Forcepoint Web Security
integrations web security forcepoint
The following instructions are for configuring Forcepoint Web Security to facilitate log ingestion into Secureworks® Taegis™ XDR.
Connectivity Requirements ⫘
| Source | Destination | Port/Protocol |
|---|---|---|
| Forcepoint Web Security | Taegis™ XDR Collector (mgmt IP) | TCP/601 |
Data Provided from Integration ⫘
| Antivirus | Auth | DHCP | DNS | Encrypt | File | HTTP | Management | Netflow | NIDS | Process | Thirdparty | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Forcepoint Web Security | D |
Y = Normalized | D = Out-of-the-Box Detections | V = Vendor-Specific Detections
Note
XDR detectors are not guaranteed to be triggered, even if a data source's logs are normalized to a schema associated with a given detector. However, you can create Custom Alert Rules to generate alerts based on normalized data from a data source.
Configure the Forcepoint Web Security Platform ⫘
Follow the instructions in the Enabling and configuring SIEM integration section on page 3 of Forcepoint Security Information Event Management (SIEM) Solutions to configure log forwarding.
Enter the following information:
| Option | Required Value |
|---|---|
| IP address or hostname | XDR Collector (mgmt IP) |
| Port | 601 |
| Transport protocol | TCP |
| SIEM format | "syslog/CEF" |
Example Query Language Searches ⫘
To search for Forcepoint Web Security events from the last 24 hours:
FROM http WHERE sensor_type = 'FORCEPOINT_SECURE_WEB_GATEWAY' and EARLIEST=-24h
To search for http events associated with a specific URL:
FROM http WHERE sensor_type = 'FORCEPOINT_SECURE_WEB_GATEWAY' and uri_host = 'test.domain.com'
To search for http events associated with a specific source IP address:
FROM http WHERE sensor_type='FORCEPOINT_SECURE_WEB_GATEWAY' AND source_address = '10.19.50.23'
Event Details ⫘
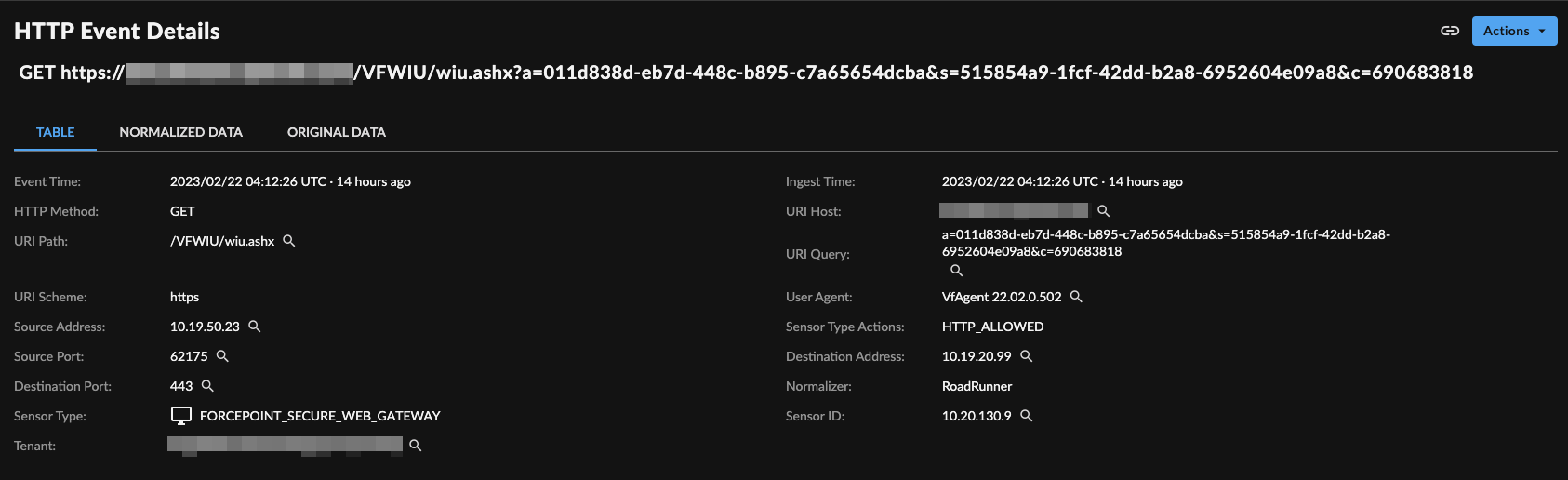
Forcepoint Web Security Event Details
