Lambda Migration
integrations cloud aws amazon lambda
The following instructions are for updating the Secureworks® Taegis™ XDR Lambda function used in the following integrations:
- AWS CloudTrail
- AWS CloudWatch Logs
- Amazon Applicaiton Load Balancer (ALB)
- Amazon VPC Flow Logs
- AWS Web Application Firewall
- Cisco Umbrella
Download Files from XDR ⫘
- From the left-hand side navigation in XDR, select Integrations → Cloud APIs.
- Select the Download Integration icon for any any active Lambda deployments
Download Integration Button
- Select Download CloudFormation Shared Resources and save it as
taegis-cloudformation-shared-resources.yaml. - Select Download CloudFormation Lambda Template and save it as
taegis-cloudformation-lambda-template.yaml. - Select Download Lambda; the file should be named
taegis-lambda-amd64.zip. - Select Download Credentials.
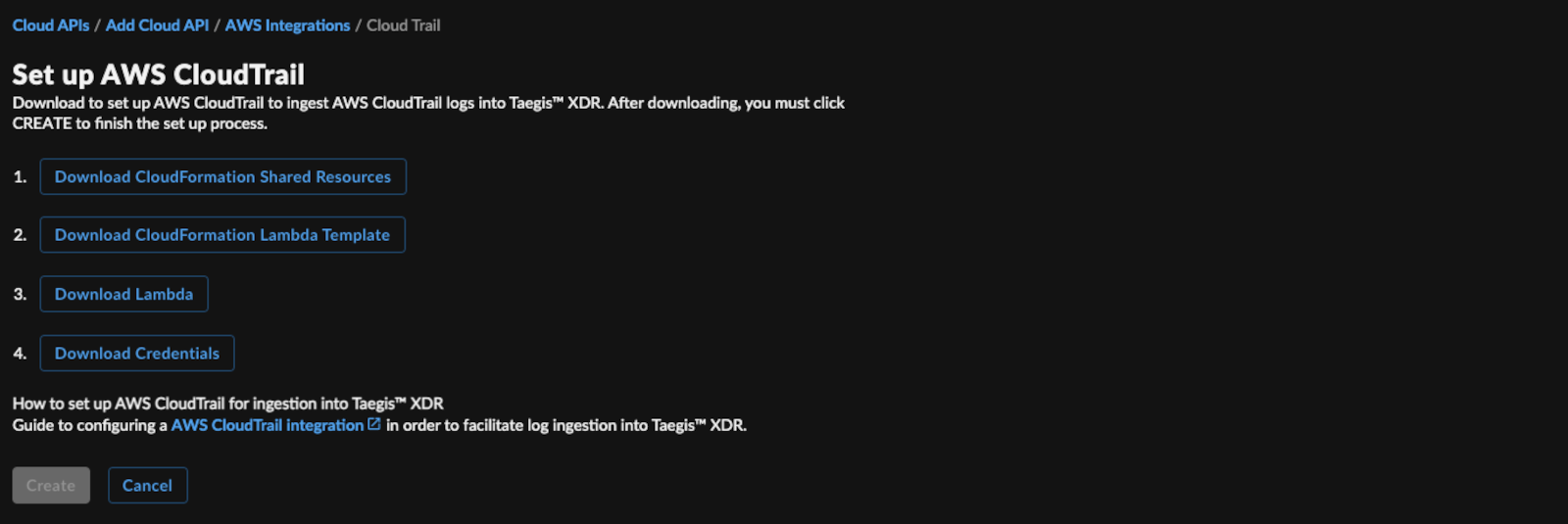
Download Lambda Integration Files
Upload the Lambda Executable and CloudFormation Templates to S3 ⫘
- Log in to the AWS Console for the region (e.g., https://us-east-1.console.aws.amazon.com/cloudformation) with an account that has permissions to create roles, lambdas, secrets, and policies, or using a role that can assume another role with these permissions.
- In the Storage section, select S3.
- Create a new bucket or locate an existing bucket in which to store the Lambda executable and, optionally, the CloudFormation templates. The bucket does not need to be public, versioned, or encrypted.
- Upload the Lambda
taegis-lambda-amd64.zipto the root of the bucket and take note of the bucket name. - Optionally upload
taegis-cloudformation-shared-resources.yamlandtaegis-cloudformation-lambda-template.yamlto the same bucket.
