IP Watchlist
The IP Watchlist Detector uses a Secureworks Counter Threat Unit™ (CTU) Threat Intelligence curated list of suspicious IP addresses and compares them to Netflow telemetry collected via supported endpoint and syslog data sources. When a suspicious IP is identified in tenant telemetry an alert is generated. The alert contains the list the suspicious IP was sourced from and the reason it is suspicious within the Alert Description.
Note
Taegis™ NDR automatically downloads the list of Secureworks malicious IP addresses and uses them within the reputation preprocessor to detect malicious traffic in real-time.
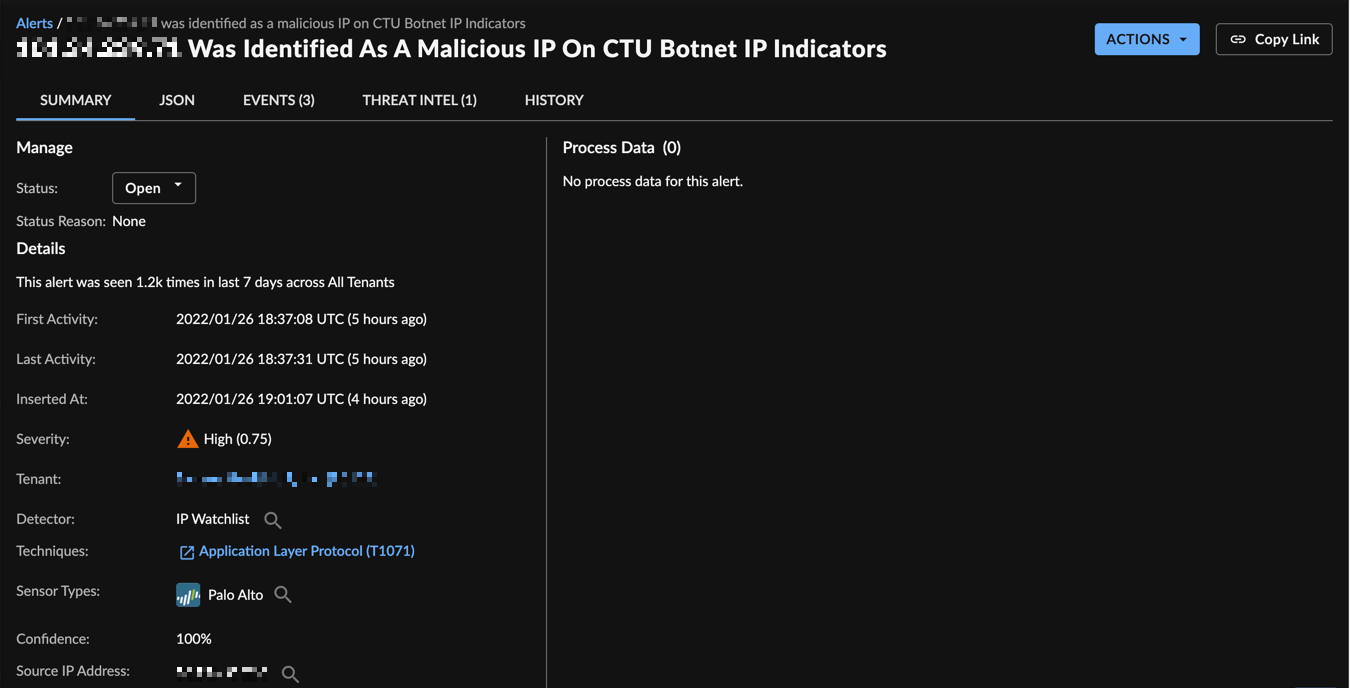
IP Watchlist Alert
Inputs ⫘
Netflow Source and Destination IP events, Endpoint Netflow events
Outputs ⫘
Malicious IP Alerts pushed to the Secureworks® Taegis™ XDR Alert Database and XDR Dashboard
- High alert severity, if matched IP address is the destination
- Low alert severity, if matched IP address is the source
MITRE ATT&CK Category ⫘
The IP Watchlist Detector has no MITRE Mapping.
Detector Requirements ⫘
- NIDS, Netflow
