Alert Suppression Rules
Alert suppression rules may be created to mark alerts as suppressed at time of alert creation. Suppressed alerts are not included on the Secureworks® Taegis™ XDR Alert Triage Dashboard but can still be found in searches.
Tip
The Secureworks Professional Services team is here to help you realize the full potential from your Taegis XDR investment if a higher level of support is desired. Our highly skilled consultants can help you deploy faster, optimize quicker, and accelerate your time to value. For more information, see Professional Services Overview.
View Alert Suppression Rules ⫘
- From the XDR left-hand side navigation, select Tenant Settings → Rules. The Rules table displays.
- Select the Suppression Rules tab from the Rules table. The table displays all of the currently suppressed rules.
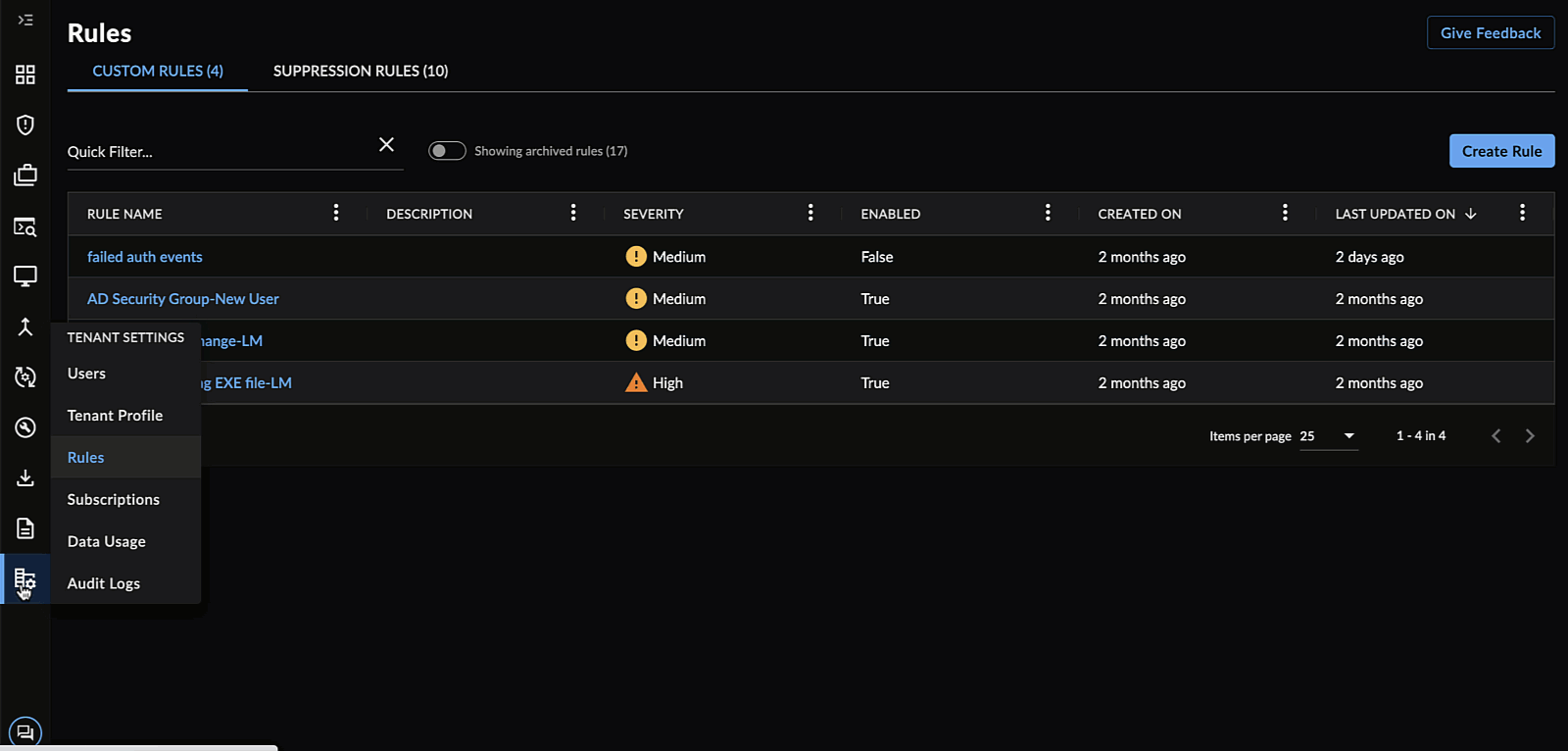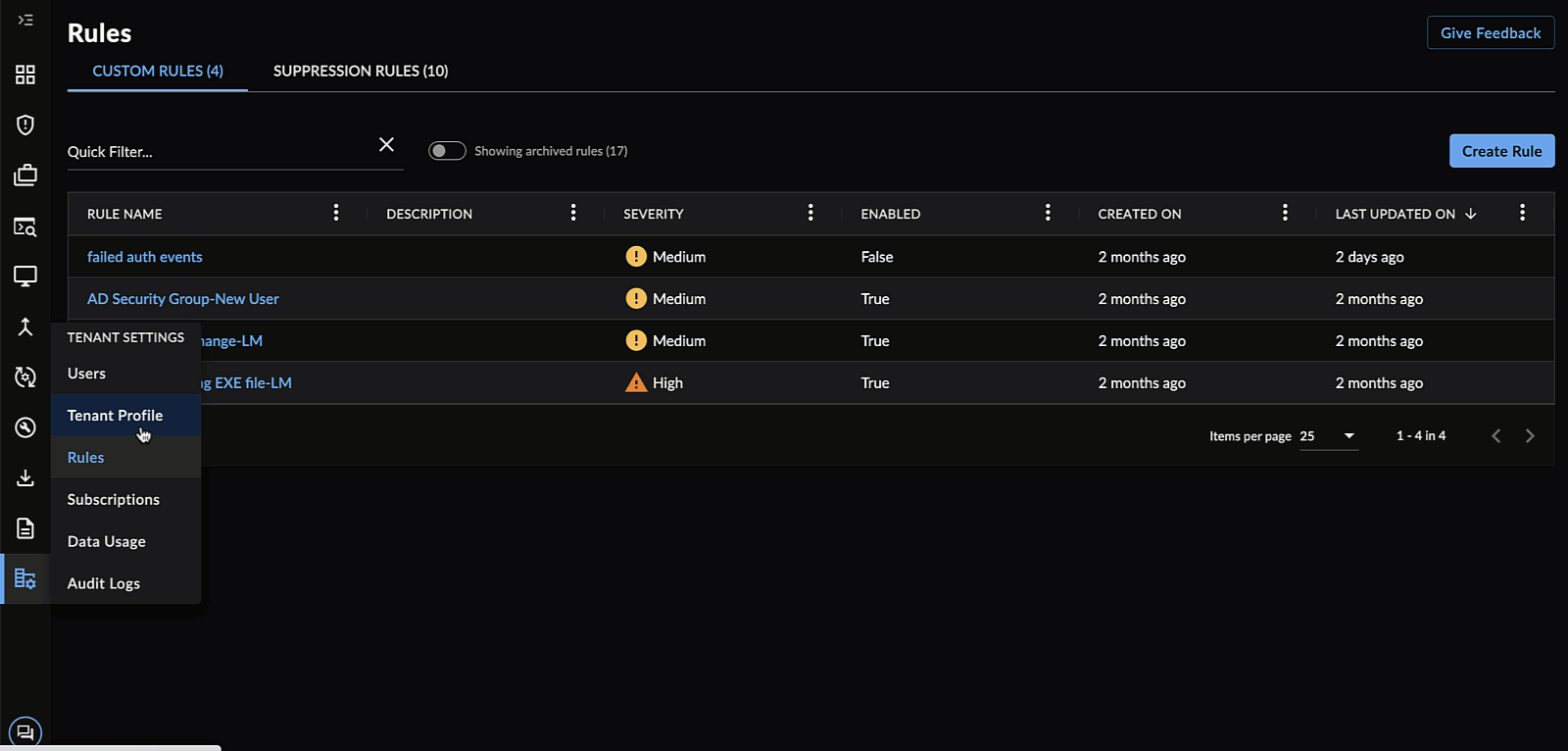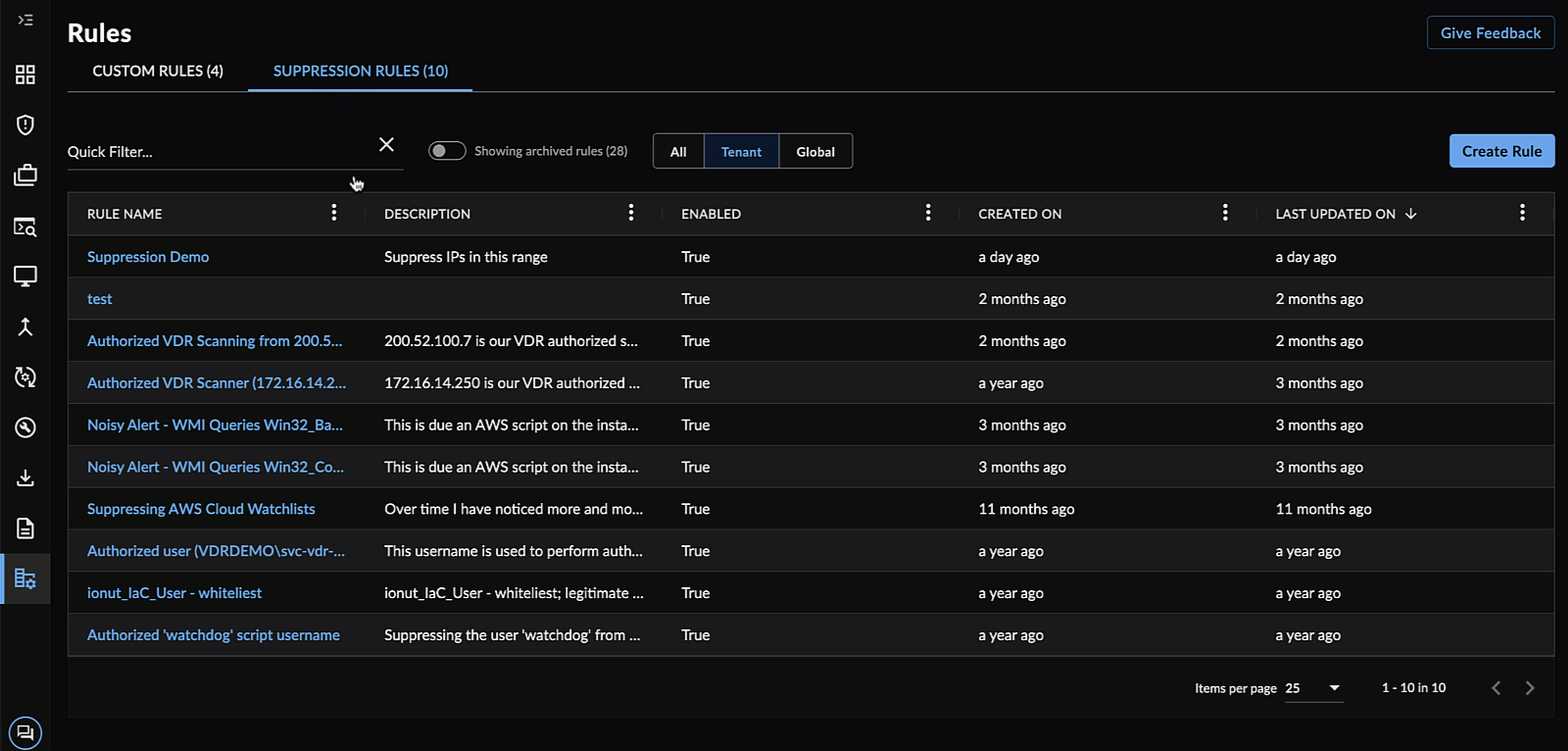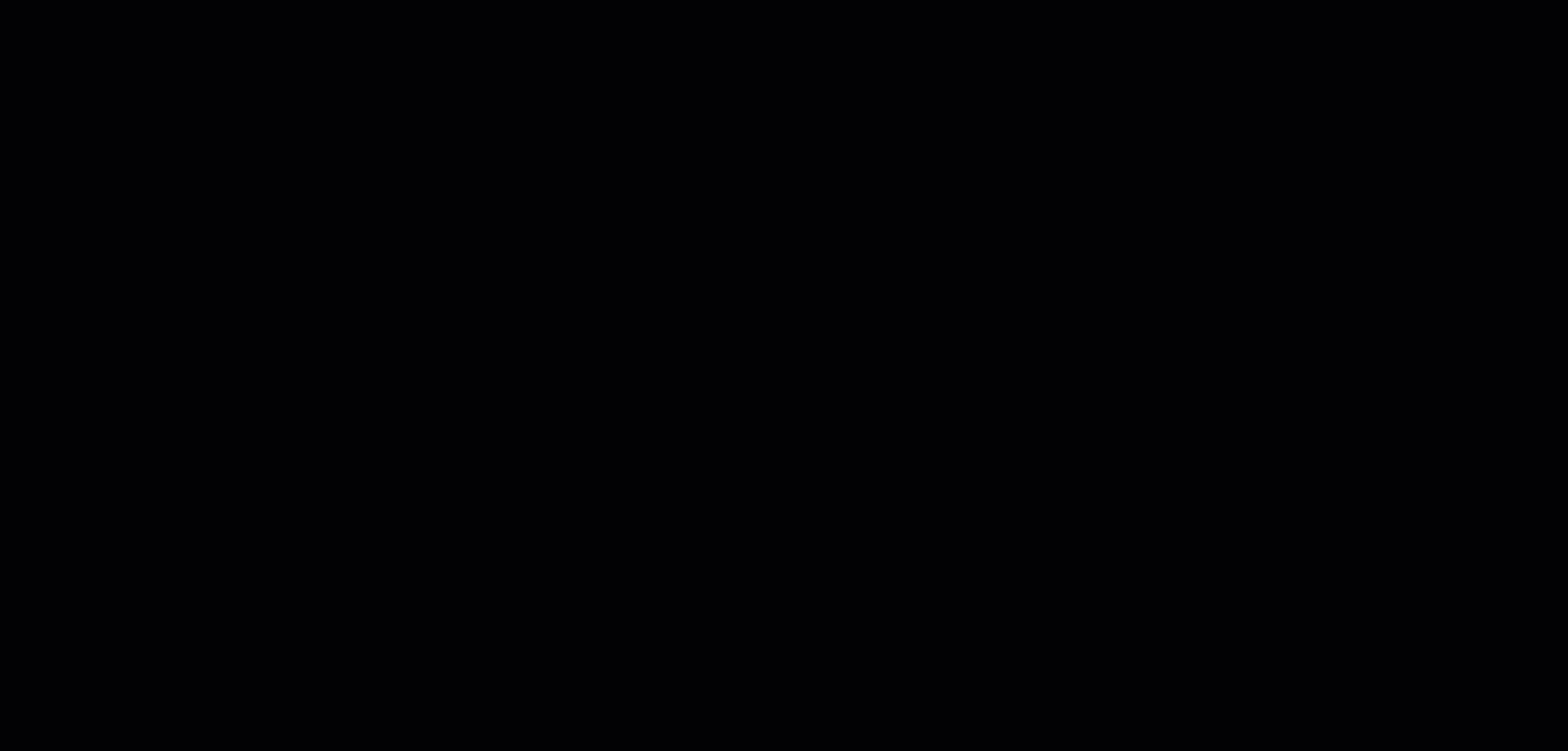
Suppression Rules
Create a Suppression Rule ⫘
There are a few ways to create an alert suppression rule.
From the Suppression Rules Table ⫘

Create a Suppression Rule from the Suppression Rules Table
- From the Suppression Rules Table, select Create Rule.
