Tactic Graphs
The Tactic Graphs™ Detector models adversary behavior in order to detect malicious behaviors by anticipating adversary tactics. Security applications typically identify threats using countermeasures that detect known malicious adversary actions and activities. When countermeasures block or detect these, the adversaries are forced to modify their tactics in order to continue to operate. It’s an arms race where threat actors and countermeasure developers are constantly iterating on their tactics and the countermeasures to stop them. The Secureworks® Taegis™ XDR Tactic Graphs Detector breaks this cycle through adversary behavior modeling.
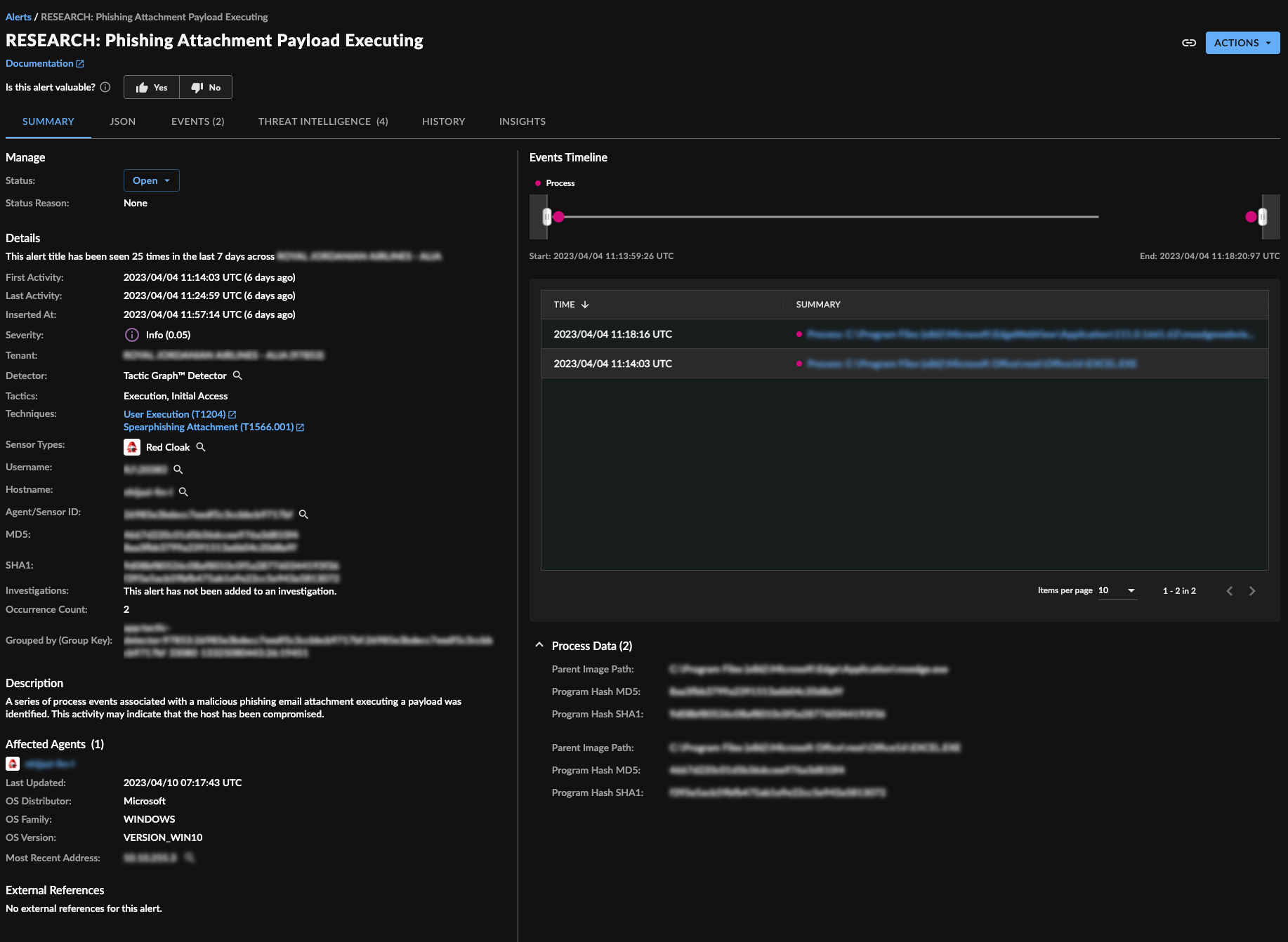
Tactic Graphs Detector Alert
Note
The Events Timeline displays when available.
When tactics are identified in your environment XDR generates alerts which are displayed in your XDR tenant.
The Tactic Graphs Detector alerts contain the individual behaviors that were identified, and the order of the malicious behaviors.
Inputs ⫘
Authentication events, Netflow records, Process events, XDR Alerts.
Outputs ⫘
Tactic Graphs Detector alerts pushed to the XDR Alert Database and XDR Dashboard whenever a tactic is observed in your environment.
MITRE ATT&CK Category ⫘
The XDR Tactic Graphs Detector has no MITRE Mapping.
Configuration Options ⫘
No configuration is required; Secureworks data scientists continuously tune and add tactics to the detector.
Detector Requirements ⫘
- Alerts, Auth, DNS, NIDS, Netflow, Process
