Claroty Continuous Threat Detection (CTD) Integration Guide
Claroty Continuous Threat Detection (CTD) is an agentless and passive security solution designed to keep Industrial Control Systems (ICSs) operational. It provides real time visibility over assets and networks and uses both anomaly-based and behavior-based profiling to identify operational and security threats, including network failures, malicious attacks and operator errors.
The following instructions are for configuring CTD to facilitate log ingestion into Secureworks® Taegis™ XDR.
Logs can be sent from individual CTD Servers or the Enterprise Management Console (EMC).
Important
Adding this integration to your XDR tenant requires Taegis™ XDR for OT. Contact your account manager or CSM to acquire the required license.
Connectivity Requirements ⫘
| Source | Destination | Port/Protocol |
|---|---|---|
| CTD Server or EMC | Taegis™ XDR Collector (mgmt IP) | TCP/601 |
Data Provided from Integration ⫘
The following CTD event types are supported by XDR.
- Alerts (all Alert Types)
Note
CTD event types not listed above are normalized to the generic schema.
| Antivirus | Auth | DHCP | DNS | Encrypt | File | HTTP | Management | Netflow | NIDS | Process | Thirdparty | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Claroty CTD | D | V |
Y = Normalized | D = Out-of-the-Box Detections | V = Vendor-Specific Detections
Note
