Event Details
Event Details are visible in search results, Investigations, and from Alert Detail panels. What details are displayed for each event vary by event type and available data.
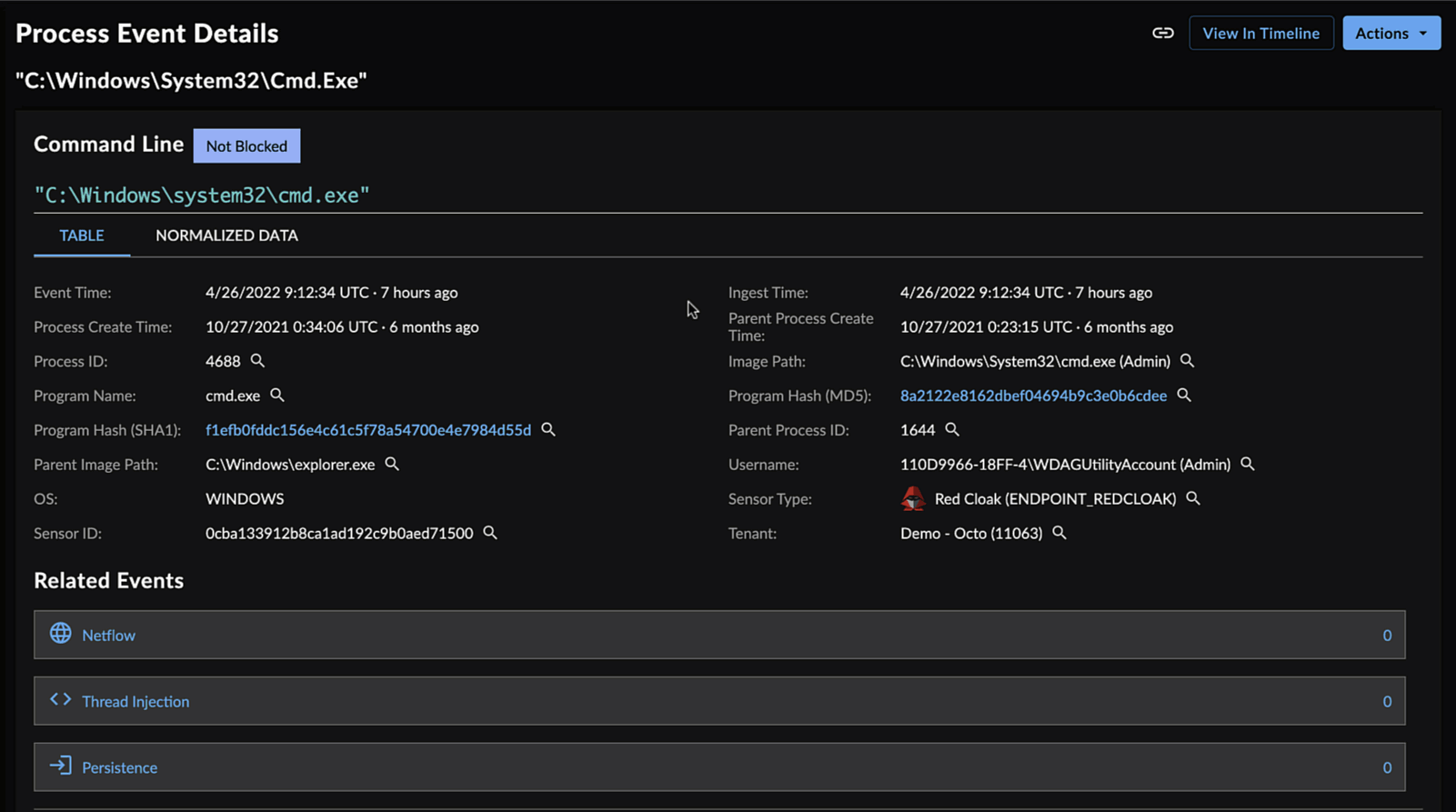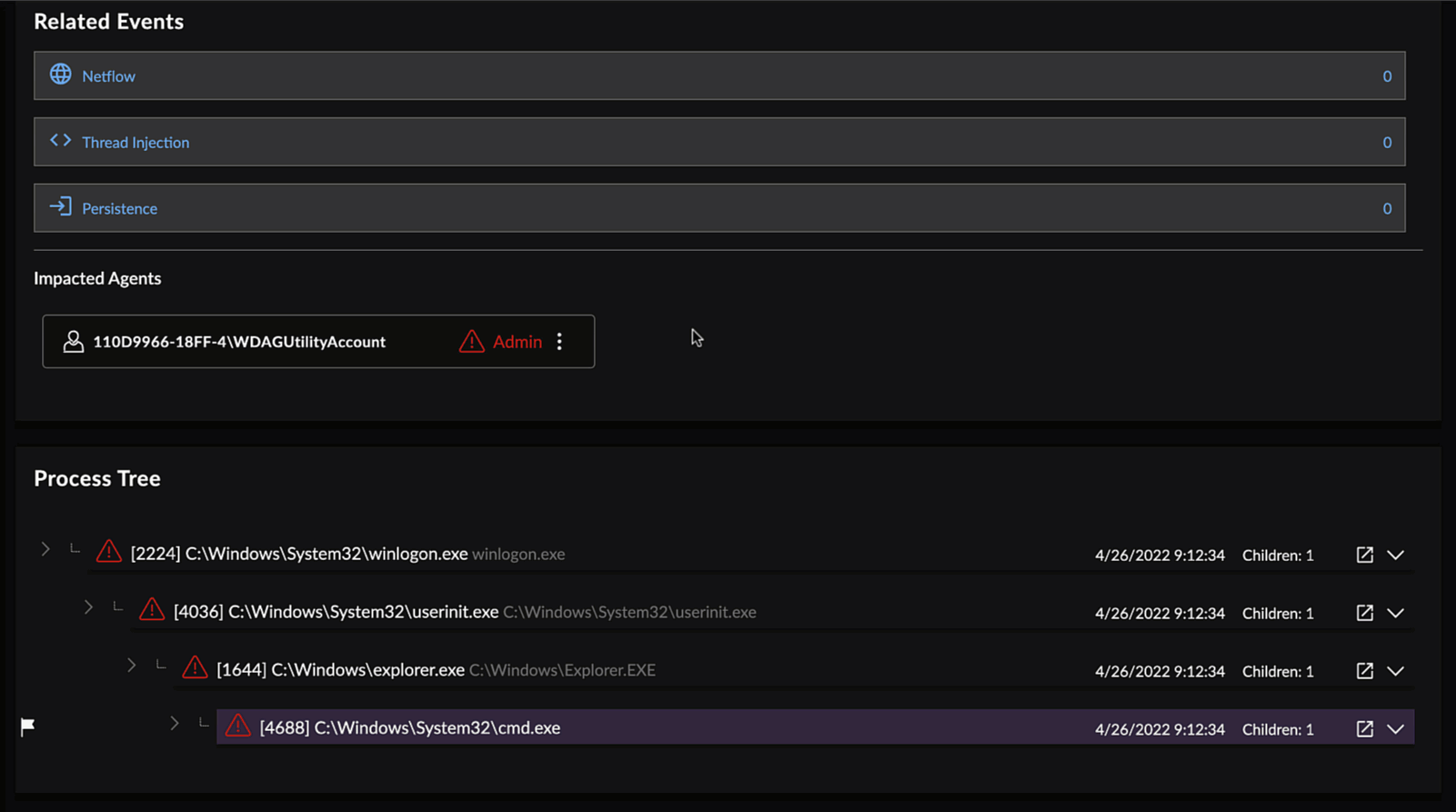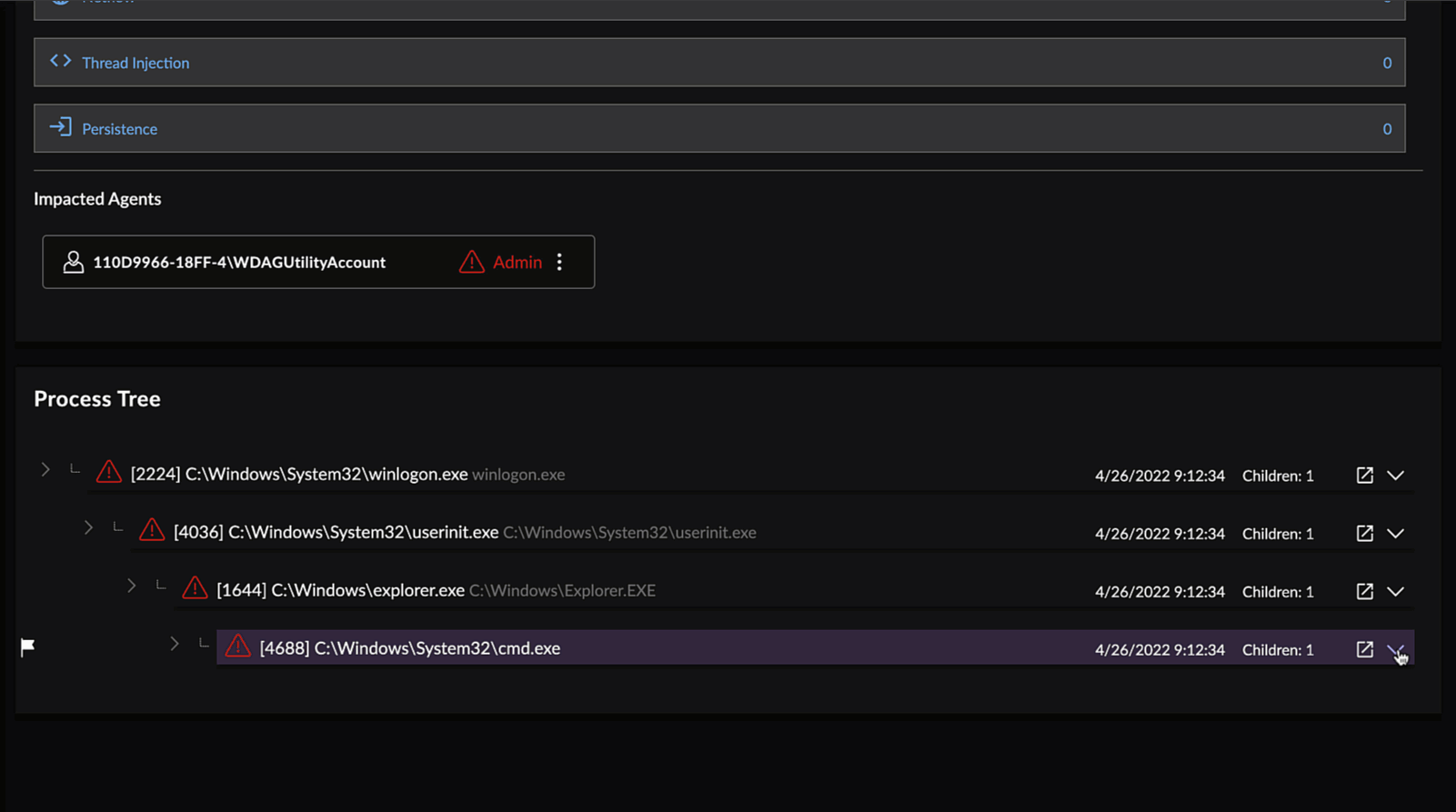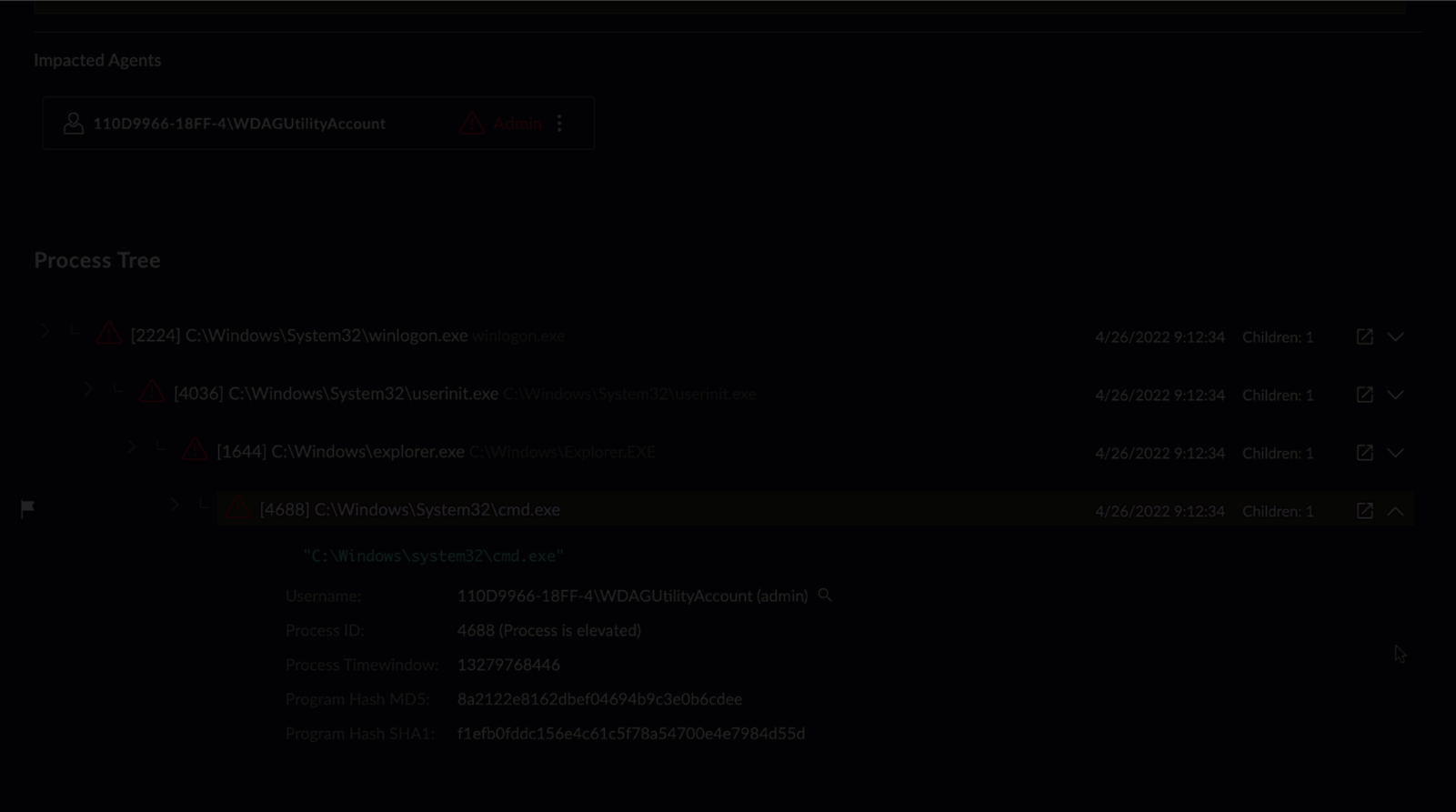