- Add one or more match criteria.
- Multiple criteria are AND’ed together.
- Criteria use PCRE regular expressions to perform matching.
Note
The following characters have special meaning within regular expressions: . ^ $ * + - ? ( ) [ ] { } \ | /. For IP addresses, domain names, and other instances, take care to escape the characters with a backslash: 1\.1\.1\.1.
To escape long sequences that contain multiple characters, enclose the whole string between \Q and \E so that the string is not evaluated for regex characters. For example, escaping this full string:
\Q${jndi:ldap://log4shell-smb-21yg3cbuy21gbcy21gc321uc${lower:ten}.w.nessus.org/nessus}\E
is equivalent to:
\$\{jndi:ldap:\/\/log4shell\-smb\-21yg3cbuy21gbcy21gc321uc\$\{lower:ten\}\.w\.nessus\.org\/nessus\}
- Add a Name and Description to the rule.
- Choose an Alert Resolution Status for the rule.
- Select Save.
From an Alert ⫘
Create a Suppression Rule from a Specific Alert
- Open the details of an alert you wish to suppress.
- From the alert details page, select Actions > Create Suppression Rule.
-
The Create Suppression Rule form is pre-populated with entities from the alert. Drag and drop these entities into the box to build your rule, and/or manually add match criteria.
- Multiple criteria are AND’ed together.
- Criteria use PCRE regular expressions to perform matching.
Tip
Regular expression special characters (i.e. . ^ $ * + - ? ( ) [ ] { } \ | /) are automatically escaped when dragged and dropped.
- Add a Name and Description to the rule.
- Choose an Alert Resolution Status for the rule.
- Select Save.
From Query Language ⫘
Advanced suppression rules support matching on an alert's underlying event data using Query Language. For example, advanced suppression rules can leverage Query Language elements such as process.commandline, process, parent_image_path, and other event schemas.
Note
See the FAQ for additional information on advanced suppression rules.
Create an Advanced Suppression Rule ⫘
Note
Enable Preview mode to create advanced suppression rules using Query Language.
-
Build your query in Advanced Search to verify which past alerts are to be suppressed in the future. Once you are satisfied with the results, copy the query and save it to paste into the rule builder.
-
Navigate to Tenant Settings → Rules and select the Suppression Rules tab. The Suppression Rules table displays.
-
Select Create Rule and configure the rule.
Note
If the Advanced Suppression Rule option is not shown, enable Preview mode first.
- Paste the verified query from Step 1.
- Add a Name and Description to the rule.
- Choose an Alert Resolution Status for the rule.
- Select Create Rule.
View Suppression Rule Details and History ⫘
Select a rule name from the Suppression Rules table to view its details and history.
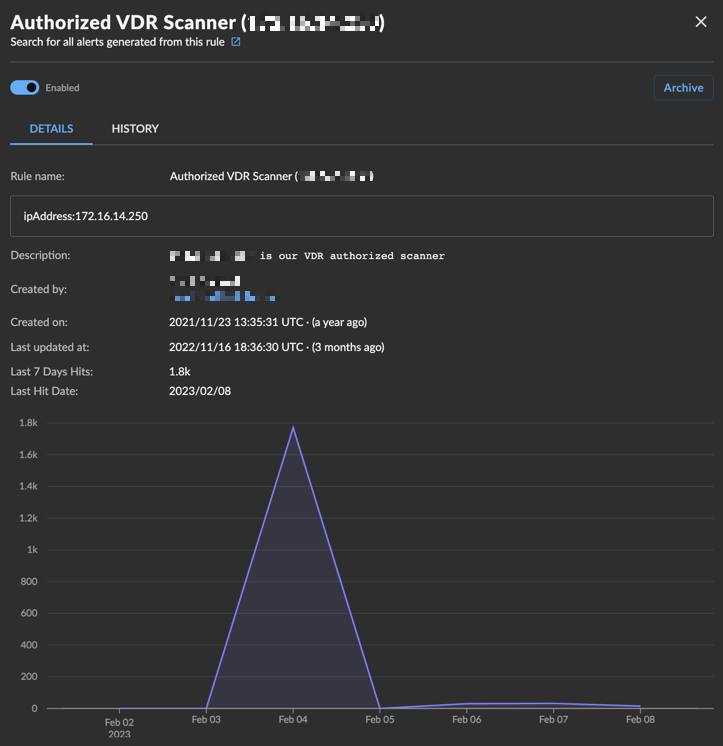
View the Details of a Suppression Rule
The Detail tab of the suppression rule contains overview information for the rule with the criteria the rule matches on. If the rule has matched on and suppressed alerts in the last seven days, the following display:
- Number of hits in the last seven days
- Last hit date
- Line graph visualizing the amount of hits
If there has been no activity in the last seven days, this section does not display.
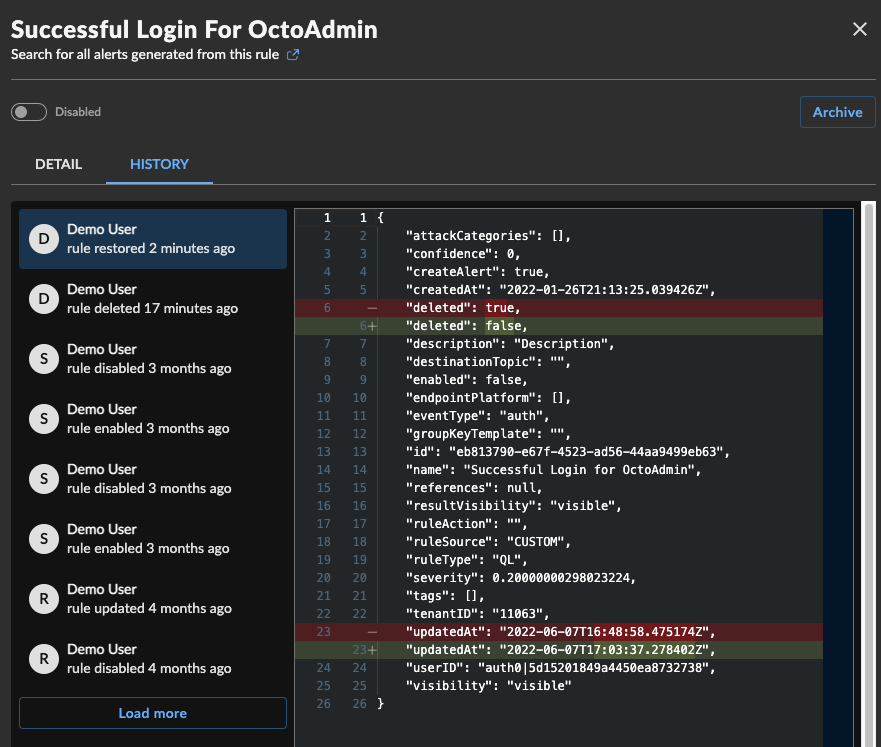
View the Changelog of a Rule
The History tab of the suppression rule contains a changelog of edits to the rule. Choose an audit log from the list on the left to view the diff in the right pane.
