user basis.
Enabling SSO provides the following benefits:
- XDR adheres to your password and MFA standards
- No need for a separate MFA system or remembering an additional password
- User admin is centralized to your corporate authentication system as this is linked to XDR
- Once your session times out and you need to log back in, there is no need for password and MFA entry to reaccess the system
Prerequisites ⫘
Security Assertion Markup Language 2.0 is a version of the SAML standard for exchanging authentication and authorization identities between security domains.
Your authentication system must be compatible with the SAML2.0 authentication protocol to set up an integration with XDR.
Enterprise SSO Overview ⫘
Important
If you have been supplied XDR through a Partner (MSSP) organization, please confirm with your Partner that SSO integration is supported before continuing.
Tenant Administrators can manage SSO connections via the Enterprise SSO page. To access this page, from the XDR left-hand side navigation, select Tenant Settings → Enterprise SSO.
Note
Enterprise SSO is only configurable by users with the Tenant Admin role.
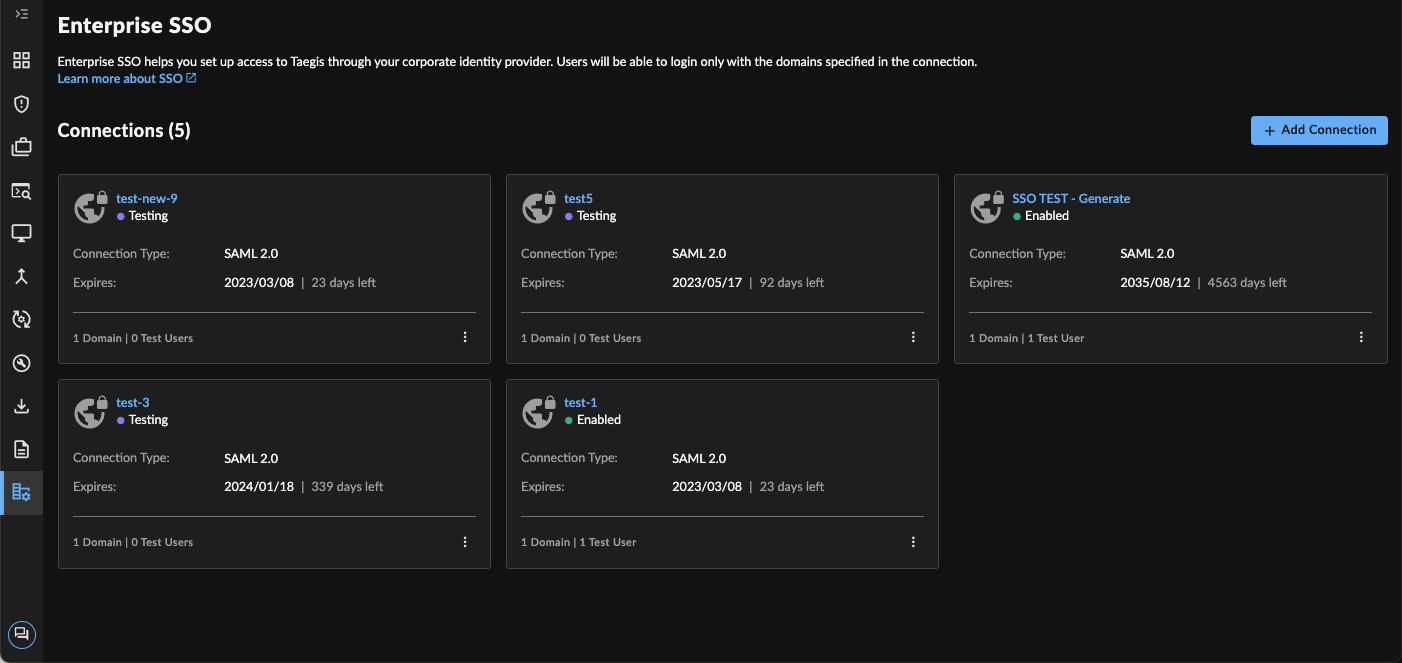
XDR SSO
Current SSO connections display as summary cards with the number of domains, expiration date of the signing certificate, and one of the following statuses of the connection below the name:
- Enabled — All users whose email login credentials match the domains specified in the SSO configuration will access XDR using SSO.
- Testing — The Testing status allows you to test the connection prior to it being active for users.
- Disabled — The SSO connection is not active for any users with email addresses matching the configured domains. Only disabled connections can be deleted.
- Draft — A connection is moved into Draft status if the configuration is incomplete. This may happen if an update is applied and the system reboots, if there are issues on the browser, etc.
