Cloud Recon to Change Detector
The Cloud Recon to Change Detector identifies unusual exfiltration of AWS RDS and related AWS service data by a user. Secureworks® Taegis™ XDR records users’ API usage at the API action name level, and scans incoming events for behavior that statistically exceeds what has been previously observed. This detector correlates anomalous behaviors for multiple event names, across different categories of event name, to alert malicious activity with higher confidence.
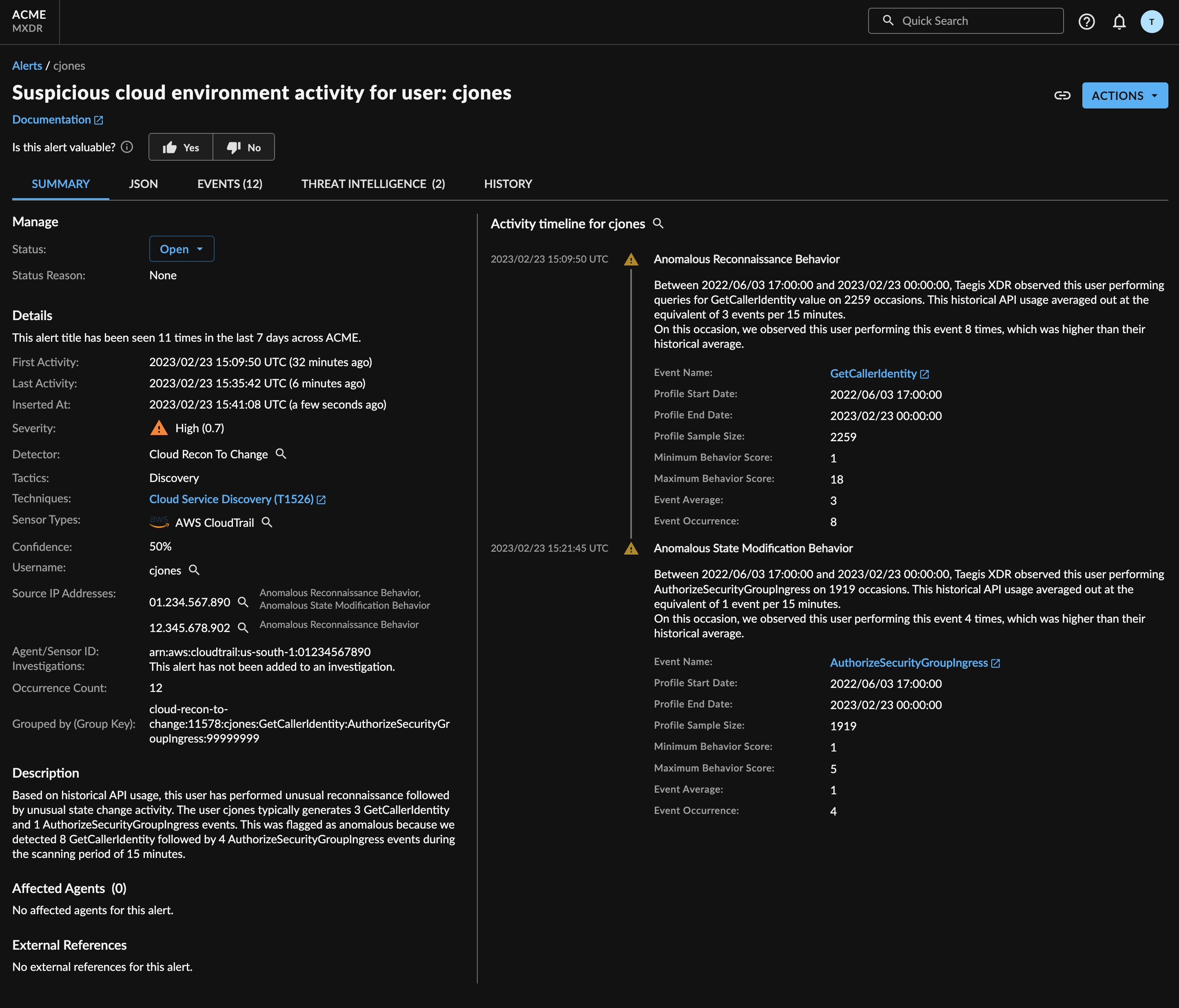
Cloud Recon to Change Alert
Schema ⫘
CloudAudit, by way of detections from input detectors.
Inputs ⫘
Alerts from two sub-detectors:
- Cloud User Unusual Recon
- Cloud User Unusual State Modification
Each sub-detector scans for events in fixed time windows for occurrences where the number of events with the same event name is higher than the number generated by the user. The sub-detectors scan for different sets of event names and uses different thresholds for what is defined as anomalous. Detections from these sub-detectors are not searchable in XDR.
Event names with behaviors categorized reconnaissance or state modification are decided by internal definition. Reconnaissance events are associated with users gathering information in the cloud environment; state change denotes actions where the user copies, deletes, or otherwise changes cloud data.
Reconnaissance and state modification detections are correlated for the same user. If an anomalous reconnaissance behavior is followed by an anomalous state modification behavior within a short window, an alert is created.
The Cloud Recon to Change Detector supports AWS CloudAudit events. The API action logged in the event must be an exact match to one of the reconnaissance or state modification actions that the sub-detectors are scanning for.
Outputs ⫘
Cloud Recon to Change alerts are pushed to the XDR Dashboard.
MITRE ATT&CK Category ⫘
Mitre Enterprise ATT&CK - Cloud Service Discovery. For more information, see MITRE Technique T1526.
