Adversary Software Coverage
adversary software coverage mitre att&ck
Secureworks® Taegis™ XDR’s Adversary Software Coverage enables you to view the coverage provided by XDR detector and event filter rules as mapped to the MITRE ATT&CK® framework. The coverage displays as countermeasures. You can use Adversary Software Coverage to learn how XDR covers you from general threats, such as ransomware, or from something more specific such as the SUNBURST trojanized DLL.
XDR Adversary Software Coverage
How to Use XDR Adversary Software Coverage ⫘
To view XDR’s Adversary Software Coverage, navigate to https://docs.ctpx.secureworks.com/detect/. The default view displays no selections; you can choose from the list on the left-hand side. The MITRE ATT&CK framework provides a curated list of malicious software and the tactics and techniques associated with that software.
Select Software ⫘
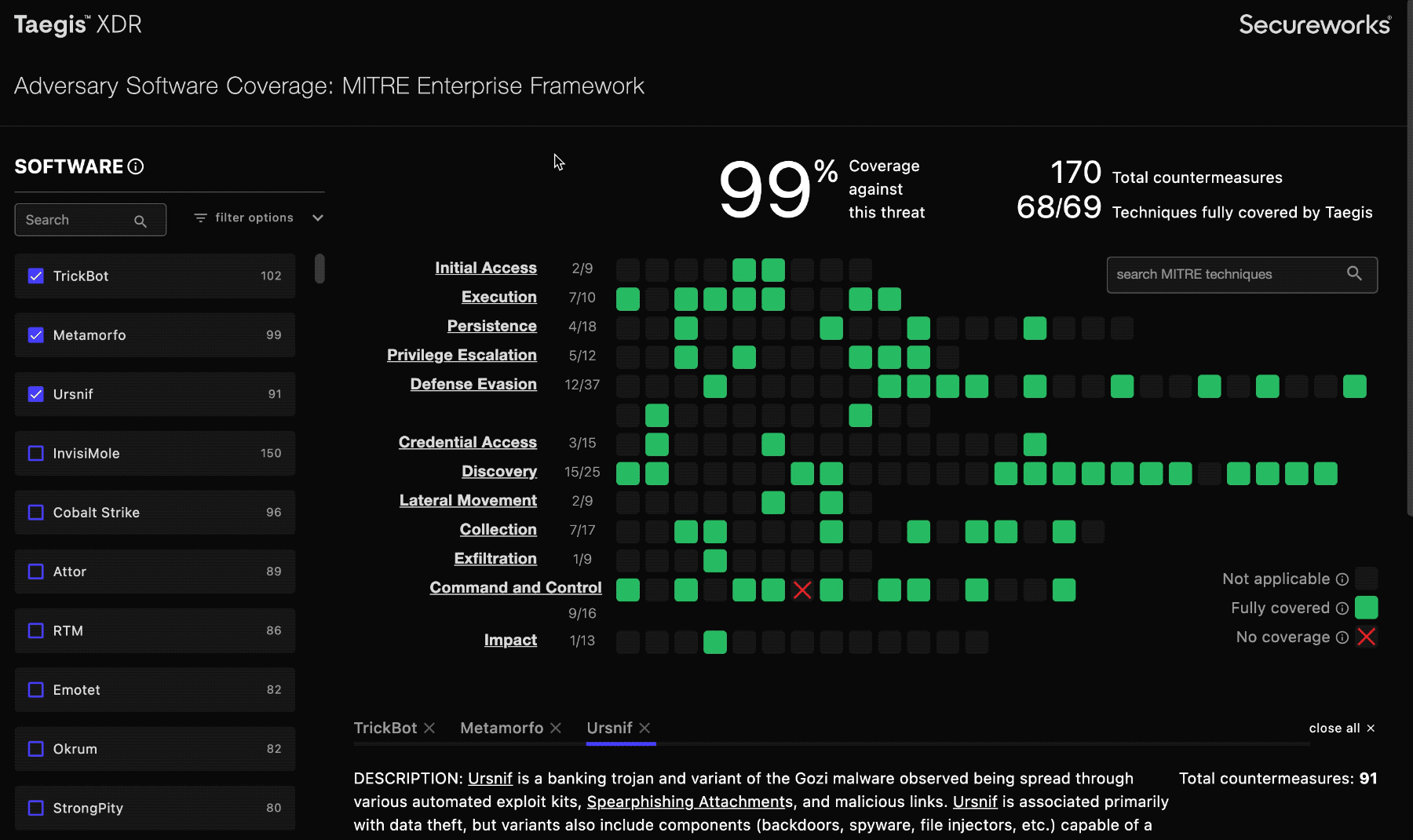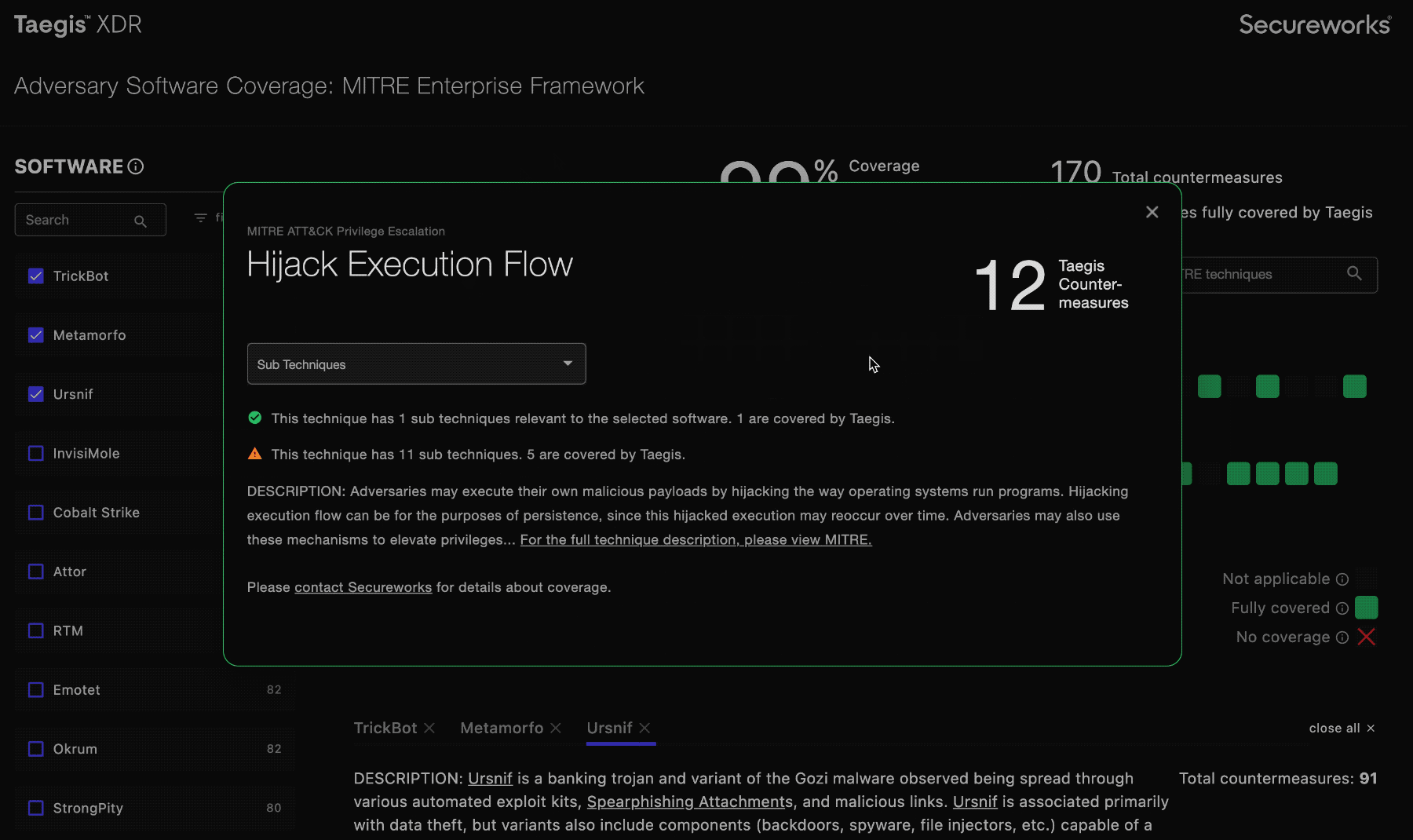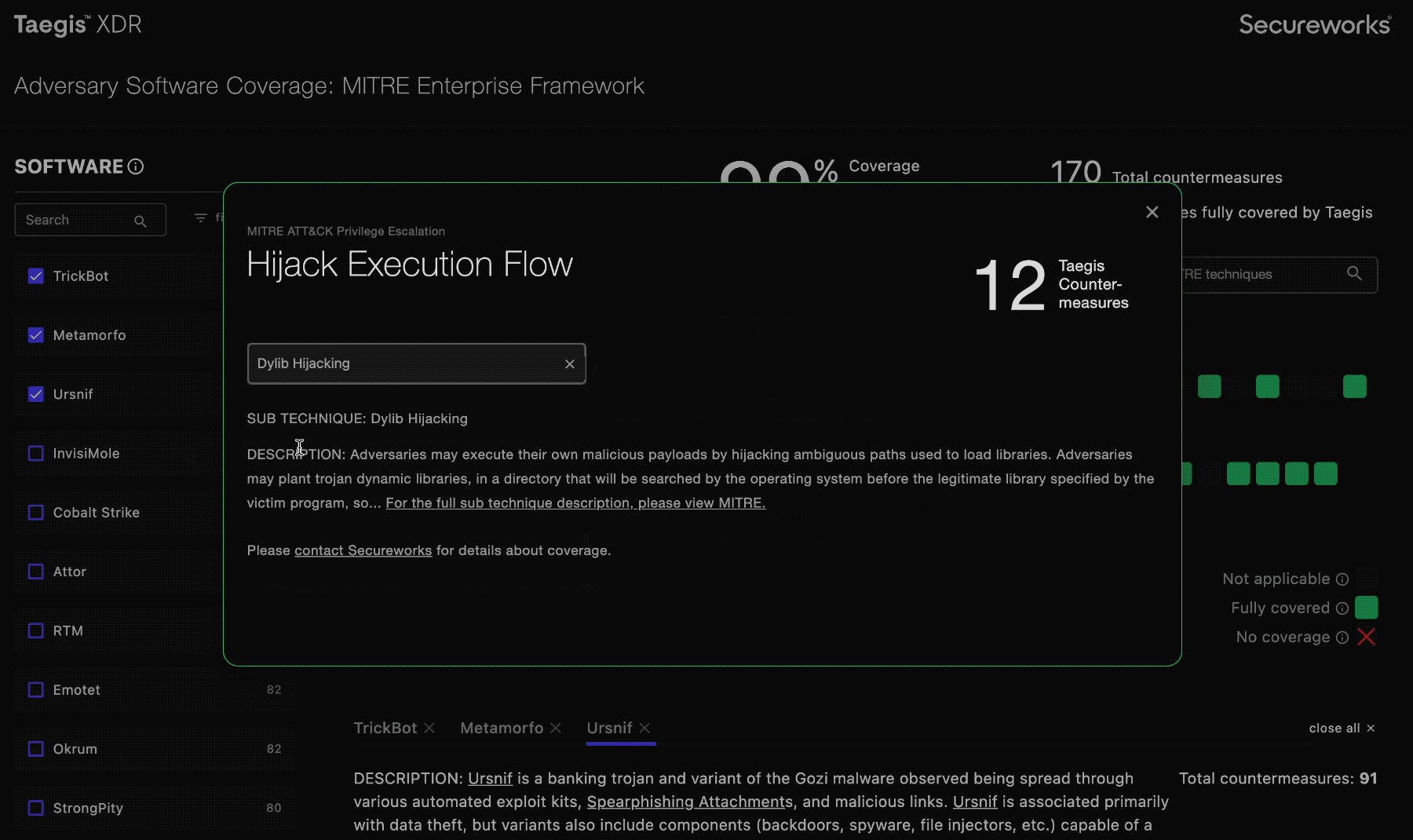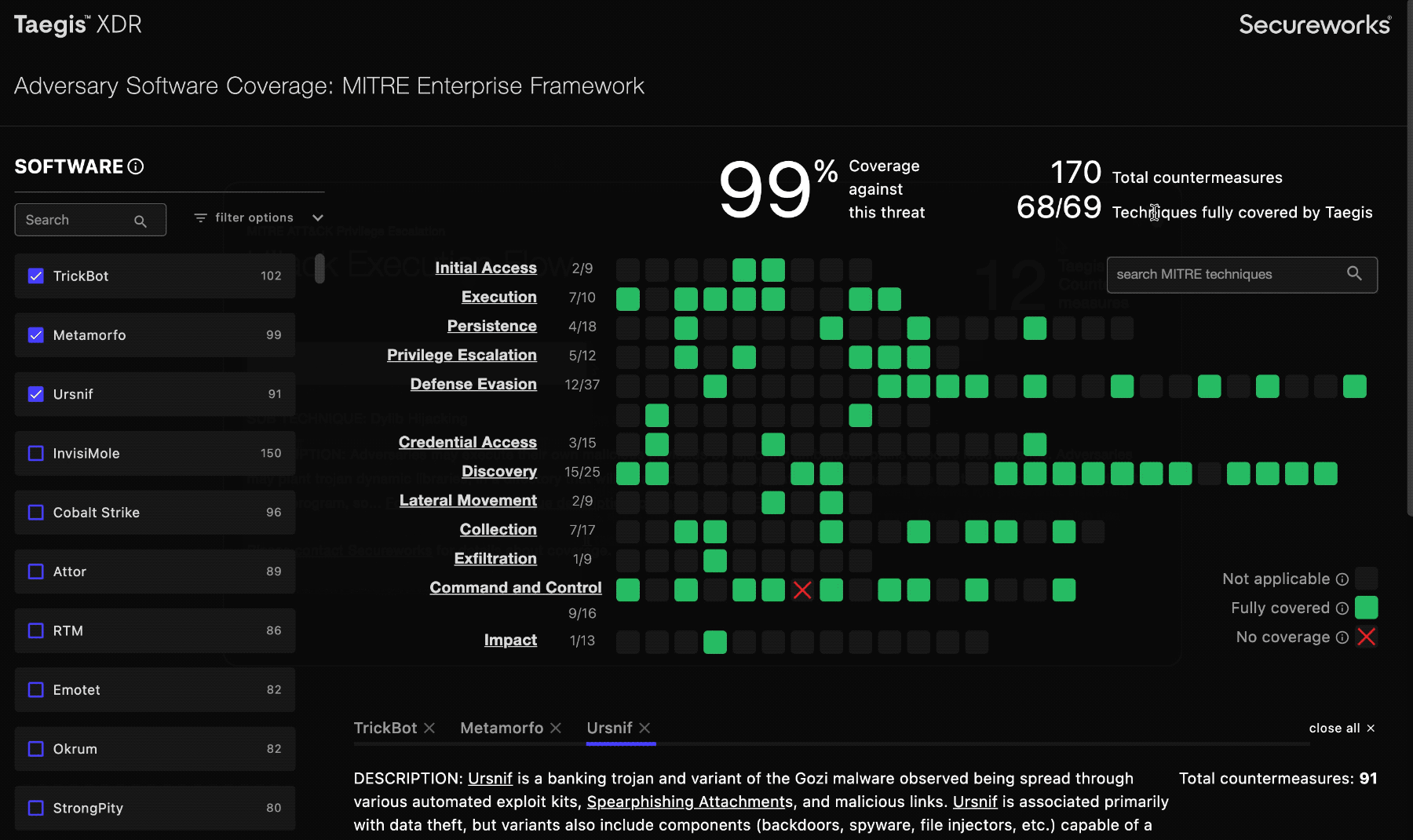
Select from the software list on the left to explore how XDR protects you from adversaries.
Select Coverage