Select a summary card to review the connection details, change the status, edit details, or delete the connection. For connections in Draft status, select the summary card to complete the configuration.
You can also change the status or delete the connection by selecting the menu icon from the bottom-right corner of a card on the Enterprise SSO page.
Add New SSO Connection ⫘
Tenant Administrators can configure up to six SSO connections per tenant. Specified domains must be unique per connection and not span across connections.
To set up a new connection, follow these steps:
- From the XDR left-hand side navigation, select Tenant Settings → Enterprise SSO.
- Select + Add Connection. The Add a New Connection panel displays. Use the guidance within each of the following sections to complete configuration.
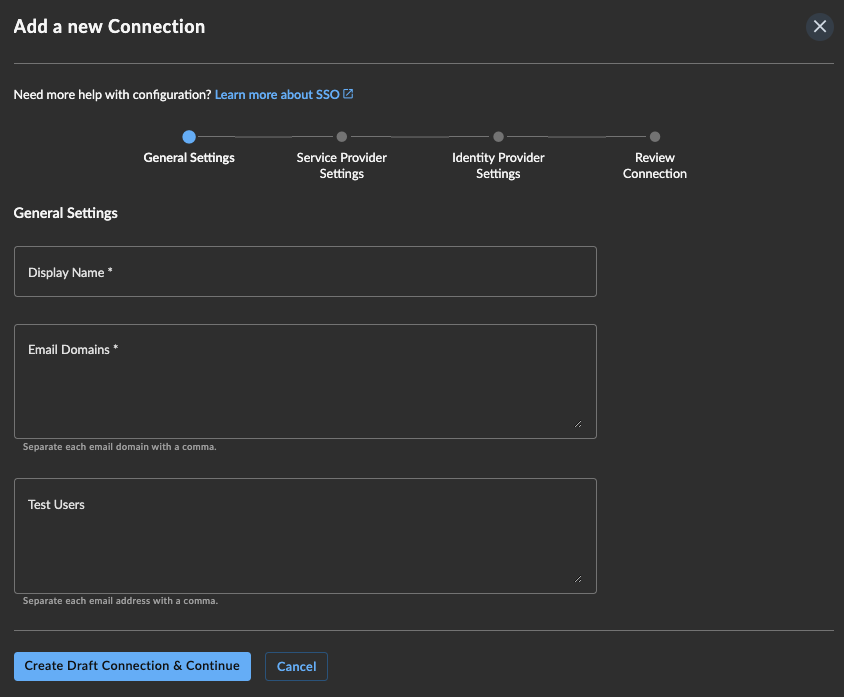
Add a New SSO Connection
Notes
Test users are no longer used for testing and this field will soon be removed.
General Settings ⫘
Provide the following information in General Settings, and then select Create Draft Connection & Continue:
- Display Name — Enter a descriptive name for the connection to easily identify it for audit and in case you configure multiple.
- Email Domains — Enter all domains for approved email addresses separated by a comma; e.g.,
company.com, companytemp.com, company123.com. - Test Users — Test users are no longer used for testing and this field will soon be removed. To test the connection, see Test and Confirm SSO Connection.
Service Provider Settings ⫘
Within the SSO configuration, XDR is defined as the Service Provider while your authentication system (Active Directory, PingFederate, Okta, etc.) is defined as the Identity Provider. After defining the SSO connection, Service Provider details will need to be added within your authentication system. Consult the documentation specific to your authentication system for details on how this information should be used.
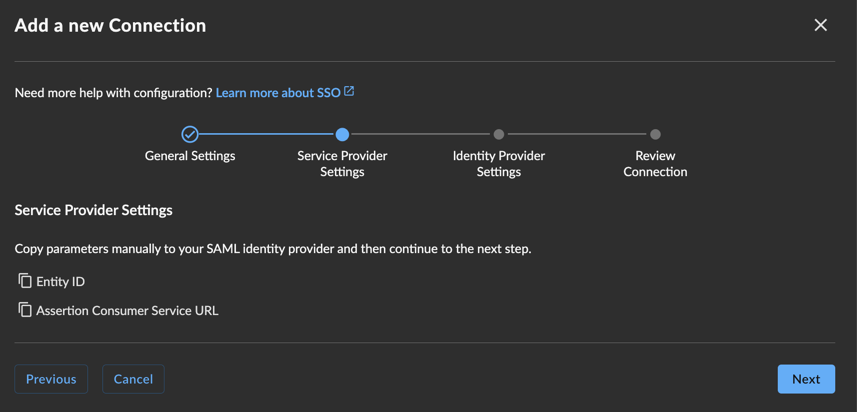
Service Provider Settings
Copy the Entity ID and Service URL in Service Provider Settings by selecting the copy icon to the left of these items for use in your authentication system as needed, and then select Next.
