Advanced Search Builder
search queries advanced search builder
Secureworks® Taegis™ XDR’s Advanced Search Builder enables you to search for alerts and events according to queries that you define by choosing operators and defining fields to refine your search.
To access Builder:
-
Navigate to Advanced Search from the left navigation bar.
-
Select Use Builder from the top right of the page.
-
Builder is now your default search preference until you toggle back to Query Language.

Access Advanced Search Builder
Note
The advanced search interface you most recently chose is saved as your default search preference. Use the button at the top right of either Advanced Search option to toggle between them. For example, if you most recently used the Advanced Search Query Language, you may need to select Use Builder from the top right.
Build Search Queries ⫘
XDR’s search grammar allows you to add criteria to filter your search query. For event queries, XDR allows you to select multiple event types. You can then add definitions to that criteria as you need to, to further refine and limit the scope of your search.
When you add new criteria and operators, a visual representation of the query is updated in the gray text below the query builder. Toggle the representation to view it in Builder or Query Language format. You can also add as many terms as you need.
Note
Text entered in search queries is case insensitive.

Search for alerts and events
Construct Your Search ⫘
Advanced Search currently allows you to search for one datatype at a time—either alerts or events. When you create an Advanced search, you must select either Alerts or one or more Event Types using the checkboxes in the Datasource drop-down menu. Available types are:
Data Types ⫘
-
Alerts — Output from detectors based on events or event sets that trigger XDR alerts.
-
Events — Security telemetry from a single point in time.
Event Types ⫘
-
Antivirus Events — Events related to malware activity on hosts and networks.
-
API Call Events — Instances in which a process attempted (successfully or not) to call an operating system API.
-
Auth Events — Activities including login successes & failures, logoffs, etc.
-
Cloud Audit Events — Audit events from cloud-based applications and cloud-hosted infrastructure.
-
DHCP Events — Records of client and server DHCP activity, such as IP address assignments.
-
DNS Events — Records of domain name resolution requests by hosts.
-
Email Events — Events from email security services related to techniques such as phishing and spam.
-
Encrypt Events — Events related to SSL/TLS connection and X.509 certificate metadata.
-
File Modification Events — Instances in which a process attempted to create, modify, write, or delete a file.
-
Generic Events — Stores all raw log messages from syslog and some other ingestion sources. Note that generic events may also get normalized into other event types.
-
HTTP Events — Details on HTTP connections. For example, from proxy server logs.
-
Management Events — Instances in which management information has been accessed from hosts in an enterprise environment, for example, via WMI for Windows.
-
Netflow Events — Network traffic information from in and out of the box communications, including source/destination IPs and ports.
-
NIDS Events — Events from network intrusion detection and/or prevention systems.
-
Persistence Events — Events related to techniques such as Run keys, Scheduled Tasks, or Services, commonly used by attackers to maintain persistence in a compromised system.
-
Process Events — Arbitrary code execution in other live processes. Process events may have information about program launches and their associated command lines, parent/child relationships, and other information about programs and commands executed on the host, including target programs launched by main parent executables—for example, by PowerShell in Windows.
-
Process Module Events — Events generated when libraries have been loaded by different processes.
-
Registry Events — Properties of certain Windows registry entries, which may help to detect attacks.
-
Script Block Events — Executions of blocks of code (scripts) on a remote endpoint by an attacker or other entity.
-
Taegis Agent Events — Detections reported by the Taegis Agent
-
Third Party Alert Events — The event record of alerts produced on sources external to XDR
-
Thread Injection Events — Instances in which a thread has inserted and run code within the memory address space of a different target process.
Note
Alerts may be searched for any time period.
However, event data is treated differently and can be searched for any period of 31 days or less in duration. Event data can be queried either from Advanced Search by choosing any non-Alert Type or from Quick Search. When using either of these ways to query event data, a custom date picker allows you to specify a search time range. From this custom date picker, you can select any start date for which the account may have retained data. But when selecting the end date for the search time range, note that the number of days in the range (the difference between the start and end date) must be less than or equal to 31 days.
