Remove Cloud Permissions
integrations cloud cloud apis aws amazon
Secureworks integrations leverage a least-privilege model, where the set of permissions requested will allow Secureworks read-only access to the data set to be integrated. Because of this, when an integration is deleted, Secureworks will remove any credentials sent and will stop collection of data; but, access configurations stored externally must be removed manually. This document outlines how users can manually remove permissions and configurations that allow Secureworks access to cloud data.
AWS ⫘
AWS integrations leverage an IAM role to push data via a Lambda function. Since these artifacts are created via CloudFormation, CloudFormation can also be leveraged to remove all artifacts that were created by deleting the CloudFormation stack. Before deleting the CloudFormation stack, any triggers associated with the Lambda function must be removed.
To delete a CloudFormation stack:
- Access the AWS Console.
- Browse to your Lambda services.
Lambda in AWS
- Select Lambda and find the related Lambda function. The name should be
stackname-scwx-tdr-lambda-for-integrationNamewhere stackName is the name of your stack, likecloudtrail-corp, and integrationName is the name of your AWS integration, likeawscloudtrail.
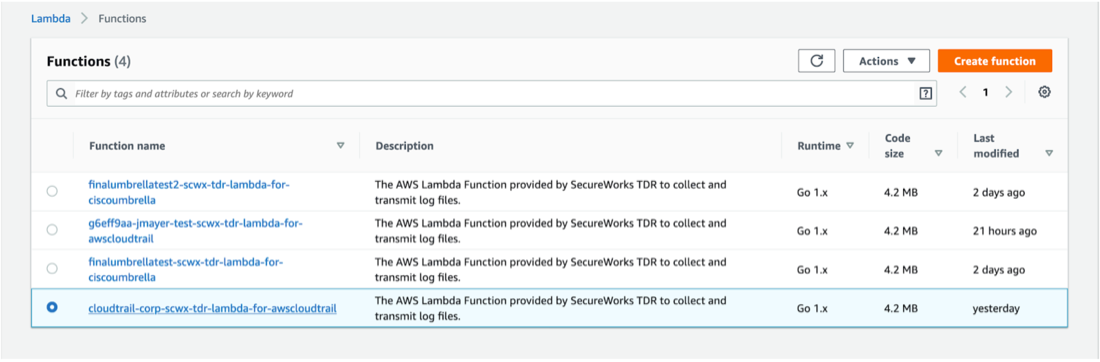
Select the Lambda Function
- Remove the trigger associated with the Lambda function.
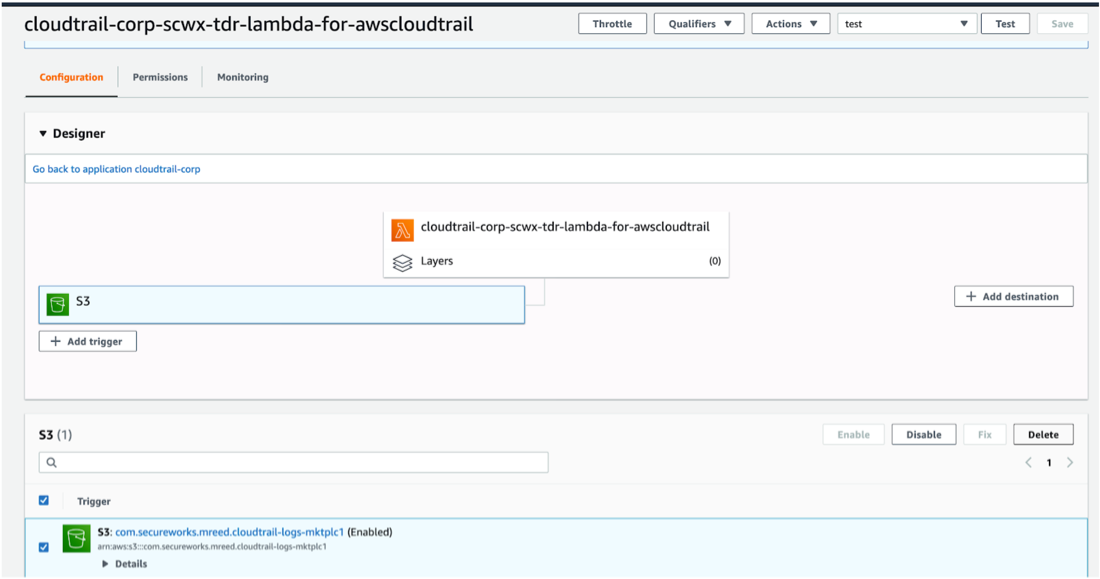
Remove Trigger
- Search for the CloudFormation stack that was created for the integration you wish to delete. The AWS CloudFormation stack name was named by user input at the time of deployment.
- Select the CloudFormation stack by selecting the stack name.
- Select Delete.