The number to the right of the software indicates the available number of countermeasures XDR and NDR currently have in place against it:
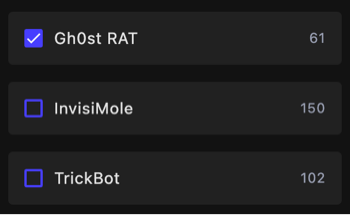
Available Countermeasures
Filter ⫘
Use the filter option pull-down to narrow down the software list according to your use case. You can filter the list by type; the display automatically updates. The number to the right of the software type shows the available countermeasures XDR and NDR have against that threat type.
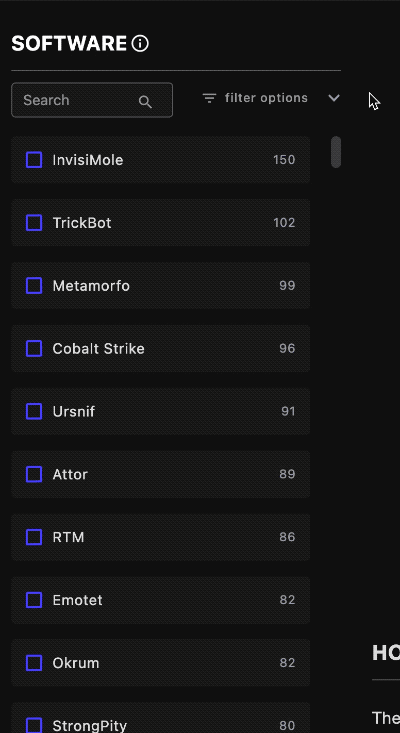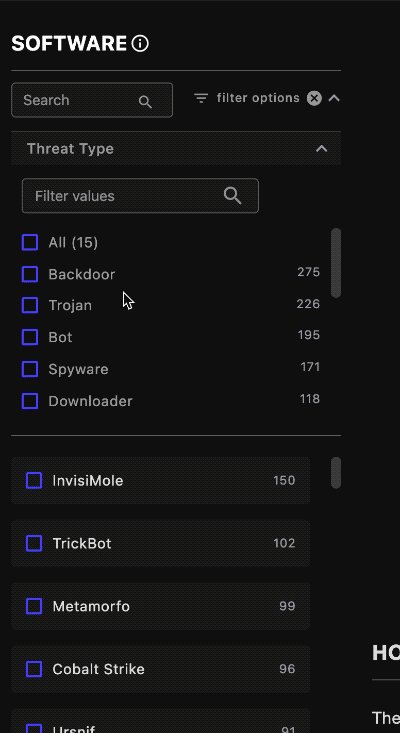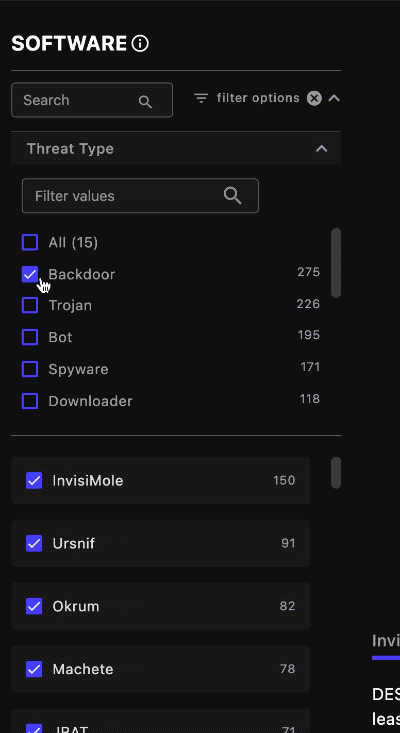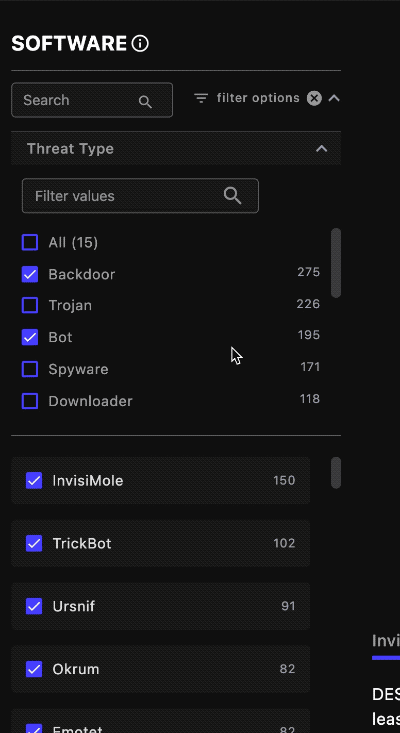
Filter by Threat Type
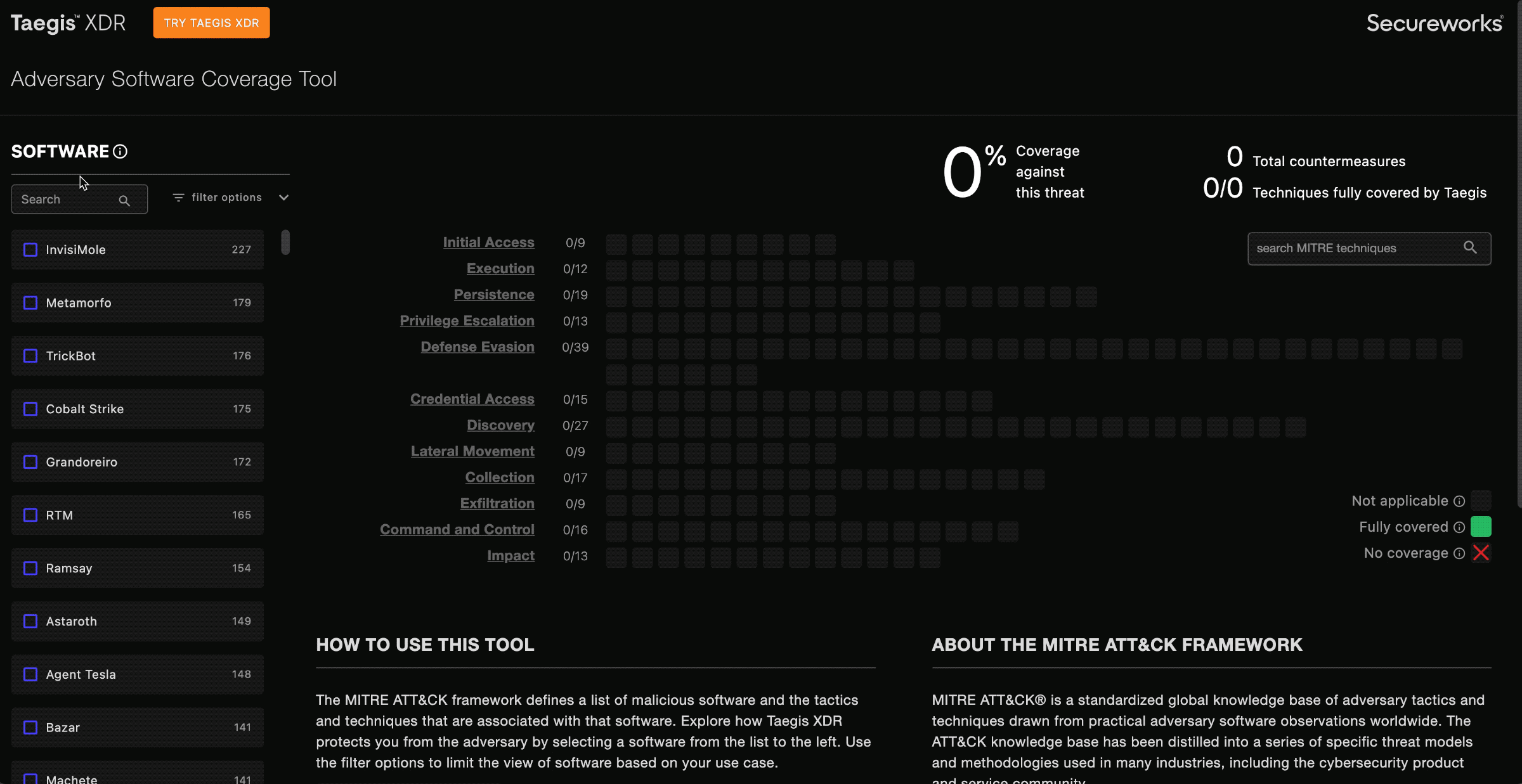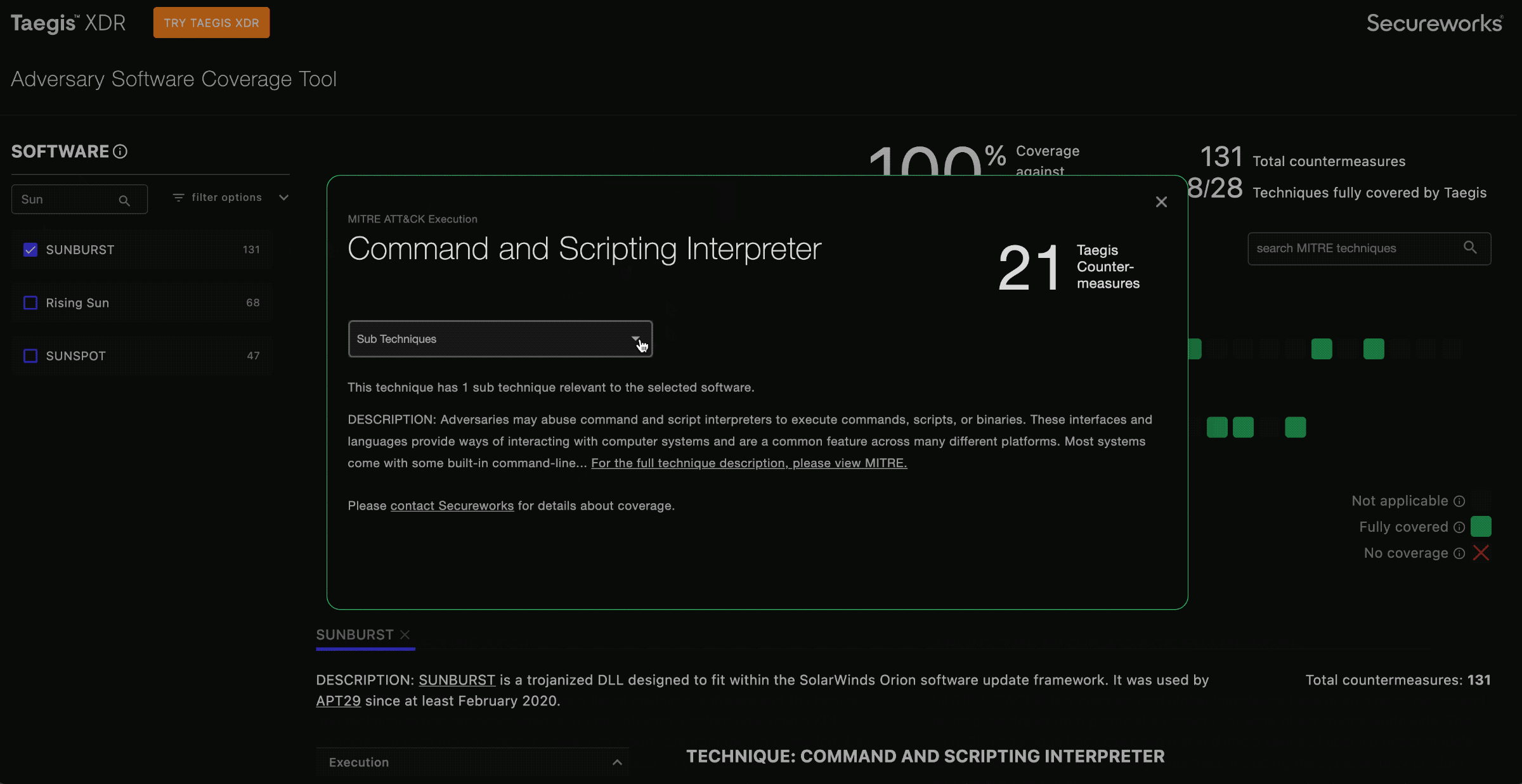