Tip
Take note of the bucket name and the key, including any prefix. These identifiers are needed when you create a stack.
Update in Each AWS Region That Contains the Existing Lambda Deployment ⫘
Create a Shared Resources Stack in Each AWS Region That Contains a Lambda Deployment ⫘
Important
The Shared Resources Stack (Steps 1-11) only needs to be deployed once per AWS region.
- Log in to the AWS Console for the region (e.g., https://us-east-1.console.aws.amazon.com/cloudformation) with an account that has permissions to create roles, lambdas, secrets, and policies, or using a role that can assume another role with these permissions.
- In the Management and Governance section, select CloudFormation.
- Select the Create Stack button to create a new stack using the
taegis-cloudformation-shared-resources.yamltemplate provided.
Note
You might see a list of CloudFormation stacks when you select CloudFormation like the following image. If that is the case, select the Create Stack drop down and choose With new resources (standard).
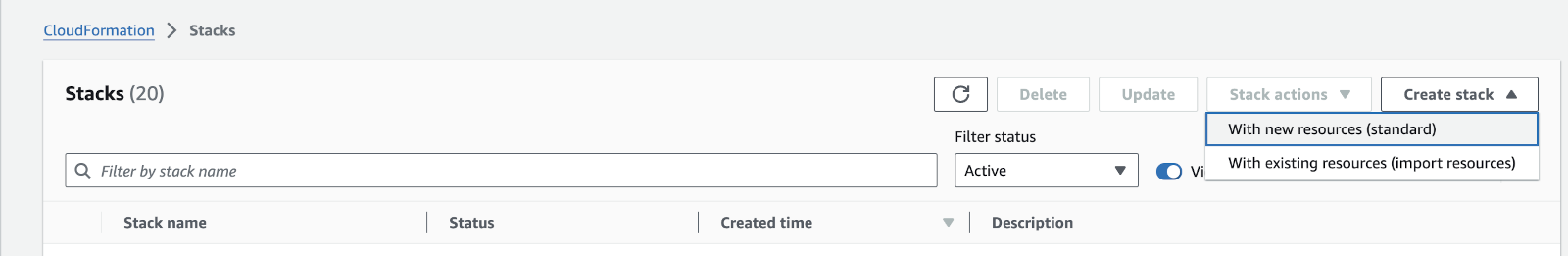
Create New Stack
- From the Prepare Template section, choose Template is ready.
- From the Specify Template section, choose Amazon S3 URL OR choose Upload a template file.
- If you choose Amazon S3 URL, input the CloudFormation object URL gathered previously into the Amazon S3 URL field. For example,
https://cwl-poc.s3.amazonaws.com/taegis-cloudformation-shared-resources.yaml.
To find the URL, navigate to the S3 service and open the S3 bucket to which the taegis-cloudformation-shared-resources.yaml file was uploaded. Select the CloudFormation template, then click the Copy URL button.