Archive and Restore a Suppression Rule ⫘
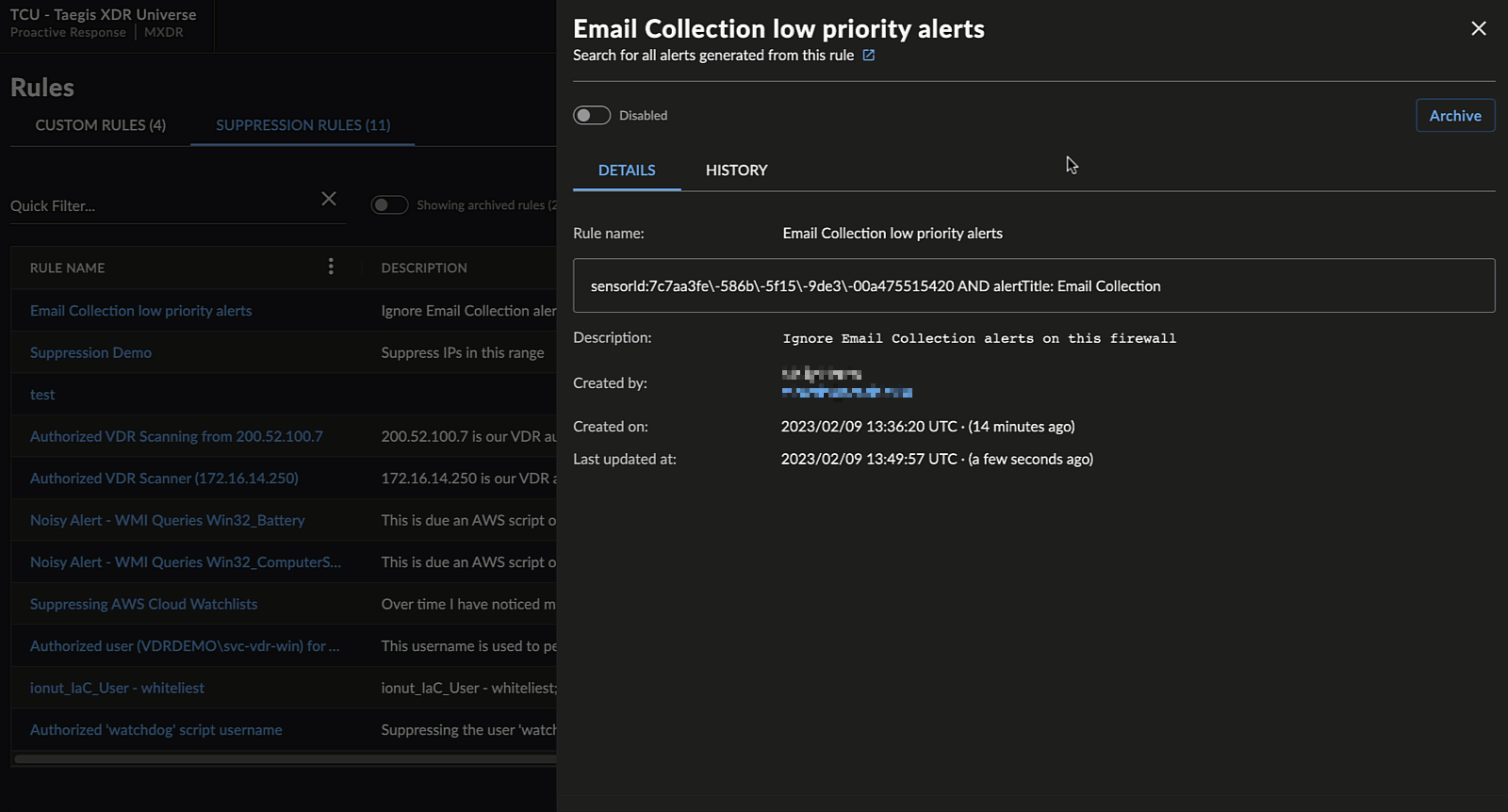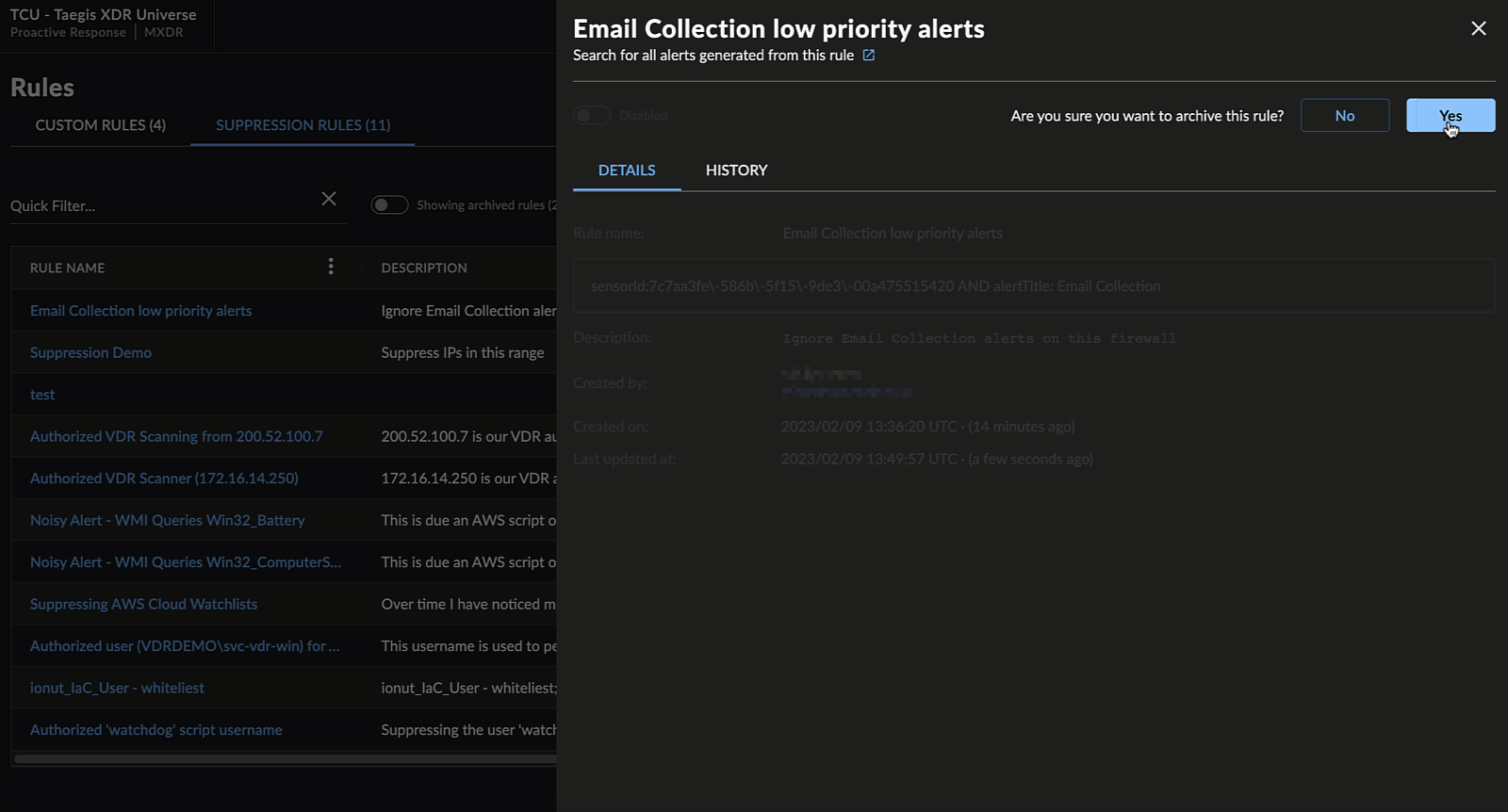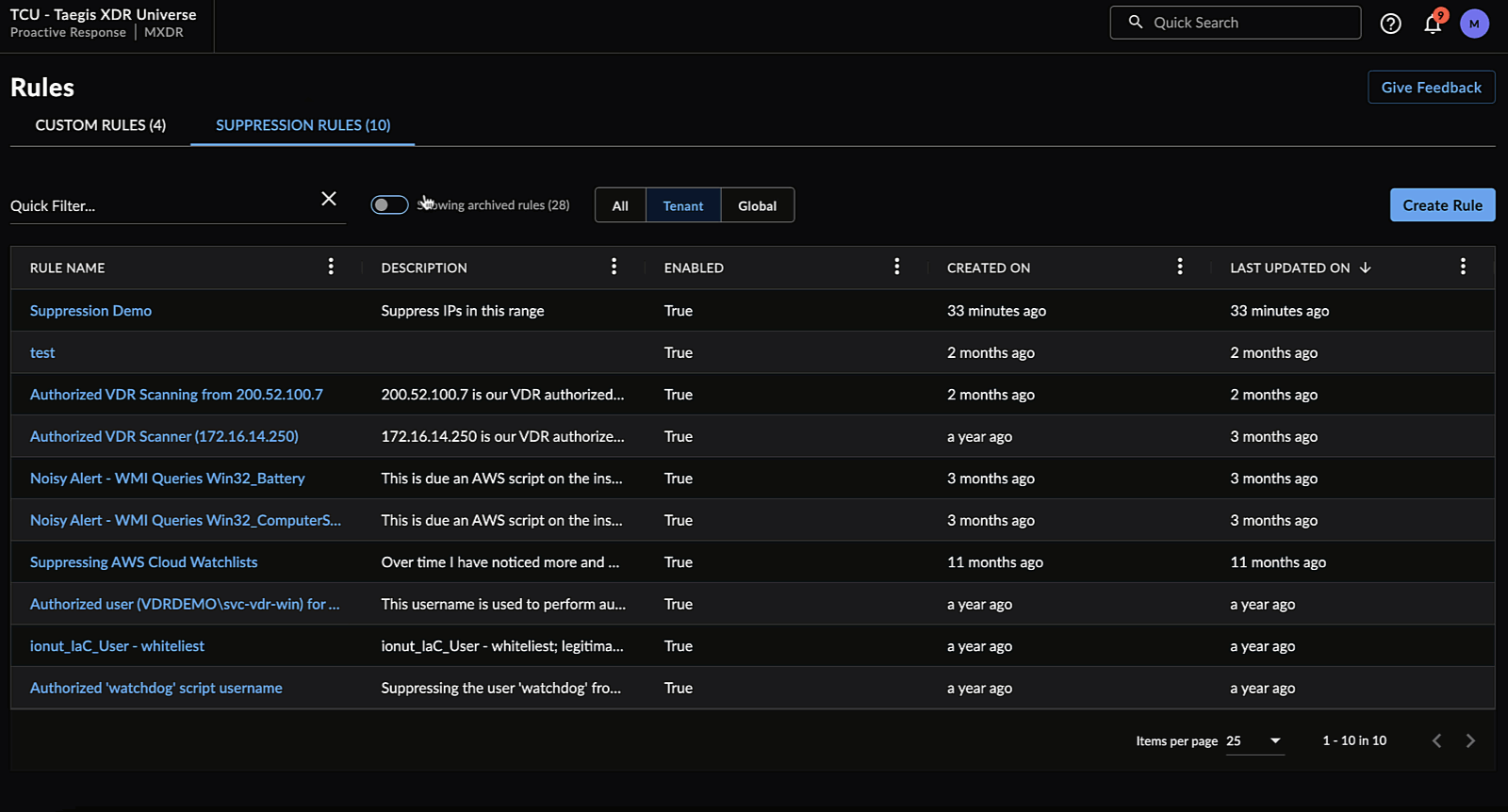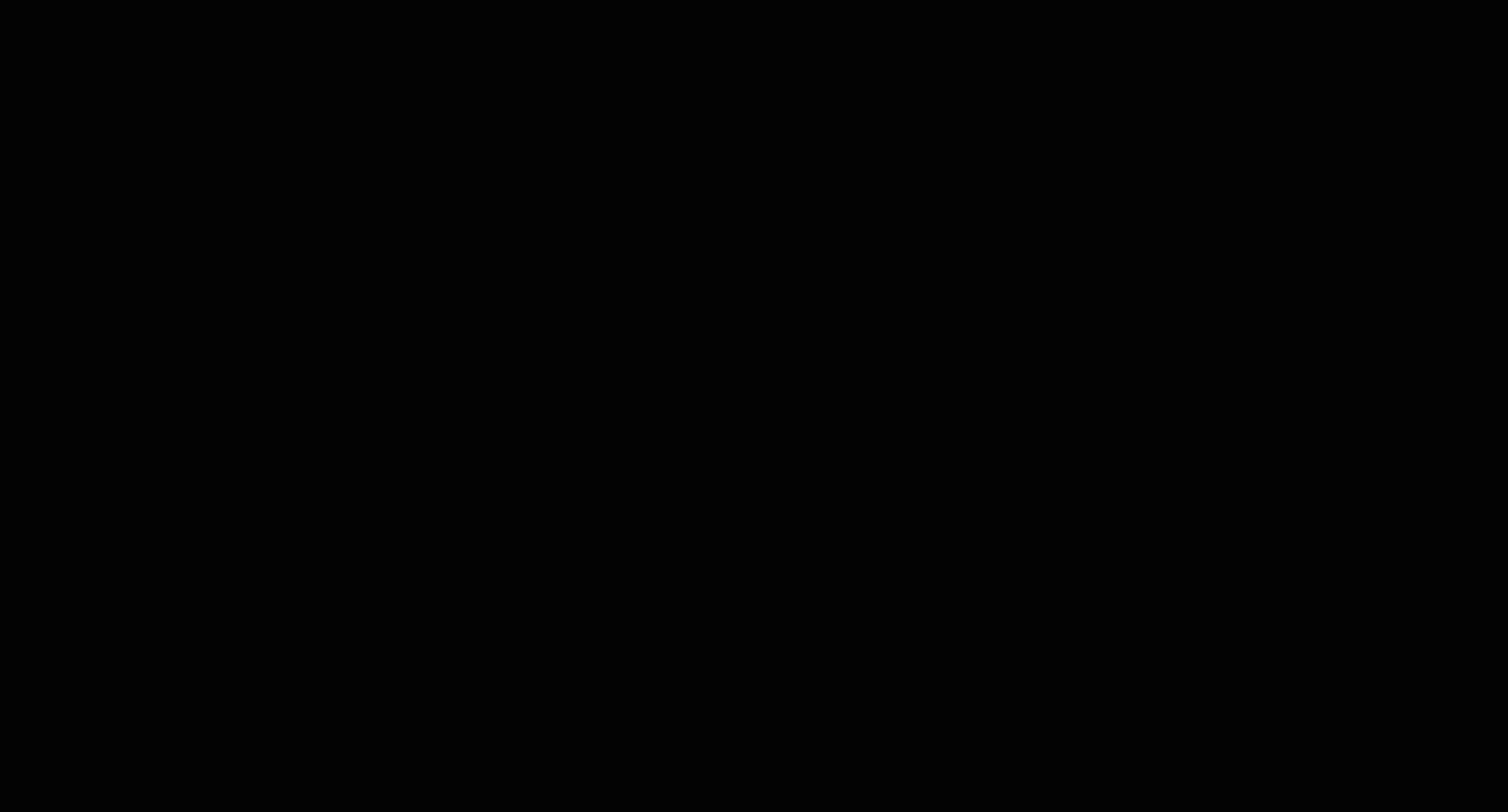
Archive and Restore Suppression Rules
When viewing a suppression rule, you can archive the rule by selecting Archive and confirming the action. This will disable the rule, mark it as archived, and remove it from the default view of the Suppression Rules table.
To view archived rules, select the Showing Archived Rules toggle above the Suppression Rules table.
When viewing an archived suppression rule, you can restore the rule by selecting Restore and confirming the action. This will restore the rule in a disabled state and return it to the default view of the Suppression Rules table. Select the toggle to enable the rule.
Share a Suppression Rule ⫘
To share a suppression rule with another user within the tenant, select the Copy share link icon from the rule details for a direct URL.