Event Details for a Process Event
When viewing tables of events, select an event title to view some of its essential details in a preview side panel. This allows you to continue browsing through the results table without losing your place or your filters. To view the full details of the event, select Open in a New Tab. The event details panel opens in a new tab.
Tip
Adjust the width of the preview side panel by holding and dragging it.
Event Details ⫘
Most events include:
-
Event Summary — A short summary of what occurred in the event.
-
Netflow Diagram — Netflow and NIDS events may show a netflow diagram.
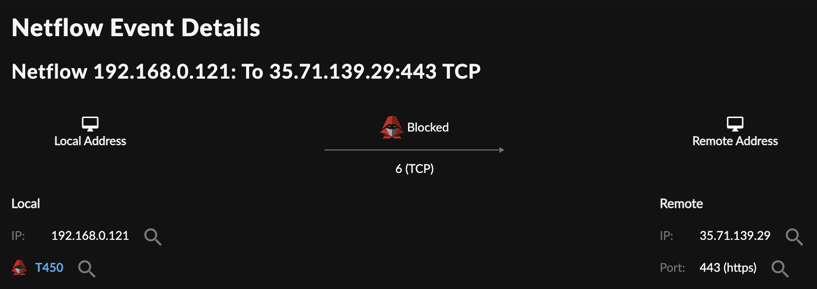
NIDS Event Showing Netflow Diagram
-
Event Details Table — Provides a selection of the normalized information about the event. The line items in the table vary dependent on event type.
-
Normalized Data — Shows all of the normalized information about the event, in JSON format in an expandable/foldable tree view.