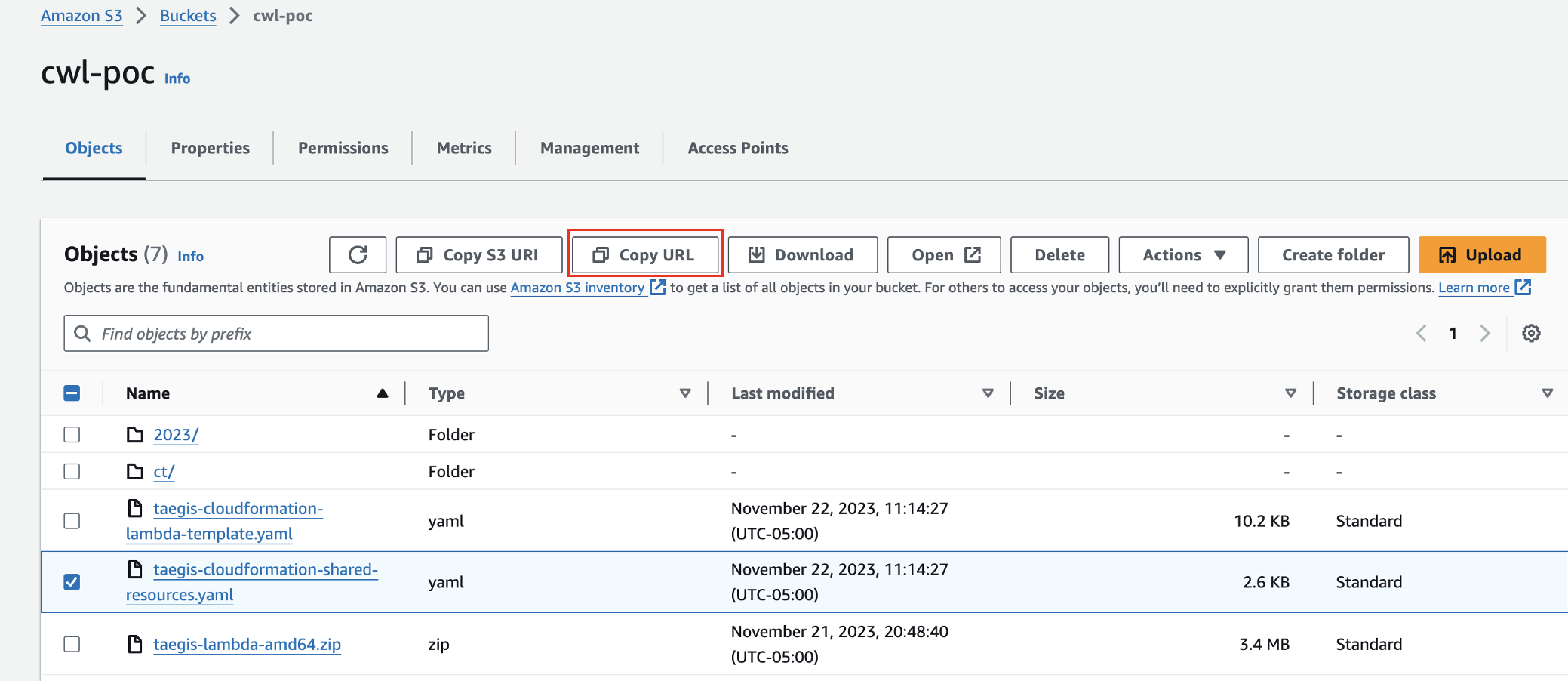
Copy CloudFormation URL
- Select Next.
- Enter an appropriate stack name.
Note
Spaces are not allowed in stack names.
- Enter the contents of the
credentials.txtfile into theSecretValuefield. - Select the correct
TaegisRegionbased off of your XDR login URL; for example, selectctpxif you use https://ctpx.secureworks.com/login orfoxtrotif you use https://foxtrot.taegis.secureworks.com/. - Select Next.
- On the Configure stack options page, the default selections and values can be accepted. Select Next.
- On the Review and create page, Select Submit.
Update the Current Running Lambda Stack ⫘
- Log in to the AWS Console for the region (e.g., https://us-east-1.console.aws.amazon.com/cloudformation) with an account that has permissions to create roles, lambdas, secrets, and policies, or using a role that can assume another role with these permissions.
- In the Management and Governance section, select CloudFormation.
- Select the button for the existing XDR Lambda CloudFormation stack.
Note
During the intial Lambda deployment, any string could be used to name the Lambda CloudFormation stack. The default CloudFormation template description may be helpful in identifying the existing Lambda CloudFormation stack. For example, “This CloudFormation template deploys the SecureWorks TDR Lambda function for <integration name> logs stored in an S3 bucket.” where <integration name> is, for example, “awscloudtrail”
- From the top right, select Update.