Identity Provider Settings ⫘
Having copied the Service provider details from XDR to your Identity Provider configuration, XDR will require information from the Identification Provider to complete the connection to your Tenant. Any user requiring access to XDR still needs an account created within XDR, but password and MFA authentication procedures will be taken from your corporate authentication system, such as Okta or Active Directory.
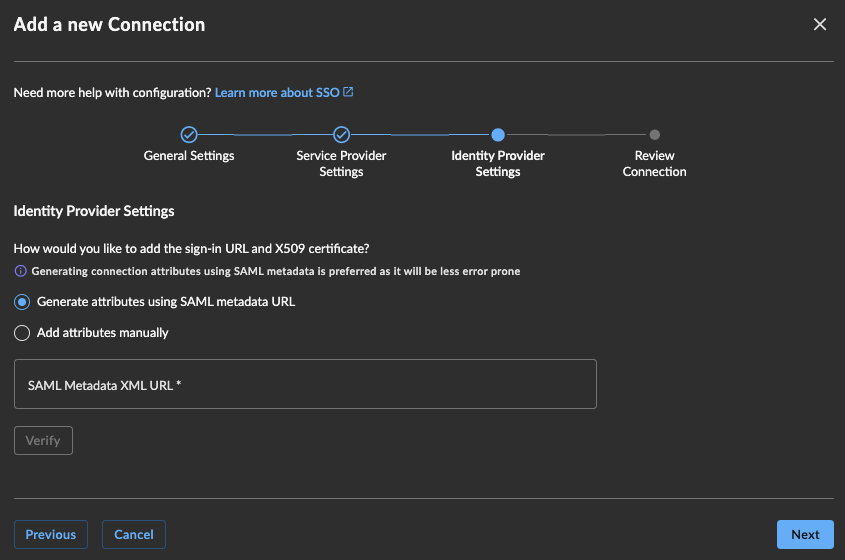
Identity Provider Settings
In Identity Provider Settings, supply the following details from your authentication system to integrate with XDR:
- The sign-in url
- A signing certificate
Use one of the following methods to supply these details:
- Generate attributes using SAML metadata URL — If supported, enter a metadata URL from your authentication system to extract the login URL and signing certificate, and then select Verify. Once Verify has been selected, you can display the signing certificate with the expiration date as a way to ensure that the correct details have been captured as a part of the connection. If the details don't look as expected, check the metadata url or the selected signing certificate that was uploaded for any errors.
- Add attributes manually — Select this option to input the sign-in URL and upload the signing certificate.
Select Next once complete to review the connection.
Note
SAML Attributes ⫘
The identity provider must be configured to return the user’s email address in the SAML assertion. Configuration for this is provider specific. The name of the SAML attribute to return should be http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress and the value set to the email address. The email address returned in the SAML assertion must match the email address registered with XDR.
Review Connection ⫘
In Review Connection, confirm that all entered information is correct, and then choose Save Connection.
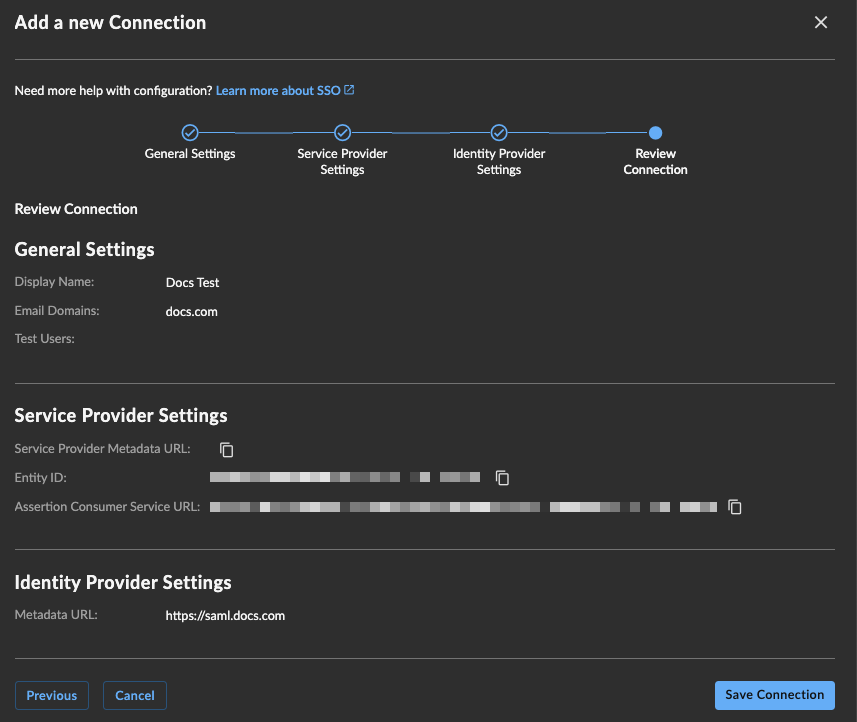
Review Connection
The new connection now appears as a summary card on the Enterprise SSO page in Testing status.