Search Rules ⫘
Each search rule is a query composed of one or more terms. If a search rule is composed of multiple terms, then AND logic is applied to them — i.e., all of the specified term matches must occur to return results.
Logical Types ⫘
Logical types are special fields that map to field names under the appropriate data schemas for that particular field category. The logical types are designed to alleviate the need to remember and specify each individual field name for each pertinent schema. Logical types are denoted with the @ prefix. A logical type, specified with @<logical type name>, automatically queries all relevant event fields.
Logical Type Mappings ⫘
The following are the latest logical type mappings:
@command - Command line ⫘
apicall: commandlineauth: commandlinefilemod: commandlineprocess: commandline, commandline_decodedthreadinjection: commandline
@domain - Domain name ⫘
alert: entities prefix - ipDomain, targetAuthDomainName, sourceAuthDomainName, authDomainNameauth: target_domain_name, source_domain_name, extra_targetoutbounddomainnamednsquery: query_name
@hash - Hash/digest ⫘
alert: entities prefix - fileMd5, fileSha1, fileSha256, programMd5, programSha1, programSha256, programSha512auth: process_file_hash, process_file_hash.md5, process_file_hash.sha1, process_file_hash.sha256, process_file_hash.sha512filemod: file_hash,parent_process_file_hash.md5, parent_process_file_hash.sha1, parent_process_file_hash.sha256, parent_process_file_hash.sha512, process_file_hash.md5, process_file_hash.sha1, process_file_hash.sha256, process_file_hash.sha512, file_hash.md5, file_hash.sha1, file_hash.sha256, file_hash.sha512process: program_hash.md5, program_hash.sha1, program_hash.sha256, program_hash.sha512, target_program.sha1_hash, host_program.sha1_hash
@host - Host name ⫘
alert: entities prefix - hostNameauth: target_host_name, extra_targetservername, extra_workstationnamemanagementevent: client_hostname, client_hostname_fqdn, target_hostname, target_hostname_fqdnprocess: process, computer_name
@ip - IP v4/6 address ⫘
alert: entities prefix - destIpAddress, destIpGeo, ipAddress, sourceIpAddress, sourceIpGeoauth: target_address, source_addresscloudaudit: source_addressdnsquery: source_address, destination_addresshttp: source_address, destination_address, true_source_addressnetflow: source_address, destination_address, source_nat_address, destination_nat_addressnids: source_address, destination_address
@mac - MAC address ⫘
http: source_mac, destination_macnetflow: source_mac, destination_mac
@path - File path ⫘
alert: entities prefix - fileNameauth: process_filenamecommand: host_program.path, host_program.user_path, host_program.native_path, program.path, program.user_path, program.native_pathfileinfo: path, user_path, native_pathfilemod: file_namemanagementevent: script_file_pathmemoryallocation: file.path, file.user_path, file.native_pathpersistence: file.path, file.user_path, file.native_path, command.host_program.path, command.host_program.user_path, command.host_program.native_path, command.program.path, command.program.user_path, command.program.native_path, service.image_path, scheduled_task.action.path, shortcut.relative_path, shortcut.working_directory, shortcut.target_path, shortcut.file.path, shortcut.file.user_path, shortcut.file.native_pathprocess: image_path, parent_image_path, allocations.file.path, allocations.file.user_path, allocations.file.native_path, modules.file.path, modules.file.user_path, modules.file.native_path, host_program.path, target_program.path, host_module.file.path, host_module.file.user_path, host_module.file.native_pathprocessmodule: file.path, file.user_path, file.native_pathscheduledtask: action.pathscriptblock: interpreter_pathservice: image_pathshortcut: relative_path, working_directory, target_path, file.path, file.user_path, file.native_paththreadinjection: source_process_name, target_process_name
@port - TCP/UDP port ⫘
auth: target_port, source_porthttp: source_port, destination_portnetflow: source_port, destination_port, source_nat_port, destination_nat_portnids: source_port, destination_port
@raw - Raw log/message data ⫘
- Searches the
original_datafield for all available/applicable event types
@url - URL ⫘
cloudaudit: resources.resource_id
@user - User name ⫘
alert: entities prefix - userNameauth: target_user_name, source_user_name, extra_targetoutboundusername, extra_userprincipalname, extra_virtualaccount, extra_subject_domain_user_id, extra_target_domain_user_idcloudaudit: user_namemanagementevent: usernameprocess: username
Nested Queries ⫘
Nested queries allow you to create more complex searches by grouping together multiple search rules. To construct one, select + Add Group and build your group of rules.
Nested Queries and Match (AND/OR) ⫘
Select OR if you want the search to match Any of your nested queries, or AND to match All of them.
Note
Be sure to apply the AND/OR selection to the intended nesting level of the query, as indicated by the colored lines in the rule builder.