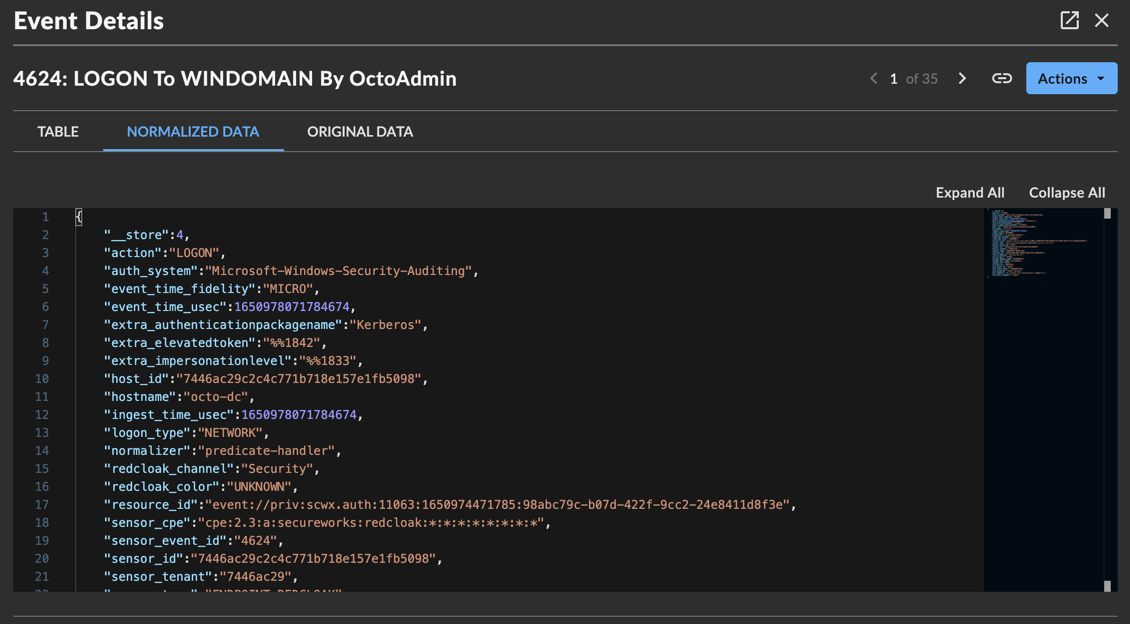
JSON View in Event Details for an Auth Event
- Original Data — If available, shows the original, pre-normalization data for the event.
Process Event Details ⫘
In addition to the above Event Details, process events include:
- Process Tree — A hierarchical view of process ancestry in a tree display.
- View in Timeline — Allows the user to pivot from the selected process to a timeline view of related alerts and events that occurred on the same host, by host_id. For more information, see Related Events Timeline View.
Data Types ⫘
-
Alerts — Output from detectors based on events or event sets that trigger XDR alerts.
-
Events — Security telemetry from a single point in time.
Event Types ⫘
-
Antivirus Events — Events related to malware activity on hosts and networks.
-
API Call Events — Instances in which a process attempted (successfully or not) to call an operating system API.
-
Auth Events — Activities including login successes & failures, logoffs, etc.
-
Cloud Audit Events — Audit events from cloud-based applications and cloud-hosted infrastructure.
-
DHCP Events — Records of client and server DHCP activity, such as IP address assignments.
-
DNS Events — Records of domain name resolution requests by hosts.
-
Email Events — Events from email security services related to techniques such as phishing and spam.
-
Encrypt Events — Events related to SSL/TLS connection and X.509 certificate metadata.
-
File Modification Events — Instances in which a process attempted to create, modify, write, or delete a file.
-
Generic Events — Stores all raw log messages from syslog and some other ingestion sources. Note that generic events may also get normalized into other event types.
-
HTTP Events — Details on HTTP connections. For example, from proxy server logs.
-
Management Events — Instances in which management information has been accessed from hosts in an enterprise environment, for example, via WMI for Windows.
-
Netflow Events — Network traffic information from in and out of the box communications, including source/destination IPs and ports.
-
NIDS Events — Events from network intrusion detection and/or prevention systems.
-
Persistence Events — Events related to techniques such as Run keys, Scheduled Tasks, or Services, commonly used by attackers to maintain persistence in a compromised system.
-
Process Events — Arbitrary code execution in other live processes. Process events may have information about program launches and their associated command lines, parent/child relationships, and other information about programs and commands executed on the host, including target programs launched by main parent executables—for example, by PowerShell in Windows.
-
Process Module Events — Events generated when libraries have been loaded by different processes.
-
Registry Events — Properties of certain Windows registry entries, which may help to detect attacks.