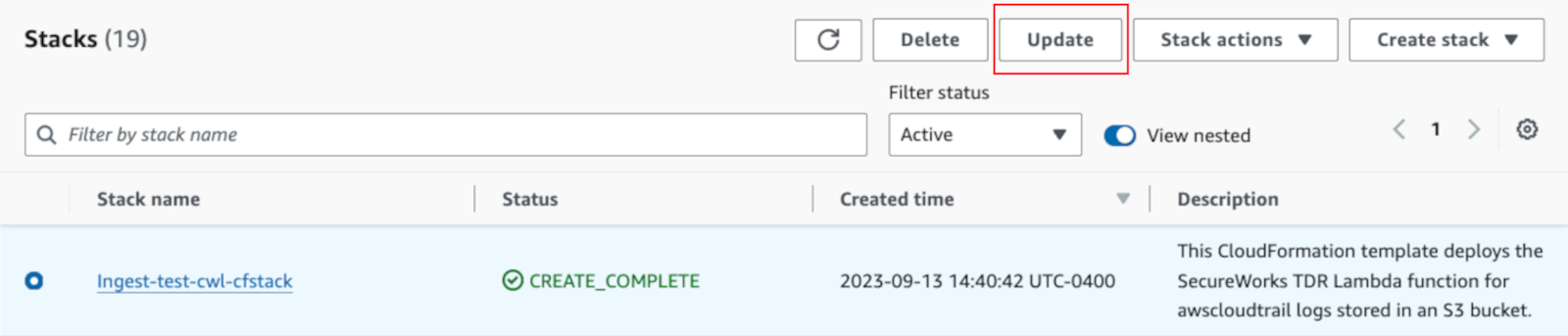
Update Lambda Stack
- Select Replace current template.
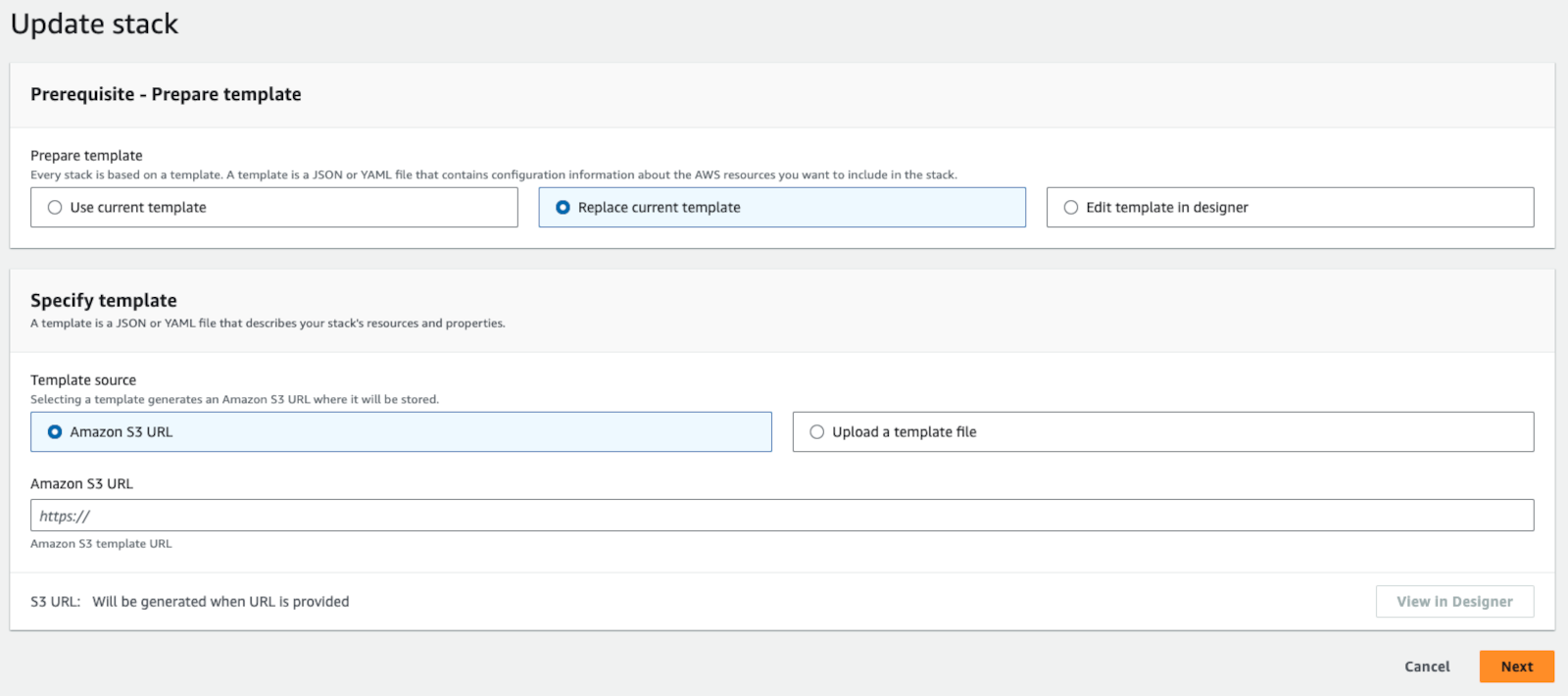
Replace Existing Lambda Stack
- Either Upload a template file and choose
taegis-cloudformation-lambda-template.yaml, or if you uploaded the template to an S3 bucket, use the Amazon S3 URL option. - Select Next.
