Zscaler Integration Guide
Zscaler must be configured to send logs via the Nanolog Streaming Service (NSS) to the Taegis™ XDR Collector.
This information below provides the necessary actions and steps to configure log forwarding on Zscaler NSS.
Connectivity Requirements ⫘
| Source | Destination | Port/Protocol |
|---|---|---|
| Zscaler NSS | XDR Collector (mgmt IP) | TCP/601 |
Data Provided from Integration ⫘
| Antivirus | Auth | DHCP | DNS | Encrypt | File | HTTP | Management | Netflow | NIDS | Process | Thirdparty | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Zscaler Cloud Firewall | D | D |
| Antivirus | Auth | DHCP | DNS | Encrypt | File | HTTP | Management | Netflow | NIDS | Process | Thirdparty | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Zscaler Secure Web Gateway | D | V |
Y = Normalized | D = Out-of-the-Box Detections | V = Vendor-Specific Detections
Note
XDR detectors are not guaranteed to be triggered, even if a data source's logs are normalized to a schema associated with a given detector. However, you can create Custom Alert Rules to generate alerts based on normalized data from a data source.
Logging Configuration Requirements ⫘
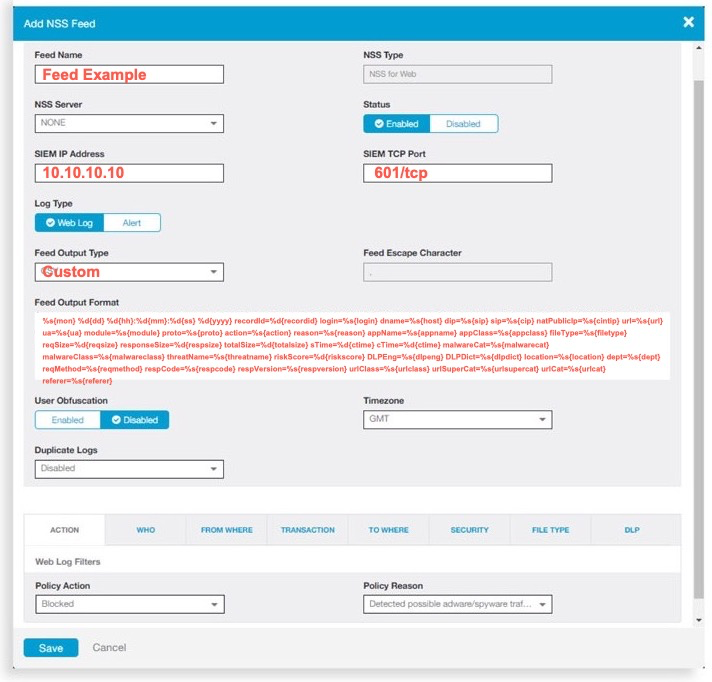
Zscaler Configuration
Note
You can choose any option for the Policy Reason field as it is not used by Secureworks.
Web Logs ⫘
Consider the following requirements when completing the configuration steps for web logs:
- SIEM IP Address — This may be the IP address of the XDR Collector.
- SIEM TCP Port — Enter 601/tcp
- NSS Type — Select NSS for Web.
- Feed Output Type — Custom
- User Obfuscation — Disable
- Feed Output Format — Enter the following string:
NSS_Web_v1 %s{mon} %d{dd} %d{hh}:%d{mm}:%d{ss} %d{yyyy} recordId=%d{recordid} login=%s{login} dname=%s{host} dip=%s{sip} sip=%s{cip} natPublicIp=%s{cintip} url=%s{url} ua=%s{ua} module=%s{module} proto=%s{proto} action=%s{action} reason=%s{reason} appName=%s{appname} appClass=%s{appclass} fileType=%s{filetype} reqSize=%d{reqsize} responseSize=%d{respsize} totalSize=%d{totalsize} sTime=%d{ctime} cTime=%d{ctime} malwareCat=%s{malwarecat} malwareClass=%s{malwareclass} threatName=%s{threatname} riskScore=%d{riskscore} DLPEng=%s{dlpeng} DLPDict=%s{dlpdict} location=%s{location} dept=%s{dept} reqMethod=%s{reqmethod} respCode=%s{respcode} respVersion=%s{respversion} urlClass=%s{urlclass} urlSuperCat=%s{urlsupercat} urlCat=%s{urlcat} referer=%s{referer}
Firewall Logs ⫘
Consider the following requirements when completing the configuration steps for firewall logs:
- SIEM IP Address — This may be the IP address of the XDR Collector.
- SIEM TCP Port — Enter 601/tcp
- NSS Type — Select NSS for Firewall.
- Feed Output Type — Select Custom.
- User Obfuscation — Disable
- Feed Output Format — Copy and paste the following:
time="%s{time}" login="%s{login}" dept="%s{dept}" location="%s{location}" cdport="%d{cdport}" csport="%d{csport}" sdport="%d{sdport}" ssport="%d{ssport}" csip="%s{csip}" cdip="%s{cdip}" ssip="%s{ssip}" sdip="%s{sdip}" tsip="%s{tsip}" tsport="%d{tsport}" ttype="%s{ttype}" action="%s{action}" dnat="%s{dnat}" stateful="%s{stateful}" aggregate="%s{aggregate}" nwsvc="%s{nwsvc}" nwapp="%s{nwapp}" ipproto="%s{ipproto}" ipcat="%s{ipcat}" destcountry="%s{destcountry}" avgduration="%d{avgduration}" rulelabel="%s{rulelabel}" inbytes="%ld{inbytes}" outbytes="%ld{outbytes}" duration="%d{duration}" durationms="%d{durationms}" numsessions="%d{numsessions}"
DNS Logs ⫘
Consider the following requirements when completing the configuration steps for DNS logs:
- SIEM IP Address — This may be the IP address of the XDR Collector.
- SIEM TCP Port — Enter 601/tcp
- NSS Type — Select NSS for DNS.
- Feed Output Type — Select Custom.
- User Obfuscation — Disable
- Feed Output Format — Copy and paste the following:
time="%s{time}" login="%s{login}" dept="%s{dept}" location="%s{location}" reqaction="%s{reqaction}" reqrulelabel="%s{resrulelabel}" reqtype="%s{reqtype}" req="%s{req}" cip="%s{cip}" sport="%d{sport}" durationms="%d{durationms}" sip="%s{sip}" domcat="%s{domcat}"
