Office 365 and Azure Integration Guide
integrations cloud microsoft office 365 azure
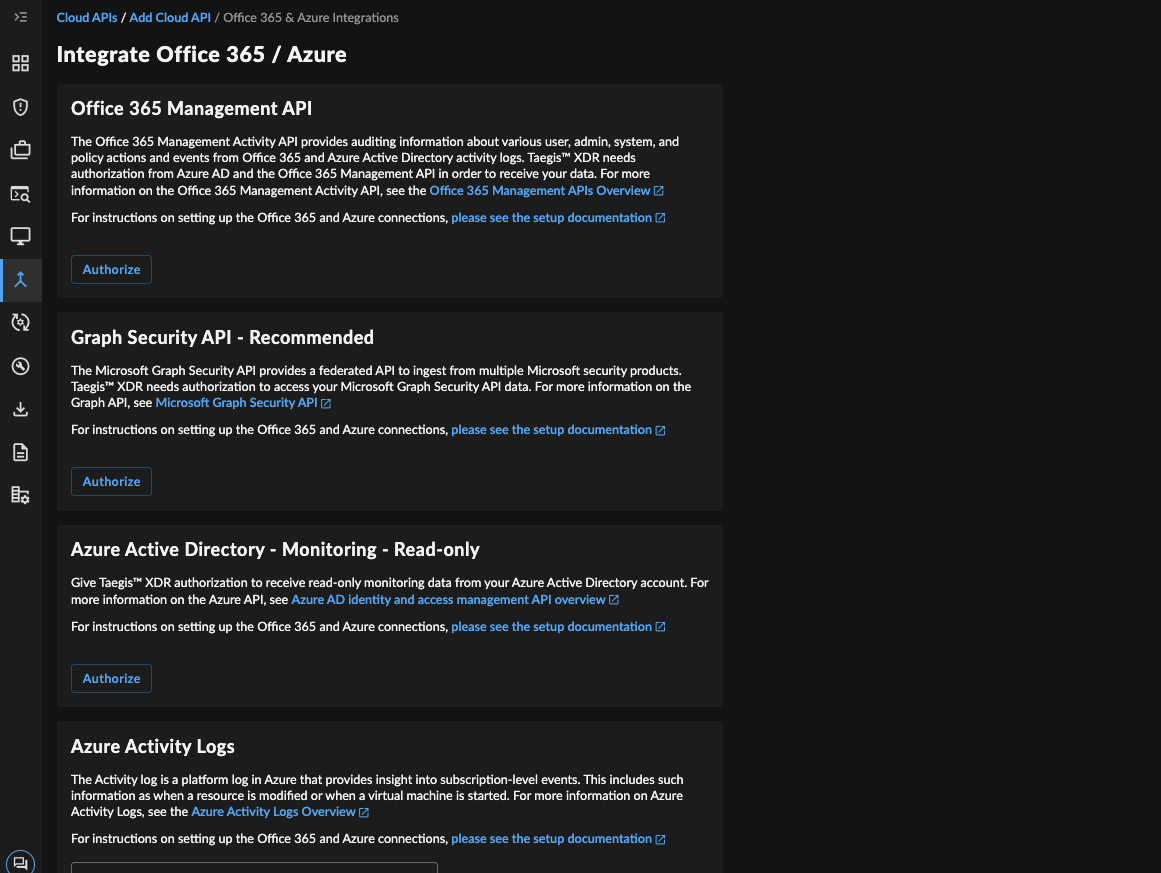
Secureworks® Taegis™ XDR is capable of ingesting data from Microsoft Office 365, the Security Graph, and the Azure AD Audit Logs, through Microsoft’s Azure AD Audit Log API (within the Graph API), Office 365 Management API, and Graph Security API, respectively. Configuration can be done in XDR; you must authorize XDR to work with the Microsoft service(s) that you want to integrate with. It is possible to monitor multiple Microsoft accounts for the same service. Navigate to Integrations > Cloud APIs in XDR to set it up.
Manage Azure Integrations in XDR
Available Integrations ⫘
Existing options for XDR in-app integration with Microsoft Office 365 and Azure Active Directory include the following.
Notes
- Azure integrations are supported in US and EU regions, but may not be supported by Microsoft in other regions. Contact Microsoft directly to verify their support of services in other regions.
- Azure Active Directory and Microsoft 365 integrations are available for the global Azure cloud. Other national clouds, such as Azure Government, Azure China 21Vianet, and Azure Germany are currently not supported.
Office 365 Management API ⫘
Note
This integration has been superseded by the new Microsoft Office 365 Management API integration.
