Cato Networks Integration Guide
integrations cato sd-wan sase sse
The following instructions are for configuring Cato Networks to facilitate log ingestion into Secureworks® Taegis™ XDR.
Data Provided from Integration ⫘
The following Cato Networks event types are supported by XDR.
- Anti Malware
- Internet Firewall
- WAN Firewall
- IPS
Note
Cato Networks event types not listed above are normalized to the generic schema.
| Antivirus | Auth | DHCP | DNS | Encrypt | Filemod | HTTP | Management | Netflow | NIDS | Process | Thirdparty | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Cato Networks | Y | D | Y |
Y = Normalized | D = Out-of-the-Box Detections | V = Vendor-Specific Detections
Note
XDR detectors are not guaranteed to be triggered, even if a data source's logs are normalized to a schema associated with a given detector. However, you can create Custom Alert Rules to generate alerts based on normalized data from a data source.
Configure the Cato Platform to Send Logs to S3 ⫘
Follow the instructions in the Cato documentation to configure syslog forwarding to an S3 bucket.
Deploy the XDR Lambda Function in Your AWS Environment ⫘
Follow these instructions to deploy the Lambda function that will send Cato Networks logs from your S3 bucket to XDR.
Note
The above instructions reference CloudTrail; however, the mechanism to send logs from S3 to XDR are data source-agnostic. You must follow all steps in the instructions.
Advanced Search Using the Query Language ⫘
Example Query Language Searches ⫘
To search for thirdparty events from the last 24 hours:
FROM thirdparty WHERE sensor_type = 'Cato Networks' and EARLIEST=-24h
To search for netflow events:
FROM netflow WHERE sensor_type = 'Cato Networks'
To search for events that were classified by Cato Networks as High:
WHERE sensor_type = 'Cato Networks' AND vendor_severity = 'High'
To search for antivirus events from a source IP address:
FROM antivirus WHERE sensor_type = 'Cato Networks' AND source_address = '10.10.10.10'
Event Details ⫘
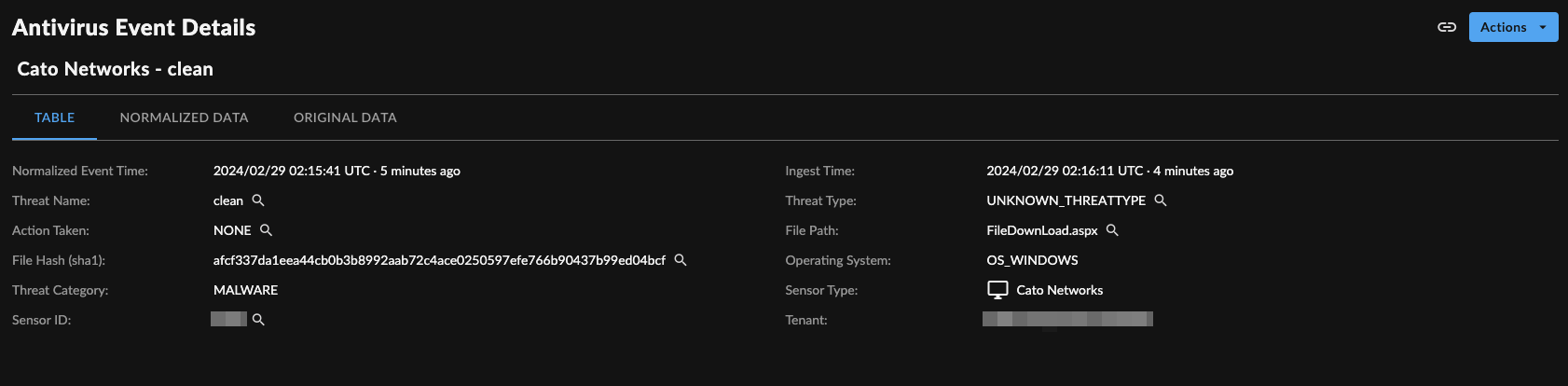
Cato Networks Event Details
Sample Logs ⫘
Cato WAN Firewall Event ⫘
{"time_str":"2024-02-21T04:57:21Z","time":1708534641652,"event_count":1,"http_host_name":"api.example.com","ISP_name":"ACME Co.","rule":"Example_HTTP/HTTPS_Allow","src_isp_ip":"10.10.10.10","src_site":"AAA","src_ip":"10.90.10.10","internalId":"1ab234567890c1","domain_name":"api.example.com","event_type":"Security","src_country_code":"JP","action":"Monitor","categories":["Network Utilities","Business Information"],"subnet_name":"To AAA_10.90.10.0/24","dest_user_id":-1,"pop_name":"Atlantis","dest_port":443,"rule_name":"Example_HTTP/HTTPS_Allow","event_sub_type":"Internet Firewall","ad_name":"Unidentified","insertionDate":1708534705403,"dest_country_code":"US","ip_protocol":"TCP","rule_id":"20000","src_is_site_or_vpn":"Site","account_id":9999,"application":"Cato Management Application","src_site_name":"AAA","src_country":"Atlantis","user_id":-1,"dest_ip":"192.168.1.90","os_type":"OS_LINUX","app_stack":["TCP","TLS","HTTP(S)","Cato Management Application"],"dest_country":"United States"}
