Quick Mail Consent (MS O365)
Mail.Read and Mail.ReadWrite delegated permissions are extremely sensitive permissions that can allow access to user email without a signed-in user. Secureworks® Taegis™ XDR’s Office 365 Quick Mail Consent Detector monitors your Office 365 audit logs for applications granted Mail.Read or Mail.ReadWrite permissions, and related application consent logs that occur within a short period of time. The time period is calibrated according to attack patterns by known threat actors. Due to the sensitivity of the permission set being monitored and the detector monitoring for fully consented applications, alerts produced by this detector contain a high severity rating. Suppression is supported.
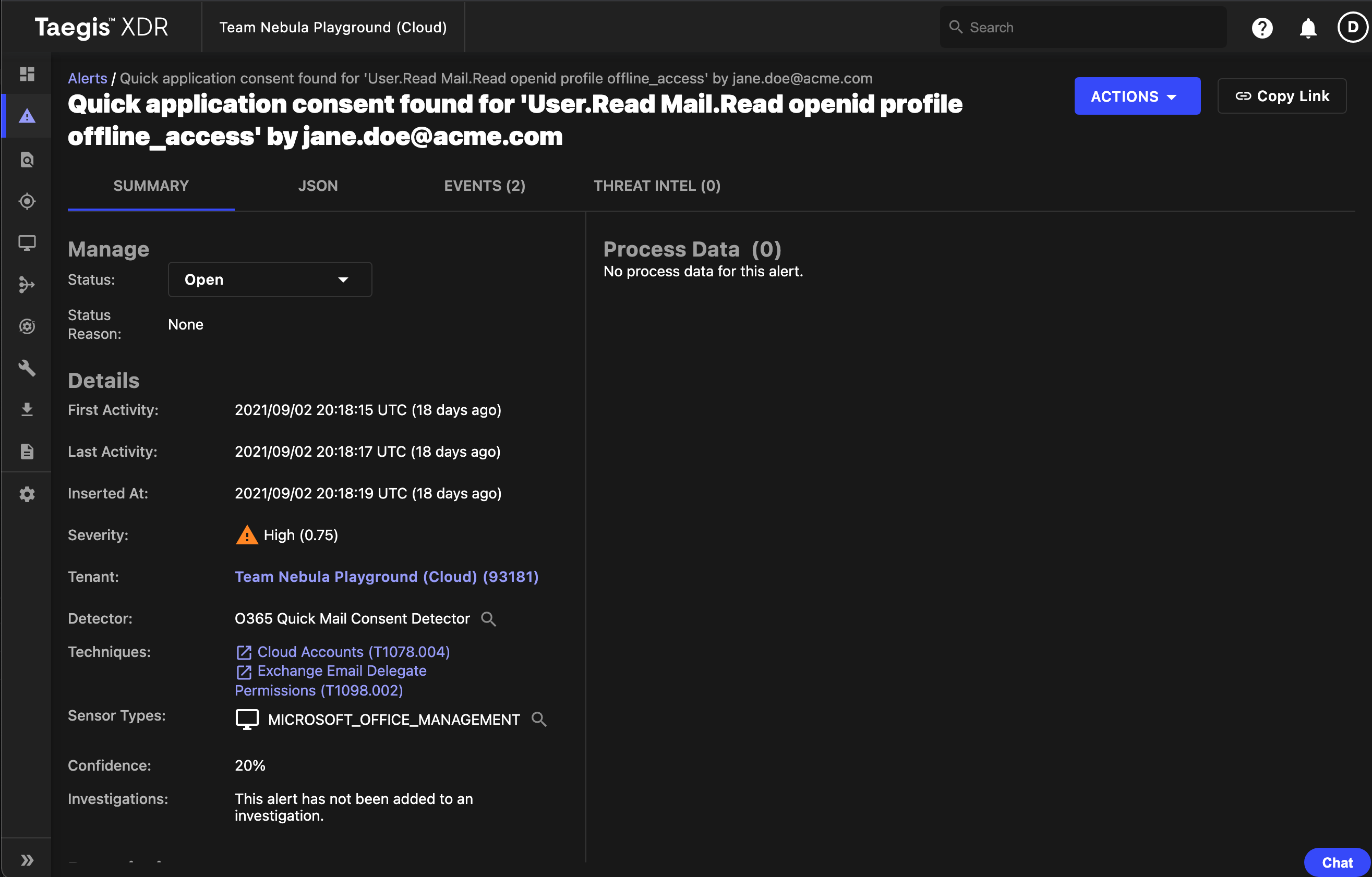
O365 Quick Mail Consent Detector Alert
Inputs ⫘
Microsoft Office 365 audit logs collected through the Microsoft Office 365 Management API integration and normalized to the CloudAudit schema in the XDR data lake.
Outputs ⫘
Alerts generated by Tactic Graphs™ Detector are pushed to the XDR Alert Triage Dashboard.
MITRE ATT&CK Category ⫘
- MITRE Enterprise ATT&CK - Defense Evasion - Valid Accounts - Cloud Accounts. For more information, see MITRE Technique T1078.004.
- MITRE Enterprise ATT&CK - Persistence - Account Manipulation - Exchange Email Delegate Permissions. For more information, see MITRE Technique T1098.002.
Configuration Options ⫘
None
Detector Requirements ⫘
- Microsoft Office 365 Management API audit logs