Make the Updates to the Current Running Lambda Stack ⫘
- Select
IntegrationTypefrom the dropdown. This describes what sort of log objects are in theNotificationBucket. If more than one type, or you are not sure, selectgeneric.
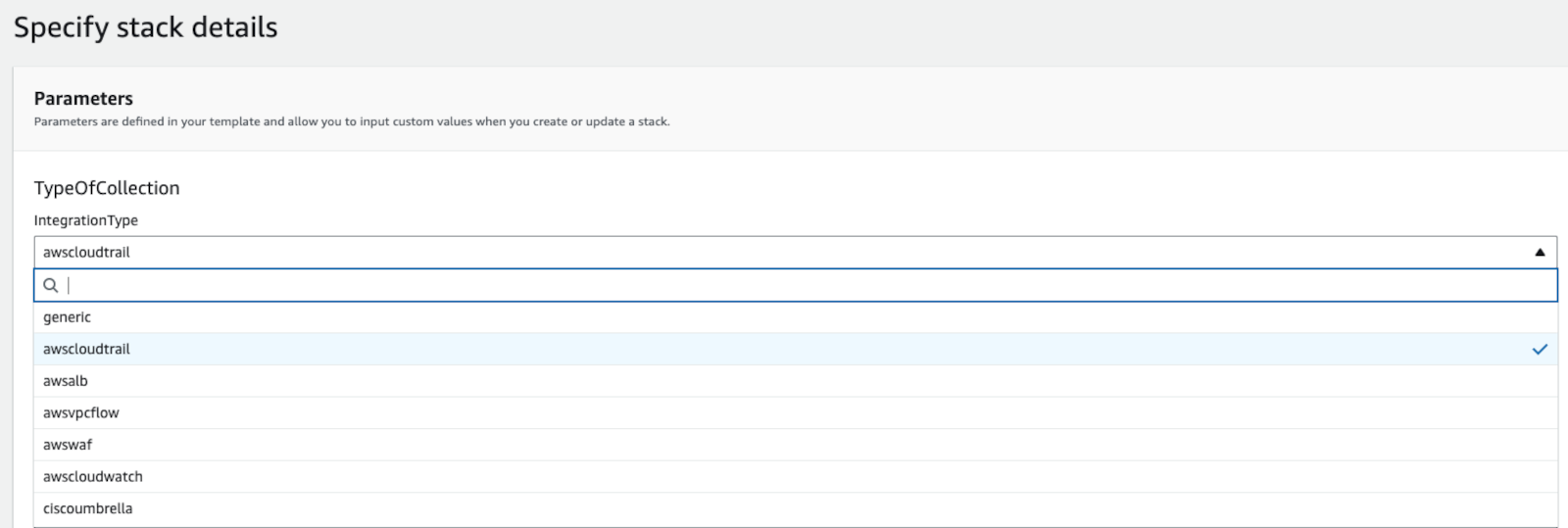
Update Lambda Stack Integration Type
- The field
NotificationBucketdoes not need to be changed. - The field
SNSNotificationarndoes not need to be changed, unless you wish to use SNS notifications going forward instead of S3 notifications. - The field
NotificationBucketCustomerManagedKMSarndoes not need to be changed, unless you wish to add the KMS key ARN that may be encrypting the objects in theNotificationBucket. The KMS key policy must haveEnable IAM User Permissions. If not, the Lambda ARN can be added to your KMS key. - The field
TaegisLambdaS3BucketNameshould be the bucketName specified in the Upload the Lambda Executable and CloudFormation Templates to S3 section. - The field
LambdaEnvKMSarncan be left empty. If populated, the KMS key must haveEnable IAM User Permissions. - The remaining fields can be left at their defaults.
- Select Next.