Using a Nested Query
Share Search Results ⫘
You can share a link to the results of an advanced search to provide to other users in your tenant. Select the share ( ![]() ) icon above the search results table and the link to the results copies to your clipboard.
) icon above the search results table and the link to the results copies to your clipboard.
Share Search Results
Note
Anyone you share the results link with must be an XDR user and have an account in the tenant the search is from.
Add a Saved Search to an Investigation ⫘
To add a saved search to an investigation:
- Select Advanced Search from the XDR left navigation menu. Advanced Search displays.
- Select Saved Searches and find the saved search you want to add to an investigation from My Queries or My Organization’s.
- Select the overflow menu icon for the desired query and then choose Create New Investigation to add the search query to a new empty investigation or Add to Investigation to add the search query to an existing investigation.
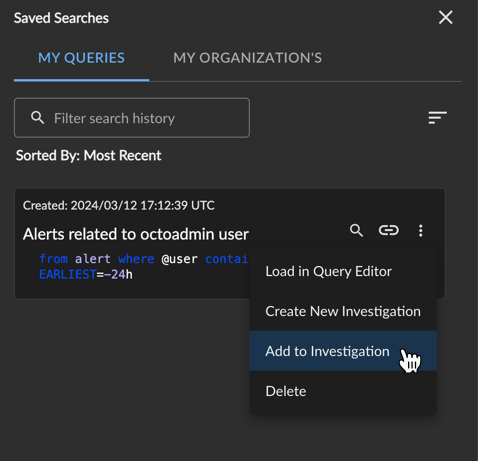
Add a Query to an Investigation
- Follow the prompts for the desired option and select Submit to add the search query.
Note
When you do this, the investigation will include a link to the original search query. Please note that this does not make a copy of the search results. It also does not make a copy of the original alert or event data and does not alter the retention policy for alerts and events.
For more information on this feature, see Link a Saved Search to an Investigation.
Data Retention Policy ⫘
Secureworks retains event and alert data for 12 months from the date the data is received. All other data concerns are covered in the Secureworks Cloud Services Interface Privacy Statement.
Examples ⫘
The following search examples can be used in Advanced Search Builder in XDR. These are a few examples of how you can search and filter your data. They use sensor types along with their supported detectors.
Netflow Searches ⫘
To query network traffic events for a device type (known as sensor_type in XDR) of interest, use type netflow and the desired sensor_type.
Netflow ⫘
[Type: netflow AND sensor_type: is: PALOALTO_FIREWALL]
Netflow Logs for a Specific Cisco ASA ⫘
[Type: netflow AND sensor_type: is: CISCO_FIREWALL_ASA AND sensor_id: is: 10.207.32.7]
NIDS Searches ⫘
To query Network Intrusion Detection events for a device type (known as sensor_type in XDR) of interest, use type nids and the desired sensor_type.
NIDS ⫘
[Type: nids AND sensor_type: is: Watchguard Firewall]
Search for NIDS from Palo Alto Devices with Specific Threat ID ⫘
[Type: nids AND sensor_type: is: PALOALTO_FIREWALL] AND [signature_id: > 10000 AND signature_id: < 30000]
Authentication (Auth) Searches ⫘
To query authentication events for a device type (known as sensor_type in XDR) of interest, use type auth and the desired sensor_type.
Auth ⫘
[Type: auth AND sensor_type: is: CISCO_FIREWALL_ASA]
Search for Auth Logs from Specific Cisco ASA (WebVPN Activity) ⫘
[Type: auth AND sensor_type: is: CISCO_FIREWALL_ASA AND sensor_id: is: 192.168.2.98]
Search for Authentication Events from a Specific Windows Host (sensor_id) ⫘
[Type: auth AND sensor_id: is: CALSDC01]
Search for Azure Authentication Events ⫘
Add Sensor tenant to table details to see the Azure subscription ID.
[Type: auth AND auth_system: is: AzureActiveDirectory]
[Type: auth AND auth_system: is: AzureAD]
For both use:
[Type: auth AND auth_system: starts with: AzureA]
Search for Authentication for a Specific User ⫘
[Type: auth AND target_user_name: is: John.Brown]
Search for Authentication Failure for a Specific User ⫘
[Type: auth AND target_user_name: is: John.Brown AND action: is: FAILURE]
Search for Auth Events from Linux Hosts ⫘
Type: auth AND [sensor_type: is: sshd OR sensor_type: is: sudo]
Search for Authentication from MS Cloud Services ⫘
auth + normalizer contains microsoft
[Type: auth AND normalizer: contains: microsoft]
Last 7 Days
- Looking for authentication data from MS Office 365 or Azure AD