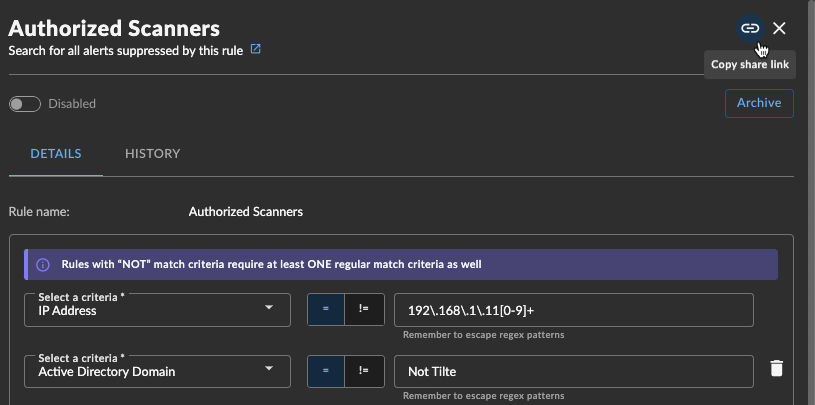
Copy Link to Share Rule
Common Alert Suppression Rules ⫘
Authorized Scanner ⫘
Use Source IP Address to suppress alerts originating from an authorized scanner.
If you have multiple authorized scanners, use a regular expression to include all IP addresses into one suppression rule.
Guest Network Range ⫘
Use Source IP Address to suppress alerts from a guest network range, using a regular expression to match the entire network range.
Authorized Process Execution on Endpoint ⫘
Use a combination of patterns to match both the endpoint and process.
- Use one to match endpoint:
- Sensor Host ID
- IP Address (if host has a static IP address and does not have an endpoint agent installed)
- Use one to match the process:
- File Name
- File (MD5|SHA1|SHA256|SHA512)
- Program Name
- Program (MD5|SHA1|SHA256|SHA512)
- Script SHA1 (This is a hash of the executed script)
FAQ ⫘
How do I know if an alert has been suppressed? ⫘
- Suppressed alerts are marked with a feedback label of Suppressed.
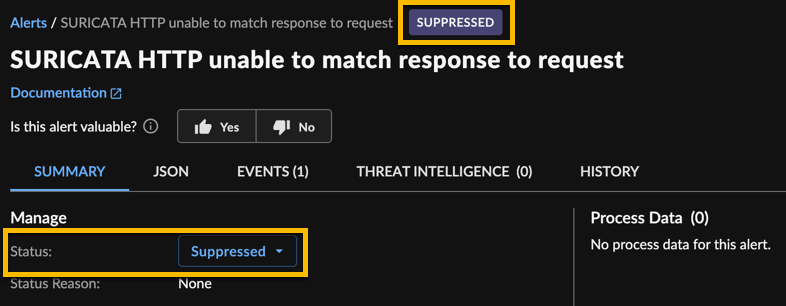
Suppressed Alert
What are global and tenant rules? ⫘
- Tenant rules are specific to the tenant and only suppress alerts for that individual tenant. Global rules apply to ALL XDR tenants. Global rules are commonly created to triage alert floods until the alerting rule or detector is tuned. Global rules are read-only. Please contact support if you have questions about a global rule.
How can I search for suppressed alerts? ⫘
- Suppressed alerts have the feedback label Suppressed. You can search for them using the following query:
from alert where suppressed = true
To exclude suppressed alerts from your results, add a NOT to the labelName criteria match:
from alert where suppressed = false
Another method is to run a pivot search from the rule itself. Open up a rule, find the search query at the bottom of the details, and select the new tab icon. This opens up an Advanced Search that is pre-populated with the query. These results include only alerts that were suppressed by this specific rule.
Can I add suppressed alerts to an investigation? ⫘
- Yes, suppressed alerts can still be added to new or existing investigations.
Can I change the feedback label on a suppressed alert? ⫘
- Yes, in the alert detail view, you can remove the feedback label or change the label.
Can I audit rule manager activity? ⫘
- Yes, actions in the rules manager are viewable by navigating to Tenant Settings → Audit Logs. Audit logs will have the category of Rules.
Additionally, a changelog of edits to the rule is available from the rule itself. See View Suppression Rule Details and History.