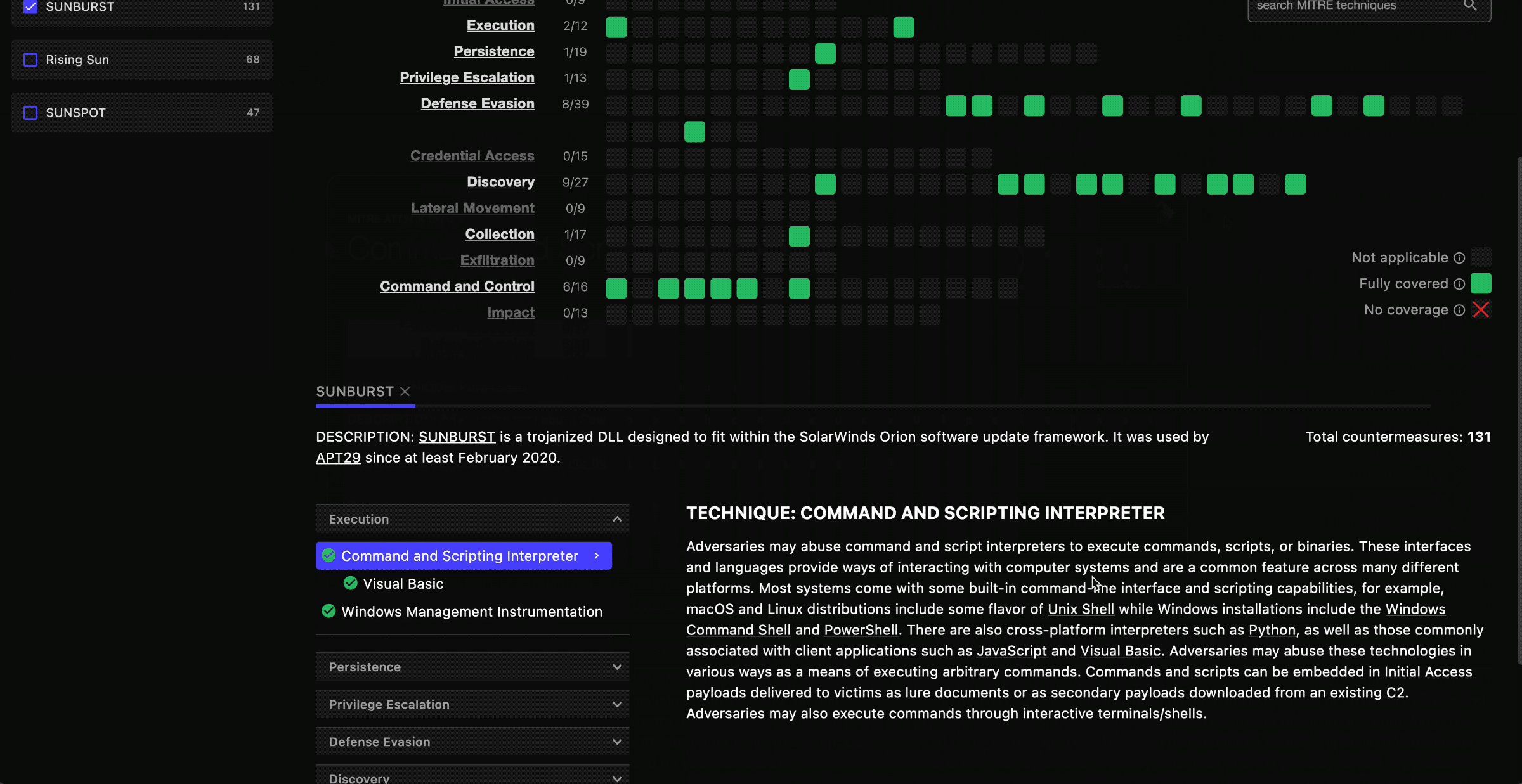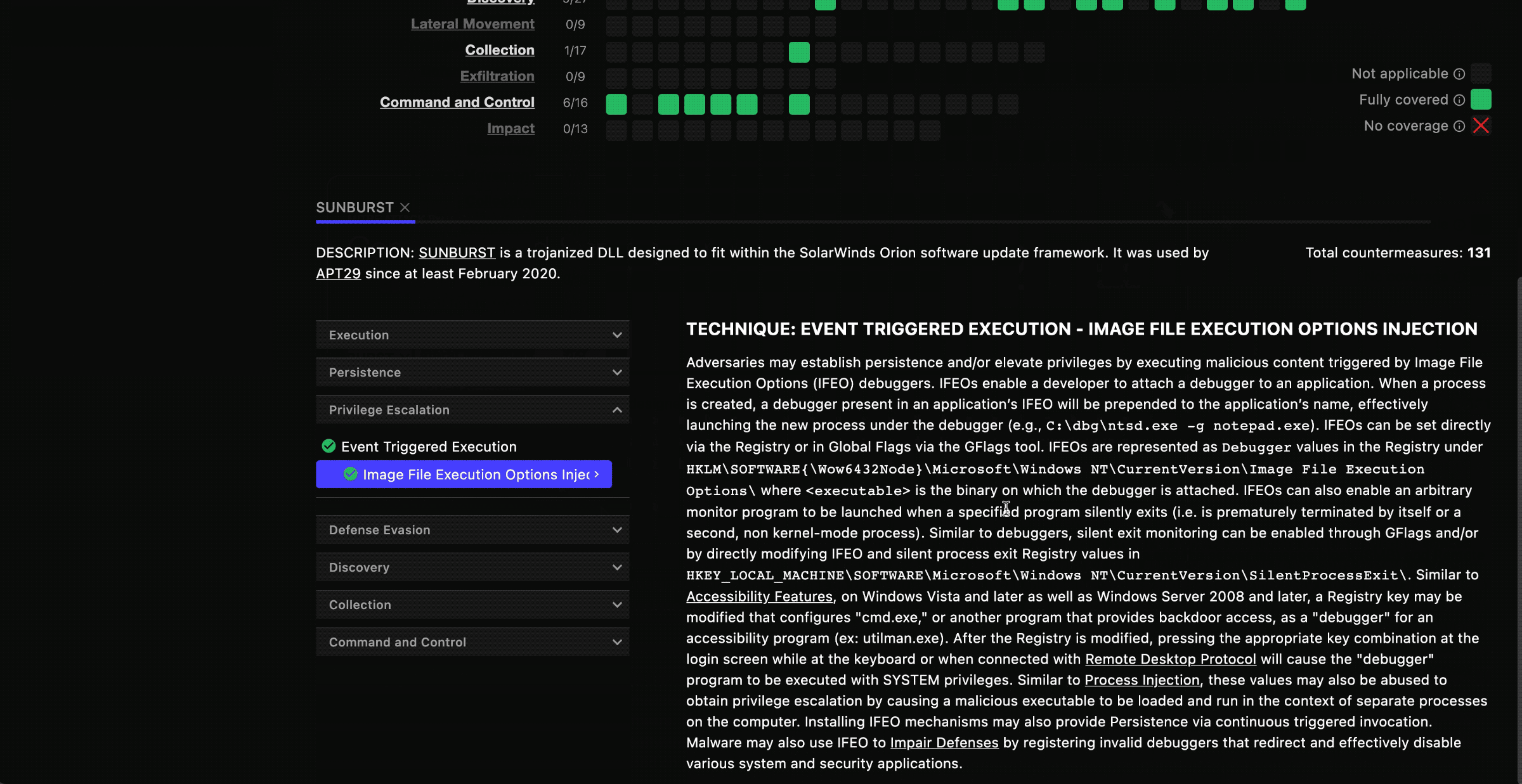
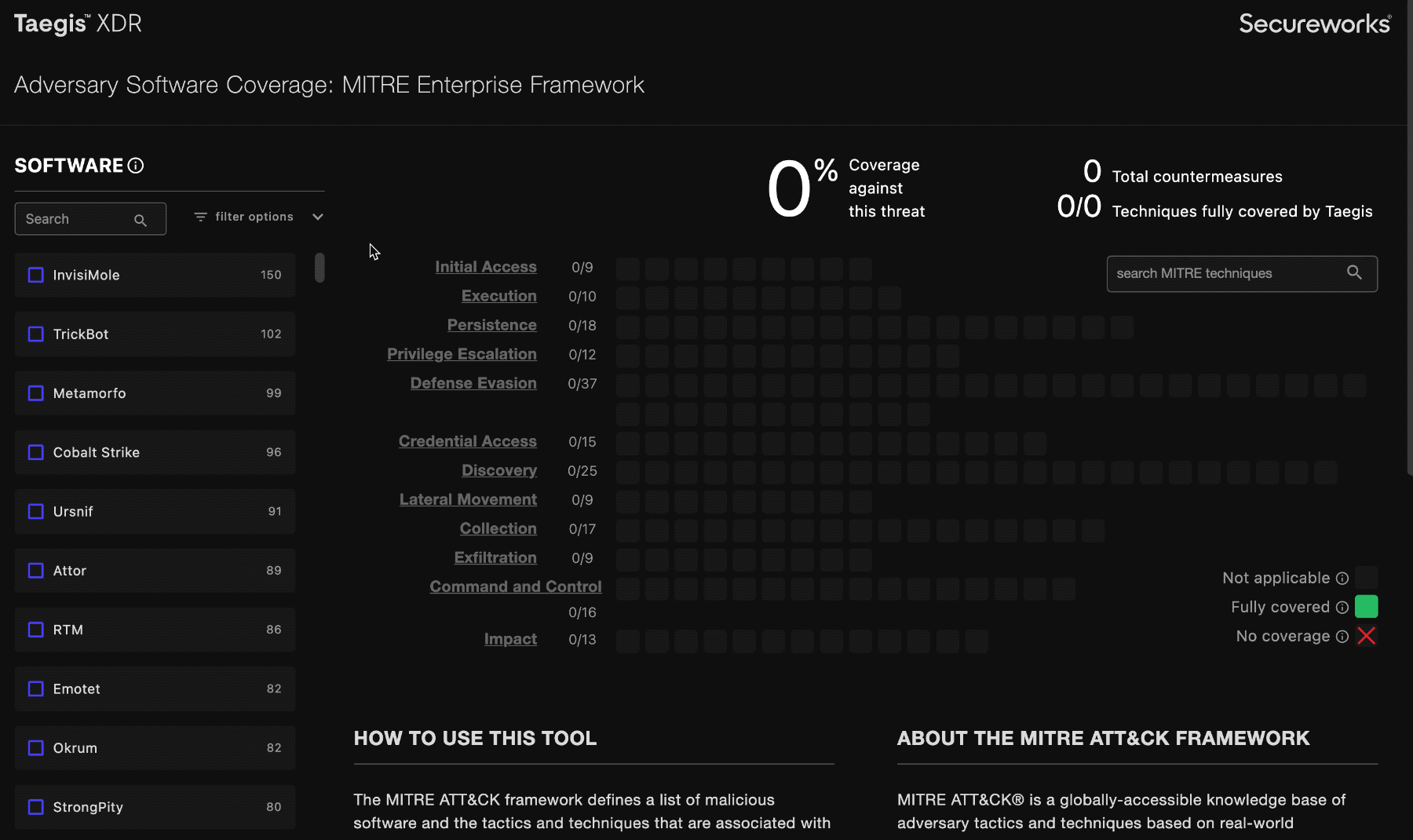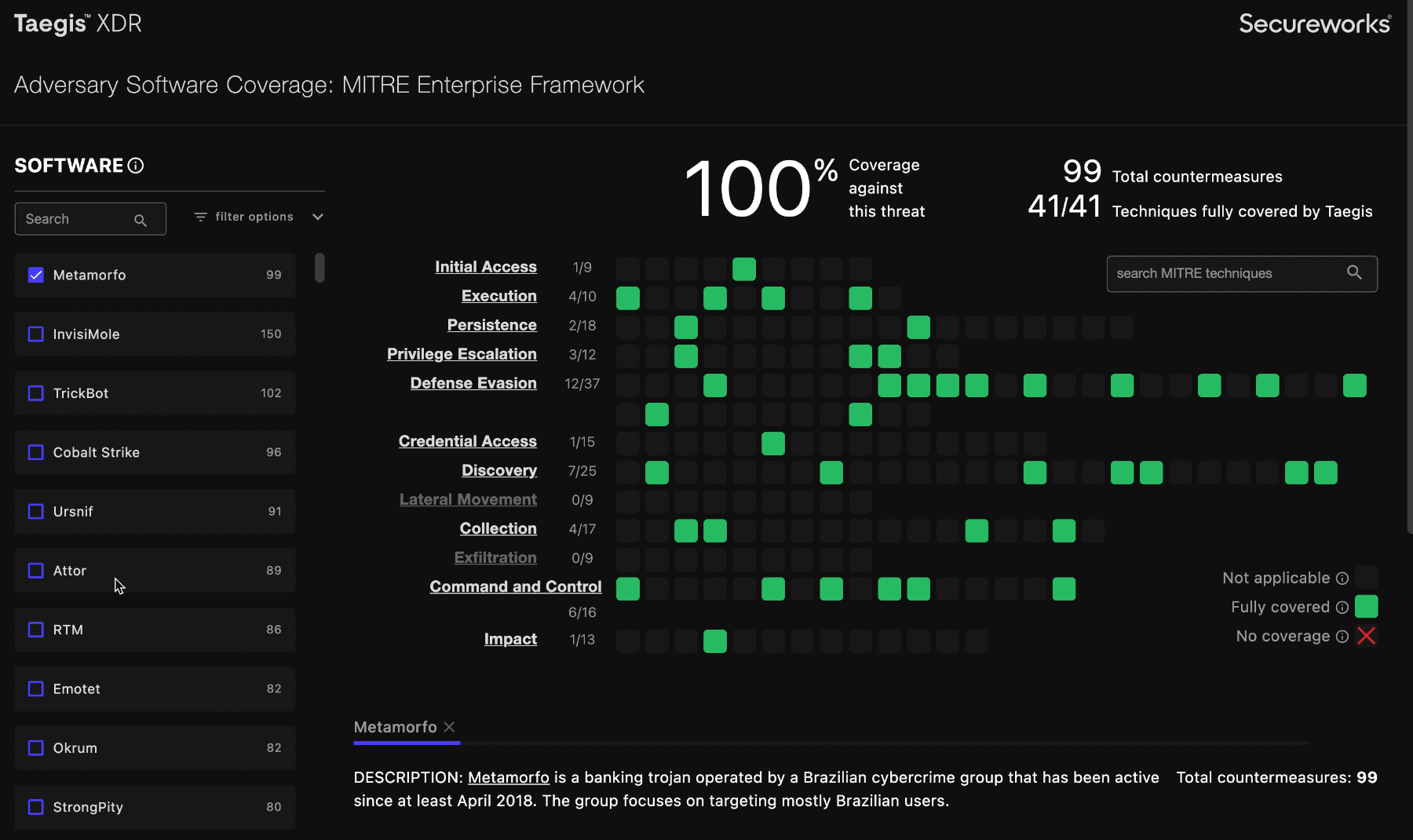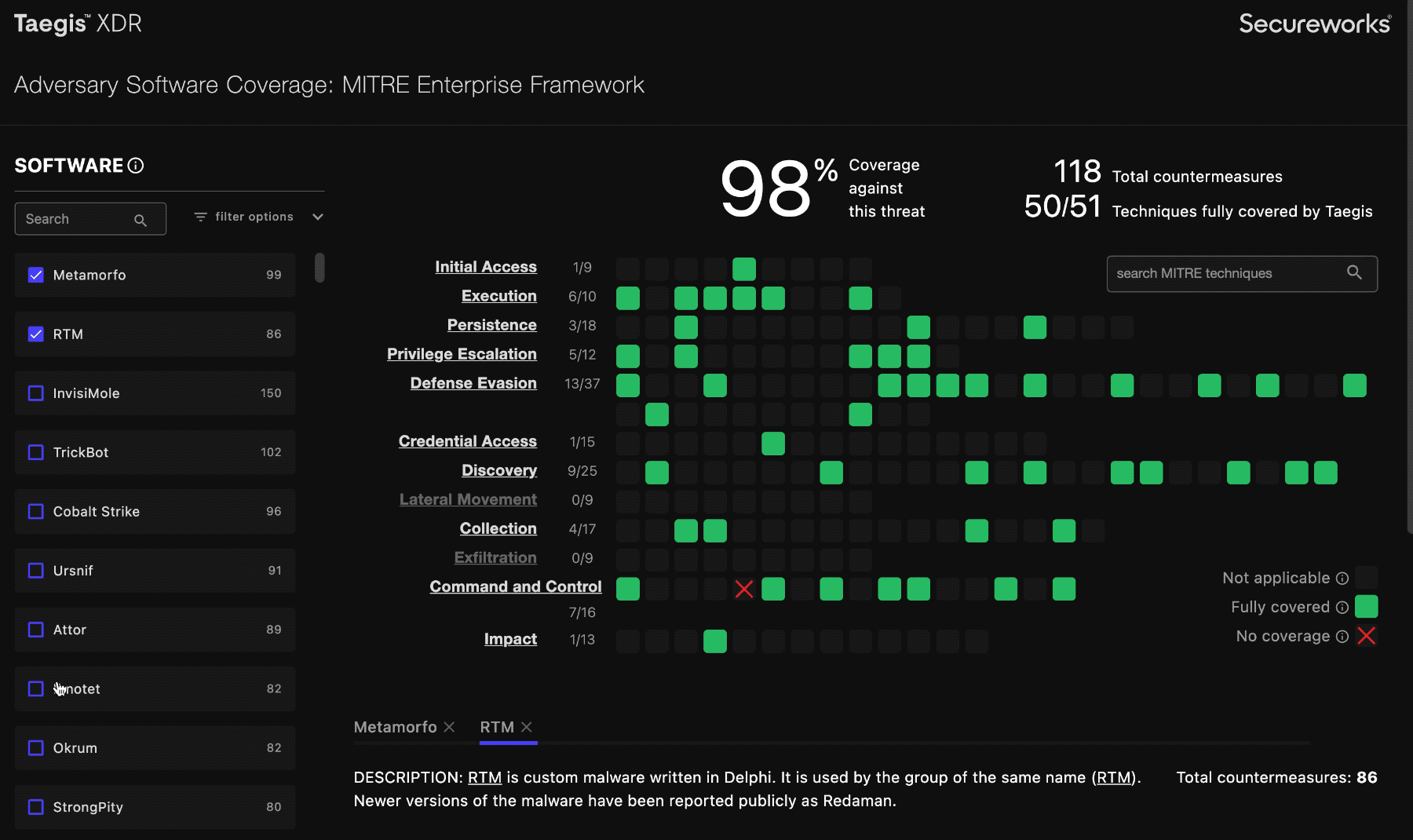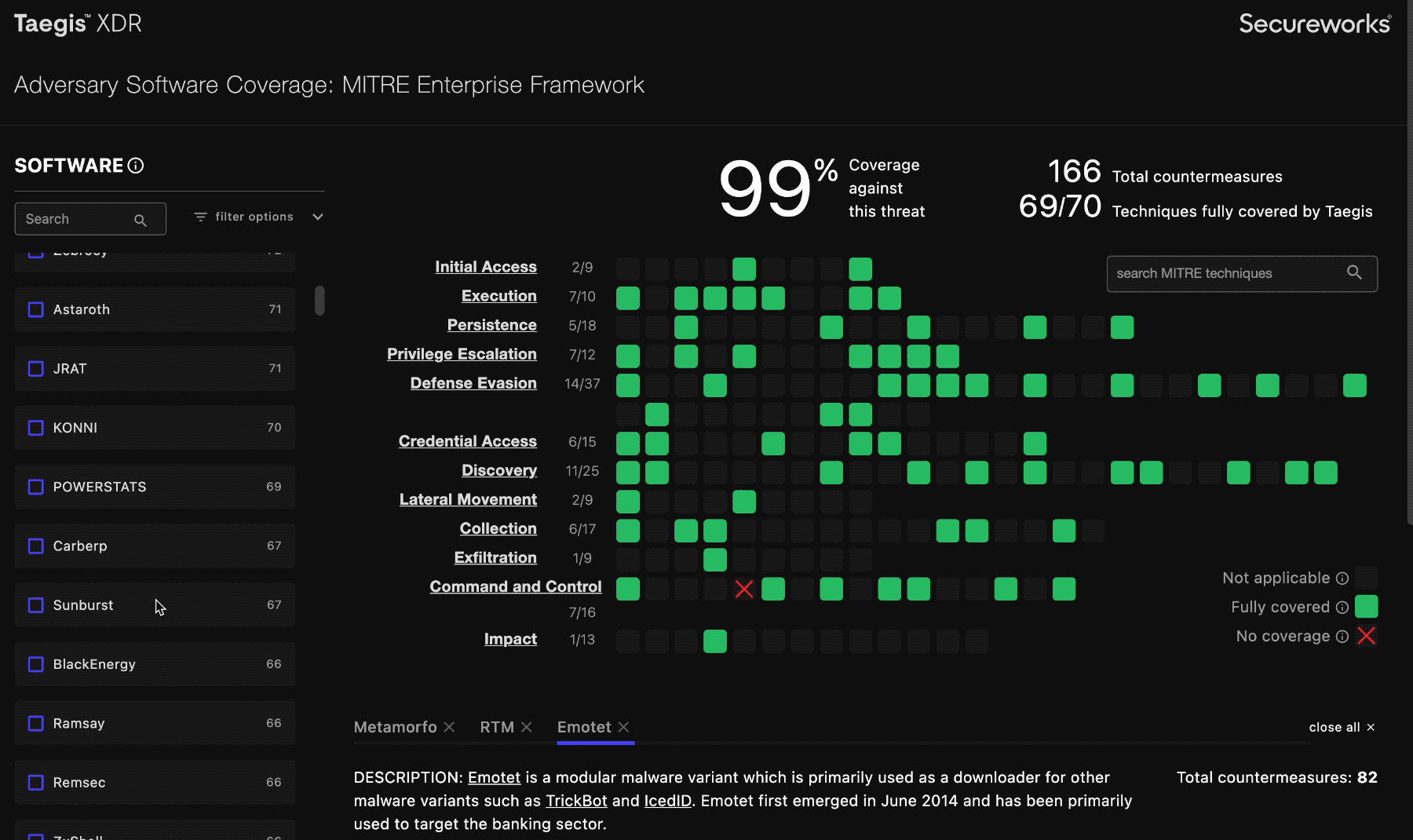
When you select an item from the software list, the coverage grid highlights all relevant techniques with full green to indicate that it’s covered, or a red X to indicate that it is not covered. Techniques that aren’t relevant to the selected software’s attack profile are grayed out.
 indicates that a MITRE technique is used in the software, and is covered.
indicates that a MITRE technique is used in the software, and is covered.
 indicates that a MITRE technique is used in the software, and is not covered.
indicates that a MITRE technique is used in the software, and is not covered.
 indicates that a MITRE technique is not used in the software selected.
indicates that a MITRE technique is not used in the software selected.
Tip
You can click on the squares in the grid to display information about that indicated technique and vulnerabilities that the MITRE ATT&CK Enterprise framework describes.
MITRE Techniques