-
Script Block Events — Executions of blocks of code (scripts) on a remote endpoint by an attacker or other entity.
-
Taegis Agent Events — Detections reported by the Taegis Agent
-
Third Party Alert Events — The event record of alerts produced on sources external to XDR
-
Thread Injection Events — Instances in which a thread has inserted and run code within the memory address space of a different target process.
Create an Investigation From an Event ⫘
- At the top of the Event Details page, open the Actions drop-down and select Create New Investigation. The Create New Investigation dialog displays.
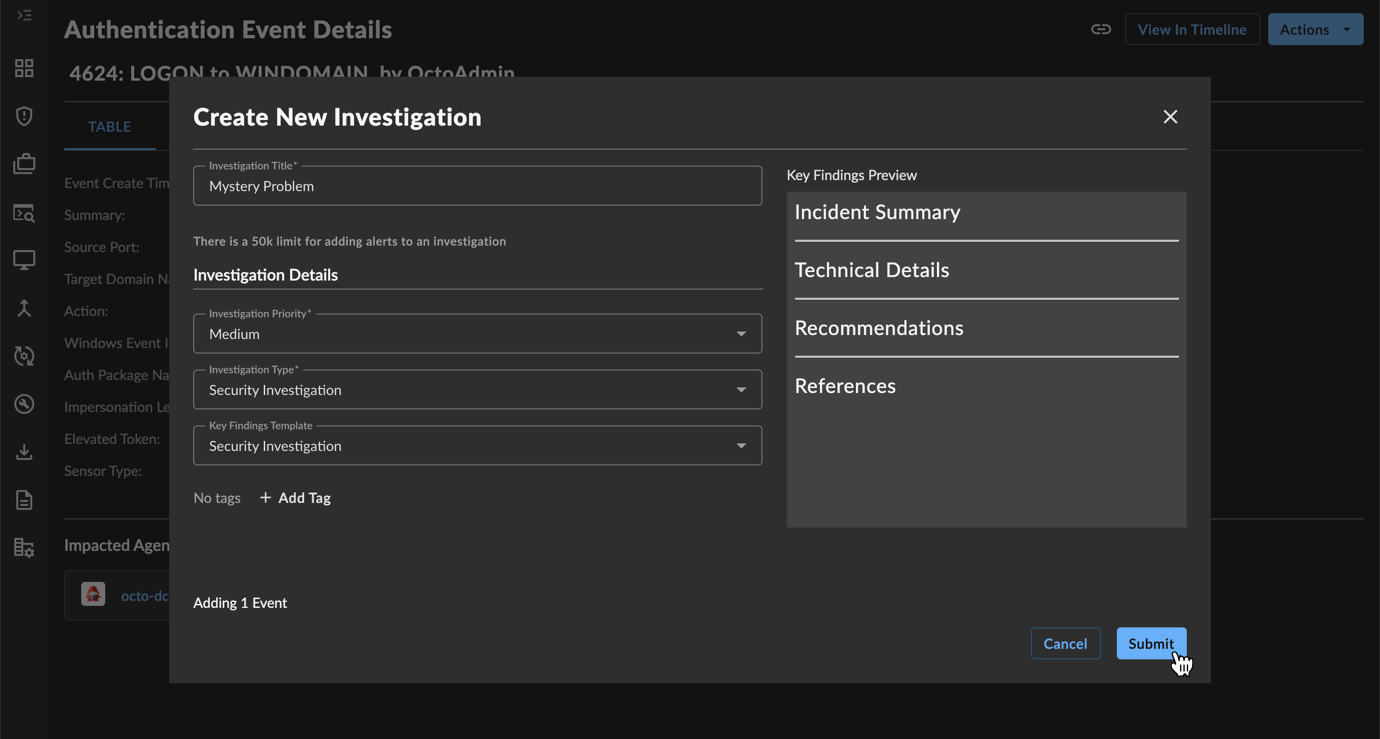
New Investigation
- Give the investigation a title and select a Priority and Type.
- Specify the Key Findings Template as blank or Security Investigation, then select Submit. The investigation is created.
Add an Event to an Existing Investigation ⫘
-
At the top of the Event Details page, open the Actions drop-down and select Add to Existing Investigation. The Add Evidence to Investigation dialog displays.
-
Select the investigation you want to add the event to, then select Submit.