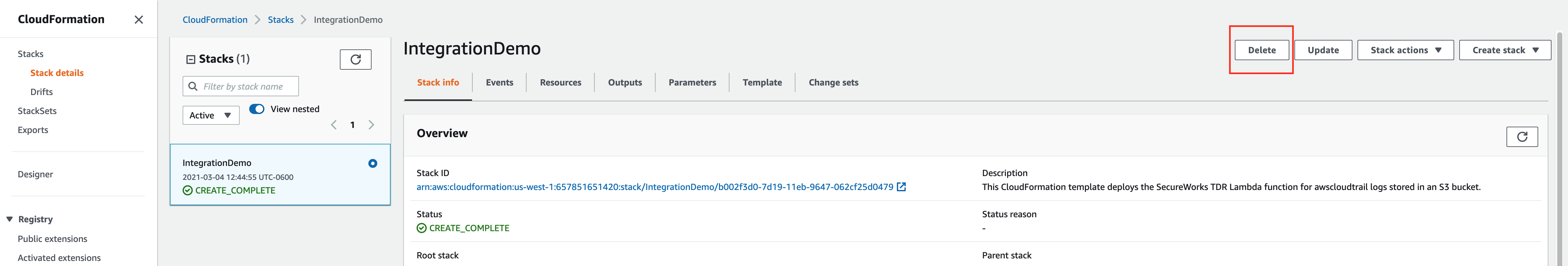
Delete AWS CloudFormation stack
Microsoft Office 365 and Azure ⫘
Microsoft Office 365 and Azure integrations leverage an application consent process to permit Secureworks access to data. Performing consent during the integration copies the application permission manifest into a security principal in the Azure tenant that is being integrated. This local security principal can be deleted to remove access.
To delete a security principal:
- From the Azure Portal, navigate to the Enterprise Applications services screen.
- Search for the application that was integrated. Use the following table to aid in searching:
| Secureworks integration | Application ID | Application Name |
|---|---|---|
| Microsoft 365 | d020ee65-6aec-47ff-b18f-7424c8a631df | RC-TDR - Office 365 |
| Microsoft Azure Active Directory | e6f06a01-1202-4e41-86d4-6a0cb45011e3 | RC-TDR - Azure AD Audit |
| Microsoft Graph Security | cc4b19d5-2bcf-48d0-9633-fc1725d4f484 | RC-TDR - Graph Security |
| Microsoft Azure Activity |
|
Secureworks Taegis - Azure Activity Logs Integration |
- Select the service principal. Navigate to Manage > Properties and select Delete.
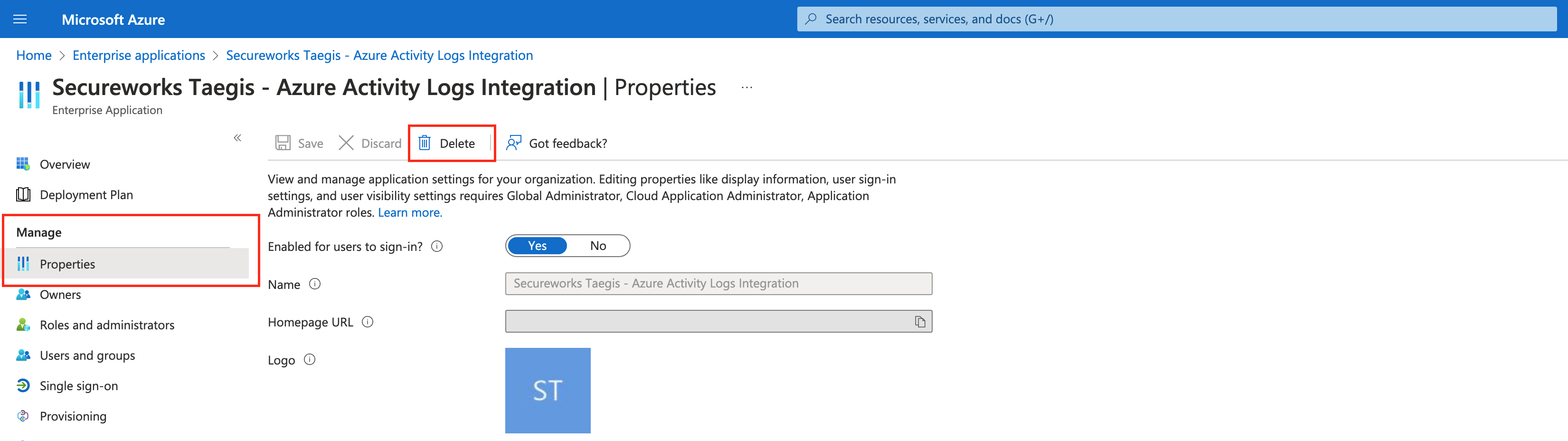
Delete Azure Service Principal
Okta ⫘
Background ⫘
Taegis obtains logs from Okta by creating an application by the client credential grant flow.
Removal instructions ⫘
To remove the Okta API integration completely you must:
- Delete the intergration from the Taegis portal, taking note of the service account name and the Org URL.
- Delete the application created by Taegis in the Okta UI by either an API call or via the UI.