When an alert is suppressed, how do I know which rule suppressed the alert? ⫘
- When viewing an alert detail, at the bottom of the alert, open Alert Data. Inside the JSON, locate the
labels_data.labelsobject, which contains thelabel_idattribute with the rule ID.
A future release will provide the rule name that can be selected to navigate to the rule.
What regular expression features do the rules support? ⫘
- The alert suppression engine utilizes Hyperscan to apply regular expressions. Hyperscan supports the pattern syntax used by the PCRE library
libpcre, described at http://www.pcre.org/. However, not all constructs available inlibpcreare supported. The use of unsupported constructs will result in compilation errors. 1
For domain names or IP addresses, do I need to do anything special to handle the dots? ⫘
- Yes, you need to escape the dots using a backslash. In regular expressions, a dot means to match any single character except newline.
Example: 192\.168\.1\.1 or www\.secureworks\.com
What entities can I match against? ⫘
- The best way to build a suppression rule is to leverage entities listed on an existing alert. To view entities available on an alert when viewing an Alert Detail:
- Open the JSON tab.
- Scroll down to entities and select to expand the JSON object.
- Observe entities listed on the alert.
Note
If the alert does NOT have entities, that alert is not able to be suppressed yet at this time. Efforts are under way to add alert suppression to all alerts.
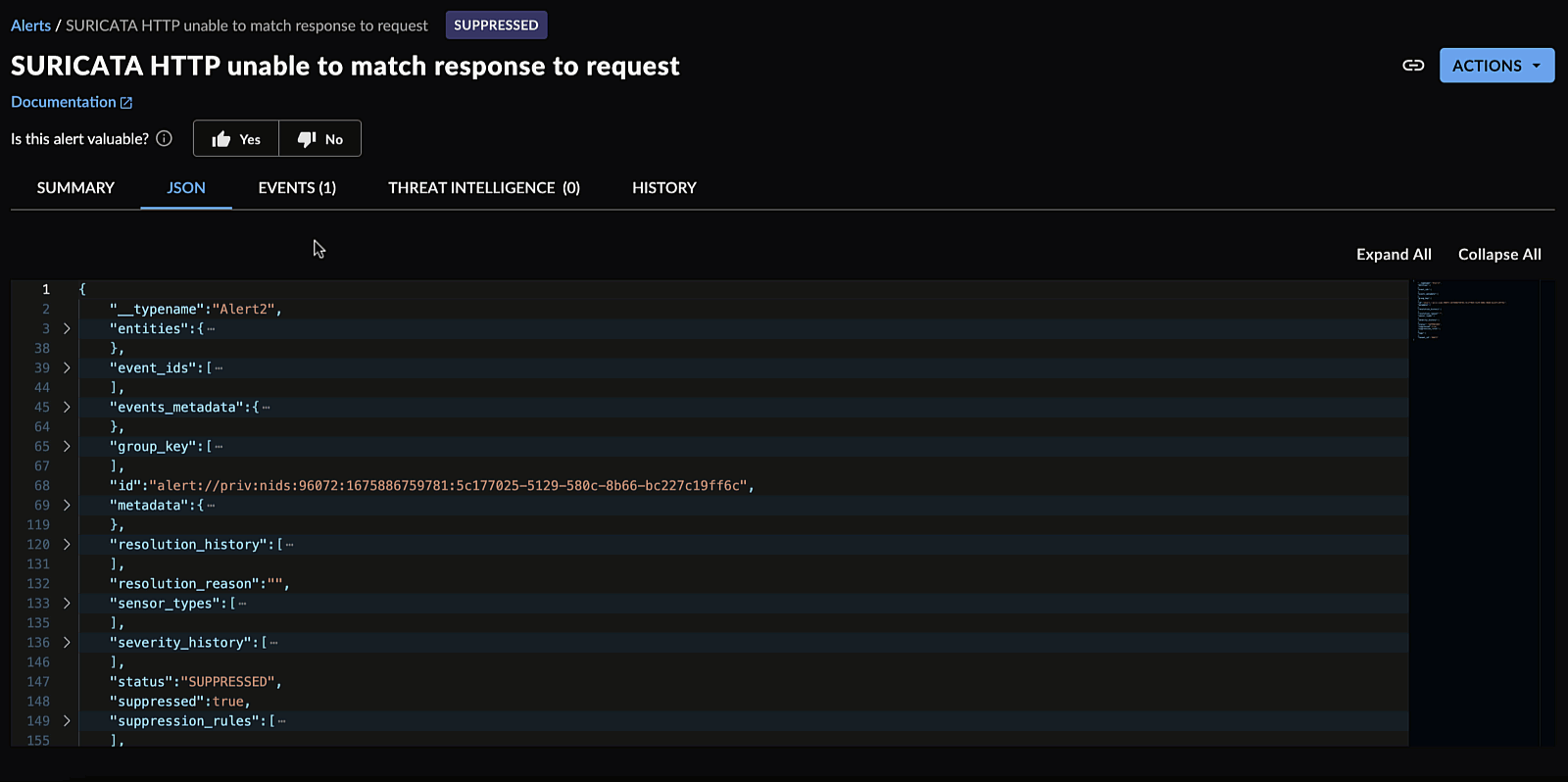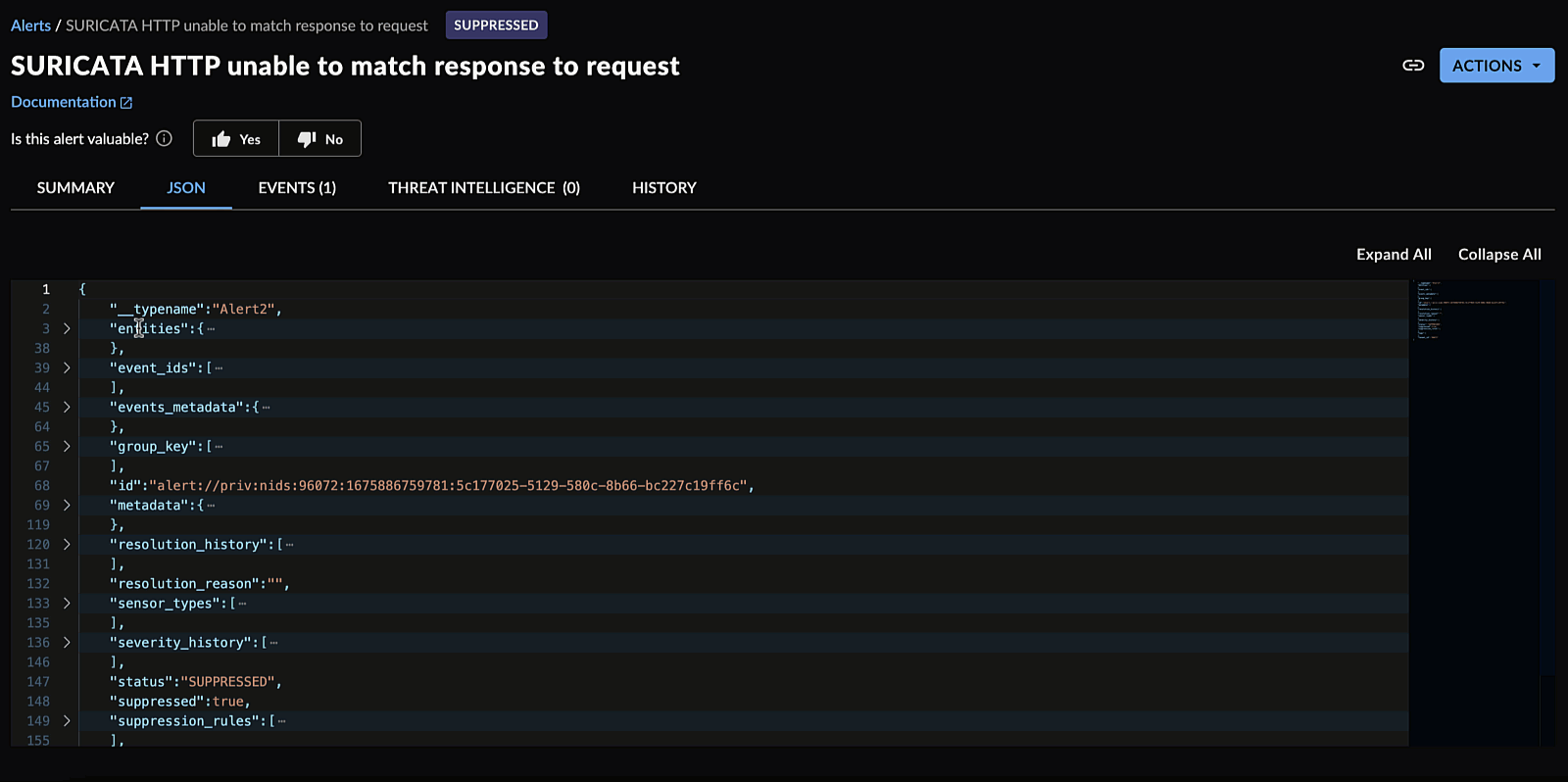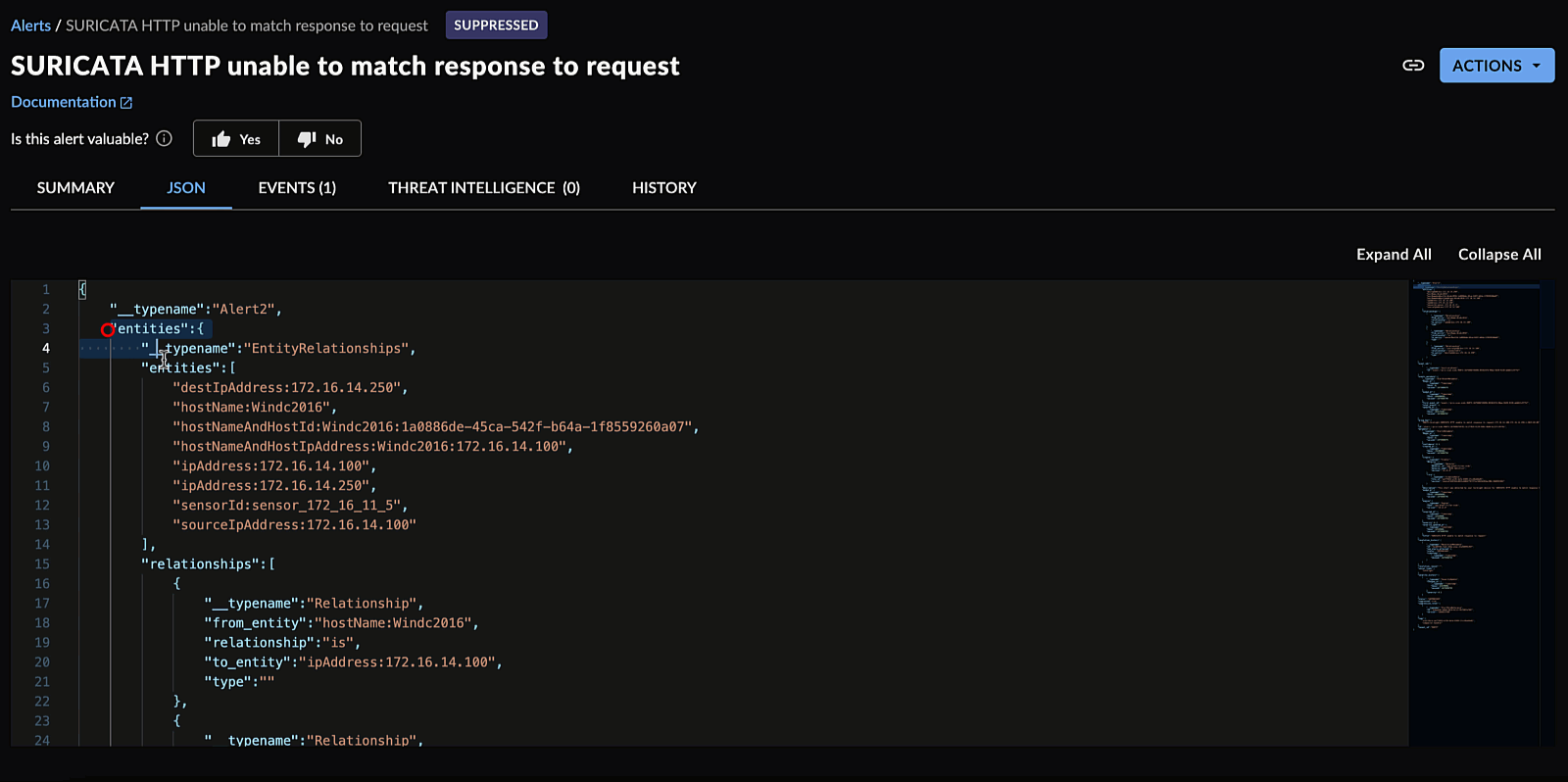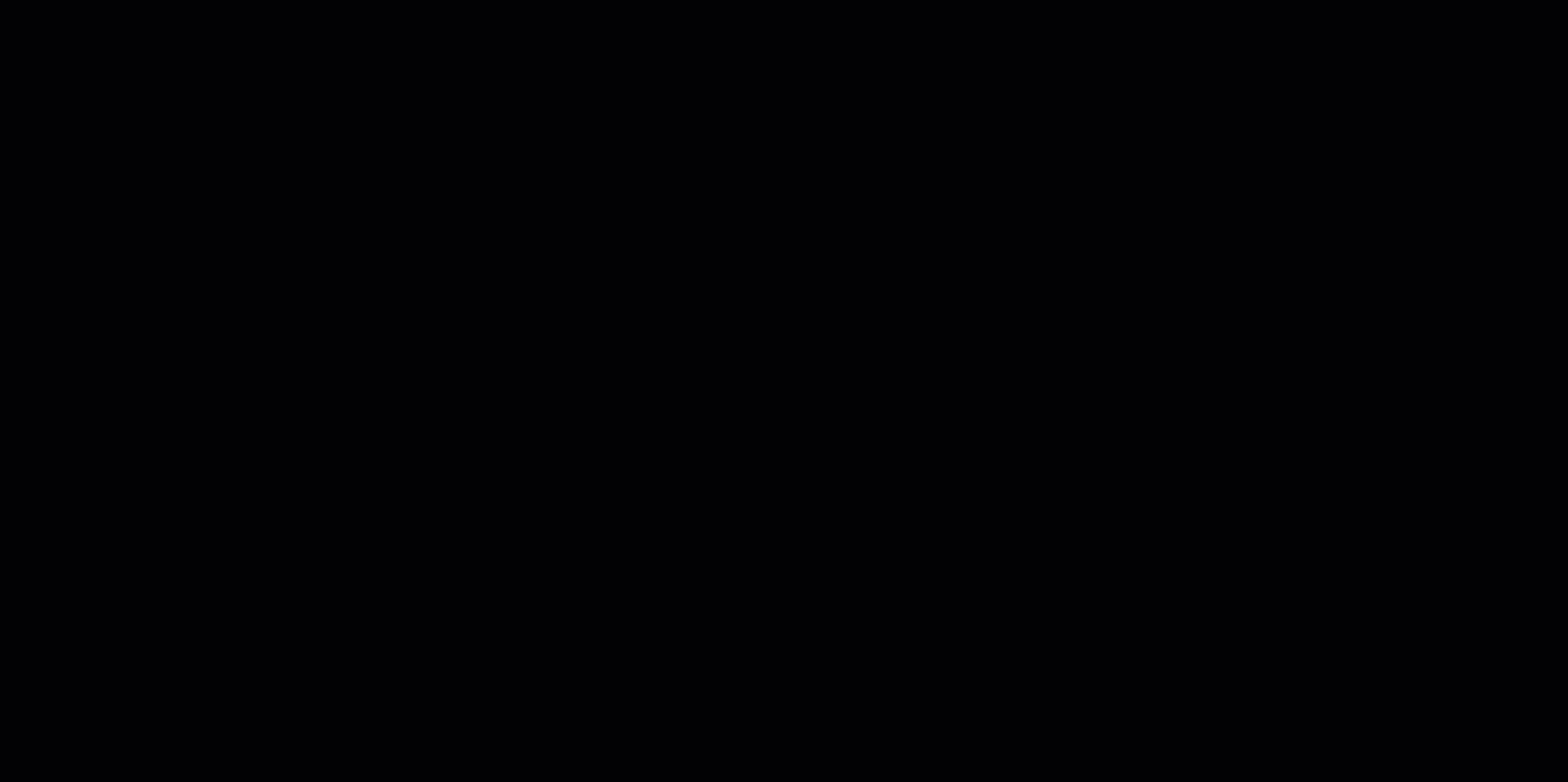
Alert Entities
When building your rule, you can pick entities from a drop down. The following entities can be used to create alert suppression rules. Unique entities are parsed from the individual events included in the alert.
| Entity Prefix | Entity Description |
|---|---|
| authDomainName | Active Directory Domain |
| sourceUserName | Auth Source Username |
| sourceAuthDomainName | Auth Source Domain Name |
| targetUserName | Auth Target Username |
| targetAuthDomainName | Auth Target Domain Name |
| computerName | Computer Name |
| decodedScriptSha1 | Decoded Script SHA1 |
| destHostName | Destination Hostname |
| destIpAddress | Destination IP Address |
| destIpGeo | Destination IP Geolocation |
| destMacAddress | Destination MAC Address |
| dnsName | DNS Name |
| fileMd5 | File MD5 |
| fileName | File Name |
| fileSha1 | File SHA1 |
| fileSha256 | File SHA256 |
| fileSha512 | File SHA512 |
| ipAddress | IP Address |