Test and Confirm SSO Connection ⫘
After you have completed the steps to add a new SSO connection, select the summary card for the connection from Tenant Settings → Enterprise SSO. Select Test from the bottom of the connection details to confirm the configuration settings are operational. If there are any errors reported, reapply the settings and retest until successful.
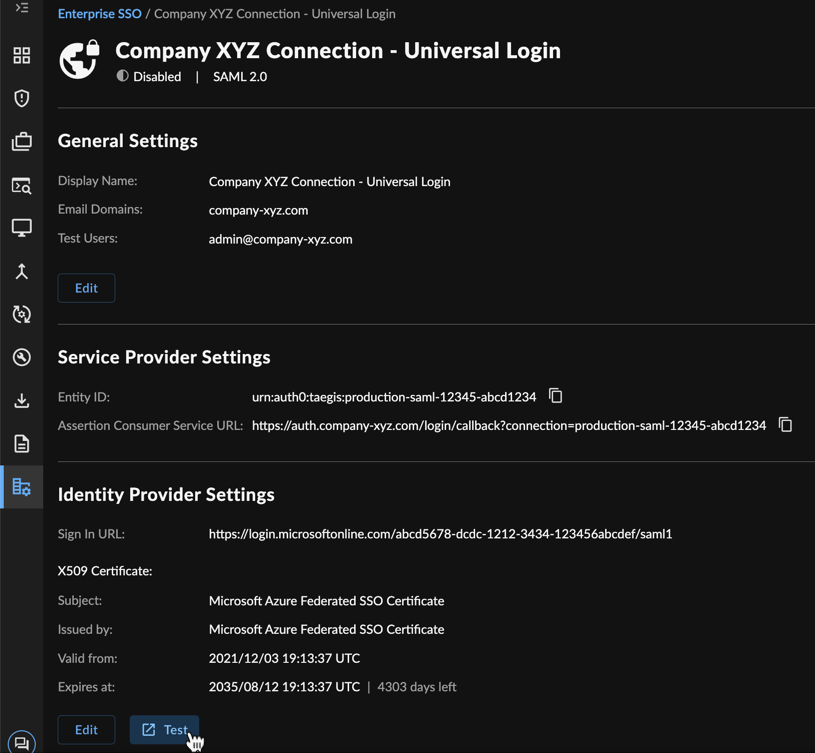
Review Connection
After you have successfully tested the connection, change the connection status to Enabled so all users within the specified domain(s) are subject to SSO.
Note
Identity provider initiated logins are not supported. All logins must be initiated from XDR.
Change Connection Status ⫘
Note
You must complete the configuration for connections in Draft status by selecting the summary card prior to changing the status.
To change the status of a connection, from the Enterprise SSO page:
- Select the menu icon from the lower-right corner of a connection summary card and choose Change Status, or select a summary card to view the connection details and choose Change Status from the top right of the page.
- Select the status you wish to change the connection to.
- Choose Save.
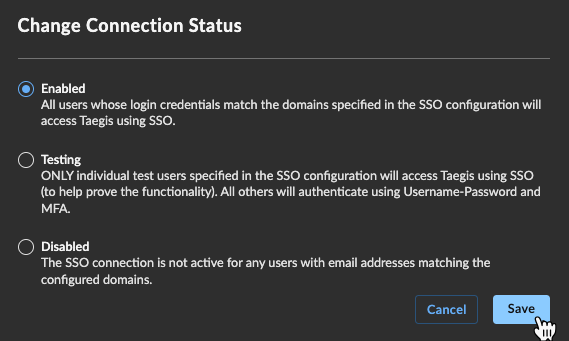
Change Connection Status
Edit Connection Details ⫘
Note
You must complete the configuration for connections in Draft status by selecting the summary card prior to editing.
To edit the details of a connection, from the Enterprise SSO page:
- Select a summary card to view the connection details.
- Choose Edit from the General Settings or Identity Provider Settings.
