Domain Watchlist
The Domain Watchlist Detector uses a Secureworks Counter Threat Unit™ (CTU) Threat Intelligence curated list of suspicious domains and compares them to Domain Name System (DNS) telemetry collected via supported endpoint and syslog data sources. When a suspicious domain is identified in tenant telemetry an alert is generated. The alert contains the list the suspicious domain was sourced from, the reason it is suspicious, and the associated confidence value. If a domain exists on multiple lists, the number of lists shows within the Alert Summary. In addition, the Alert Description includes each list, reason, and confidence.
The Domain Watchlist Detector also uses correlation whereby any subsequent matches for the same domain are appended to an existing alert. This enables users to quickly see which hosts are communicating with the suspicious domain without having to manually search.
Note
Taegis™ NDR automatically downloads the list of Secureworks malicious domains and uses them within the reputation preprocessor to detect malicious domains in real-time.
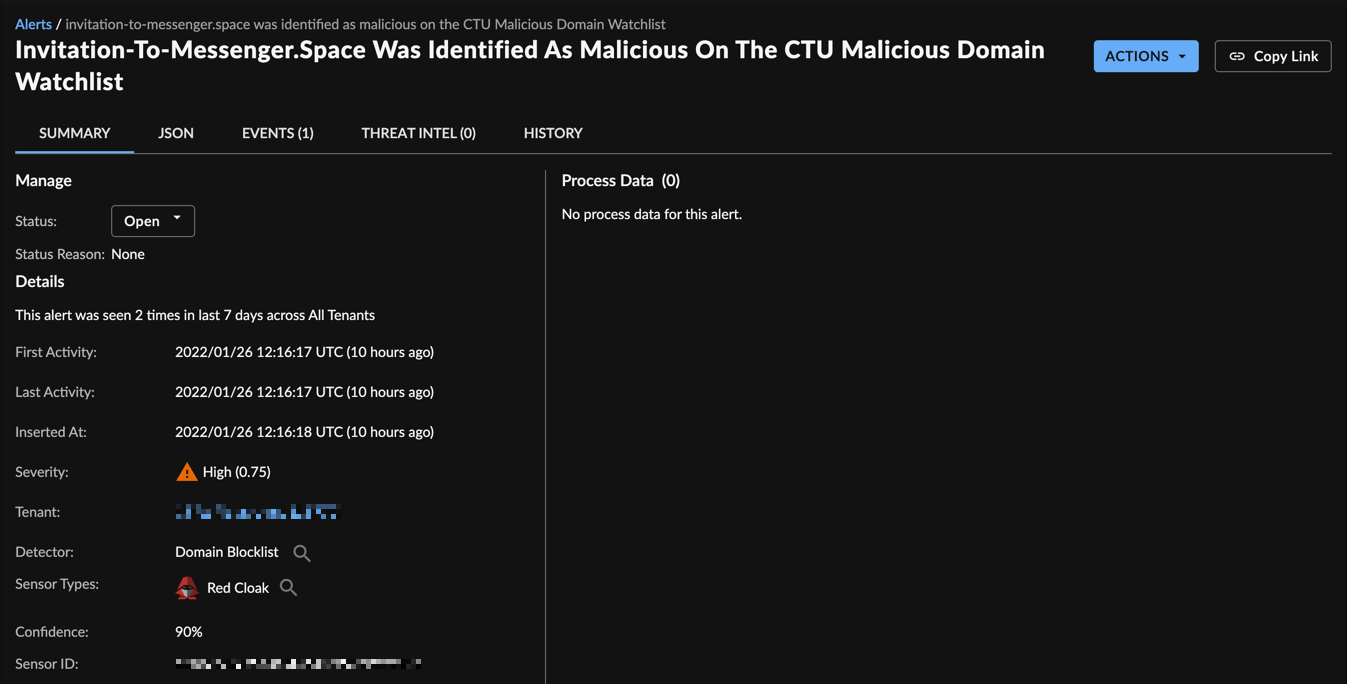
Domain Watchlist Alert
Inputs ⫘
DNS events
Outputs ⫘
Malicious Domain Alerts pushed to the Secureworks® Taegis™ XDR Alert Database and XDR Dashboard
MITRE ATT&CK Category ⫘
The Domain Watchlist detector has no MITRE Mapping.
Detector Requirements ⫘
- DNS