XDR detectors are not guaranteed to be triggered, even if a data source's logs are normalized to a schema associated with a given detector. However, you can create Custom Alert Rules to generate alerts based on normalized data from a data source.
Configure the Continous Threat Defense Platform ⫘
Follow the instructions in the Claroty CTD Administration Guide to configure Syslog forwarding.
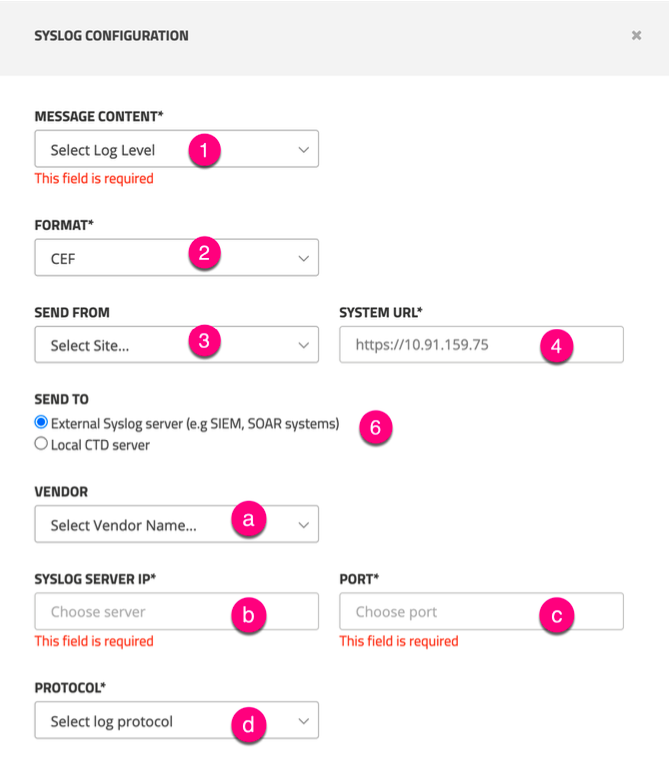
Syslog Configuration
Enter the following information:
| Parameter | Value |
|---|---|
| MESSAGE CONTENT | Alerts (all Alert Categories and Types) |
| FORMAT | CEF |
| SEND FROM (when sending from the EMC) | Select applicable CTD Servers |
| SYSTEM URL (when sending from the EMC) | Read-Only Value |
| SEND TO | External Syslog server |
| VENDOR | Other |
| SYSLOG SERVER IP | XDR Collector (mgmt IP) |
| PORT | 601 |
| PROTOCOL | TCP |
Advanced Search using the Query Language ⫘
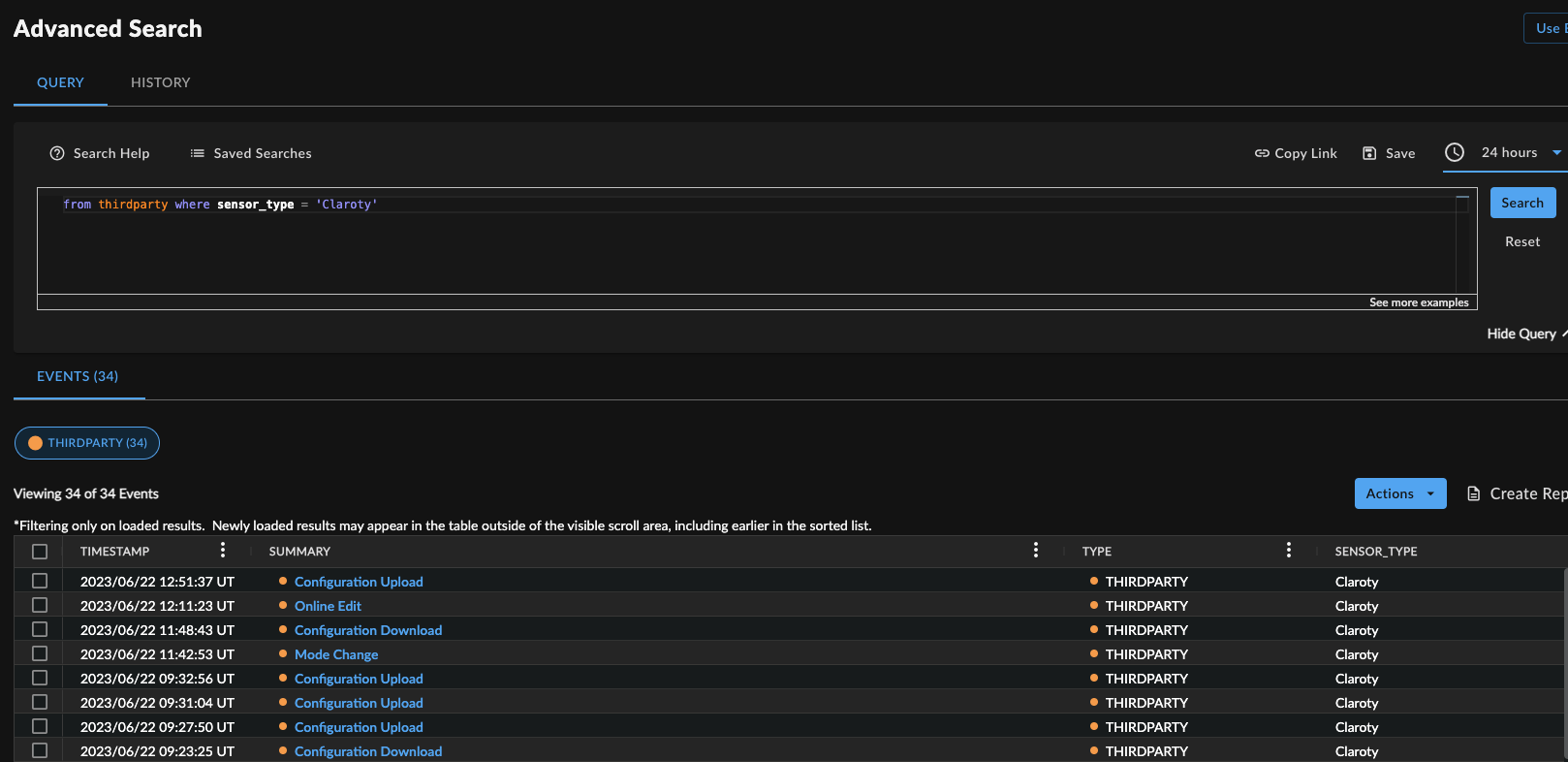
Claroty Advanced Search
Example Query Language Searches ⫘
To search for thirdparty events from the last 24 hours:
FROM thirdparty WHERE sensor_type = 'Claroty' and EARLIEST=-24h
To search for netflow events:
FROM netflow WHERE sensor_type = 'Claroty'
To search for events that were classified by Claroty as "Critical":
WHERE sensor_type = 'Claroty' AND vendor_severity = 'Critical'
To search for thirdparty events from a specific CTD Server or EMC:
FROM thirdparty WHERE sensor_type = 'Claroty' AND sensor_id = '10.10.10.10'
