Microsoft DNS Integration Guide
integrations endpoints microsoft
This guide provides configuration instructions for Microsoft Windows Domain Name Server (DNS) logging in order to transmit the logs for security monitoring by other agents. Supported agents can be found at Connect Microsoft Windows Event Log.
The Secureworks® Taegis™ XDR On-Premises Data Collector accepts logs in the Snare over Syslog format.
Note
XDR parses the Microsoft DNS debug format that can be collected by Snare or NXLog CE.
Microsoft DNS Analytics trace events are not currently supported by XDR.
Connectivity Requirements ⫘
| Source | Destination | Port/Protocol |
|---|---|---|
| Windows server | Taegis™ XDR Collector (mgmt IP) | UDP/514 |
Data Provided from Integration ⫘
| Auth | DHCP | DNS | File | HTTP | Management | Netflow | NIDS | Process | Thirdparty | |
|---|---|---|---|---|---|---|---|---|---|---|
| Microsoft DNS | D |
Y = Normalized | D = Out-of-the-Box Detections | V = Vendor-Specific Detections
Note
XDR detectors are not guaranteed to be triggered, even if a data source's logs are normalized to a schema associated with a given detector. However, you can create Custom Alert Rules to generate alerts based on normalized data from a data source.
Logging Configuration Instructions ⫘
Logging configuration depends on the version of Windows DNS you are running.
Important
The data source must be configured to report timestamps as UTC to ensure that XDR reports the correct time zone.
Note
NXLog CE does not support changing the timestamp into UTC. If that is required, a different product like NXlog Enterprise Edition is required.
Configuring Windows DNS 2008+ Debug Logging ⫘
Note
These steps support Microsoft Windows DNS versions 2008 and later.
Important
As with many diagnostic functions, there may be performance issues when enabling DNS debugging. If you are unsure how enabling Microsoft DNS debug logs will impact your system, Secureworks suggests enabling them on a non-critical system first to determine the impact.
Note that customers who have integrated a XDR-supported Endpoint, Detection, and Response (EDR) solution may forgo Microsoft DNS debug logs, as the EDR solution will provide DNS telemetry sufficient to power XDR detectors for those systems. However, customers should consider other non-EDR systems in their infrastructure that may benefit from monitoring Microsoft DNS debug logs.
- From your Windows machine, go to Start > Programs > Administrative Tools > DNS.
- Within the DNS management console, right-click on the DNS server you are configuring and select Properties.
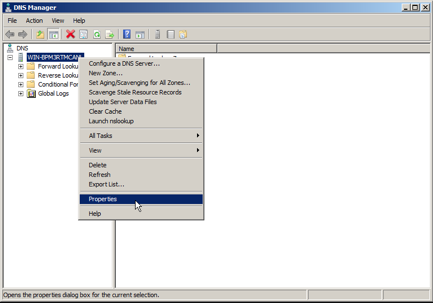
Open DNS server Properties
- Select the Debug Logging tab.
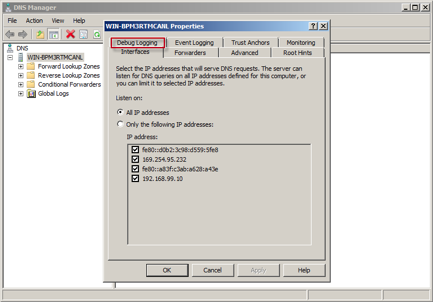
Select the Debug Logging Tab
-
Select the following fields:
- Packet direction — Outgoing and Incoming
- Transport protocol — UDP and TCP
- Packet contents — Queries/Transfers and Updates
- Packet type — Request and Response
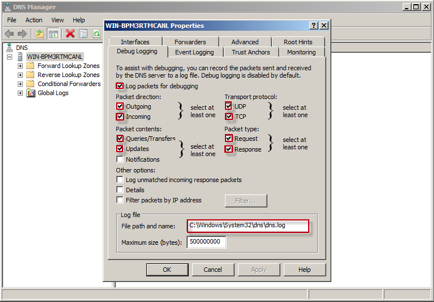
Select the Appropriate Fields
- Under Log File, the default directory path for the log file is C:\WINDOWS\system32\dns\dns.log.
Note
Please note if your log file path is different than the default, as the path is needed when configuring your logging agent.
- Select OK to save your changes. You can now configure your logging agent.
