Kerberoasting Detector
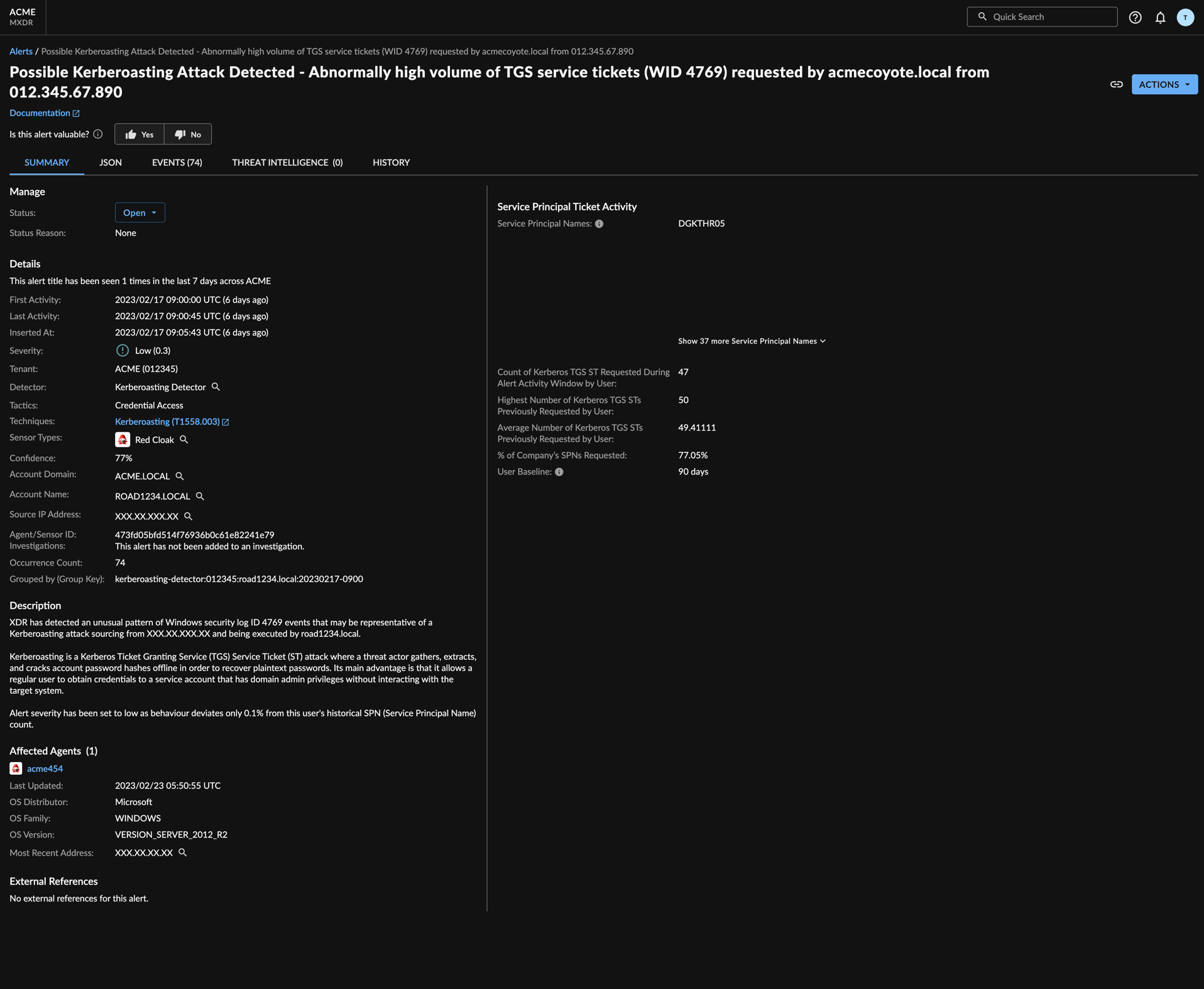
The Kerberoasting Detector identifies a possible Kerberos Ticket Granting Service (TGS) Service Ticket (ST) attack where a threat actor gathers, extracts, and cracks account password hashes offline in order to recover plaintext passwords. Its main advantage is that it allows a regular user to obtain credentials to a service account that has domain admin privileges without interacting with the target system.
Kerberoasting Detector
Schema ⫘
Auth
Outputs ⫘
Alerts pushed to the Secureworks® Taegis™ XDR Alert Database and XDR Dashboard.
MITRE ATT&CK Category ⫘
MITRE Enterprise ATT&CK - Credential Access - Steal or Forge Kerberos Tickets: Kerberoasting. For more information, see MITRE Technique T1558.003.
Configuration Options ⫘
None