Complete Remaining Stack Options ⫘
- On the Configure stack options page, accept the defaults and click Next.
- Review the stack changes. The
Action,Logical ID,Resource typeandReplacementvalues should match the following:
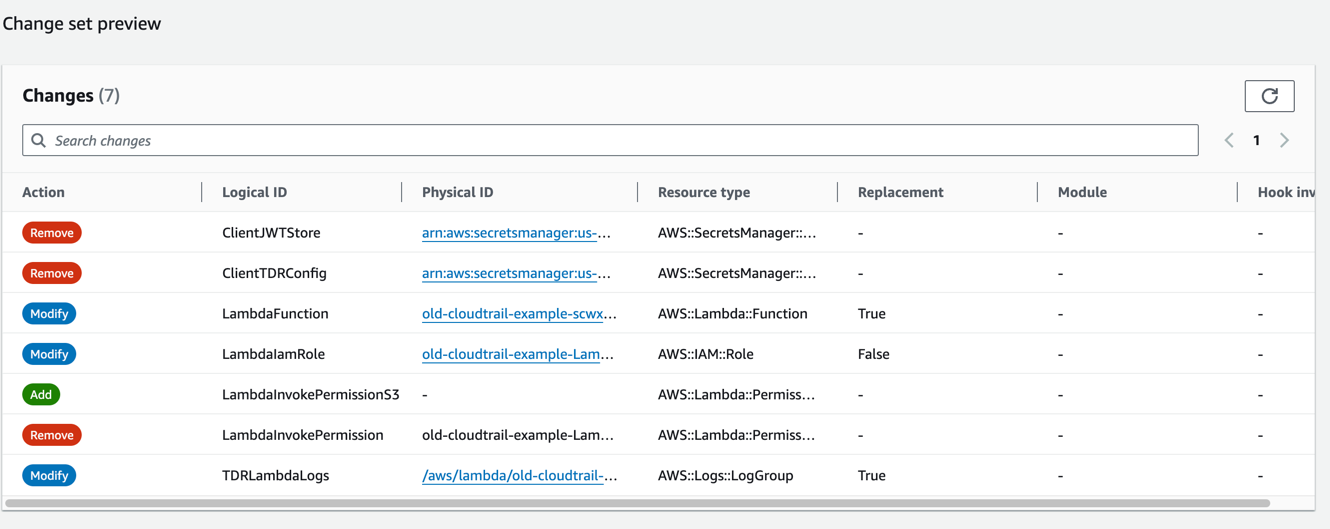
CloudFormation Change Set Preview
- Select the I acknowledge that AWS CloudFormation might create IAM resources checkbox and choose Submit.
Verification Steps ⫘
- In the AWS console for the region (e.g., https://us-east-1.console.aws.amazon.com/), navigate to Amazon S3 (e.g. https://s3.console.aws.amazon.com/s3/home?region=us-east-2), and select the S3 bucket where logs are hosted (Notification Bucket).
S3 Bucket Properties
- Navigate to the Event notifications section. If a Lambda function exists, select and delete it.
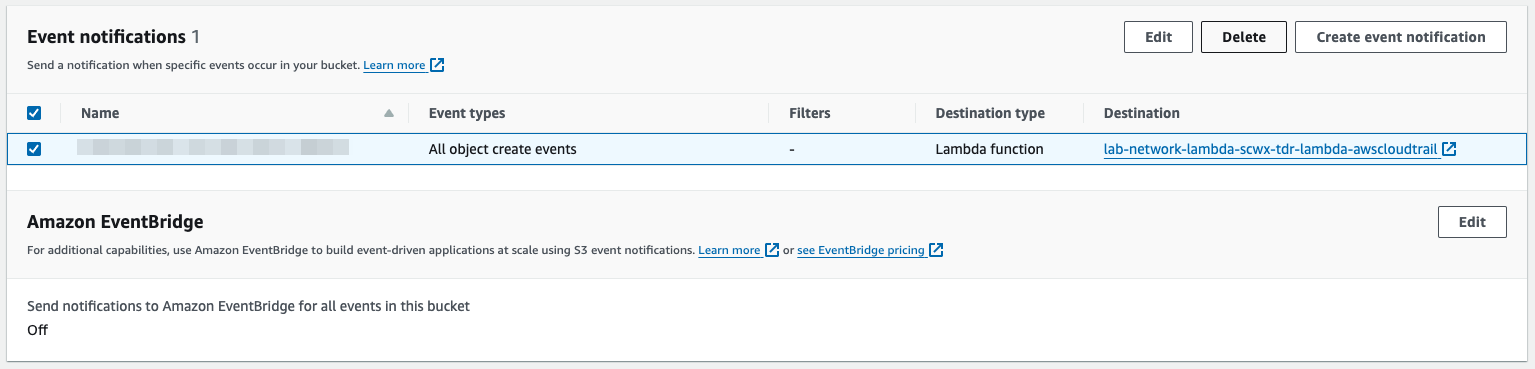
S3 Event Notification
-
Navigate to the Lambda service, select the recently updated Lambda function (e.g. lab-network-lambda-scwx-tdr-lambda-awscloudtrail), and add the S3 trigger.