Authentications from MS Cloud Services
HTTP Searches ⫘
To query web events for a device type (known as sensor_type in XDR) of interest, use type http and the desired sensor_type.
HTTP ⫘
[Type: http AND sensor_type: is: 'Watchguard Firewall']
DNSquery Searches ⫘
To query DNS events for a device type (known as sensor_type in XDR) of interest, use type dnsquery and the desired sensor_type.
DNSquery ⫘
[Type: dnsquery AND sensor_type: is: MSDNS]
Search for Named DNS Query/Response Events ⫘
[Type: dnsquery AND sensor_type: is: named]
Process Events Searches ⫘
The following are search examples using XDR’s Advanced Search panel for process events.
process + host_id contains {specified ID} for [selected date range]
[Type: process AND host_id: contains: abc123]
Last 72 Hours
This search is looking for process events tied to a particular host ID that occurred in a very tight time window.
You can also increase the specificity of a process event search. This search looks for cmd.exe:
process + host_id contains {specified ID} + parent_image_path contains cmd.exe for [selected date range]
[Type: process AND host_id: contains: abc123] AND parent_image_path: contains: cmd.exe
Last 7 Days
Process Command Line Search ⫘
process commandline contains echo + commandline contains cmd + commandline contains [string]
[Type: process AND commandline: contains: echo] AND [commandline: contains: cmd AND commandline: contains: test]
Last 7 Days
- Looking for particular command line activity with a nested query.

Process Command Line Search
Multi-Event Searches ⫘
To search for multiple event types at once, select the checkboxes at the left of the desired types from the Datasource drop-down menu.
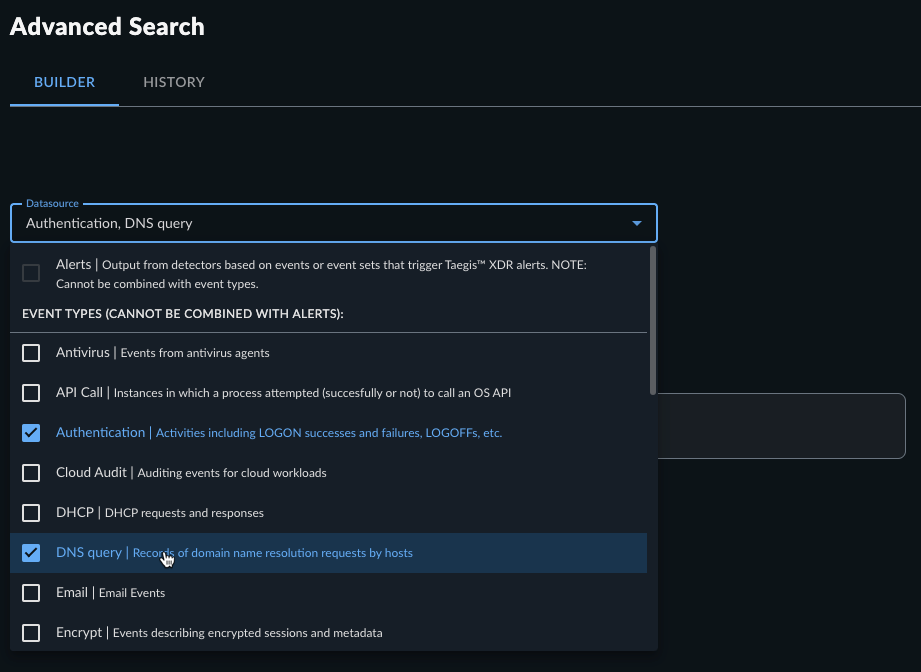
Multi-Event Search
Search for Netflow and Auth Events for a Specific IP ⫘
[ Type: auth,netflow AND @ip: is: 10.10.10.1 ]
Alerts Searches ⫘
alert + [selected date range]
Type: alert
Last 72 Hours
- Quite often you’ll be searching for an alert in a time range.

Search For Alerts In Time Range
Search Alerts by Severity ⫘
You can search by alert severity by selecting the severity term and entering a value between zero and one that aligns to the desired severity percentage. This search looks for alerts that are high or critical severity:
alert + severity >= .6 for [selected date range]
[Type: alert AND severity: >=: .6]
Last 72 Hours

Search For Alerts by Severity
Search Alerts by Integration ⫘
To query alerts for an integration of interest, use type alert and the desired app, alertType, etc.
Search for Kerberoasting Alerts ⫘
[Type: alert AND creator: is: app:detect:kerberoasting-detector]
Search for Alerts from Amazon GuardDuty ⫘
[Type: alert AND alertType: is: aws_guard_duty]