Event Details ⫘
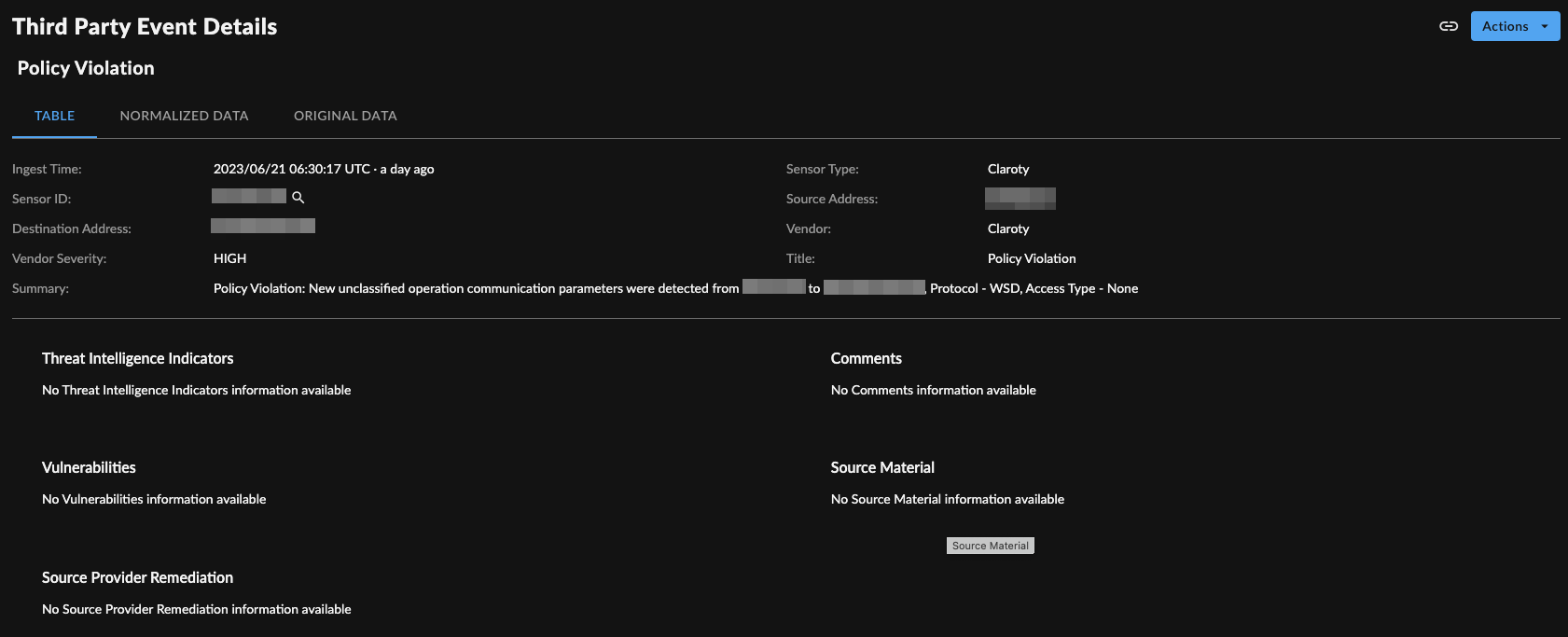
CTD Event Details
Sample Logs ⫘
CTD Alerts ⫘
CEF:0|Claroty|CTD|4.2.3|Alert|Known Threat Alert|5| cn1Label=SiteId cn1=1 cs1Label=Site cs1=Default cs2Label=Network cs2=Default cs3Label=Resolve-dAs cs3=Unresolved cs5Label=Src Zone cs5=Default Zone cs6Label=Dst Zone cs6=Default Zone cs7Label=Category cs7=Security cs8Label=AlertUrl cs8=http://<IP.Address>/alert/1-1 outcome=Unresolved request=http://<IP.Address>/alert/1-1 cn2Label=Alert Score cn2=100 cs10Label=PrimaryAssetIP cs10=10.5.22.101 cs11Label=PrimaryAssetType cs11=Endpoint cs12Label=PrimaryAssetHostname cs12=N/A cs13Label=PrimaryAssetMAC cs13=00:00:00:00:00:00 cs14Label=PrimaryAssetOS cs14=Windows 7/Server 2008 R2 cs15Label=PrimaryAssetVendor cs15=Hewlett Packard cs16Label=NonPrimaryAssetIP cs16=000.00.0.000 cs17Label=NonPrimaryAssetType cs17=Endpoint cs18Label=NonPrimaryAssetHostname cs18=N/A cs19Label=NonPrimaryAssetMAC cs19=00:00:00:00:00:f1 cs20Label=NonPrimaryAssetOS cs20=N/A cs21Label=NonPrimaryAssetVendor cs21=Netgear cn3Label=StoryId cn3=1 src=10.5.22.101 smac=00:08:00:00:00:00 shost=N/A dst=000.00.0.000 dmac=00:00:00:00:00:00 dhost=N/A externalId=1 cat=Create rt=Nov 17 10:18:55 start=Oct 12 2020 17:28:33 msg=Out of working hours Known Threat: Threat Claroty Rule: GranCrab Ransomware - C2 Certificate was detected from 10.5.22.101 to 000.00.0.000