| city | IP Address Geolocation City |
| country | IP Address Geolocation Country |
| latLon | IP Address Latitude,Longitude |
| macAddress | MAC Address |
| programMd5 | Program MD5 |
| programName | Program Name |
| programSha1 | Program SHA1 |
| programSha256 | Program SHA256 |
| programSha512 | Program SHA512 |
| registryName | Registry Name |
| registryPath | Registry Path |
| scriptSha1 | Script SHA1 |
| sensorHostId | Sensor Host ID |
| sensorId | Sensor ID |
| sourceIpAddress | Source IP Address |
| sourceIpGeo | Source IP Geolocation |
| sourceMacAddress | Source MAC Address |
| topPrivateIpDomain | Top Private IP Domain |
| userName | Username |
| workstationName | Workstation Name |
Which detectors support alert suppression? ⫘
- All detectors and alert sources support suppression.
FAQ for Query Language Advanced Suppression Rules ⫘
Do advanced suppression rules remain enabled if the rule author changes their profile settings back to Production stable? ⫘
- Yes, the rules remain active. The author will be able to view the rule in read-only mode when using Production Stable. To edit the rule, the author must change their profile back to Preview mode.
Are there limitations to using Query Language for advanced suppression rules? ⫘
The following Alert schema fields are not supported at this time:
- enrichment_details
- third_party_details — use
thirdpartyevent schema instead - status
- investigation
How can I create an advanced suppression rule for alerts containing a specific commandline? ⫘
-
To suppress by commandline, use the
process.commandlineschema in the Query Language for the advanced suppression rule.from alert where process.commandline contains 'your_string'
How can I use alert entities in my suppression rules? ⫘
- There are two ways to utilize the alert entities:
-
Use logical types in the query to include the desire alert entity. To suppress by hostname, use
@host.from alert where @host='somehostname' -
Use the entities field directly; when viewing an alert you want to suppress, in the JSON view, open
entities.entities. Use the entire string to match against the desired entity. To suppress by destination IP address:from alert where entities='destIpAddress:128.206.10.3'á
How can I use IP CIDR ranges for suppression? ⫘
- You can now use IP CIDR ranges in your rule’s query. For more details on CIDR notation; please see CIDR Notation
Note
Alert search does not support CIDR ranges, so these queries cannot be built using advanced search. It is recommended to build the query in advanced search without the CIDR ranges and then add the CIDR when ready to pivot into a suppression rule.