-
Verify Lambda Runtime settings. The
Runtimevalue should be Custom runtime on Amazon Linux 2.
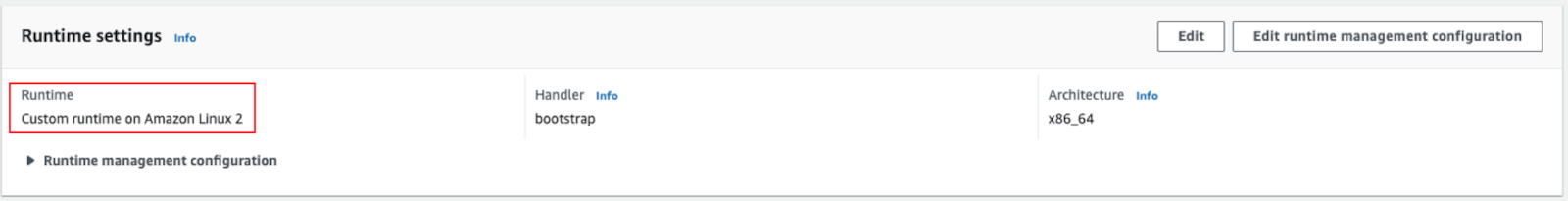
Verify Lambda Runtime Settings
-
See Test AWS Lambda Logs to verify that the AWS Lambda function for your integration is working by configuring a test for it in the AWS Console.
-
In the AWS console, go to the Lambda function that was installed. If there is an error, select Fix errors.
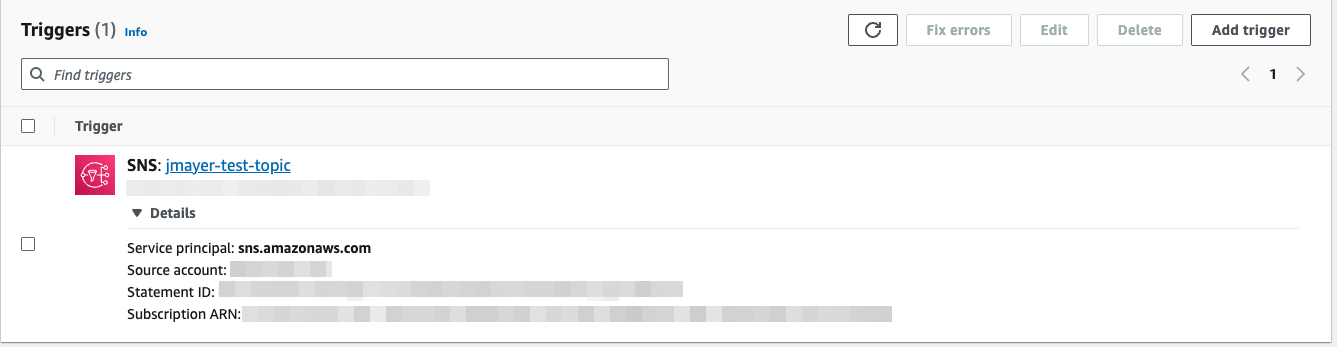
Fix Lambda Errors
- See View AWS Lambda Logs to view logs generated by your AWS Lambda functions and verify successful uploads. This verifies the trigger is working, on the assumption there is new S3 data being published to the bucket.
{"level":"debug","time":"2023-11-15T19:27:19Z","message":"Uploading data to s3"}