The Office 365 Management Activity API provides auditing information about various user, admin, system, and policy actions and events from Office 365 and Azure Active Directory activity logs. XDR needs authorization from Azure AD and the Office 365 Management API in order to receive your data.
Important
You must turn on Office 365 audit logging for XDR to receive data from it. Audit logging for Office 365 is off by default. For more information, see Turn Office 365 audit log search on or off.
For more information on the Office 365 Management Activity API, see the Office 365 Management APIs Overview.
Microsoft Graph Security API ⫘
For more information on configuring an integration of Microsoft Graph Security API Alert logs with Secureworks® Taegis™ XDR, see Microsoft Graph Security Alerts Integration Guide.
Azure Active Directory Identity Protection—Risk Detection ⫘
For more information on configuring an integration of Microsoft Entra Risk Detection logs with Secureworks® Taegis™ XDR, see Microsoft Entra Risk Detection Integration Guide.
Azure Active Directory — Monitoring ⫘
Note
This integration has been superseded by the Microsoft Azure Active Directory Activity Reports integration.
You can set up XDR to receive security data from your Azure AD account(s). This single integration runs two queries that provide different sets of data: List signIns and Get directoryAudit. Each is listed in the Cloud API Integrations table as a separate entry.
Please note that this requires a Microsoft AAD P1 license. Required permissions are documented on these pages from the Microsoft Graph documentation:
Events are ingested using the Microsoft REST APIs on a polling basis, with new data being requested every minute. Once the data is ingested, it usually takes 30 minutes to appear in XDR, but could take up to an hour.
Note
In cases where a federated Azure AD environment is in use, AD audit data may contain incomplete (null) information for some field values that prevent some detections in XDR from alerting correctly. It is recommended clients use AD Connect Health to monitor the health of their AD connections with Azure.
Azure Active Directory — Actions/Response ⫘
The XDR Azure AD Actions/Response option is no longer supported. If you want to take actions on your Azure AD accounts, configure XDR Playbooks.
Authorization ⫘
Access to Microsoft data in the Microsoft APIs requires a one-time authentication from the Cloud APIs section. The incoming data is then accessed directly from the corresponding Microsoft API.
During the authorization process, XDR asks you to log in to Azure Active Directory (AAD) as an AAD user who has the ability to grant admin consent for the requisite permissions. The admin consent prompt lists the permissions that this user must be able to grant to the XDR application.
Note
Once authorized, the XDR cloud receives data from your MS cloud-based products directly; this does not involve the Taegis™ XDR Collector.
Note
Authorization is granted by the logged in AAD (Azure Active Directory) user. Granting admin consent requires you to sign in as global administrator, an application administrator, or a cloud application administrator. If the process of authorizing an integration appears to have failed, your logged in AAD user may be missing the permissions to grant the requisite levels of admin consent. If possible, try again with a user who is a global admin role in AAD.
Data Provided from Integrations ⫘
| Antivirus | Auth | CloudAudit | DHCP | DNS | Encrypt | HTTP | Management | Netflow | NIDS | Thirdparty | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| MS Graph Security | V | V | ||||||||||
| MS Azure Active Directory Identity Protection | V | V | ||||||||||
| MS Azure Active Directory | Y | Y | ||||||||||
| MS Office 365 | D, V | V | V | V |
Y = Normalized | D = Out-of-the-Box Detections | V = Vendor-Specific Detections
Note
XDR detectors are not guaranteed to be triggered, even if a data source's logs are normalized to a schema associated with a given detector. However, you can create Custom Alert Rules to generate alerts based on normalized data from a data source.
More Reading ⫘
- Microsoft Graph Security API whitepaper: An Introduction to the Microsoft Graph Security API.
- Azure AD Audit Log API Overview
- Office 365 Management API
Link Secureworks as a Microsoft Partner ⫘
Linking Secureworks as a Solution Provider for Security is an optional process that enables Microsoft to better understand what customers Secureworks is enabling to achieve their security goals and realize the value of the Microsoft ecosystem. This allows Secureworks better access to Microsoft as a partner, enabling us to provide you, our customer, with better products and services. If you have successfully added access to your Azure environment to allow Secureworks to help enable your business through improved security, we would appreciate if you would additionally add us as a partner link to show that this is in place.
To link Secureworks as a partner, folllow these steps:
- Navigate to Link to a partner ID in the Azure Portal.
- Use a user with eligible roles or permissions, see Roles and Permissions Required to Receive Credit.
- In the Microsoft Partner ID box, enter the value:
4834104 - Click on the Link a partner ID button to complete the process.