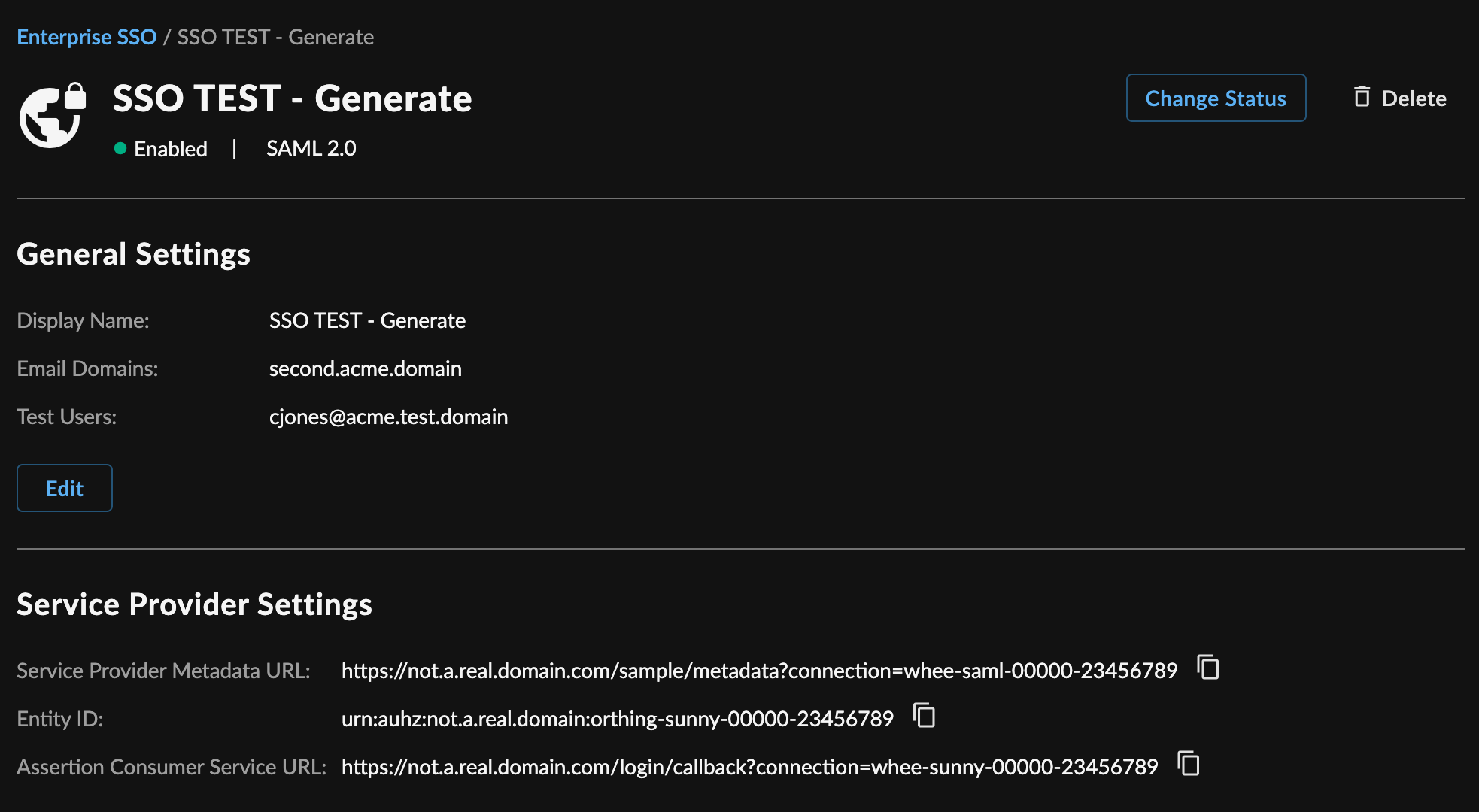
Edit Connection Details
- Make the desired changes and select Save.
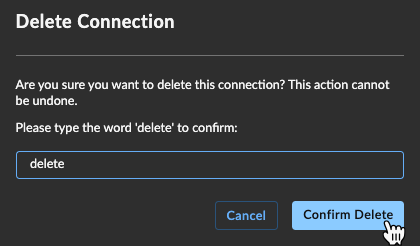
Delete Connection ⫘
Note
Connections must be changed to a Disabled status before they can be deleted.
To delete a connection, from the Enterprise SSO page:
- Select the menu icon from the lower-right corner of a connection summary card and choose Delete, or select a summary card to view the connection details and choose Delete.
- Type the word
deleteto confirm this action is required and then choose Confirm Delete.
Delete Connection
- The connection is removed.
Knowledge Base Resource ⫘
Find guidance for configuring Enterprise SSO with Azure AD in this Knowledge Base article.
